Trend Micro Maximum Security
Trend Micro Maximum Security provides comprehensive protection against ransomware, identity theft, malware issues, and so on, thereby securing your data from attacks and threats.
This document contains the best practices that ensure smooth interoperability between Trend Micro Maximum Security and Netskope Client.
Environment
This document was created using the following components:
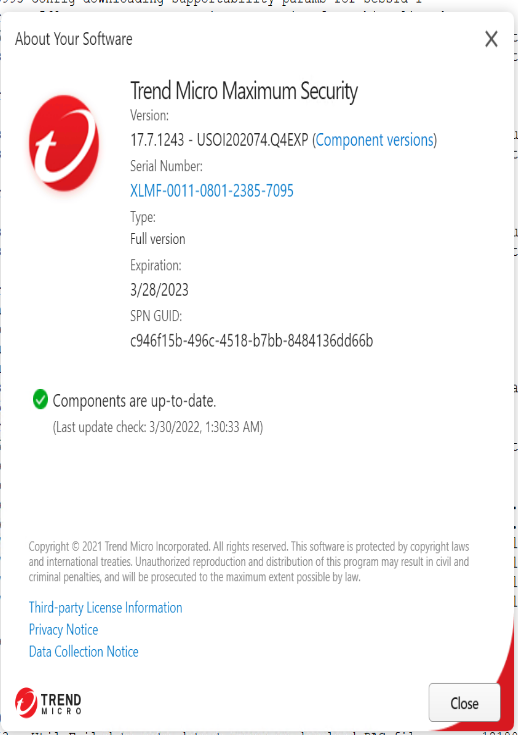
Trend Micro Maximum Security Version: 17.7.1243 - USOI202074.Q4EXP
Netskope Client version: 94.0.0.2359
OS: Windows 10
Specific configurations in Netskope tenant web UI can ensure that the processes or traffic from either of the applications are not blocked and directed to the Netskope Cloud. You must add exceptions to the Netskope Steering Configuration. To learn more, view Adding Exceptions.
Configurations In Netskope Client
Add steering configuration exceptions (Certificate Pinned Application exception type) on the Netskope tenant WebUI to allow Trend Micro traffic to bypass Netskope and reach its destination.
To add Trend Micro as a Certificate Pinned Application on the Netskope UI:
Go to Settings > Security Cloud Platform > Steering Configuration and select a configuration.
On the configuration page, click EXCEPTIONS > NEW EXCEPTION > Certificate Pinned Applications.
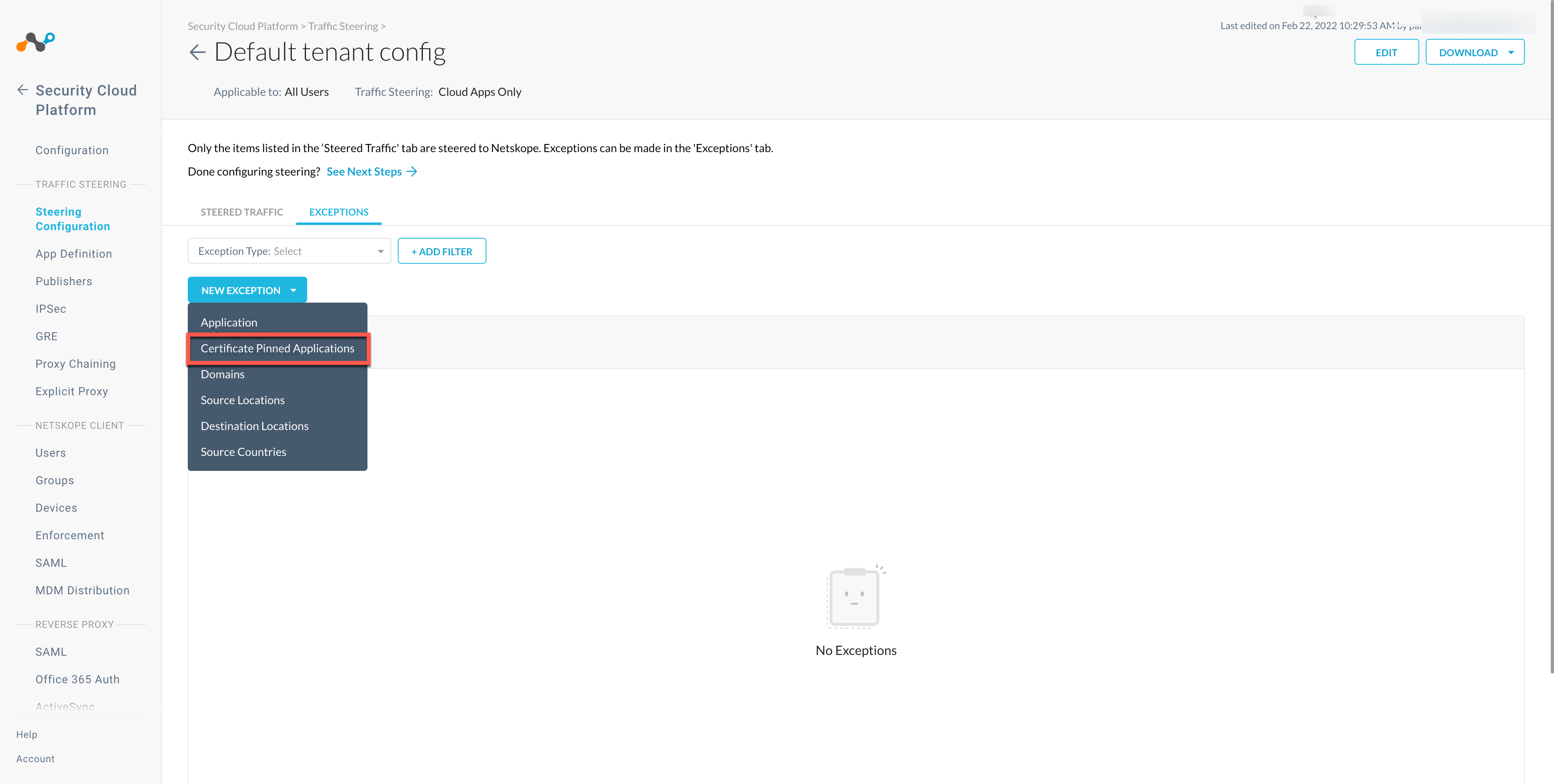
In the New Exception window, do the following:
