Executive Dashboard in Netskope IoT Security
Executive dashboard sums up the security, networking and IT devices' health on the screen.
Security Operations
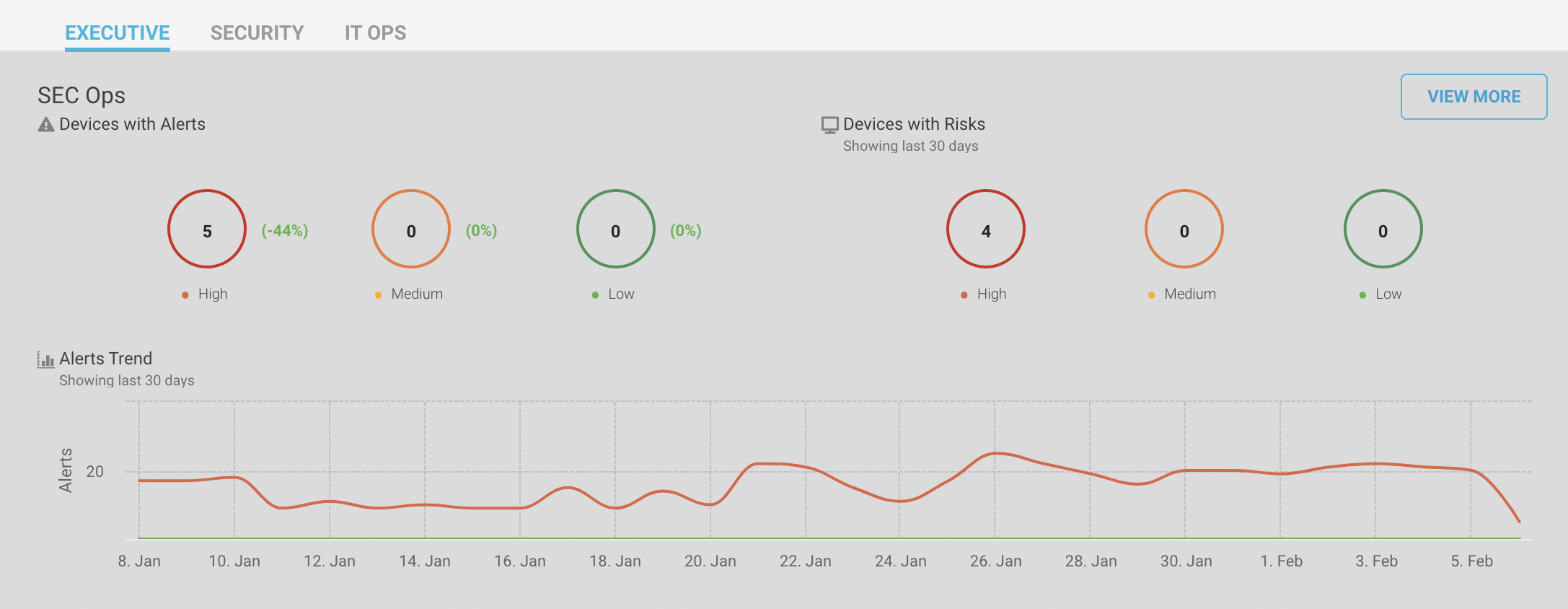 |
Devices by alerts: Alerts are notifications or warnings for applications running on the machine. The chart shows the number of devices with high/medium/low severity alerts for the last 30 days. It also shows the increase and decrease of devices in that severity in percentage. For example, 31 devices had the highest number of high severity alerts and 3% improvement in the alerts.
Devices by risks: Risk is the possibility of threat in the environment like using a malicious software. The chart shows the number of devices with high/medium/low severity risk for the last 30 days. For example, 32 devices showed the high severity risks in the last 30 days.
Alert trends: The line chart shows the number of different severity alerts generated for a specific timestamp. For example, on 18 November, statistics report that 206 high severity alerts, 2 medium severity alerts and 0 low severity alerts were generated.
Security dashboard: Click on the “View More” button to navigate to the Security dashboard. You can see the detailed drilled down information of the alerts and risks on your devices.
Risk Assessment: You can see the number of devices with high, medium and low risks in the left pane of the software dashboard. The pie chart shows the distinct threat categories distributed among the number of devices affected by it. The list below the pie chart shows the distinct threat categories with the number of devices in front of it. For example, 34 devices are used by users that perform actions that enable attacks.
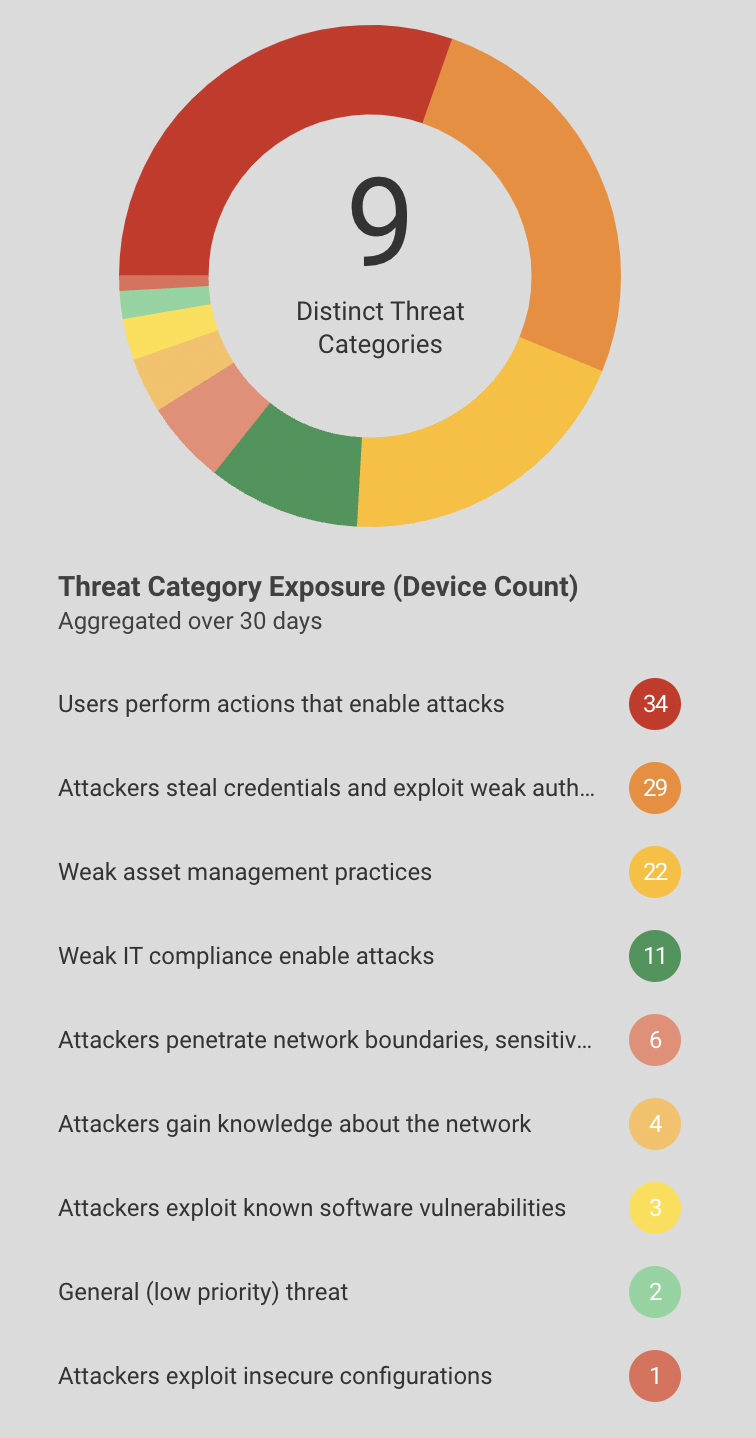
Further, the risks are broken down depending on types of devices like computer, tablets, phones, etc. and tags of the devices like network, personal, etc.
