Configure the System, DNS, and Certificates
After you've configured the interfaces on the Secure Forwarder, follow the instructions to configure the system, DNS, and certificates.
Configure the System
First you need to install the tenant license key. You can get the license key from Settings > Security Cloud Platform next to where you downloaded the VA package.
Copy the license key.
In configuration mode, install the license key with the command:
set system licensekey <licensekey>.Next, configure the system hostname. Set the hostname type with the command:
set system hostname <hostname>.
Configure the DNS Server
Configure the IP address Secure Forwarder uses to listen for DNS requests. This address is the first address specified for the dp1 interface IP. If an IP range was specified for dp1, use the first IP address in that range (in canonical order), or use dp1 's IP.
set dataplane proxy-mode dns listener-ip 172.31.10.237
or,
set dataplane proxy-mode dns listener-interface dp1
Configure the address and/or address-range Secure Forwarder uses for DNS responses for cloud app domains. This address and/or address-range will be the same as that specified for the dp1 interface IP.
set dataplane proxy-mode dns application-ips 172.31.10.237
or,
set dataplane proxy-listener-interface dp1
Configure Secure Forwarder's default client traffic listener IP. This address is the first address configured on the dp1 interface.
set dataplane proxy-listener-ip 172.31.10.237
Enable DNS service on Secure Forwarder.
set dataplane proxy-mode dns enable true
Configure the primary upstream DNS Server in the network.
set dns primary <primary upstream dns server> set dns secondary <secondary upstream dns server>
Configure the Certificates
With connectivity now configured, you need to set up server side certificates to enable SSL inspection. You can use either a self-signed CA certificate or a CA certificate preferably signed by the enterprise's Root or intermediate CA. See Use your own CA Certificates.
Alternatively, the Secure Forwarder can generate a self-signed certificate without CA. See Generate a Self-signed Certificate without CA.
Use your own CA Certificates
Make sure that the CA certificate of the Secure Forwarder has a common name.
Enter the command:
set dataplane secure-forwarder server-certCopy and paste your CA certificate in the buffer, press Enter , then type
Ctrl-Dto exit.Enter the command:
set dataplane secure-forwarder server-keyCopy and paste your private key in the buffer, press Enter , then type
Ctrl-Dto exit.Enter the command:
set dataplane secure-forwarder server-intermediate-ca-chainCopy and paste any additional certificates in the following order:
Server certificate (as provided in step 1)
Intermediate CA certificate
Root CA certificate
Press Enter , then type
Ctrl-Dto exit.Enter
saveand press Enter to save the configuration.
Generate a Self-signed Certificate without CA
If you are not using a CA and want the Secure Forwarder to generate a self-signed certificate, run the following command:
run request certificate generate secure-forwarder self-signed city <city> common-name <common-name> country <country> days <days> email-address <email-address> organization <organization> organization-unit <organization-unit> state <state>
Here's an example command to generate self-signed certificate:
run request certificate generate secure-forwarder self-signed city "Los Altos" common-name "sforwarder.netskope.com" organization "netskope" organization-unit "netskope cert authority" state "CA" country "US" email-address "admin@netskope.com"
Enter
saveand press Enter to save the configuration.
Enable the Secure Forwarder Connection
Now enable the Secure Forwarder
set dataplane secure-forwarder enable true
Now save the entire configuration with the command save, and then press Enter.
You have now completed the installation and configuration of the Secure Forwarder, and Secure Forwarder will make an initial connection to Netskope cloud.
Note
From nsshell, you can use the SCP command to export and import a configuration.
Verify the Secure Forwarder Connection
To verify that Secure Forwarder successfully connected to tenant instance in the Netskope cloud, go to Settings > Security Cloud Platform > On-Premises Infrastructure. Scroll down the page until you see Secure Forwarder displayed with a Serial Number and Name. Last Seen shows the last time Secure Forwarder connected to the Netskope cloud.
Tip
It takes few minutes to refresh the status in the UI.
Verify the Certificates
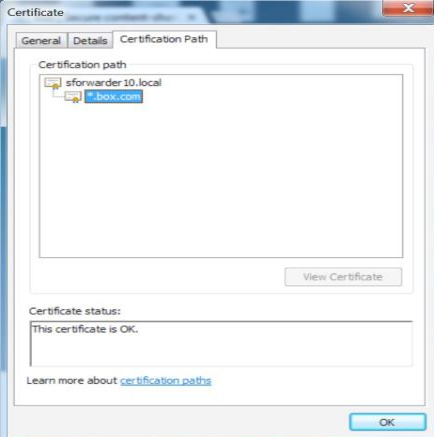
To verify that the cloud app traffic is forwarded by the Secure Forwarder to the tenant instance in the Netskope cloud, browse to any cloud app domain managed by Netskope (like Box.com) and verify that the SSL certificate presented is the certificate installed on the Secure Forwarder.
The image below shows a self-signed Root CA certificate installed on the Secure Forwarder that is presented to a browser.
 |