New Features And Enhancements In Release 96.0.0
Here is the list of the new features and enhancements.
Pivot Rank Field For Ranked Dimension
In this release, Netskope updates the Pivot Rank Limit field to limit the top X number of ranked dimensions. This field also allows the user to drill down on a pivot ranked dimension.
User Behavior Analytics (UBA) Custom Sequential Rule Enhancements
Netskope enhances Advanced UBA custom sequential rules with risky countries filter selection. The predefined risky countries policy is updated with IP-based exception (for trusted IPs or VPNs) from the same country.
SlideShare Activity Update
With this release, Netskope removes Share from the application activity list.
Forward Message Activity Rename
With this release, Netskope changes Google Group forward message activity from Post to Send.
App Suite Membership
Netskope updates the App Suite List to include the following Real-Time Policy Enforcement:
Adobe
Amazon Web Services
Atlassian
Microsoft Office 365 (GCC)
Google Suite
Microsoft Office 365
Yahoo
Zoho
Google Meet Connector Enhancement
Netskope adds a new connector for the Google Meet application that allows to use policies and supports the following activities:
Create
Join
Record
Post with DLP support
Share
Joining, Posting and Sharing of content without logging into Google account displays instance ID as Unauthenticated.
Data Loss Prevention (DLP) Support For Dropbox Files
Uploading files larger than 4MB in Dropbox app is now subject to DLP and threat inspection.
Enhanced File Detection
Netskope adds new file type and intuitive workflow for granular selection of file types, categories, and so on with enhanced detection.
SuccessFactors Connector Enhancement
Netskope supports Send and Move activities for the SuccessFactors application. Now along with moving forms and sending feedback emails, you can configure policies in real-time based on Move and Send activities.
DLP Support For Vimeo Comments
Netskope supports DLP for comments posted on public and user created videos in Vimeo.
DLP Support For SharePoint
With this release, larger files uploaded to SharePoint application is subjected to DLP and threat inspection except for files uploaded from Yammer and MS Planner. Some navigations getting multiple hits intermittently will be fixed in future releases.
Application Category Modifications
With this release, Netskope updates application category for:
Vimeo app from Consume to Content Management.
HelloSign app from Collaboration to Business Process Management.
Renamed Google Workspace
Google Workspace is now renamed to Google Accounts that governs login to all Google apps and services including Google Cloud Platform (GCP).
Seamless Policy Update
In this release, Netskope updates NPA configuration and policy which is seamlessly learned by NS Client and does not require the Client to reconnect. This enhancement is available on Windows and OS X platforms.
Hardware Device ID Support
Netskope supports duplicate hardware device ID when the Client is installed in per user mode.
Google Cloud Platform (GCP) Center for Internet Security (CIS) Profile v1.3.0
In this release, Netskope adds CIS Google Cloud Platform Foundation Benchmark v1.3.0 as part of Security Posture predefined profiles.
Azure Center for Internet Security (CIS) Profile v1.4.0
In this release, Netskope adds CIS Microsoft Azure Foundations Benchmark v1.4.0 as part of Security Posture predefined profiles.
File Type Feature Enhancement
With this release, file type capability in the Real-time Protection policy provides granular file and file category selection. In addition, detection was improved by using true file types. The file size is limited to 1.99 GB and will be expanded in the future.
New HTTP Methods
HTTP Header Profile supports the following HTTP methods defined in the Web-based Distributed Authoring and Versioning (WebDAV) extension:
move
copy
mkcol
propfind
propmatch
lock
unlock
Isolate Action Type For Filter Query
The enhanced presentation and filtering features in Skope IT > Page Events allows to identify and filter Page Events by Action. This enables to easily identify the pages sent to Netskope RBI for web isolation and filter them with the help of column Action:isolate.