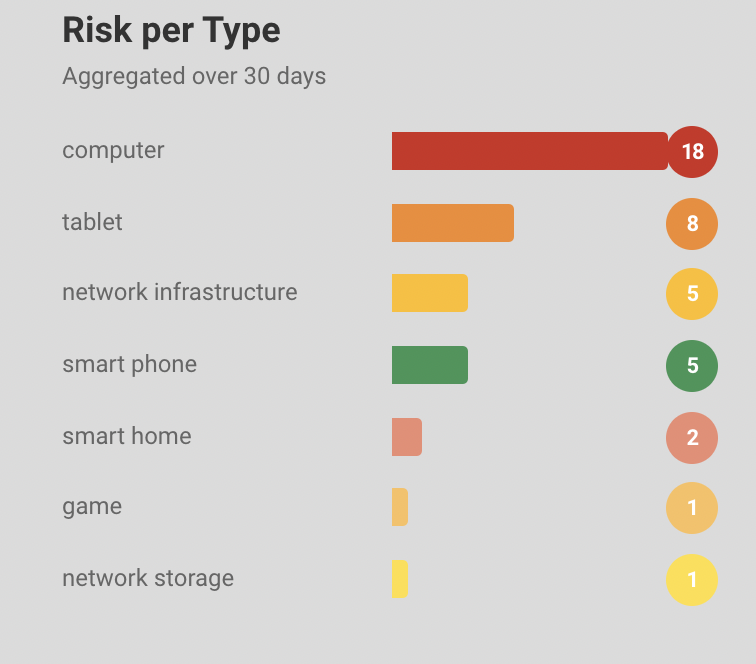
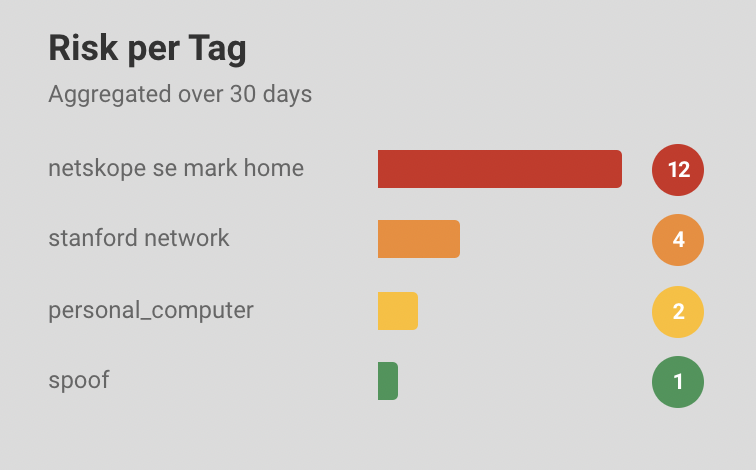
Alert Assessment: You can see the number of devices with high, medium and low alerts in the right pane of the software dashboard. The pie chart shows the distinct alert categories distributed among the number of devices affected by it. The list below the pie chart shows the distinct alert categories with the number of devices in front of it. For example, 10 devices have an ET INFO session traversal alerts.
