Microsoft Defender for Cloud Apps Plugin for Log Shipper
This document explains how to configure the Microsoft Defender for Cloud Apps integration with the Log Shipper module of the Netskope Cloud Exchange platform. This integration allows for forwarding Netskope generated events to Microsoft Cloud App Security for additional analysis and reporting.
To complete this configuration, you need:
A Netskope Tenant (or multiple, for example, production and development/test instances).
A Netskope Cloud Exchange tenant with the Log Shipper module already configured.
A Microsoft Defender for Cloud Apps instance.
Note
Verify your Microsoft Defender instance permissions are secure and not set up for open public access. Only allow access to your cloud storage instance from your Cloud Exchange Host and any other addresses that need access.
Configure the Microsoft Defender for Cloud Apps Data Source.
Configure the Microsoft Defender for Cloud Apps plugin.
Create Log Shipper Business Rules.
Create Log Shipper SIEM mappings.
Validate the plugin.
Click play to watch a video.
Go to your Microsoft Defender for Cloud Apps instance at:
https://<instance-name>.portal.cloudappsecurity.com/.
Log in to your Microsoft Defender for Cloud Apps instance.
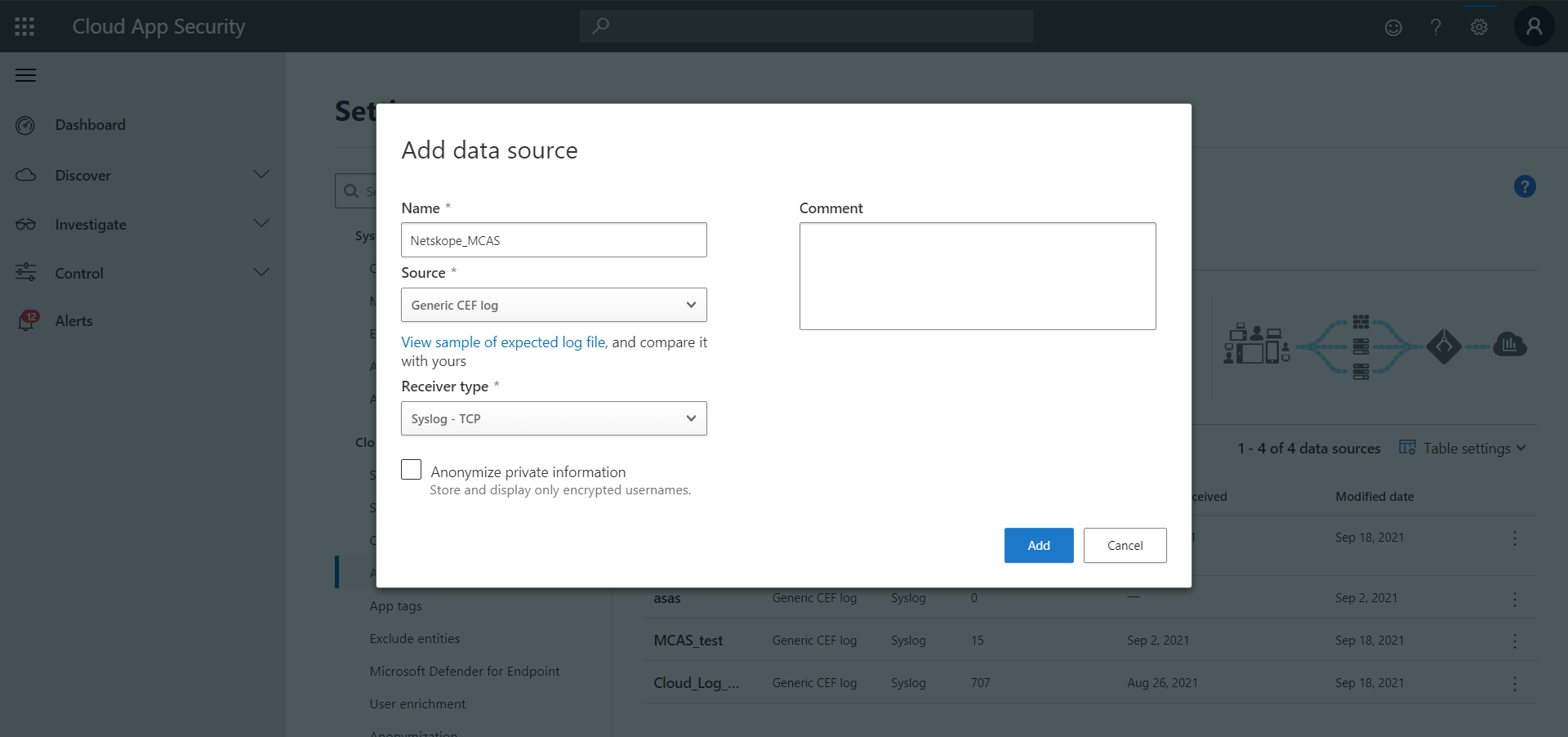
Click Settings and then click Log Collectors.
