Chronicle Plugin for Log Shipper
This document explains how to configure your Chronicle integration with the Log Shipper module of the Netskope Cloud Exchange platform. This integration allows pushing alerts and events from Netskope to the Chronicle platform.
To complete this configuration, you need:
A Netskope tenant (or multiple, for example, production and development/test instances)
A Netskope Cloud Exchange tenant with the Log Shipper module already configured.
A Chronicle account. Obtain your Chronicle Base URL and Service Account Key, and Customer ID from your Chronicle representative before proceeding.
Connectivity to the following hosts, one of these selected Regional URLs:
USA: https://malachiteingestion-pa.googleapis.com/
EU: https://europe-malachiteingestion-pa.googleapis.com/
ASIA: https://asia-southeast1-malachiteingestion-pa.googleapis.com/
Other Custom URLs you have.
Get the Chronicle service account JSON. Reach out to the chronicle team to get a service account with the following scopes: https://www.googleapis.com/auth/malachite-ingestion.
Note
Verify your Chronicle instance permissions are secure and not set up for open public access. Only allow access to your cloud storage instance from your Cloud Exchange Host and any other addresses that need access.
Configure the Chronicle Plugin.
Configure Log Shipper Business Rules for Chronicle.
Configure Log Shipper SIEM Mappings for Chronicle.
Validate the Chronicle plugin.
Click play to watch a video.
In Cloud Exchange, go to Settings > Plugins.
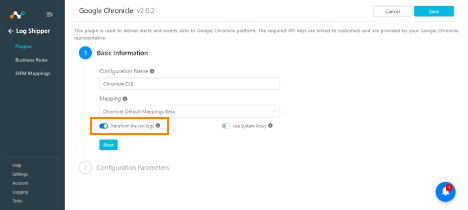
Search for and select the Chronicle v202 (CLS) box to open the plugin creation pages.

Enter a Configuration Name.
