Get Started with Cloud Exchange
These instructions are for the Admin only. This section describes the initial steps for getting started with Netskope Cloud Exchange after installation is complete.
Default User Login
By default, a single user is created with administrative capabilities with these credentials: Username: admin Password: admin
This user will have Administrator level access to the application. This user will have write access, and will be able to create new users as well.
On the first login, you will be required to change these credentials. After that, log in using your new credentials.
 |
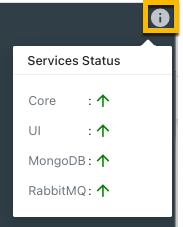
Service Status can be viewed on the i icon mouse hover at the top of the login screen. The default color of that icon should be grey. If any of the services are down, the icon will be highlighted with red color.
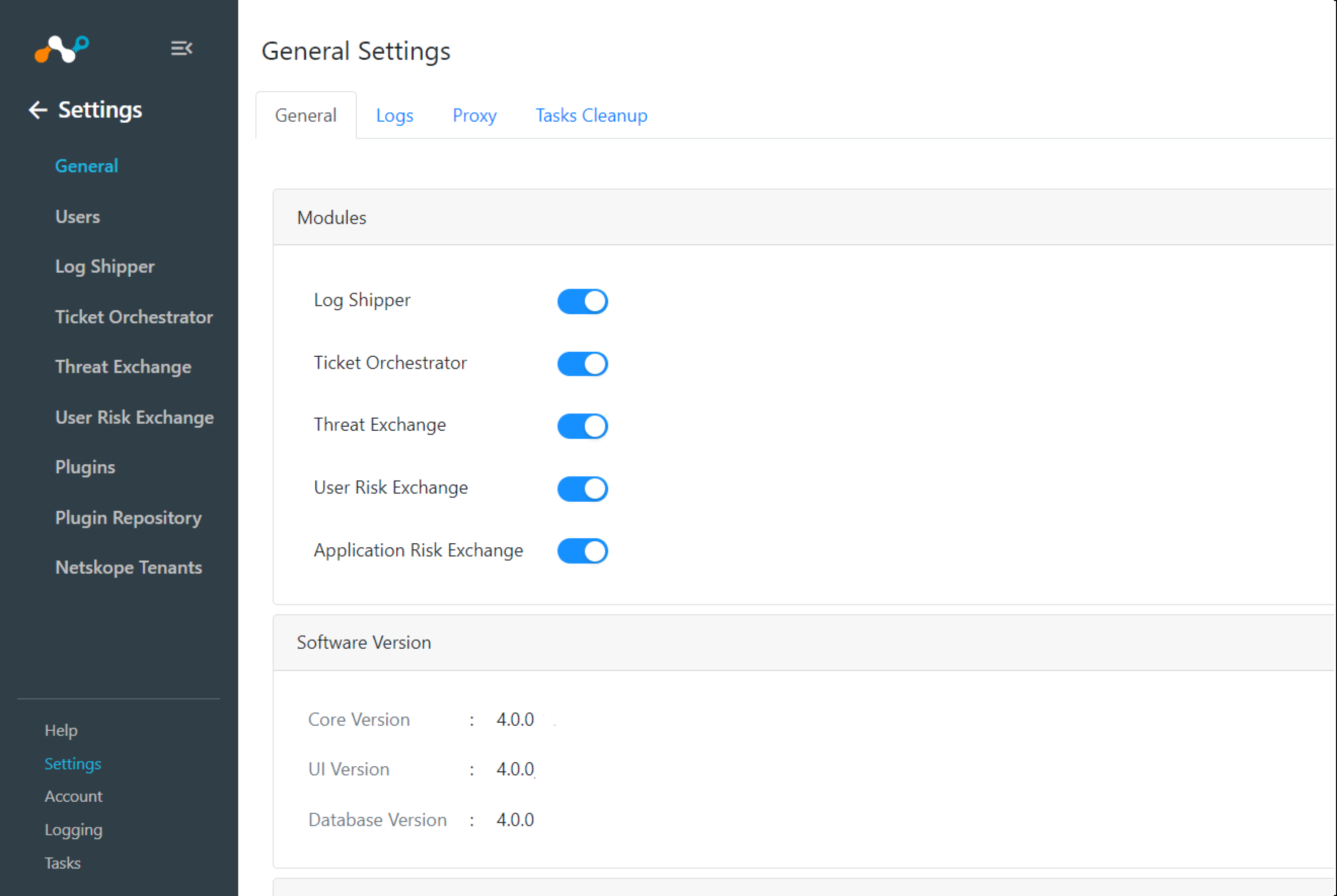
Enable Modules
Upon successful login, enable the modules you want to use.