Click Add data source.
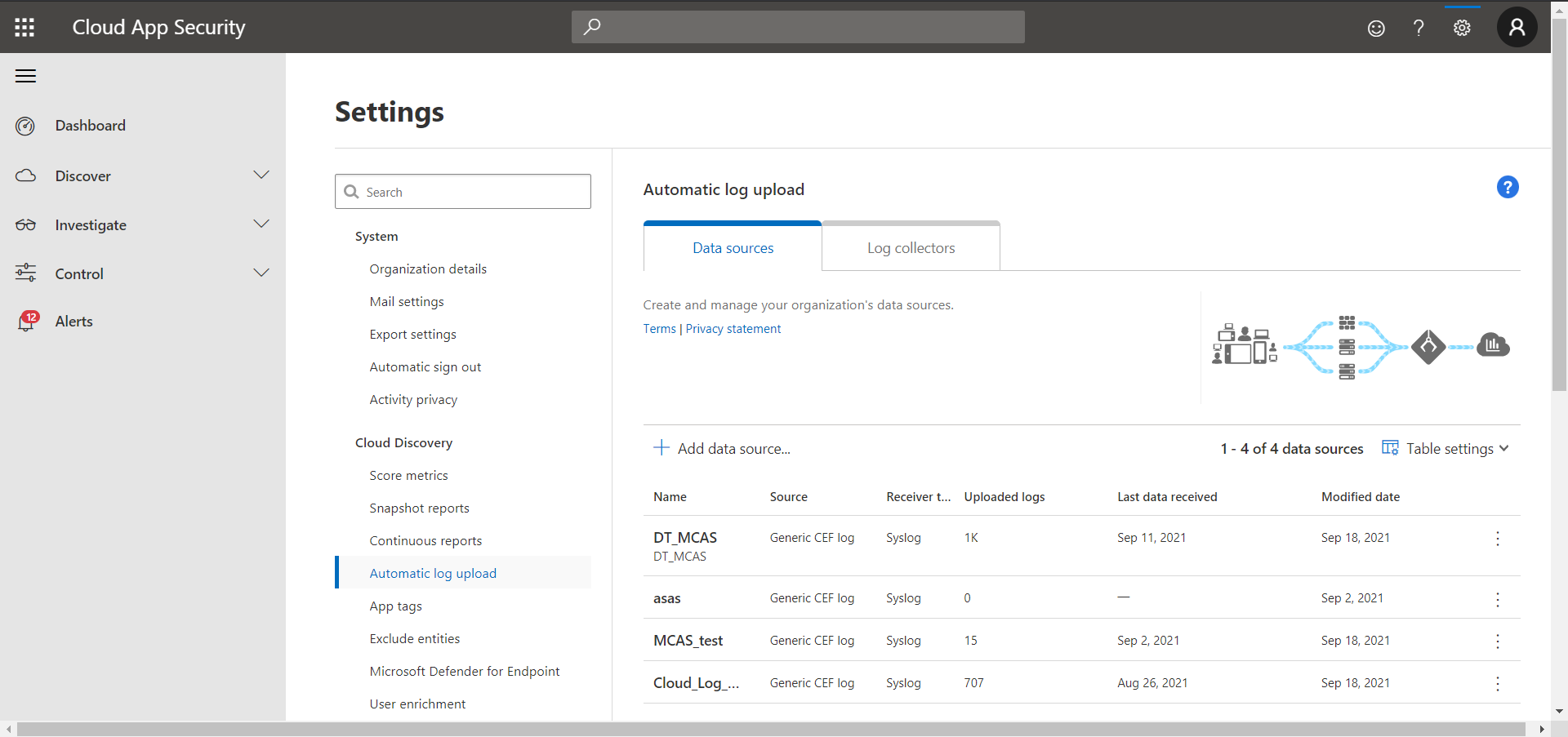
Enter a name and select Source and Receiver type, and then click Add.
In Cloud Exchange, go to Settings > Plugins.
Search for and select the Microsoft Cloud App Security (CLS) box to open the plugin creation pages.
Enter a Configuration Name.
Select the valid Mapping. (Default Mappings for all plugins are available).