Select a valid Mapping (Default Mappings for all plugins are available). If Transform the raw logs is enabled, raw logs will be transformed using selected mapping file, else raw logs will be sent to SIEM. The ingestion may be affected if the SIEM does not accept raw logs format
Click Next.
Select Region, enter your Service Account Key (which is provided to you by your Chronicle representative), and Customer ID. If the selected region is Custom Region, then ONLY enter your Custom Region’s URL
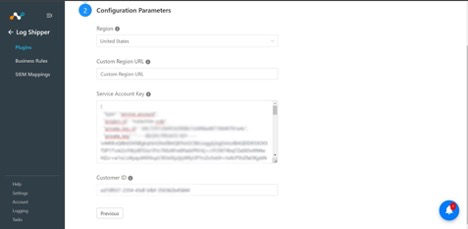
Click Save.
Go to Log Shipper > Business Rules.
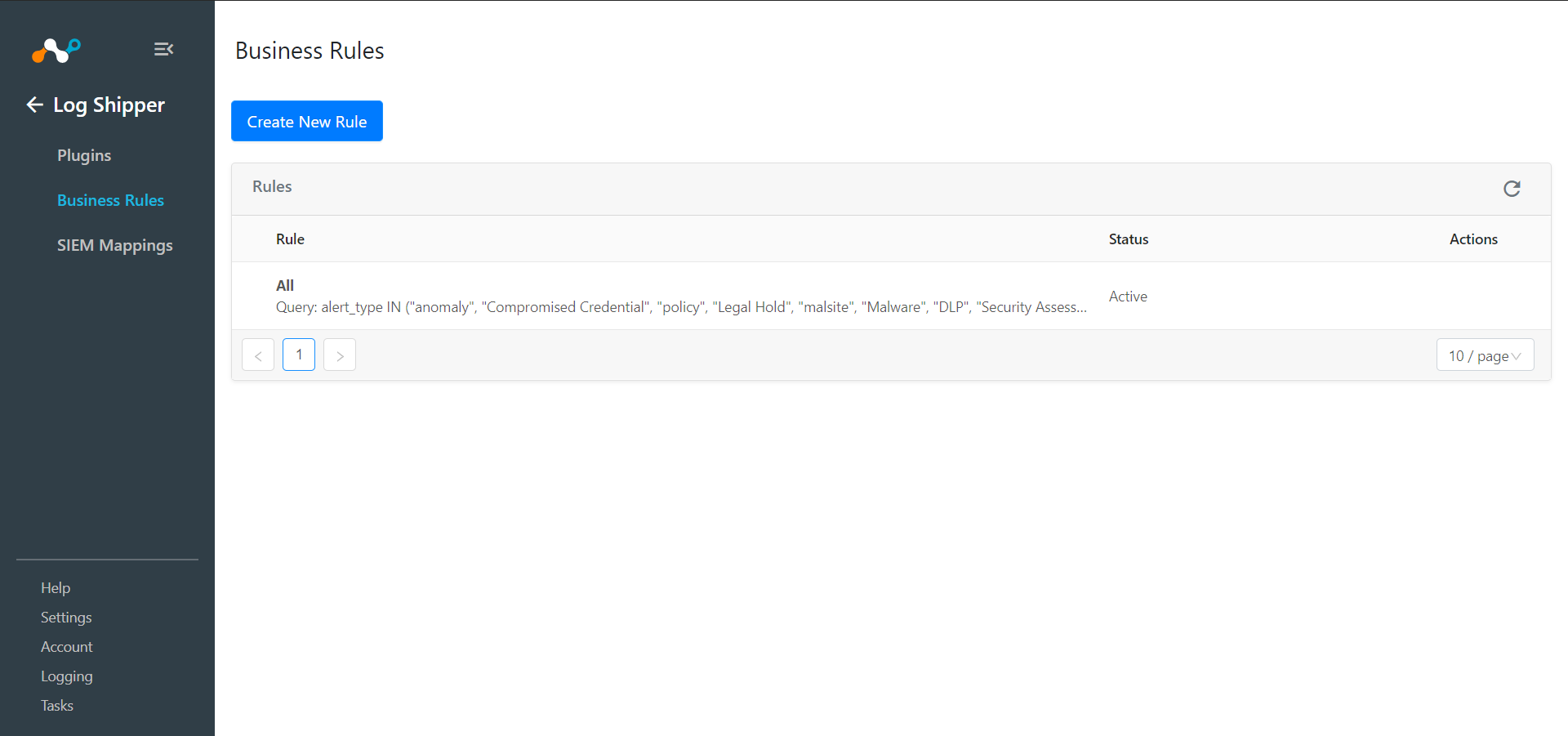
Click Create New Rule.