 |
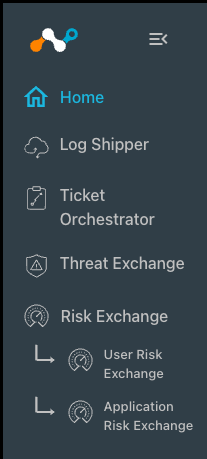
Enabled modules appear in the left panel.
 |
Go to the following sections to configure the Cloud Exchange modules you enabled.
Configure the Netskope Tenant Settings for Cloud Exchange
Before configuring the plugins for the modules you just enable, add a tenant in Cloud Exchange. To do this you must create a RESTful API v1 token in your Netskope tenant at Settings > Tools > REST API. Currently, a Netskope RESTful v1 API token must be installed for Cloud Exchange to communicate with Netskope because it is required for uploading file hashes for use in Threat Protection and DLP policies. You should also create a RESTful API v2 token in your Netskope tenant at Settings > Tools > REST API v2. Cloud Exchange will use the v2 endpoints whenever possible when communicating with the Netskope tenant.
When creating an API token for Cloud Exchange to use to communicate with a Netskope tenant, use least privileged access concepts. API v1 token should be rotated on a regular basis. Create and use in the Netskope Tenant configuration on the Cloud Exchange a properly entitled v2 token with the specified privileges.
Endpoint | Privilege | Log Shipper (CLS) | Ticket Orchestrator (CTO) | Threat Exchange (CTE) | User Risk Exchange (URE) | App Risk Exchange (ARE) | Notes |
|---|---|---|---|---|---|---|---|
Token Generated and Not Expired | (all) | x | Required for sharing file hashes |
Endpoint | Privilege | Log Shipper (CLS) | Ticket Orchestrator (CTO) | Threat Exchange (CTE) | User Risk Exchange (URE) | App Risk Exchange (ARE) | Notes |
|---|---|---|---|---|---|---|---|
/api/v2/events/data/alert | Read | ||||||
/api/v2/events/data/application | Read | ||||||
/api/v2/events/data/audit | Read | ||||||
/api/v2/events/data/infrastructure | Read | ||||||
/api/v2/events/data/network | Read | ||||||
/api/v2/events/data/page | Read | ||||||
/api/v2/events/dataexport/events/alert | Read | x | x | x | x | x | Required to validate API token |
/api/v2/events/dataexport/events/application | Read | x | x | ||||
/api/v2/events/dataexport/events/audit | Read | x | |||||
/api/v2/events/dataexport/events/connection | Read | ||||||
/api/v2/events/dataexport/events/incident | Read | x | |||||
/api/v2/events/dataexport/events/infrastructure | Read | x | |||||
/api/v2/events/dataexport/events/network | Read | x | |||||
/api/v2/events/dataexport/events/page | Read | x | |||||
/api/v2/events/dataexport/alerts/uba | Read | x | x | ||||
/api/v2/events/dataexport/alerts/securityassessment | Read | x | x | ||||
/api/v2/events/dataexport/alerts/quarantine | Read | x | x | x | |||
/api/v2/events/dataexport/alerts/remediation | Read | x | x | ||||
/api/v2/events/dataexport/alerts/policy | Read | x | x | ||||
/api/v2/events/dataexport/alerts/malware | Read | x | x | x | |||
/api/v2/events/dataexport/alerts/malsite | Read | x | x | x | |||
/api/v2/events/dataexport/alerts/compromisedcredential | Read | x | x | ||||
/api/v2/events/dataexport/alerts/ctep (or ips) | Read | ||||||
/api/v2/events/dataexport/alerts/dlp | Read | x | x | ||||
/api/v2/events/dataexport/alerts/watchlist | Read | x | x | ||||
/api/v2/policy/urllist/file | Read + Write | ||||||
/api/v2/policy/urllist | Read + Write | x | |||||
/api/v2/policy/urllist/deploy | Read + Write | x | |||||
/api/v2/incidents/uba/getuci | Read + Write | x | |||||
/api/v2/ubadatasvc/user/uci | Read + Write | x | |||||
/api/v2/services/cci/app | Read | x | |||||
/api/v2/services/cci/domain | Read | x | |||||
/api/v2/services/cci/tags | Read | x |
x: Required API scopes for the corresponding CE module.
