Threat Protection
Modern threats need a multi-layered security approach able to defend organizations from known threats and zero-days with the same level of efficacy. Netskope has built a comprehensive threat protection framework that allows organizations to defend against malware through different engines. The Standard Threat engines support:
Signature-Based Antivirus (AV)
Web IPS
Command and Control (C2 or C&C) detection
Machine learning-based detection and real-time blocking for Portable Executable malware as well as phishing sites and domains.
The Advanced Threat engines support:
Machine learning-based detection and real-time blocking for Microsoft Office files.
Advanced Heuristics Analysis
Cloud Sandboxing
While Signature-Based AV, IPS, DNS, callbacks, and threat intelligence indicators can detect and block malware in real time with Netskope fast scan, the Advanced Heuristics and Sandboxing engines require more time to analyze samples with deep scan. A malware detected by the deep scan engine can't be blocked at the first occurrence. However, its hashes and convicted URLs /domains are shared globally in the Netskope Cloud to block inline:
Within 1 hour for customers with the Advanced Threat Protection license.
Within 24 hours for customers with the Standard Threat Protection license.
The following architecture diagram illustrates how Netskope Threat Protection detects malware for your organization:
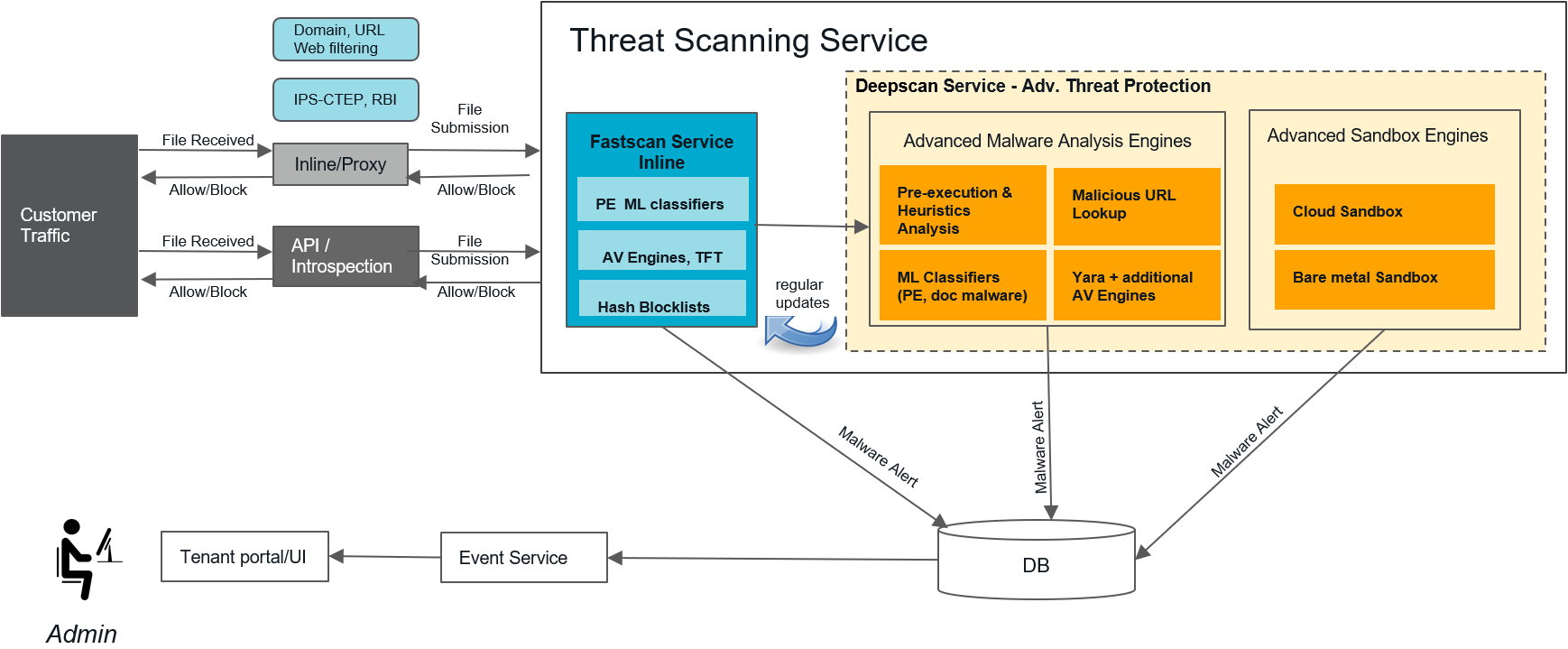
You can integrate external intelligence into Netskope’s threat protection engines with malicious hashes, domains, or URLs using Threat Exchange.
Standard Versus Advanced Threat Protection
The table below breaks down the differences between the Standard and Advanced Threat Protection features:
Feature | Standard Threat Protection | Advanced Threat Protection |
|---|---|---|
Perform real-time ML-based scanning for portable executable files, phishing sites and domains, and prevent patient zero threats. | X | X |
Leverage advanced threat engines, such as Cloud Sandbox, to corroborate AV and ML detections. | X | X |
Perform real-time ML-based scanning and blocking for Microsoft Office files. | X | |
Analyze files undetected by AV or ML in advanced threat engines. Netskope supports 30+ file types, including Portable Executables (e.g., .exe), Microsoft Office, PDF files, batch files, archive files (e.g., zip, 7z, tar), Microsoft Visio, RTF, Flash, HTML, and Java Applets. | X | |
View Sandbox reports, detailed forensics, MITRE ATT&CK mapping, and advanced heuristic analysis. | X | |
Submit files to the Cloud Sandbox via Sandbox API. | X | |
Use file hashes to query detections via RetroHunt API. | X | |
Receive patient zero alerts for newly discovered advanced threat detections. | X | |
Prevent patient zero events by creating policies to only release the file if the advanced threat engines determine it's benign. | X |
Threat Protection for Cloud Storage Apps
As organizations move to the cloud, they are increasingly susceptible to modern day threats like malware and ransomware. One of the initial transitions to the cloud for organizations is in the cloud storage category, with a number of them using SaaS apps such as Microsoft OneDrive for Business, Google Drive, Box, Dropbox, etc. Files get into these cloud storage apps in a number of ways, like through third-party vendors, attachments saved from emails, and files uploaded from desktops. Not all files get scanned by endpoint systems. Netskope provides threat protection for files stored in enterprise-managed applications in the cloud storage category.
When a malicious file is found in a SaaS app, you have three choices based on severity: send a Skope IT alert, quarantine the file, or apply a malware remediation profile to a policy. With quarantine, Netskope uses the quarantine profile in Settings > Threat Protection > API-enabled Protection as the quarantine folder and tombstone. The malicious file is zipped and protected with a password to prevent users from inadvertently downloading the file. Netskope then notifies the admin specified in the profile. The quarantine option is only available for introspection mode. You can enable it in Settings > API-enabled Protection by selecting Malware, API Data Protection, and Quarantine for your instance.
With Standard Threat Protection, you scan your organization for malware, and with Advanced Threat Protection, you can scan for ransomware. However, if you don't have the Advanced Threat Protection license enabled, you can use threat protection with Real-time Protection and API Data Protection policies to detect files with malware as well as Risk Insights to detect malicious sites.
Netskope Security Check
To verify if your Threat Protection policies are working properly and to see some examples of alerts go through the Netskope cloud, you can run tests with the Netskope Security Check.