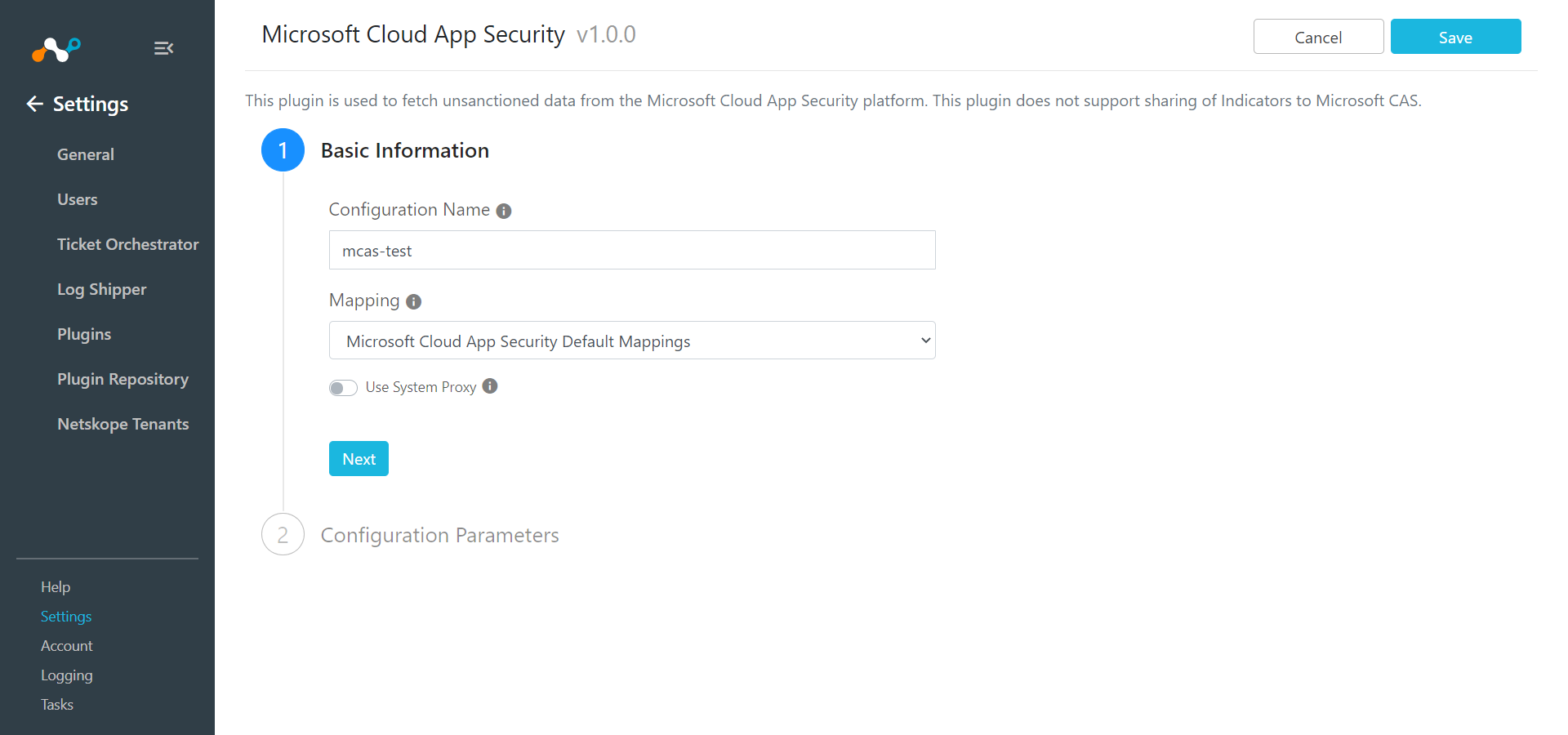
Click Next.