From Certificate Pinned App, select the application. To add a new certificate pinned application in the New Certificate Pinned Application window, do the following:
Application Name: Enter the name of the application.
Platform: Select the operating system where the application is managed.
Definition: Provide the processes and .exe(s) list that you want to bypass. Here, add the following processes:
TmBrowserProxy.exe
uiWinMgr.exe
PwmConsole.exe
SecureBrowser.exe
uiUpdateTray.exe,
uiWatchDog.exe
coreServiceShell.exe
AMSPTelemetryService.exe
AMSP_LogServer.exe
coreFrameworkHost.exe
utilRollback.exe
TmsaInstance64.exe
DREBoot64.exe
OEMConsole.exe
PackageRemover.exe
Remove.exe
RescueHelper.exe
ShorcutLauncher.exe
SupportTool.exe
TiMiniService.exe
TiPreAU.exe
TiResumeSrv.exe,
TMSToolEx.exe
uiProtectedBrowser.exe
VizorShortCut.exe
WSCTool.exe
CleanerOneChecker.exe
PtLauncher.exe
PtSessionAgent.exe
PtSvcHost.exe
PtWatchDog.exe
TMAS_OL.exe
TMAS_OLImp.exe
TMAS_OLSentry.exe
TmWscSvc.exe
WSCHandler.exe
WSCStatusController.exe
ToolbarNativeMsgHost.exe
PwmSvc.exe
uiSeAgnt.exe
PwmTower.exe
From Custom App Domains, add the URL: trendmicro.co.jp, trendmicro.com that you want to exclude.
From Actions, select Bypass for all operating systems that you want to allow directly to the destination.
Click ADD.
Note
The processes listed from TrendMicro Maximum security (Home edition), may vary in the TrendMicro enterprise edition.
These processes are used by the TrendMicro client. For specific use cases, all these may not be required to be bypassed.
