VMware Carbon Black
VMware Carbon Black (CB) is a cloud-native endpoint and workload protection platform (EPP and CWP) that monitors and protects all files in your network from malicious threats or attacks.
This document contains the best practices to ensure smooth interoperability between VMware Carbon Black and the Netskope Client.
Environment
This document was created using the following components:
VMware Carbon Black Sensor Version: 3.8.0.398
Netskope Client: 92.0.1.940
OS: Windows 10
Specific configurations in VMware Carbon Black and Netskope tenant web UI can ensure that the processes or traffic from either of the applications are not blocked and directed to the Netskope Cloud.
Configurations In VMware Carbon Black
To allow the Netskope Client to operate seamlessly, add specific rules while creating policies in the CB console. The policies are a set of rules that control the CB sensor behavior and allow the smooth functioning of the Netskope Client.
To add rules in the policies, login to the CB console and specify Netskope Client specific processes in the Enforce > Policies > Prevention tab while creating a policy and do the following steps:
Set Permission Policy Rules: To allow or block according to the specified process paths.
Upload Paths: To allow or deny uploads from a specific path by the deployed sensors.
Set Permission Policy Rules
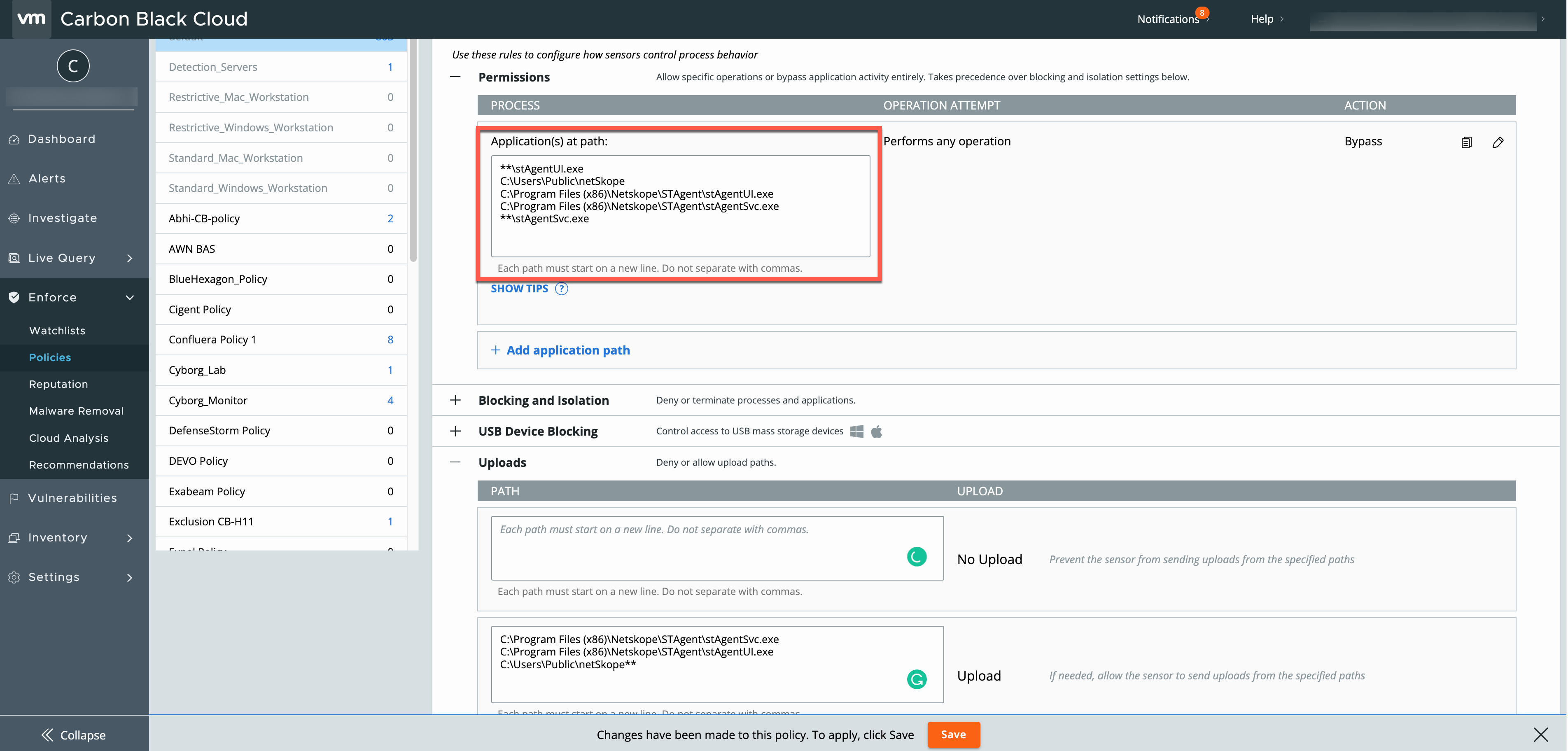
Add the following process in Prevention > Permission > Process > Application(s) at path to allow processes from the Netskope Client:
**\stAgentUI.exe
C:\Users\Public\netSkope
C:\Program Files (x86)\Netskope\STAgent\stAgentUI.exe
C:\Program Files (x86)\Netskope\STAgent\stAgentSvc.exe
**\stAgentSvc.exe
 |
Upload Paths
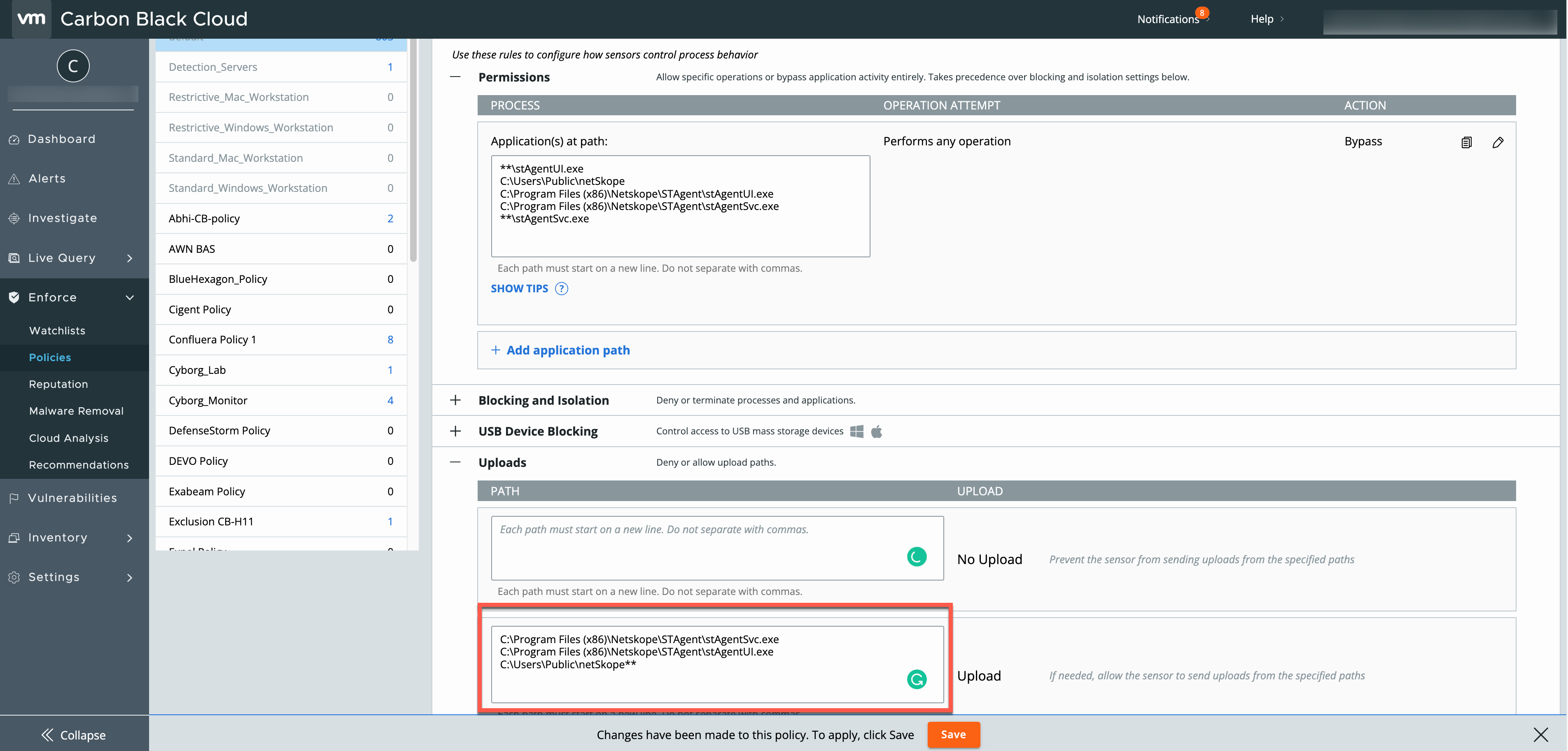
Add the following Netskope Client specific processes in Prevention > Uploads > PATH > Upload:
C:\Program Files (x86)\Netskope\STAgent\stAgentSvc.exe
C:\Program Files (x86)\Netskope\STAgent\stAgentUI.exe
C:\Users\Public\netSkope**
 |
Configurations In Netskope Client
Add exceptions (Certificate Pinned Application exception type) on the Netskope tenant Web UI to:
Allow the Carbon Black traffic to bypass Netskope and reach its destination.
Avoid Netskope Client interruption in the CB traffic and its processes. You must add exceptions to the Netskope Steering Configuration. To learn more, view Adding Exceptions.