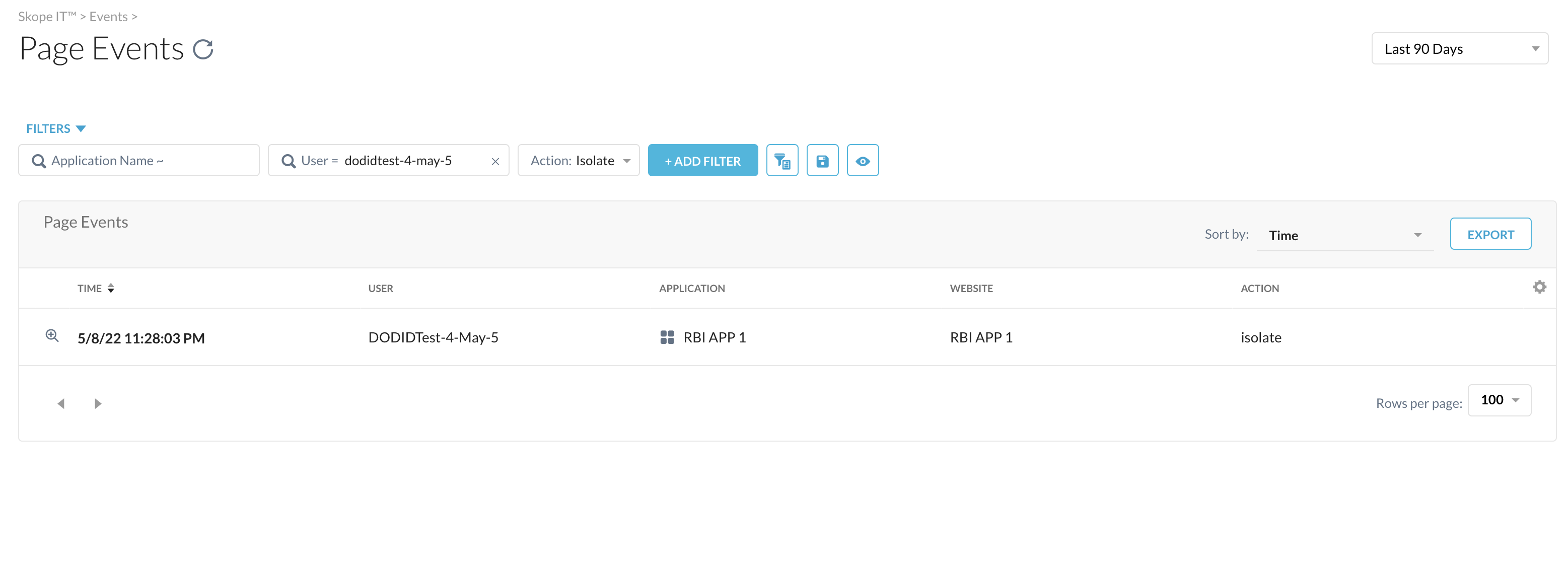 |
You can also click on the filter icon to apply the filter.
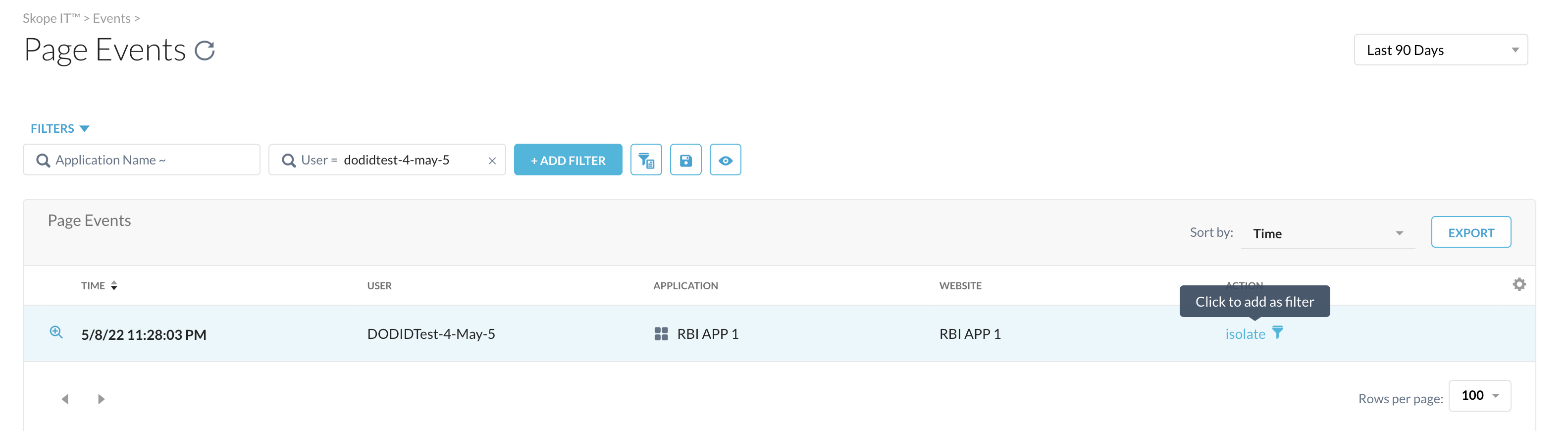 |
The advanced search capability is enhanced to suggest Action:isolate while building the query to filter Page Events.