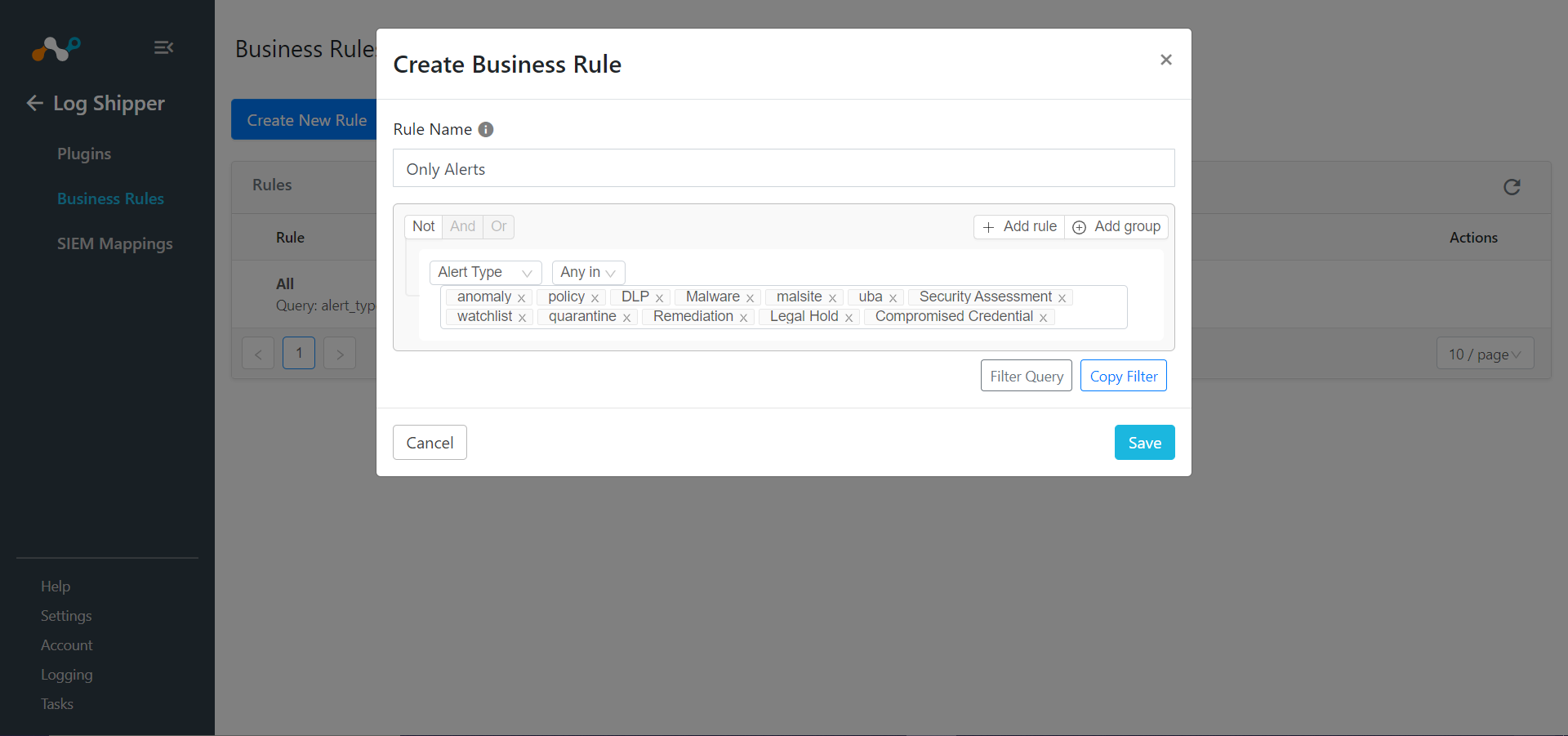
Enter a Rule Name and select the filters to use.
Click Save.
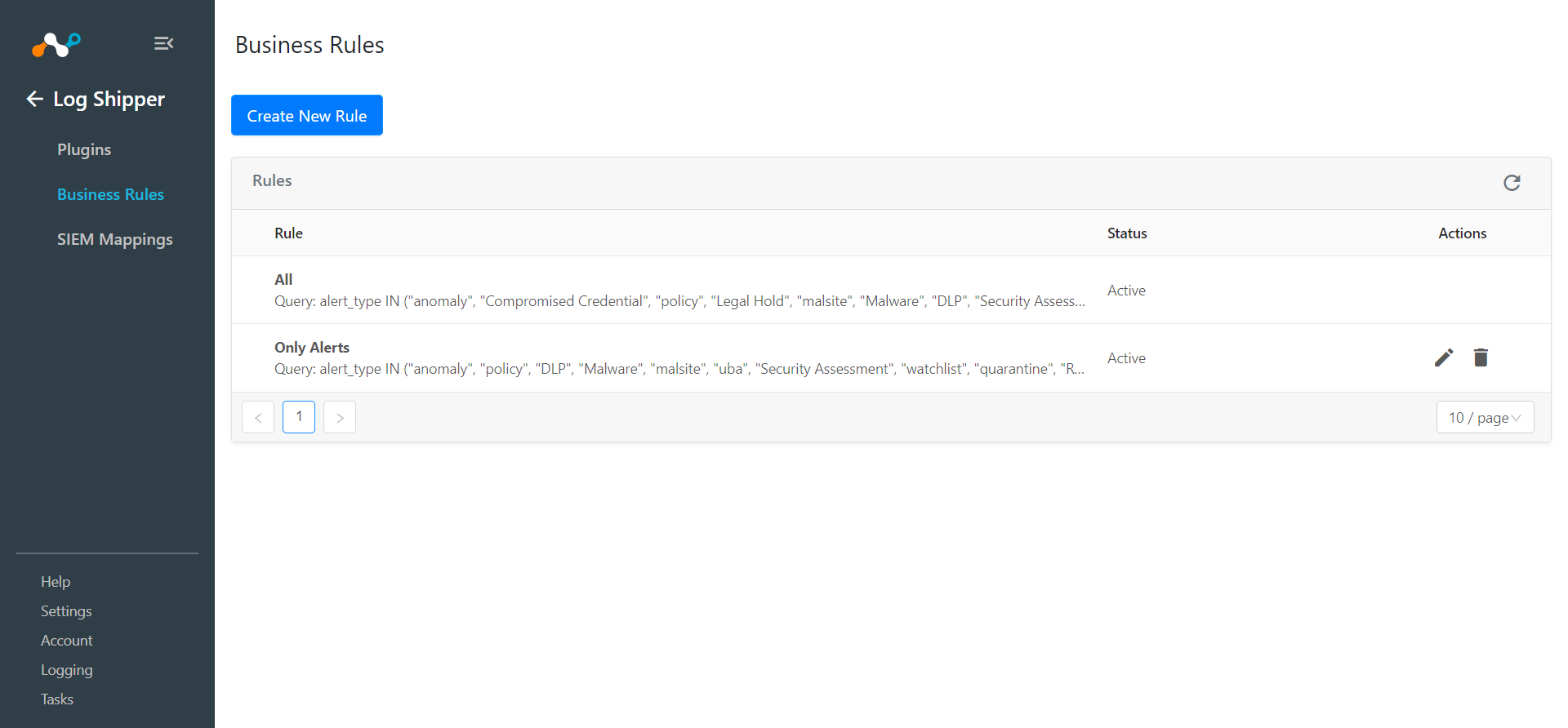
GoLog Shipper > SIEM Mappings and click Add SIEM Mapping.
Select a Source Configuration, Business Rule, and Destination Configuration.
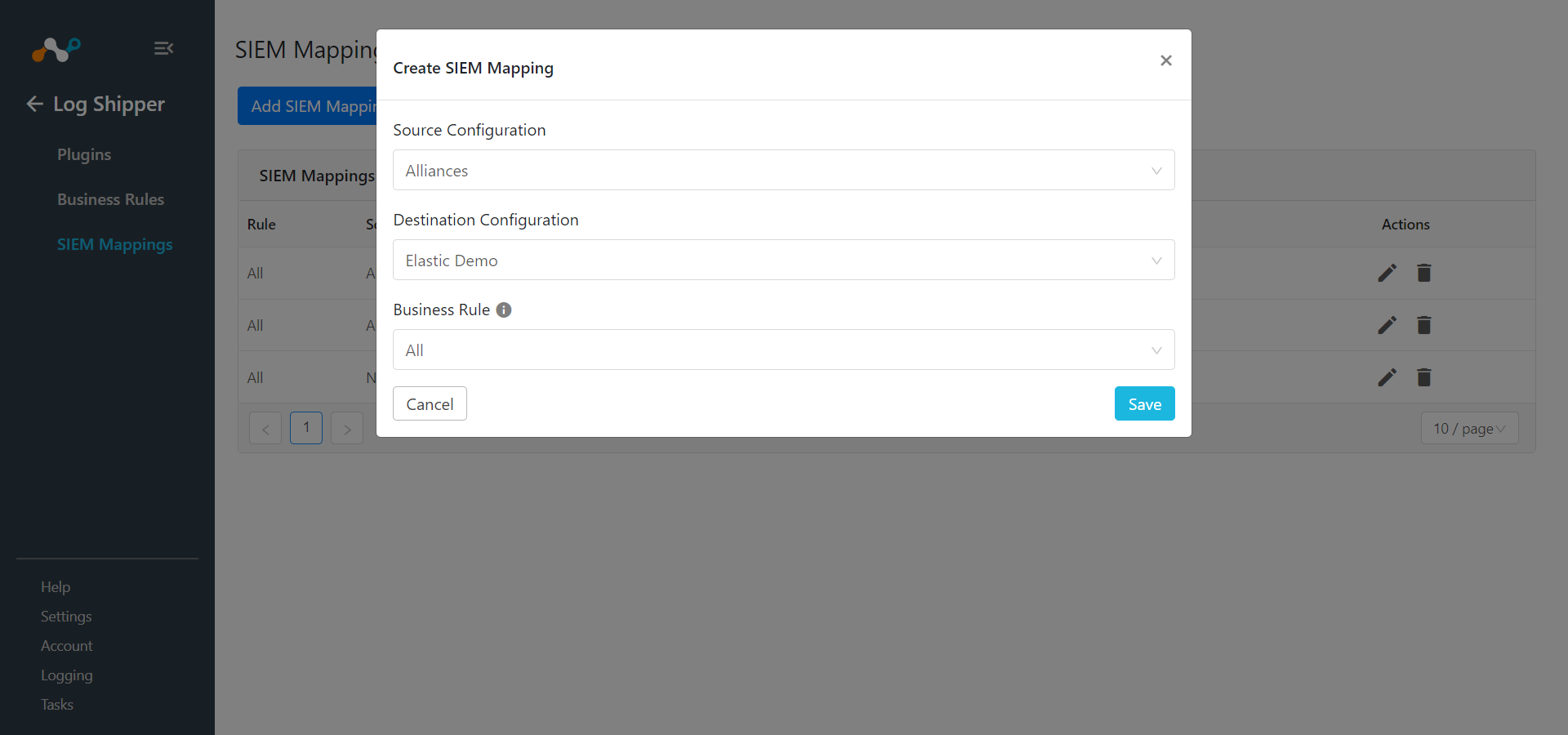
Click Save
To validate the plugin workflow, you can check from Netskope Cloud Exchange and from Chronicle Platform.
To validate from Netskope Cloud Exchange, go to Logging.
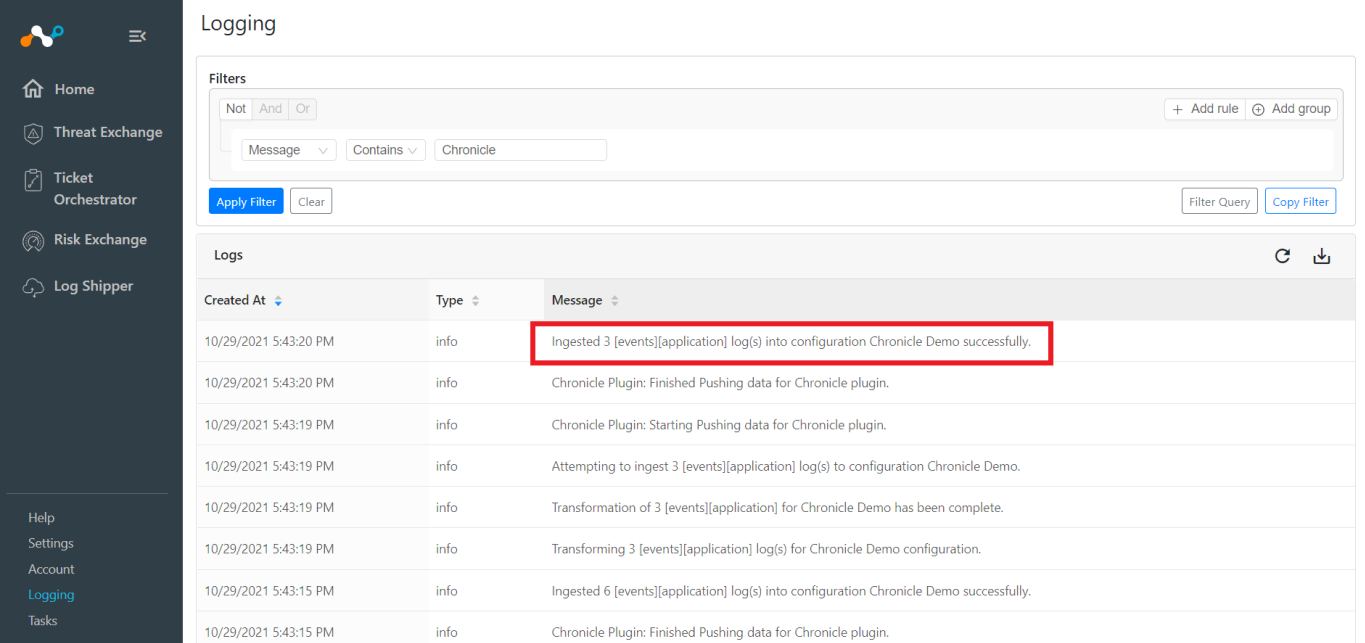 |
To validate from the Chronicle Platform.