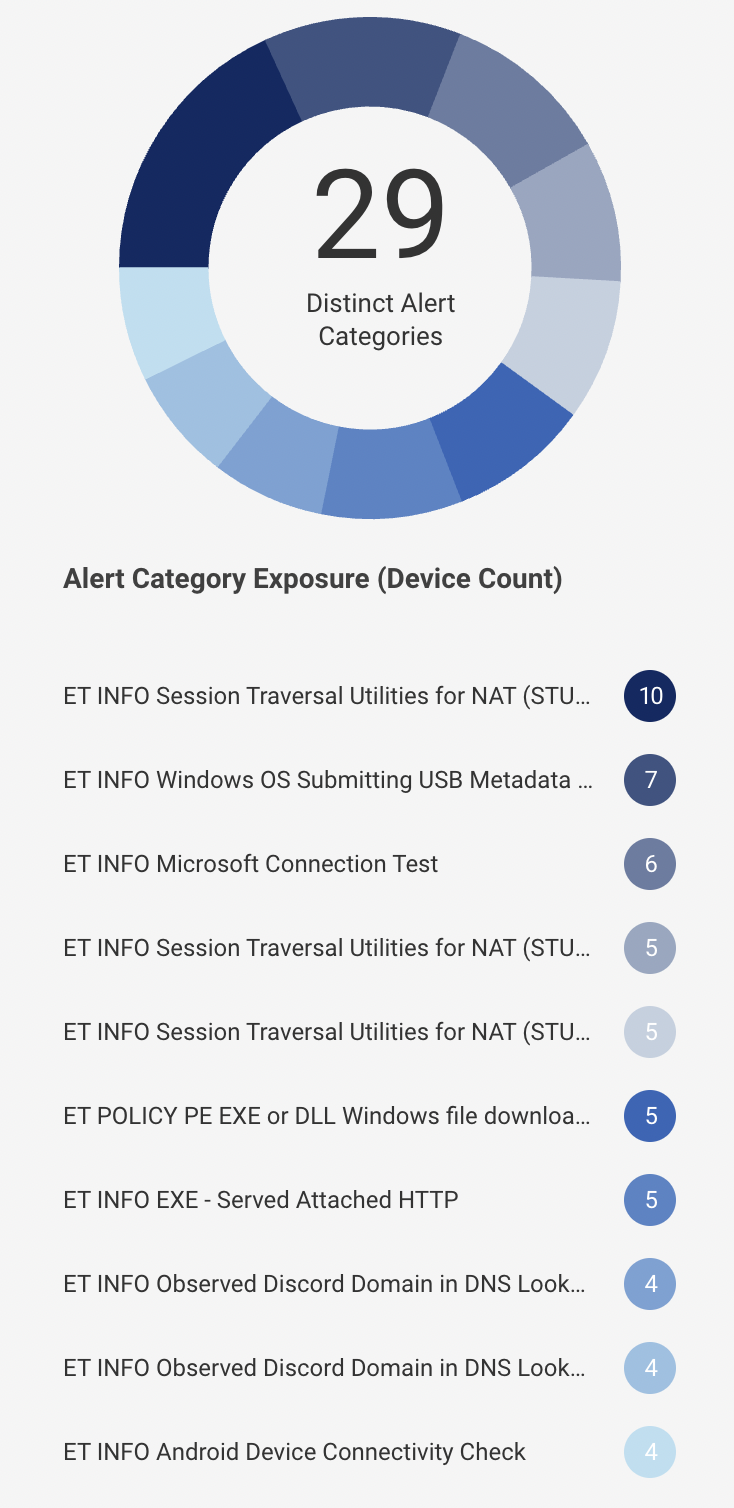
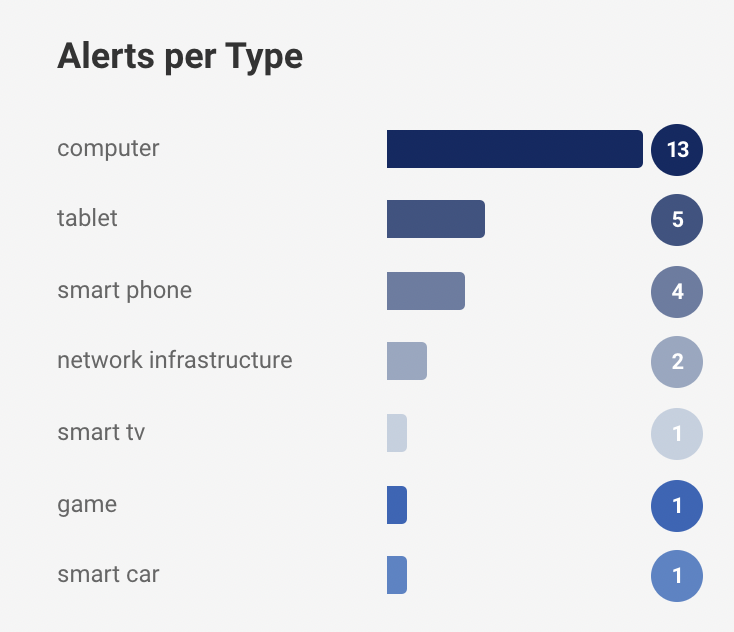
Further, the chart shows the granular alert information depending on types of devices like computer, tablets, phones, etc. and tags of the devices like network, personal, etc.
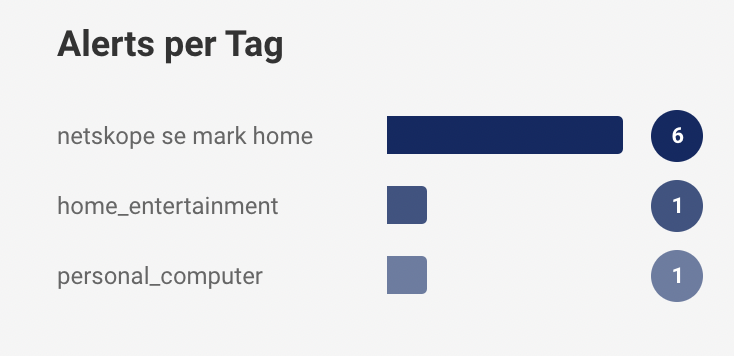
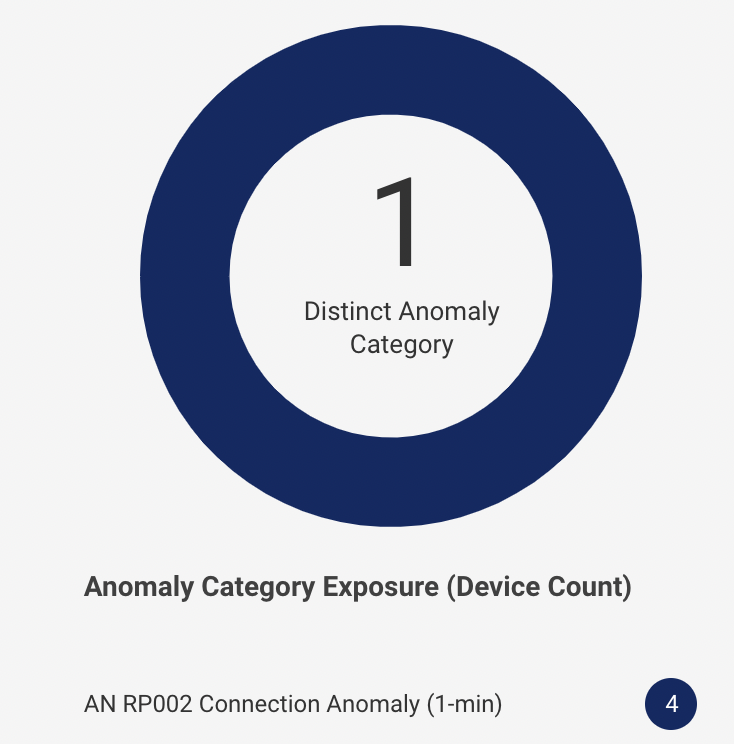
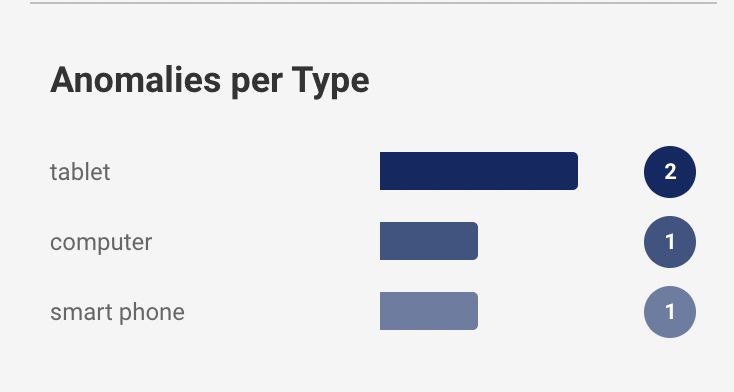
Anomaly Assessment: The pie chart shows the distinct anomaly categories distributed among the number of devices affected by it. The list below the pie chart shows the distinct threat categories with the number of devices in front of it. For example, ‘Connection Anomaly’ detected 4 devices.