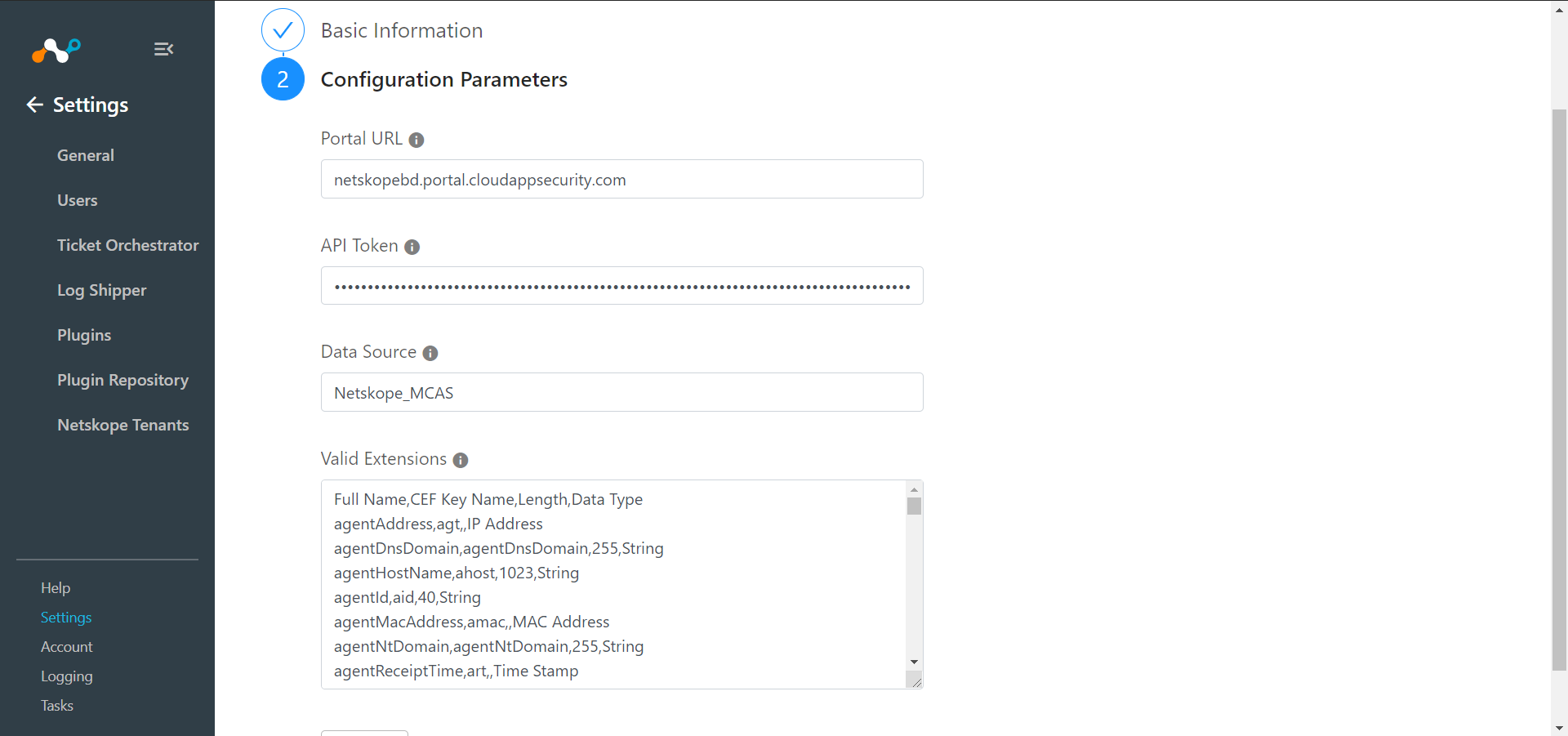
Enter the Portal URL, API Token, and Data Source. Enter valid extensions if you have other than the default one.
Click Save.
Go to Log Shipper > Business Rules.
Click Create New Rule.
