ADFS Auth Proxy
This topic describes how to configure the O365 sign-in flow to go through your Active Directory Federation Services (ADFS). The ADFS auth proxy will act as the pass-through proxy for all authentications. Use this document if you have O365 set up with ADFS using WS-Fed.
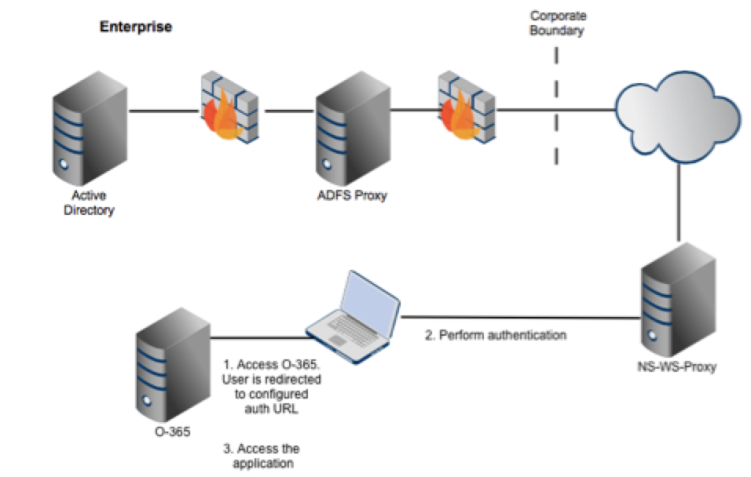
ADFS Auth Proxy intermediates the authentication workflow between enterprise users and your organization's on-premise ADFS, which typically includes an internal ADFS server hosted from within your network and an ADFS proxy residing in your organization's perimeter (DMZ). ADFS auth proxy front-ends your ADFS proxy. User experience is unchanged, as the federation service itself is unchanged.
The Netskope ADFS Auth Proxy ensures that enterprise users from your organization are protected by Netskope Security Cloud Platform. It redirects all user "Browser" sessions, which are not within the Netskope Source IP Address Ranges (Netskope Client installed and enabled) to the Netskope reverse proxy. This ensures O365 access is managed. Exceptions can be made by an admin to allow certain source IP addresses and ranges to bypass the reverse proxy redirection. And for non-browser flows, the O365 access is only allowed from managed devices.
The following diagram illustrates a deployment scenario where ADFS auth proxy is in your DMZ and accessible from the Internet.
O365 uses multiple authentication flows, namely:
Passive Authentication (used by web-based apps, like browsers)
Active Authentication (used by native apps, like Outlook on Windows)
MEX Flow (used by Native apps ex: Onedrive on Windows)
You can configure only Passive Authentication to go through the Netskope auth proxy, or both Passive and Active-MEX to go through Netskope auth proxy. With unmanaged devices, the reverse proxy redirection is applicable only for the passive authentication flow and for the browser-based apps.
The general configuration steps for the ADFS auth proxy are outlined below:
Log in to your O365 console, depending on which authentication flow is the customer intends to configure, copy your current Passive Client Signin URL or Active Client Signin URL or Federation Metadata URL. For details see, Accessing Your Active Auth, Passive Auth and MEX URLs.
Access the ADFS Auth Proxy window in your Netskope web UI. Enter :
O365 Passive Client Signin URL in the Customer Passive Auth URL field.
O365 Active Client Signin URL in the Customer Active Auth URL field.
O365 Customer Federation Metadata URL in the Customer Federation Metadata URL field.
Note
Depending on which flow customer intends to go through the Netskope Authentication Proxy, the customer can configure either of the above three fields.
Open your O365 console and change the Passive/Active/Federation-Metadata URL to point to the Netskope Passive/Active/Federation-Metadata URL . For details see, Configuring Your Netskope Passive Auth URL.
Access the ADFS Auth Proxy window in your Netskope tenant and have it open along with your O365 instance.
ADFS Auth Proxy Fields
The following table describes the ADFS Auth Proxy fields.
Field Names | Description |
|---|---|
Netskope Source IP Address/Range | Configure this list of Netskope source IPs if creating any Client Access policies on your ADFS. |
Customer Source IP Address/Range | Comma-separated bitmask IPs. You can access this field in edit mode. Note This is an optional field. Configure the set of IPs for which you want to bypass traffic redirection to Netskope's reverse proxy from an unmanaged device. For example, if you intend to bypass the reverse proxy for all on-premise users, then use this field to configure your Enterprise Public IPs. IPs configured in this field will be treated as trusted IPs and the Active and MEX authentication flows will be treated as happening from managed devices. |
Passive Client Authentication
Field Names | Description |
|---|---|
Bypass redirecting the passive auth flow to the reverse proxy | If this option is enabled, the ADFS auth proxy acts as a pass-through proxy for all passive authentication flows. |
Customer Passive Auth URL | This is your ADFS server URL that is in your DMZ which has been configured for your O365 Passive Client Sign in URL. You must have your O365 configuration with ADFS set up to access your Passive Sign in URL. |
Netskope Passive Auth URL | Netskope Passive Auth URL Copy this generated URL and configure it as the Passive Client Sign in URL and Passive Client Sign out URL in your O365 instance. |
Active Client Authentication — MEX Flow
Field Names | Description |
|---|---|
Bypass policy check for Active Auth and MEX flows | If this option is enabled, the ADFS auth proxy acts as a pass-through proxy for all active authentication and MEX flows. |
Customer Passive Auth URL | This is your ADFS server URL that is in your DMZ which has been configured for your O365 Passive Client Sign in URL. You must have your O365 configuration with ADFS set up to access your Passive Sign in URL. |
Block Unsupported Platforms | If this option is enabled, the ADFS auth proxy blocks all active authentication and MEX flows for unsupported platforms. |
Customer Active Auth URL | This is your ADFS server URL that is in your DMZ which has been configured for your O365 Active Client Sign in URL. You must have your O365 configuration with ADFS set up to access your Active Sign in URL. |
Netskope Active Auth URL | Copy this generated URL and configure it as the Active Client Sign in URL in your O365 instance. |
Customer Federation Metadata URL | This is your ADFS Federation Metadata URL that is in your DMZ which has been configured for your O365 Federation Metadata URL. You must have your O365 configuration with ADFS set up to access your Federation Metadata URL. |
Netskope Federation Metadata URL | Copy this generated URL and configure it as the Federation Metadata URL in your O365 instance. |
Access your Active Auth, Passive Auth, and MEX URLs
To access your active and passive authentication and MEX URLs:
Use Powershell to log in to your cloud O365 instance. Enter:
>> $cred=Get-Credential
Next enter your Admin credentials.