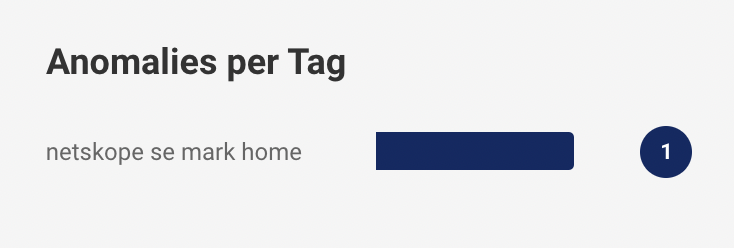
Further, the chart shows the granular information of the anomalies depending on types of devices like computer, tablets, phones, etc. and tags of the devices like network, personal, etc.
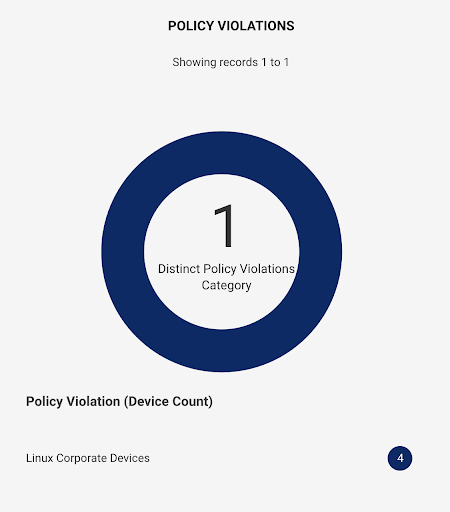
Policy Violation: The pie chart shows the distinct policy violation categories distributed among the number of devices affected by it. The list below the pie chart shows the distinct violation categories with the number of devices in front of it. For example, ‘Linux corporate devices’’ detected 4 devices.
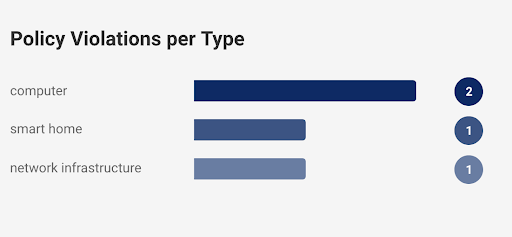
Further, the chart shows the violations depending on types of devices like computer, tablets, phones, etc. and tags of the devices like wootcloud HQ, personal, etc.
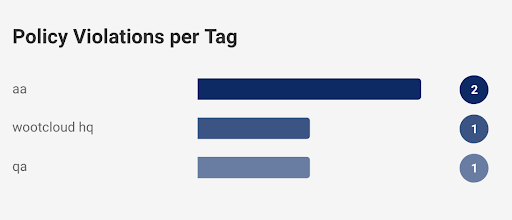
Network Operations
Network ops section shows the network health of the environment. It describes the network distribution of SSIDs and subnets.