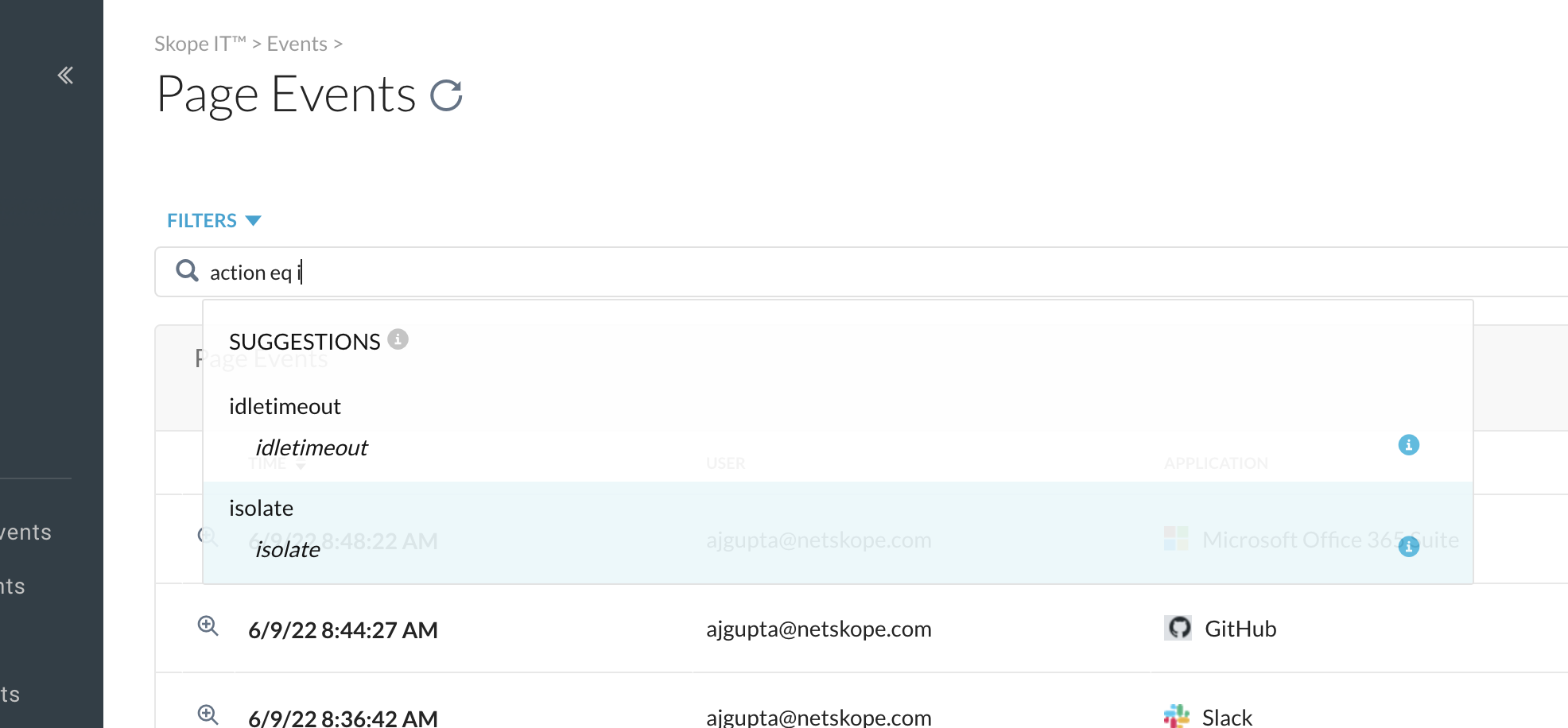 |
Enhanced Malicious Site Searching
On the Malicious Sites page, you now can search for a specific malicious site by domain name or URL. Also, the Site column was renamed to Threat Match Value.