Endpoint | Privilege | Log Shipper (CLS) | Ticket Orchestrator (CTO) | Threat Exchange (CTE) | User Risk Exchange (URE) | App Risk Exchange (ARE) | Notes |
|---|---|---|---|---|---|---|---|
Token Generated and Not Expired | (all) | y | y | x+y (*) | y | y | * Required for sharing file hashes |
Endpoint | Privilege | Log Shipper (CLS) | Ticket Orchestrator (CTO) | Threat Exchange (CTE) | User Risk Exchange (URE) | App Risk Exchange (ARE) | Notes |
|---|---|---|---|---|---|---|---|
/api/v2/events/data/alert | Read | y | y | y | y | y | |
/api/v2/events/data/application | Read | y | |||||
/api/v2/events/data/audit | Read | y | |||||
/api/v2/events/data/infrastructure | Read | y | |||||
/api/v2/events/data/network | Read | y | |||||
/api/v2/events/data/page | Read | y | |||||
/api/v2/events/dataexport/events/alert | Read | x | x | x | x | x | |
/api/v2/events/dataexport/events/application | Read | x | x | ||||
/api/v2/events/dataexport/events/audit | Read | x | |||||
/api/v2/events/dataexport/events/connection | Read | ||||||
/api/v2/events/dataexport/events/incident | Read | ||||||
/api/v2/events/dataexport/events/infrastructure | Read | x | |||||
/api/v2/events/dataexport/events/network | Read | x | |||||
/api/v2/events/dataexport/events/page | Read | x | |||||
/api/v2/events/dataexport/alerts/uba | Read | ||||||
/api/v2/events/dataexport/alerts/securityassessment | Read | ||||||
/api/v2/events/dataexport/alerts/quarantine | Read | ||||||
/api/v2/events/dataexport/alerts/remediation | Read | ||||||
/api/v2/events/dataexport/alerts/policy | Read | ||||||
/api/v2/events/dataexport/alerts/malware | Read | ||||||
/api/v2/events/dataexport/alerts/malsite | Read | ||||||
/api/v2/events/dataexport/alerts/compromisedcredential | Read | ||||||
/api/v2/events/dataexport/alerts/ctep (or ips) | Read | ||||||
/api/v2/events/dataexport/alerts/dlp | Read | ||||||
/api/v2/events/dataexport/alerts/watchlist | Read | ||||||
/api/v2/policy/urllist/file | Read + Write | ||||||
/api/v2/policy/urllist | Read + Write | x + y | |||||
/api/v2/policy/urllist/deploy | Read + Write | x + y | |||||
/api/v2/incidents/uba/getuci | Read + Write | x + y | |||||
/api/v2/ubadatasvc/user/uci | Read + Write | x + y | |||||
/api/v2/services/cci/app | Read | x + y | |||||
/api/v2/services/cci/domain | Read | x + y | |||||
/api/v2/services/cci/tags | Read | x + y |
x: Required API scopes for the corresponding CE module if modern /events/dataexport endpoints will be used (recommended).
y: Required API scopes for the corresponding CE module if legacy /events/data endpoints will be used (deprecated starting in 4.1.0).
x+y: Required API scopes for the corresponding CE module (when using either /events/dataexport or /events/data endpoints).