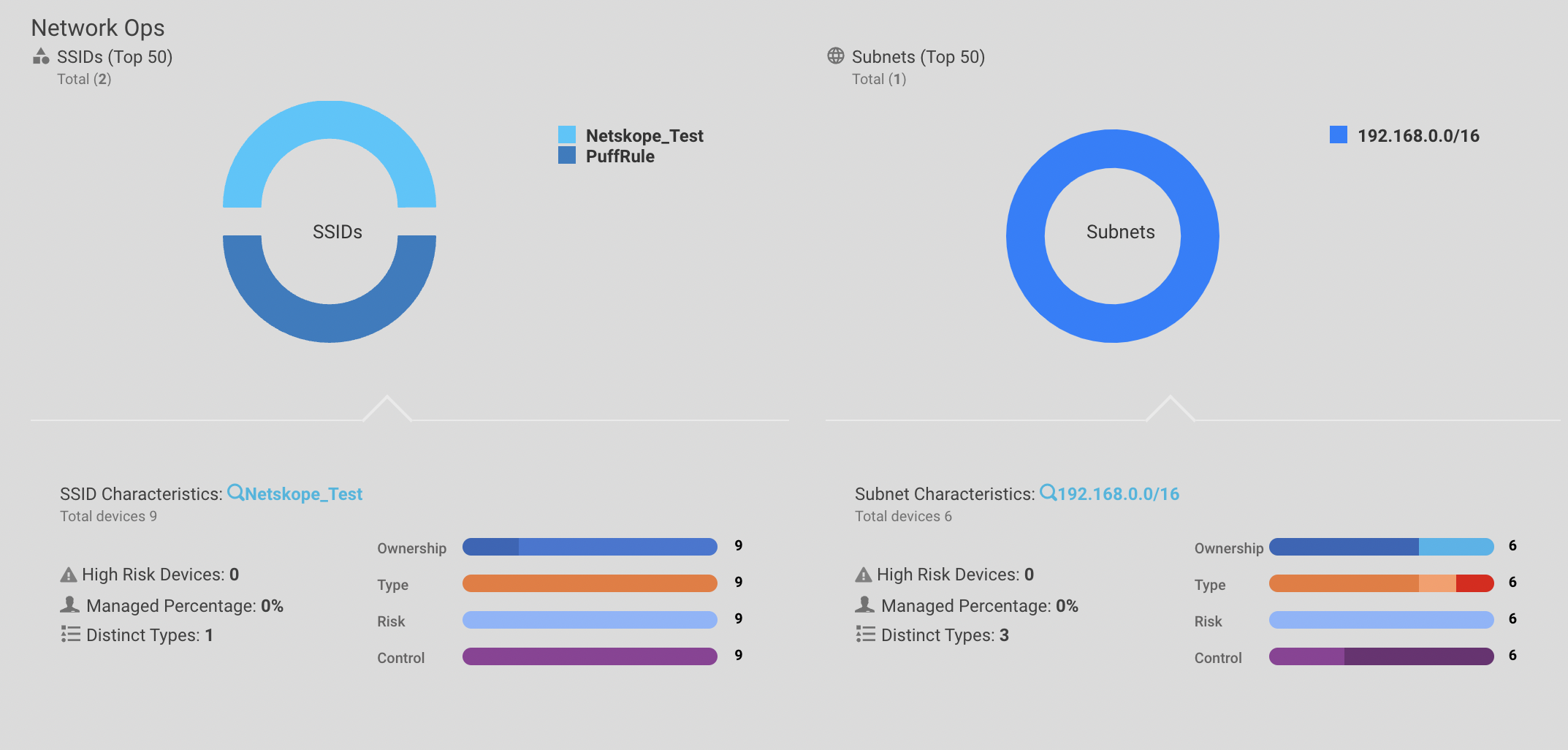 |
SSIDs chart
The chart shows the different SSIDs in the environment and their risk of health.
You can select and deselect the SSID on the right chart point to show or hide the SSID in the chart.
You can see the number of high-risk devices, percentage of managed devices and different types of devices.
You can see the chart with ownership, number of each type of device, risk of devices, and control information.
For example, PuffRule SSID has 7 high risk devices, 0 percentage managed devices and 10 distinct types of devices.
Subnets chart
Networks are broken down into subnets and the subnet chart shows the health of these subnet ranges.
You can select and deselect the subnet on the right chart point to show or hide the subnet in the chart.
You can see the number of high-risk devices, percentage of managed devices and different types of devices on the subnet.
You can see the chart with ownership, number of each type of device, risk of devices, and control information.
For example, 192.168.xx.xx/xx subnet has 64 devices, of which 18 devices have high risk, 0 percent of devices are managed and 14 distinct types of devices.
Note
You can hover over the chart to know more. When you select another SSID/Subnet in the chart, the characteristics will eventually update with the device's health.
IT Operations
The IT Ops section shows the health of devices managed in the environment. It checks the device state, compliance, and asset management.