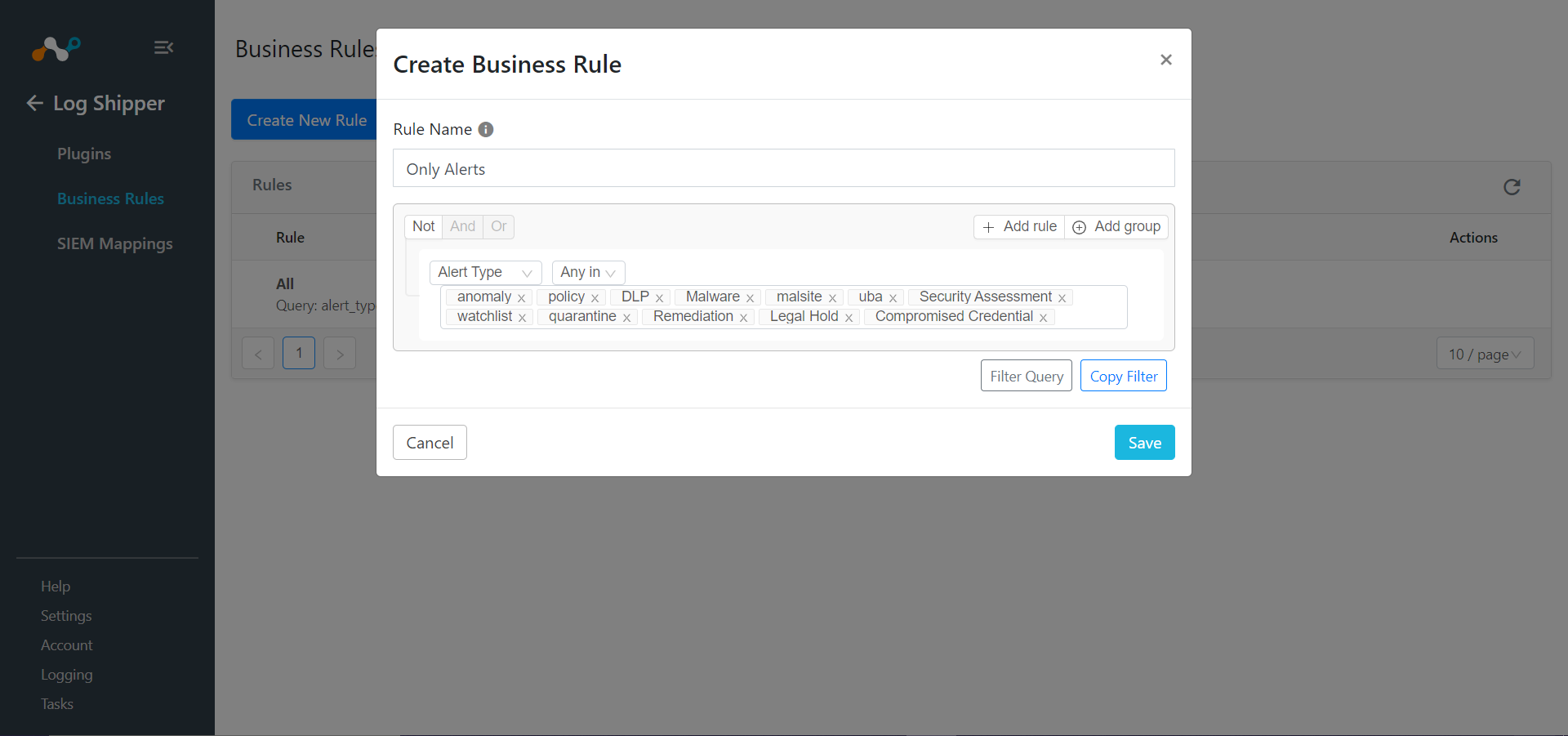
Enter a Rule Name and select the filters to use.
Click Save
Go to Log Shipper > SIEM Mappings and click Add SIEM Mapping.
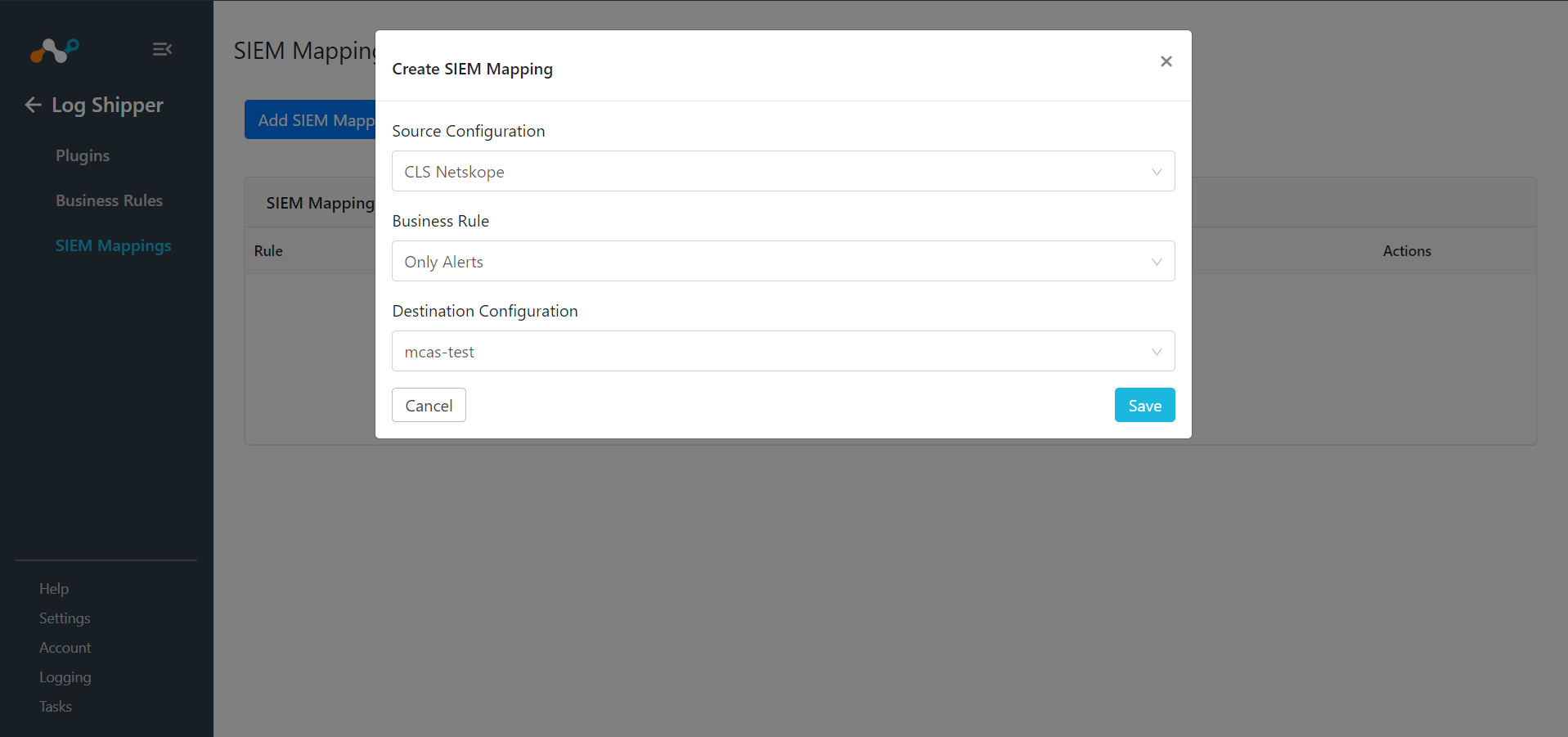