To learn more: About Malicious Sites.
Policyless CTEP/Web IPS Configuration Experience
Netskope simplified the Client Traffic Exploit Protection (CTEP) configuration by making it a policyless experience. On the CTEP Settings page, you now can enable or disable CTEP as well as create a list of exceptions. You cannot create or edit CTEP policies in real-time protection policies. You must disable or delete any existing CTEP policies for the policyless configuration to take effect.
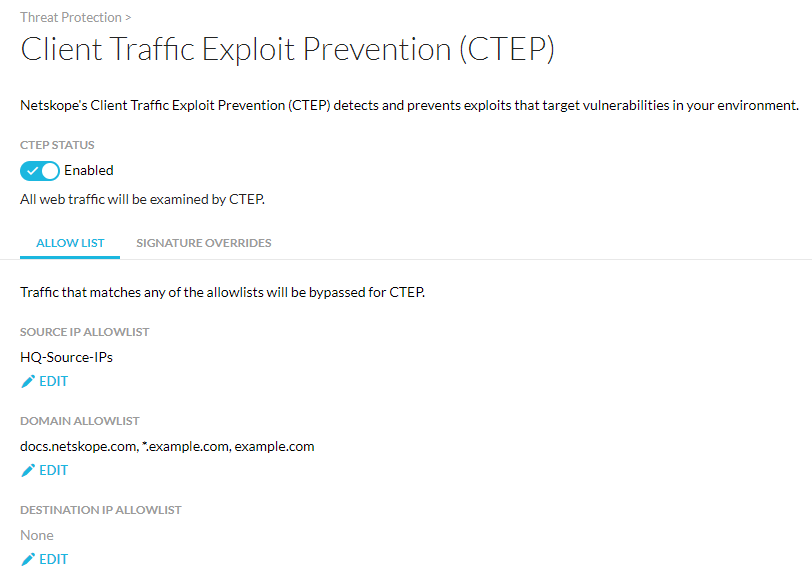 |
To learn more: About IPS Settings.
Certificate Pinned Application Management
Netskope introduces a new Certificate Pinned Apps tab under App Definitions that improve the admin workflow when creating and managing certificate pinned applications. Admins can create a new certificate pinned app as well as edit and delete the custom certificate pinned apps.