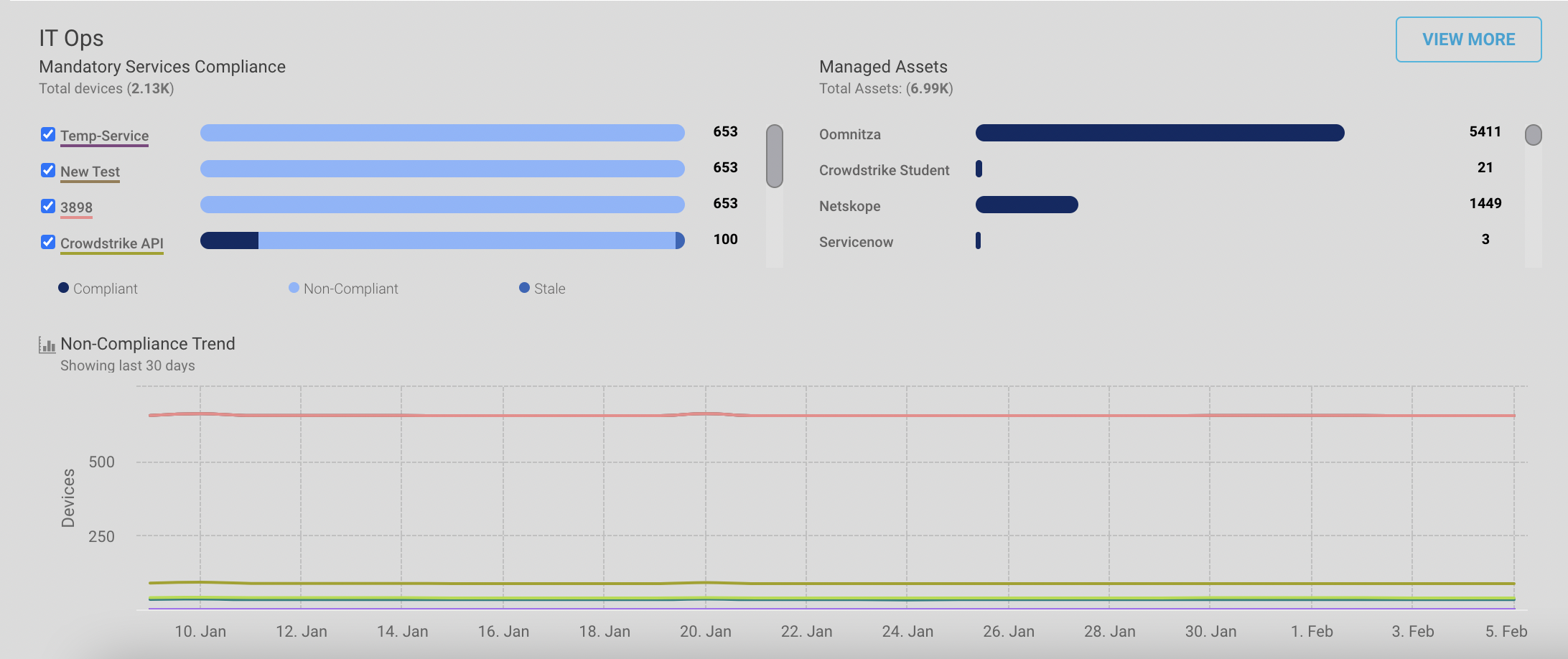 |
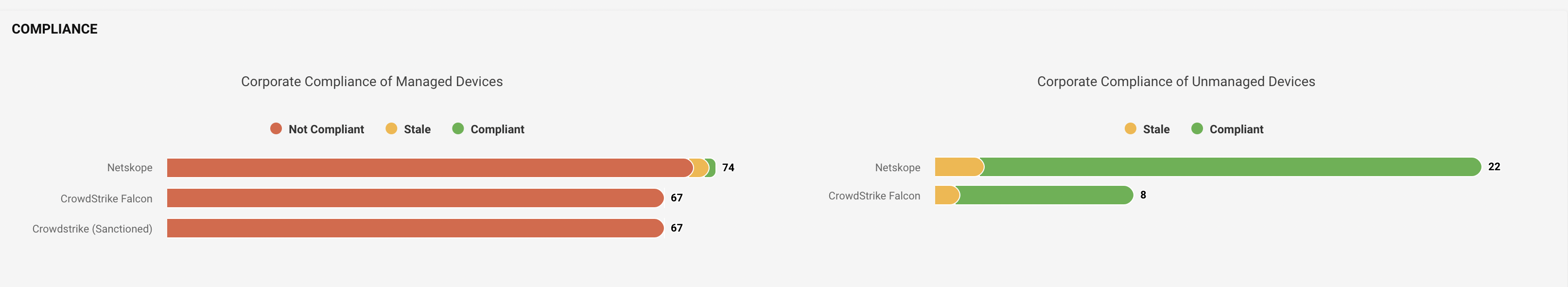
Mandatory Services Compliance
The chart shows the compliance state of asset management systems in the environment with the total number of devices managed by that particular asset management system.
For example, there are three mandatory services implied by the devices in the environment i.e. Netskope, CrowdStrike Falcon, and CrowdStrike (Sanctioned). The “Netskope” service is implied on 74 managed devices, out of which 1 device is compliant, 71 are non-compliant and 2 are stale.
Managed assets
Managed assets show the graph for asset management systems which have managed devices.
For example, the “Netskope” asset management system has 65 managed assets.
Non Compliance trends
The line chart shows the number of devices non-compliant for a specific timestamp.
For example, on 18 November, statistics reported that 72 devices were non-compliant against the “Netskope” service and the 67 devices were non-compliant against “CrowdStrike (Sanctioned)” service.
IT Ops Dashboard - Click on the “View More” button to navigate to the IT Ops dashboard. You can see the detailed drilled down information about asset management systems and compliance postures.
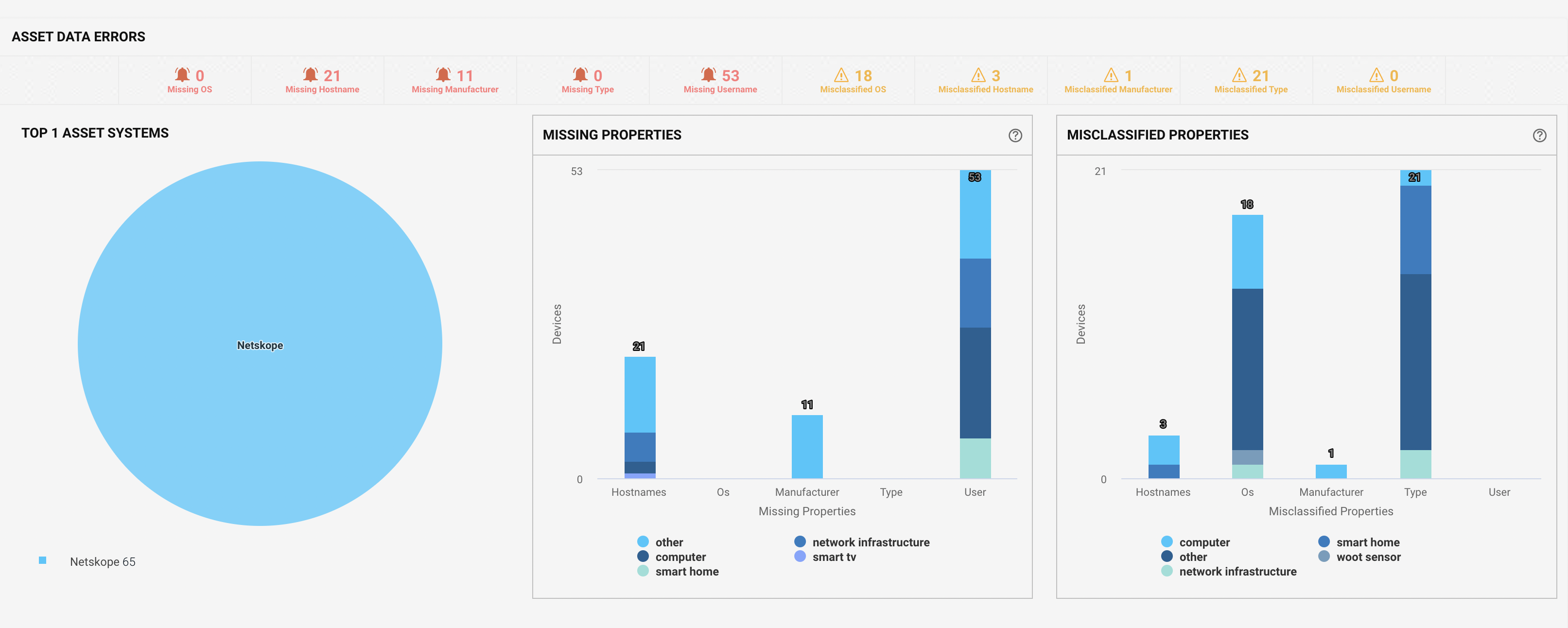
Asset Data Errors: You can see the number of devices with missing or misclassified parameters like OS, host name, manufacturer, type, and username. You can click on the individual notifications to see the detailed information of the device.