Select a Source Configuration, Business Rule, and Destination Configuration.
Click Save.
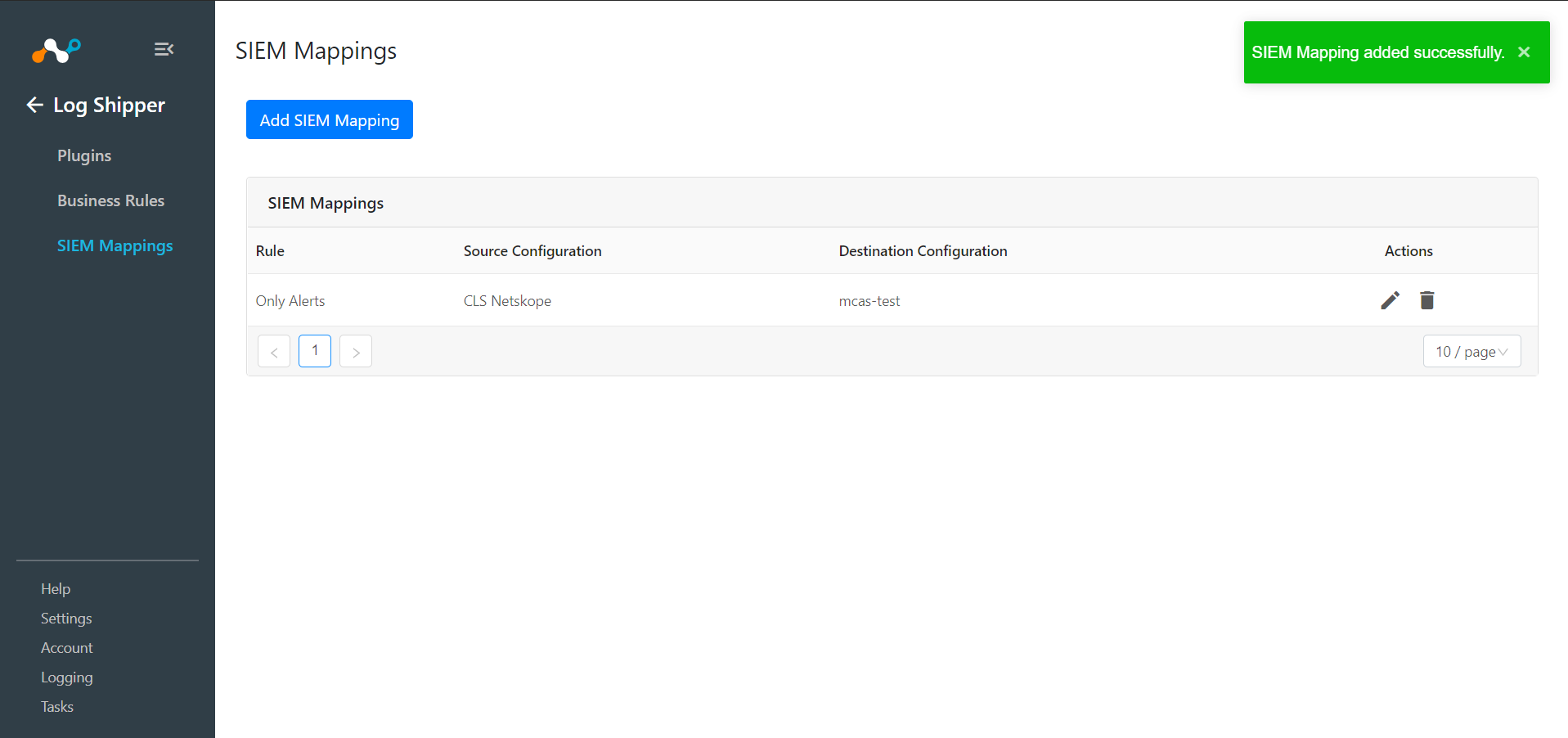
To validate the plugin workflow, you can check from Netskope Cloud Exchange and and your Microsoft Defender for Cloud Apps instance.