Enter:
>> Connect-MsolService –Credential $cred
Enter:
>> Get-MsolFederationProperty
Next enter your Federated Domain Name.
Copy the output of the above command. In the source section 'Microsoft Office 365' copy the values for the following fields:
PassiveClientSignInURL
ActiveClientSignInURL
FederationMetadataURL
Use the values from the fields above to configure the respective fields in the Netskope Admin UI below:
Customer Passive Auth URL
Customer Active Auth URL
Customer Federation Metadata URL
Configure your Active Auth, Passive Auth, and MEX URLs
To configure your active and passive authentication and MEX URLs:
Use Powershell to log in to your cloud O365 instance. Enter:
>> $cred=Get-Credential
Enter your Admin credentials.
Next enter:
>> Connect-MsolService –Credential $cred
Set the Netskope_Passive_URL variable:
>> $Netskope_Passive_URL = <Netskope Passive Auth URL in the Netskope AdminUI>
Set the Netskope_Active_URL variable:
>> $Netskope_Active_URL = <Netskope Active Auth URL in the Netskope AdminUI>
Set the Netskope_Federation_Metadata_URL variable:
>> $Netskope_Federation_Metadata_URL = <Netskope Federation Metadata URL in the Netskope AdminUI>
Set your domain variable:
>> $dom = <Customer Domain>
Update the Federation settings:
>> >> Set-MsolDomainFederationSettings –DomainName $dom -PassiveLogOnUri $Netskope_Passive_URL -LogOffUri $Netskope_Passive_URL -ActiveLogOnUri $Netskope_Active_URL -MetadataExchangeUri $Netskope_Federation_Metadata_URL
Note
Netskope_Passive_URL, Netskope_Active_URL, and Netskope_Federation_Metadata_URL are the URLs from the Netskope Admin UI.
Example Variables for the Set-MsolDomainAuthentication
For setting ONLY the Passive authentication flow through the Netskope Authentication Proxy:
$dom = "customerfeddomain.com"
$LogOnUrl = "https://aproxy.inskope.com/lna90xma60bkw05/1000/adfs/ls"
$LogOffUrl = "https://aproxy.inskope.com/lna90xma60bkw05/1000/adfs/ls"
Set-MsolDomainFederationSettings –DomainName $dom -PassiveLogOnUri $Netskope_URL -LogOffUri $Netskope_URL
For setting Passive, Active, and MEX flows to go through Netskope Authentication Proxy:
$dom = " customerfeddomain.com"
$LogOnUrl = "https://aproxy.inskope.com/lnzHsLZa90xma60bkw05/1000/adfs/ls/"
$LogOffUrl = "https://aproxy.inskope.com/lnzHsLZa90xma60bkw05/1000/adfs/ls/"
$mex = "https://aproxy.inskope.com/lnzHsLZa90xma60bkw05/1000/adfs/services/trust/mex"
$ActiveSO = "https://aproxy.inskope.com/lnzHsLZa90xma60bkw05/1000/adfs/services/trust/2005/usernamemixed"
Set-MsolDomainFederationSettings –DomainName $dom -PassiveLogOnUri $LogOnUrl -LogOffUri $LogOffUrl -MetadataExchangeUri $mex -ActiveLogOnUri $ActiveSO
Set Up Best Practices
The following table describes additional setting you can configure:
Best Practice | Description |
|---|---|
Add your ADFS domains as a custom app definition | This will make it easier to identify the app mapping and allow Netskope to track log in events. Define your custom apps by clicking Settings > Security Cloud Platform > App Definition. |
Bypass + Tunnel setting for directing special app traffic | If you have the Netskope client installed but you still want to steer traffic from the endpoint to the Netskope proxy, select Bypass + Tunnel for Certificate Pinned apps. For example, go to Settings > Security Cloud Platform > Steering Configuration and select that steering configuration. Click on Exceptions, and then click Add Exception > Certificate-Pinned Apps, and then select the Bypass action + Tunnel mode for the appropriate platforms. In addition, you should add the appropriate domains: |