Log in to the Chronicle Platform to view data.

Enter a keyword that you want to search for (in this case, an application) to search for ingested logs.

Click Search.

Click Row Log Search.
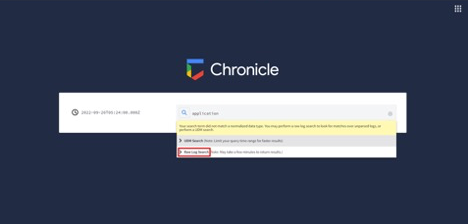
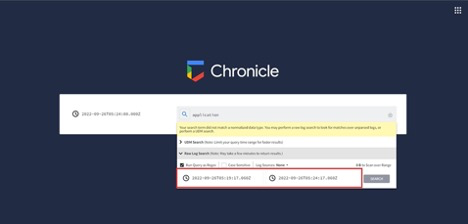
Set Start Time (UTC) and End Time (UTC) accordingly. (You can also select both times by reference (like 1 minute, 2 hours, 1 day). Click Search.
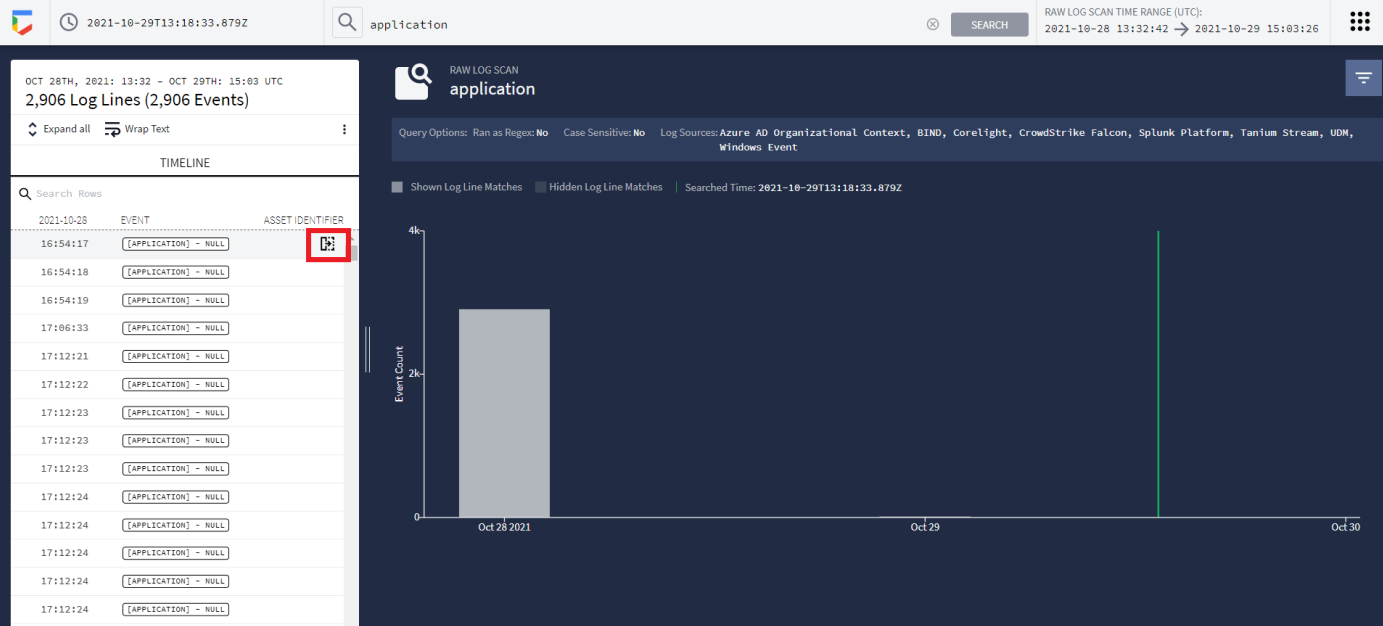
Click the adjacent icon to see details of the log.