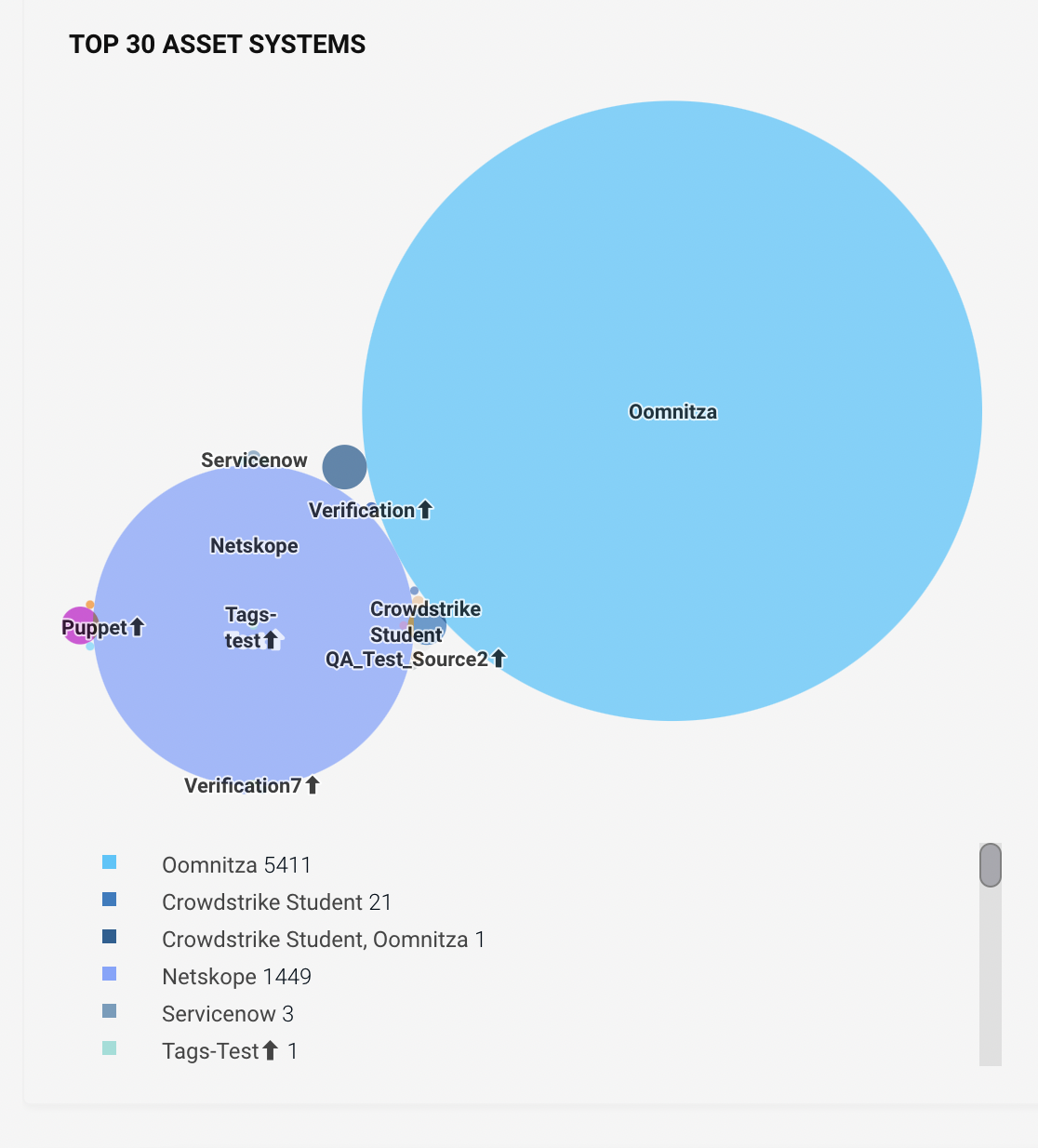
Top Asset Systems: The Venn diagram shows the top asset management systems with the number of devices in each system. Overlapping areas represent how many devices appear in over one system.
Missing parameters: The bar graph shows the number and distinct type of device with the respective missing properties. For example, a total of 21 devices are missing host name parameters, out of which 1 smart TV, 2 computers, 5 network infrastructure and 13 other devices are identified.
Misclassified parameters: The bar graph shows the number and distinct type of device with the respective misclassified or incorrect properties. For example, total 3 devices have misclassified or incorrect host name parameter entry, out of which 2 are computers and 1 is a smart home appliance.
Compliance - the chart shows the compliance state of managed and unmanaged devices in the corporate environment with the total number of devices managed by that asset management system.