To add CB as a Certificate Pinned Application on the Netskope UI:
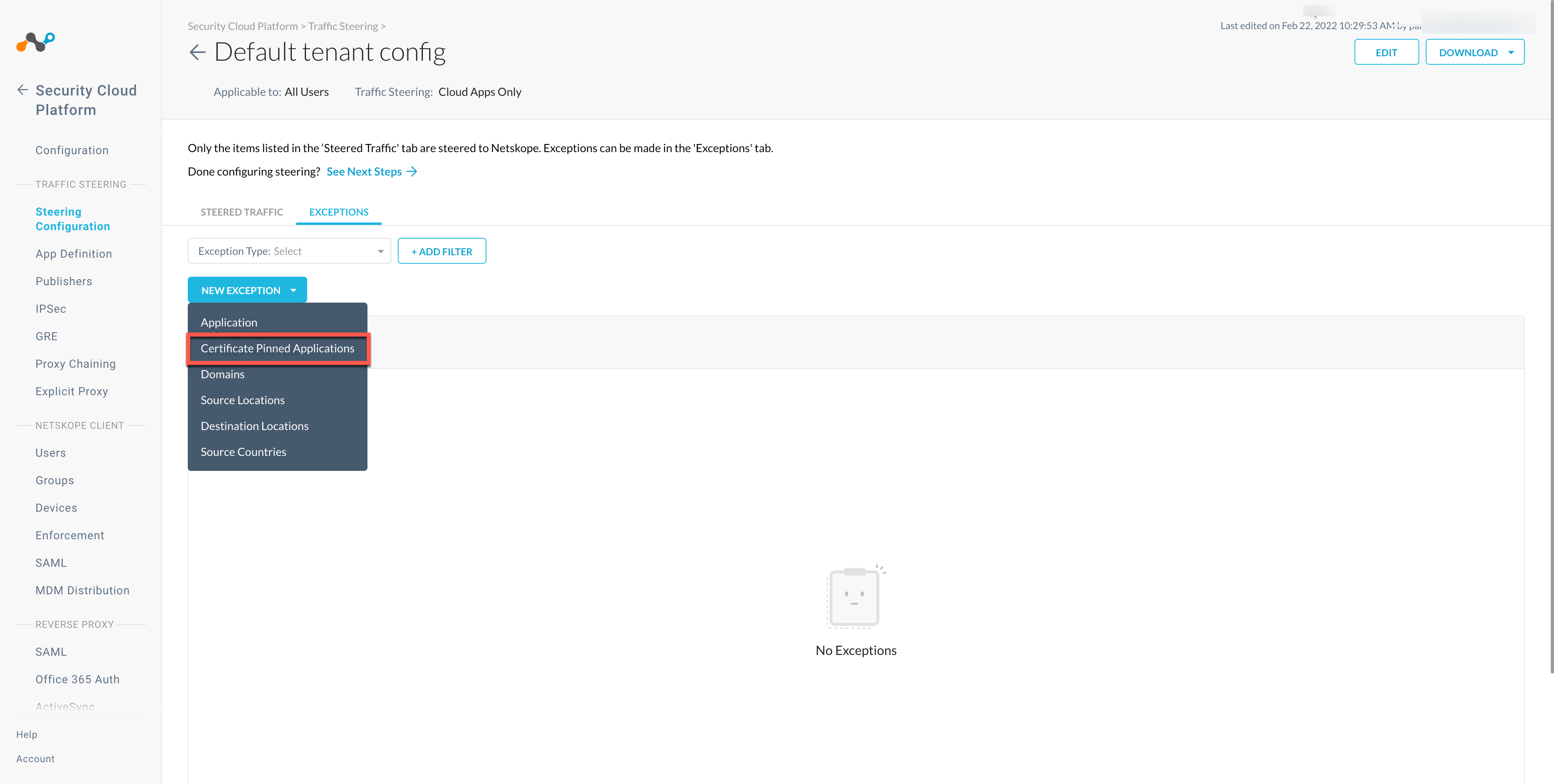
Go to Settings > Security Cloud Platform > Steering Configuration and select a configuration.
On the configuration page, click EXCEPTIONS > NEW EXCEPTION > Certificate Pinned Applications.
In the New Exception window, do the following:
From Certificate Pinned App, select the application. To add a new certificate pinned application in the New Certificate Pinned Application window, do the following:
Application Name: Enter the name of the application.
Platform: Select the operating system where the application is managed.
Definition: Provide the processes and .exe(s) list that you want to bypass. To learn more about the .exe(s) excluded, view Exclusion List.
From Custom App Domains, add the URLs that you want to exclude. To learn more about the exclusions for the Carbon Black Cloud sensor, view Allow URLs.
From Actions, select Bypass for all operating systems that you want to allow directly to the destination.
Click ADD.
Netskope Client Features
Refer to the list of validated use cases to verify Client operations.
VMware Carbon Black Features
To verify if CB features function smoothly:
Ensure that an infected file is detected by CB (optional).
View the Alert on the CB management console.