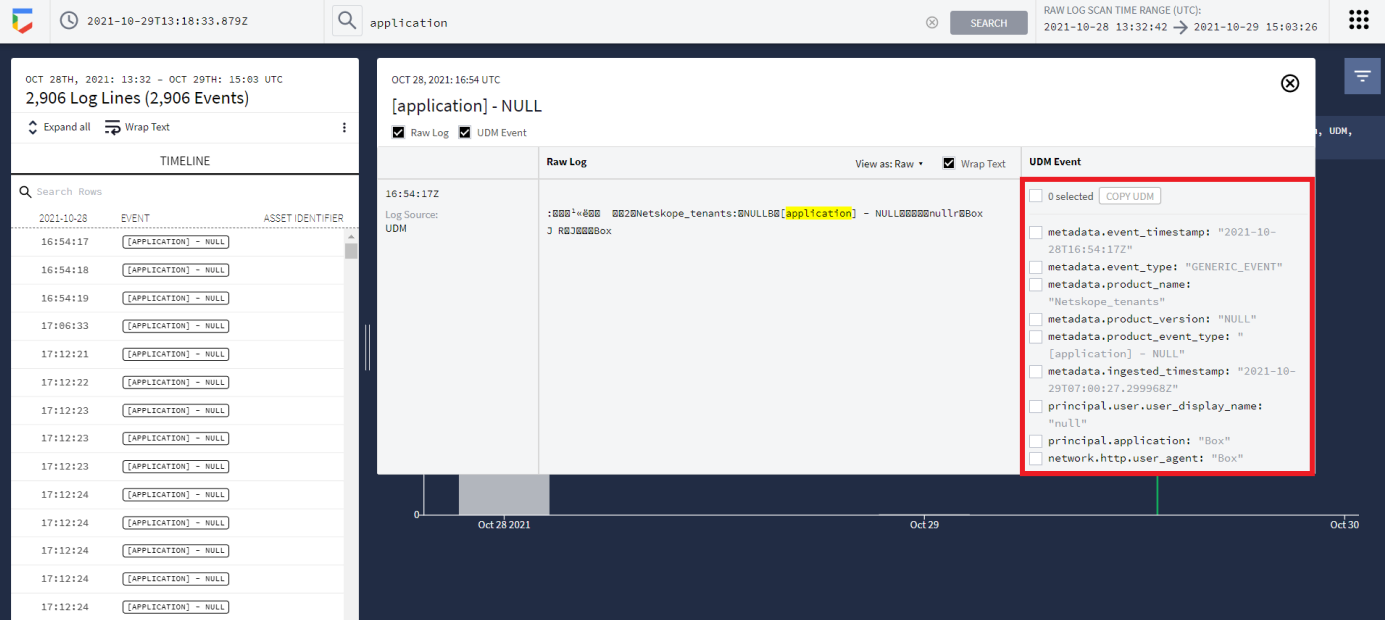
Then you see the ingested data.
Troubleshooting
If you received an error displayed in below screenshot after upgrading the core version, then try one of these steps:
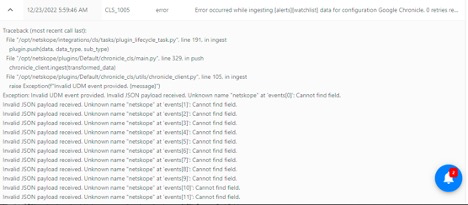 |
Remove
justification_typeandjustification_reasonfrom all the events/alerts.or
Use Default Mapping ( >= v1.0.4) file.