Netskope Client Functions
Refer to the list of validated use cases that you can use to verify Client operations.
Trend Micro Validation
To verify if Trend Micro Maximum Security features function smoothly:
Ensure that an infected file is detected by TrendMicro.
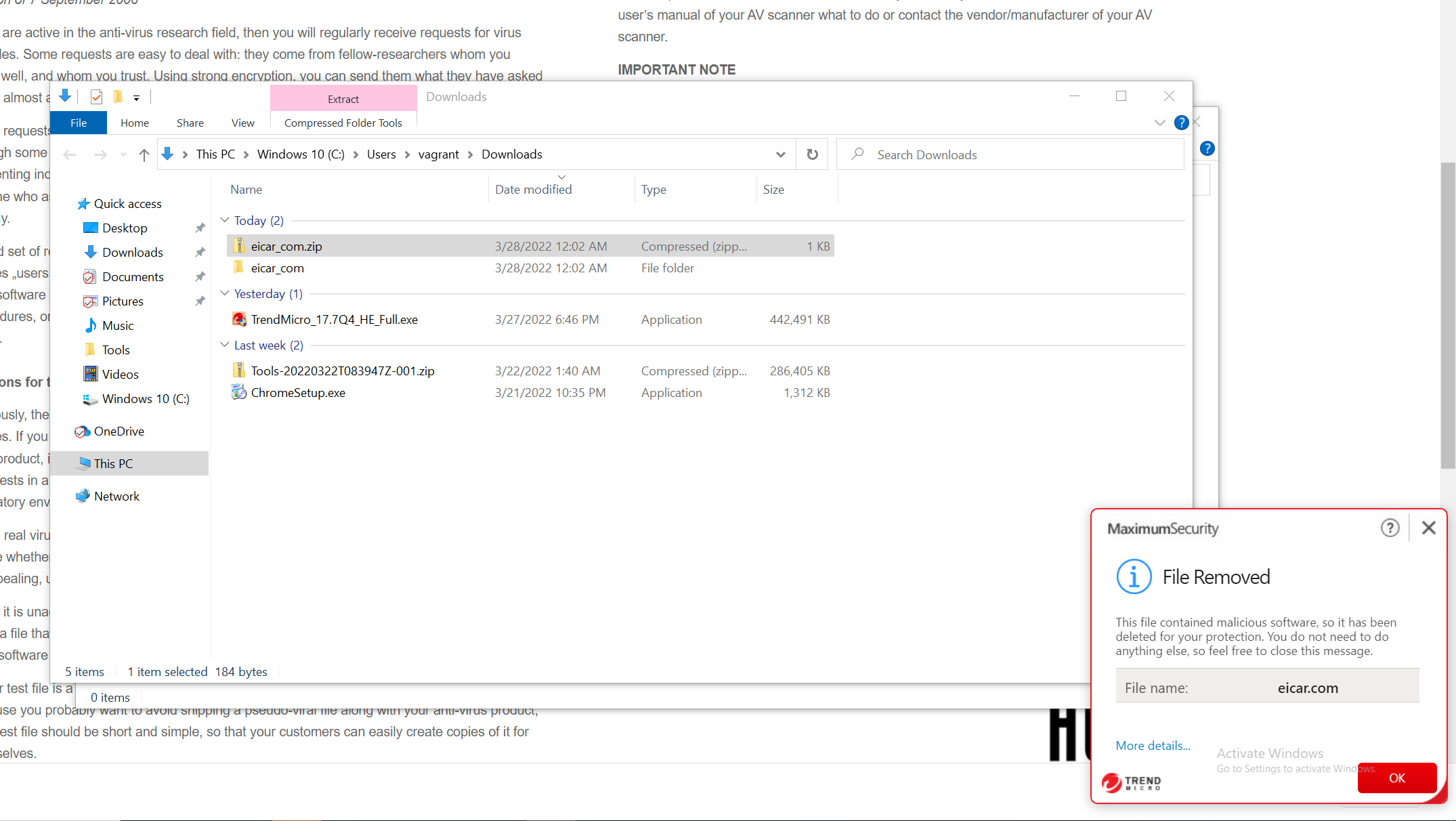
Click Check for program updates.
Ensure that Components are updated.