To validate from Netskope Cloud Exchange, go to Logging.
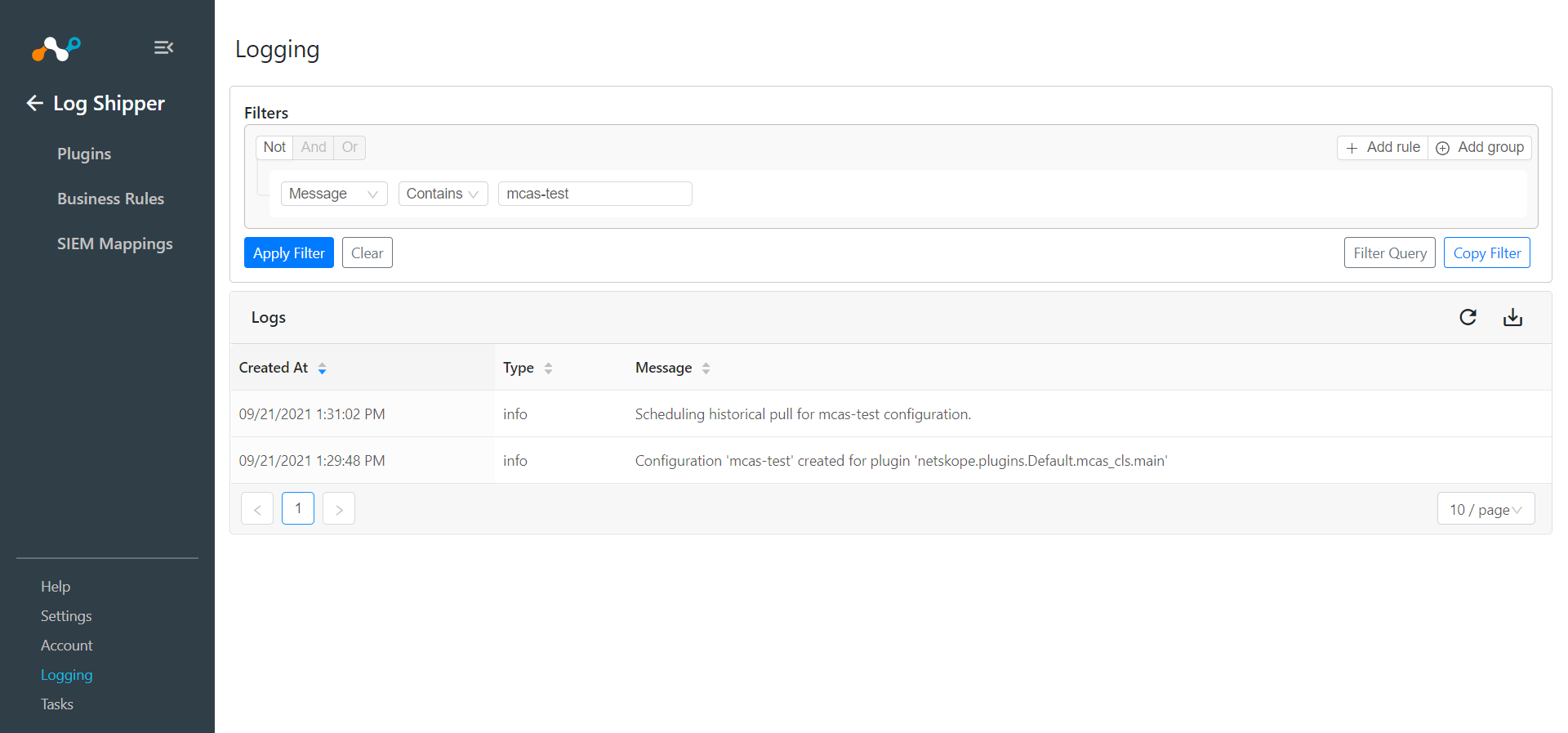 |
To validate from the Microsoft Defender for Cloud Apps instance, go to Setting Governance Log.