Endpoint | Privilege | Log Shipper (CLS) | Ticket Orchestrator (CTO) | Threat Exchange (CTE) | User Risk Exchange (URE) | App Risk Exchange (ARE) | Notes |
|---|---|---|---|---|---|---|---|
Token Generated and Not Expired | (all) | y | Required for sharing file hashes |
Endpoint | Privilege | Log Shipper (CLS) | Ticket Orchestrator (CTO) | Threat Exchange (CTE) | Cloud Risk Exchange (CRE) | Notes |
|---|---|---|---|---|---|---|
/api/v2/events/data/alert | Read | y | y | y | y | |
/api/v2/events/data/application | Read | y | ||||
/api/v2/events/data/audit | Read | y | ||||
/api/v2/events/data/infrastructure | Read | y | ||||
/api/v2/events/data/network | Read | y | ||||
/api/v2/events/data/page | Read | y | ||||
/api/v2/events/dataexport/events/alert | Read | |||||
/api/v2/events/dataexport/events/application | Read | |||||
/api/v2/events/dataexport/events/audit | Read | |||||
/api/v2/events/dataexport/events/connection | Read | |||||
/api/v2/events/dataexport/events/incident | Read | |||||
/api/v2/events/dataexport/events/infrastructure | Read | |||||
/api/v2/events/dataexport/events/network | Read | |||||
/api/v2/events/dataexport/events/page | Read | |||||
/api/v2/events/dataexport/alerts/uba | Read | |||||
/api/v2/events/dataexport/alerts/securityassessment | Read | |||||
/api/v2/events/dataexport/alerts/quarantine | Read | |||||
/api/v2/events/dataexport/alerts/remediation | Read | |||||
/api/v2/events/dataexport/alerts/policy | Read | |||||
/api/v2/events/dataexport/alerts/malware | Read | |||||
/api/v2/events/dataexport/alerts/malsite | Read | |||||
/api/v2/events/dataexport/alerts/compromisedcredential | Read | |||||
/api/v2/events/dataexport/alerts/ctep (or ips) | Read | |||||
/api/v2/events/dataexport/alerts/dlp | Read | |||||
/api/v2/events/dataexport/alerts/watchlist | Read | |||||
/api/v2/policy/urllist/file | Read + Write | |||||
/api/v2/policy/urllist | Read + Write | y | ||||
/api/v2/policy/urllist/deploy | Read + Write | y | ||||
/api/v2/incidents/uba/getuci | Read + Write | y | ||||
/api/v2/ubadatasvc/user/uci | Read + Write | y | ||||
/api/v2/services/cci/app | Read | |||||
/api/v2/services/cci/domain | Read | |||||
/api/v2/services/cci/tags | Read |
y: Required API scopes for the corresponding CE module.
Add a Netskope Tenant
Now that you have your v1 and v2 tokens ready, proceed with the Netskope tenant configuration of your Cloud Exchange instance.
Log in to your Cloud Exchange tenant.
Go to Settings and click Netskope Tenants.
Click Add Tenant.
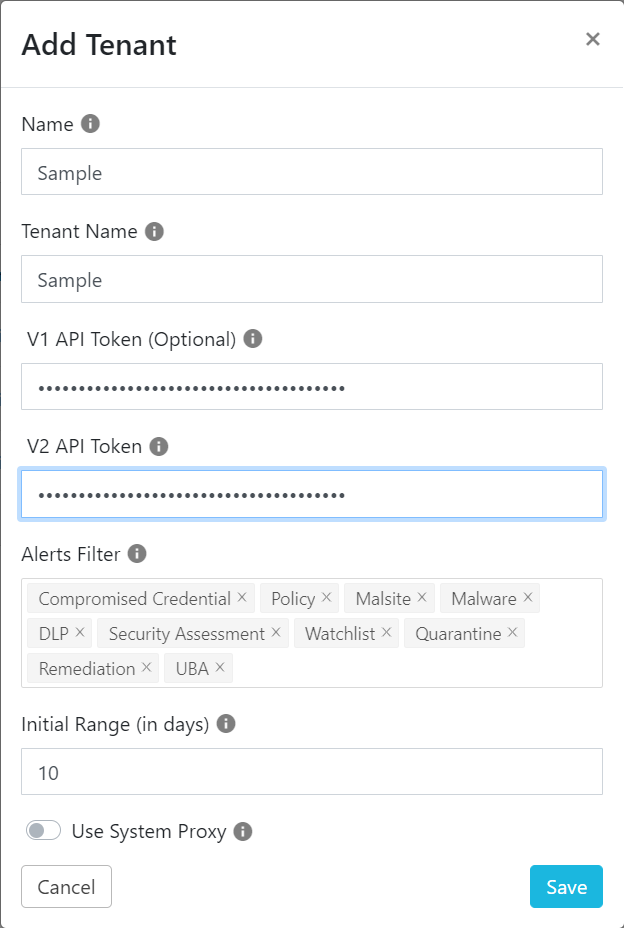
Enter a name for your Netskope tenant.
Enter your Netskope tenant name. Do not enter the
<tenant_name>.goskope.com, URL. Enter just your tenant. For example, if it'smycompany.goskope.com, just entermycompany. If your tenant haseuin the URL, entertenant_name.eu.Enter your Netskope tenant API token(s) obtained previously.
Select alerts types for filtering alerts from the tenant.
Set the range for ingesting data from Netskope. In this case, set the Initial Range to 7 days to pre-populate Log Shipper.
If you use a proxy, enable the proxy toggle.
Click Save. Your tenant appears on the page.