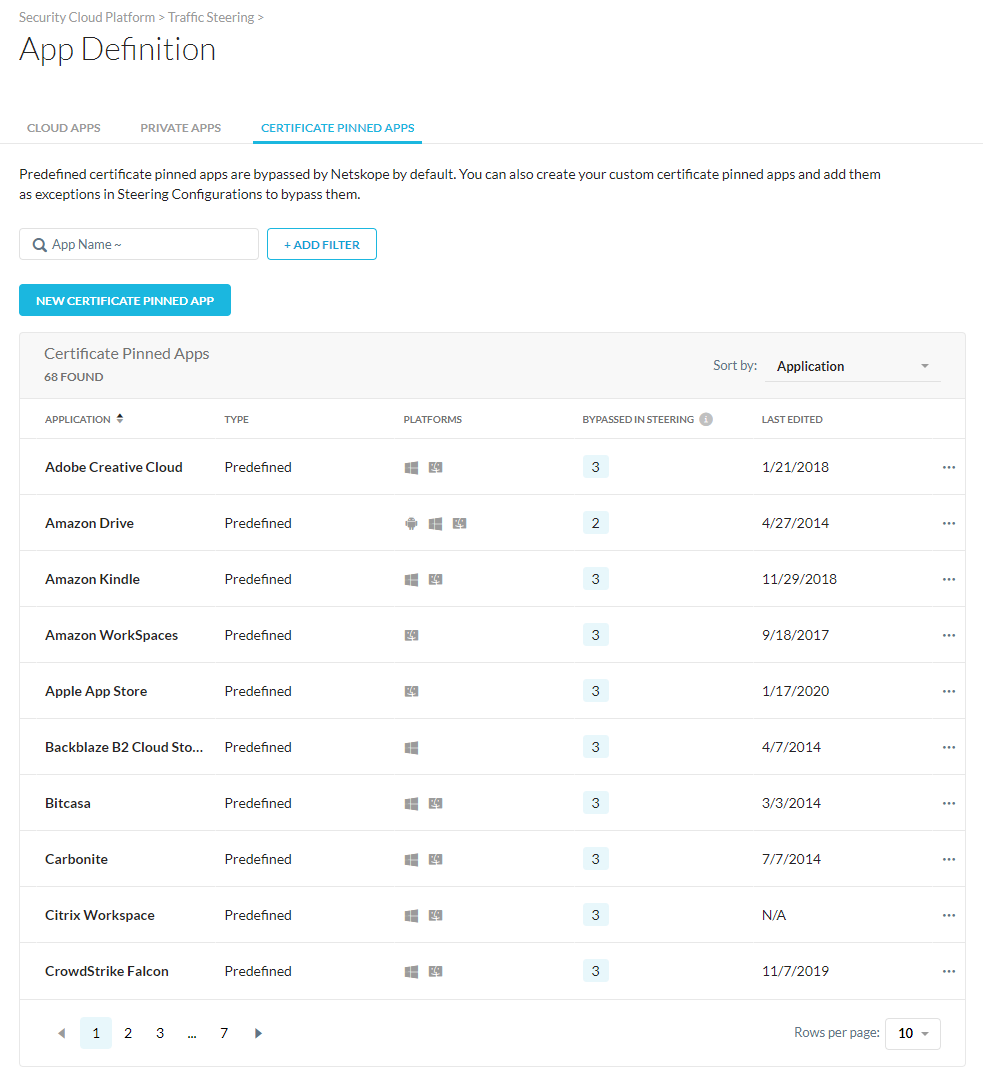 |
To learn more: Certificate Pinned Applications.
macOS Performance Improvement
With this release, the enableMacPerformance feature flag can be enabled on macOS Netskope Client to improve performance significantly. This flag is enabled by default and the Client uses VIF on macOS as part of this improvement.
Note
To disable this flag, contact your Sales Representative or Netskope Support.
While working on this enhancement “enableMacPerformance”, Netskope observed an interoperability issue with Cisco Anyconnect in full-tunnel mode. To address the same, when the Client tunnel is established, a probe process starts within three seconds to detect AnyConnect full tunnel mode. The Client switches to lwip (method prior to enableMacPerformance flag) if the probe is unsuccessful and generates a “tunnel down due to error” event. If this occurs, the Client might disconnect and reconnect intermittently for 10-20 seconds. As a workaround, Netskope recommends adding the macOS Client VIF IP range (100.127.100.0/24) to Cisco AnyConnect split tunnel exclusion range. To learn more on AnyConnect interop, Cisco AnyConnect
Important
This behavior change exists only for macOS devices.
Linux Device Classification Support
Netskope implemented Linux Device classification on Netskope Cloud.
 |
To learn more: Device Classification for Linux.
Note
This is currently a beta feature. Contact your Sales Representative or Netskope Support for more information.
IKEv1 Support Deprecated for IPSec Tunnels
Netskope no longer supports Internet Key Exchange (IKEv1). Any IKEv1 messages will be explicitly blocked and tunnel creation will fail.
In addition to documenting all new and improved features, here is the list of articles with key documentation updates:
Adding Exceptions: Improved the content and structure of the steering configuration exceptions.
Creating a Custom Certificate Pinned Application: New article on how to create custom certificate pinned apps.
Added issue number: 165382 in the release 95.0.0 Fixed Issues.