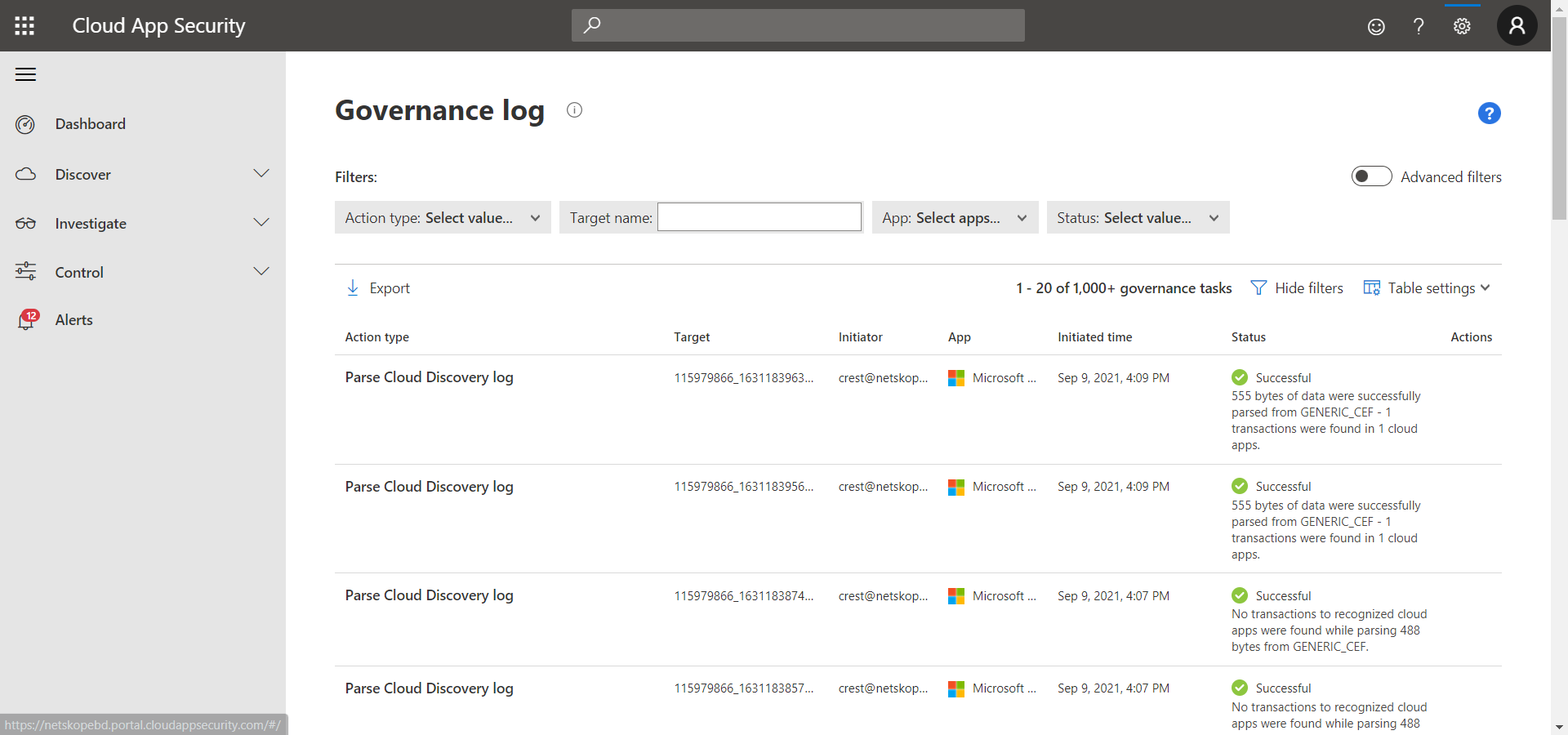 |