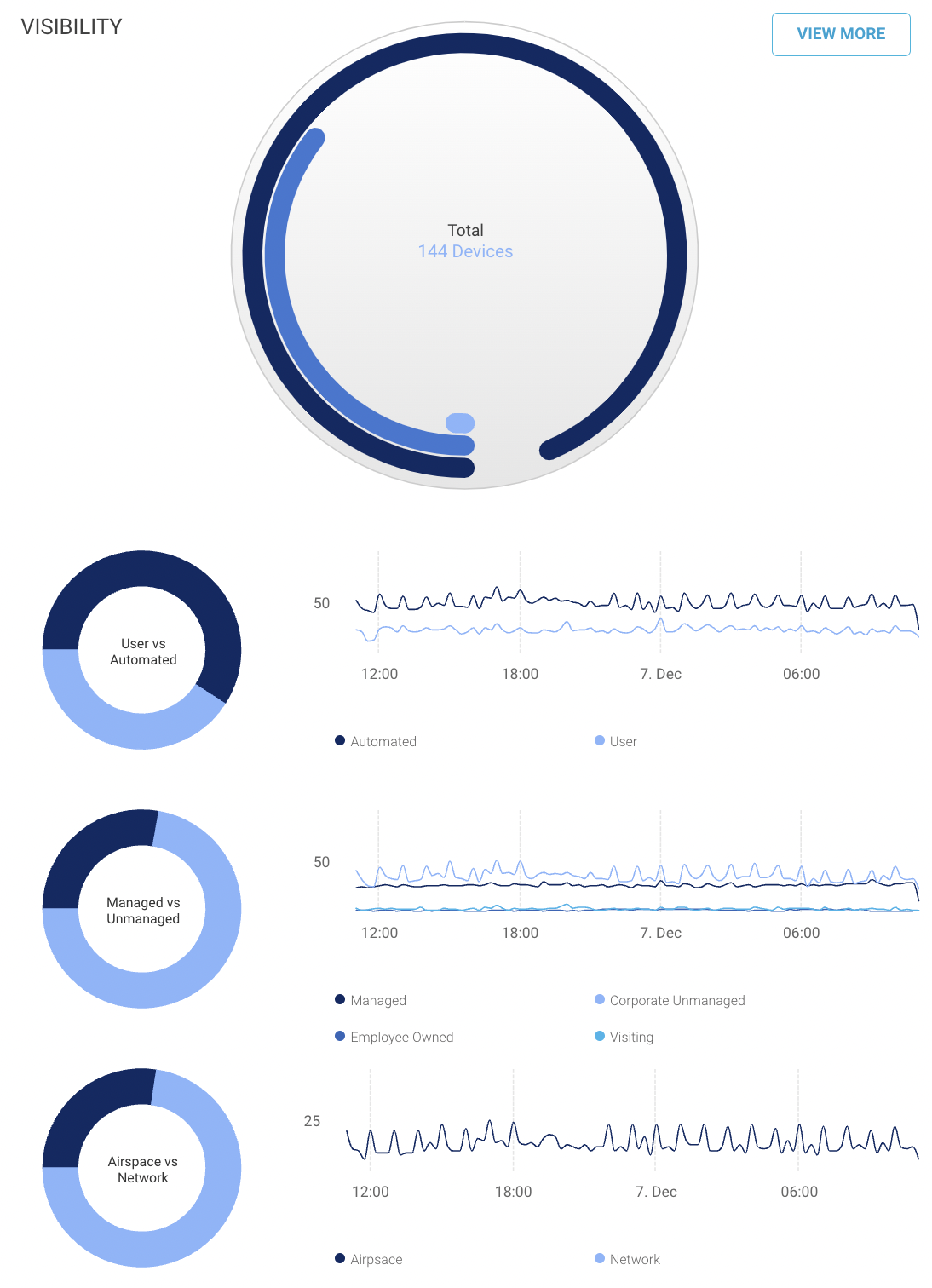
Visibility
The pie chart shows the device data for the last 24 hours, which are connected through Wi-Fi or wired connection in the environment. The algorithm marks the devices as the Wired/Wi-Fi gray section when their connectivity details are unknown if they are connected by Wi-Fi or wired connection.
Note
You can hover over the charts to read more. Navigate the View More option to see the detailed network spectrum
The radial charts are further broken down into:
User vs Automated: the chart shows the percentage of user operated devices like mobiles, laptops, etc. in comparison with automated devices like cameras, sensors, etc. in the environment. The line chart shows the record for the number of devices connected in the last 24 hours with timestamp.
Managed vs Unmanaged: the chart shows the percentage of managed and unmanaged devices, like computers, printers, cameras, sensors, etc. in the environment. The line chart shows the record for the number of devices connected in the last 24 hours with timestamps which are Managed, Corporate Unmanaged, Employee Owned and Visiting.
Airspace vs Network: the chart shows the percentage of devices connected by wireless media compared to devices connected by a wired network in the environment. The line chart shows the record for the number of devices connected in the last 24 hours with timestamps.
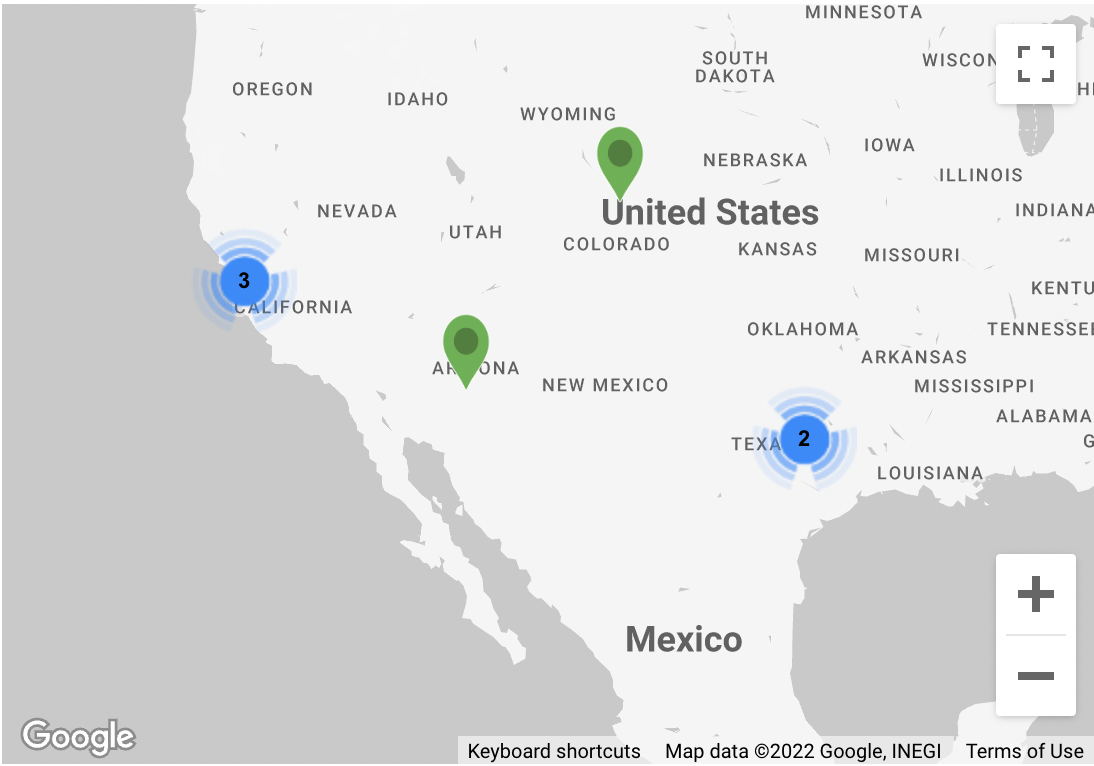
Maps
In the right bottom of the Executive dashboard, the google map shows the sites selected to view the data in the user interface. You can select a particular region or site on the map to view particular site data.
 |