Step 2/2: Configure AWS Permissions for UEBA
Netskope requires permissions to assume a role and scan your AWS resources. This screen provides a customized CFT with permissions required to set up cross account access between Netskope and your AWS accounts. The permissions defined in the CFT are updated based on the services you've enabled in the Accounts & Services page.
You can review the CFT to understand the various permissions required by Netskope.
Note
Ensure that the AWS accounts have the permissions required to run the Netskope for IaaS services.
To complete the set up you must:
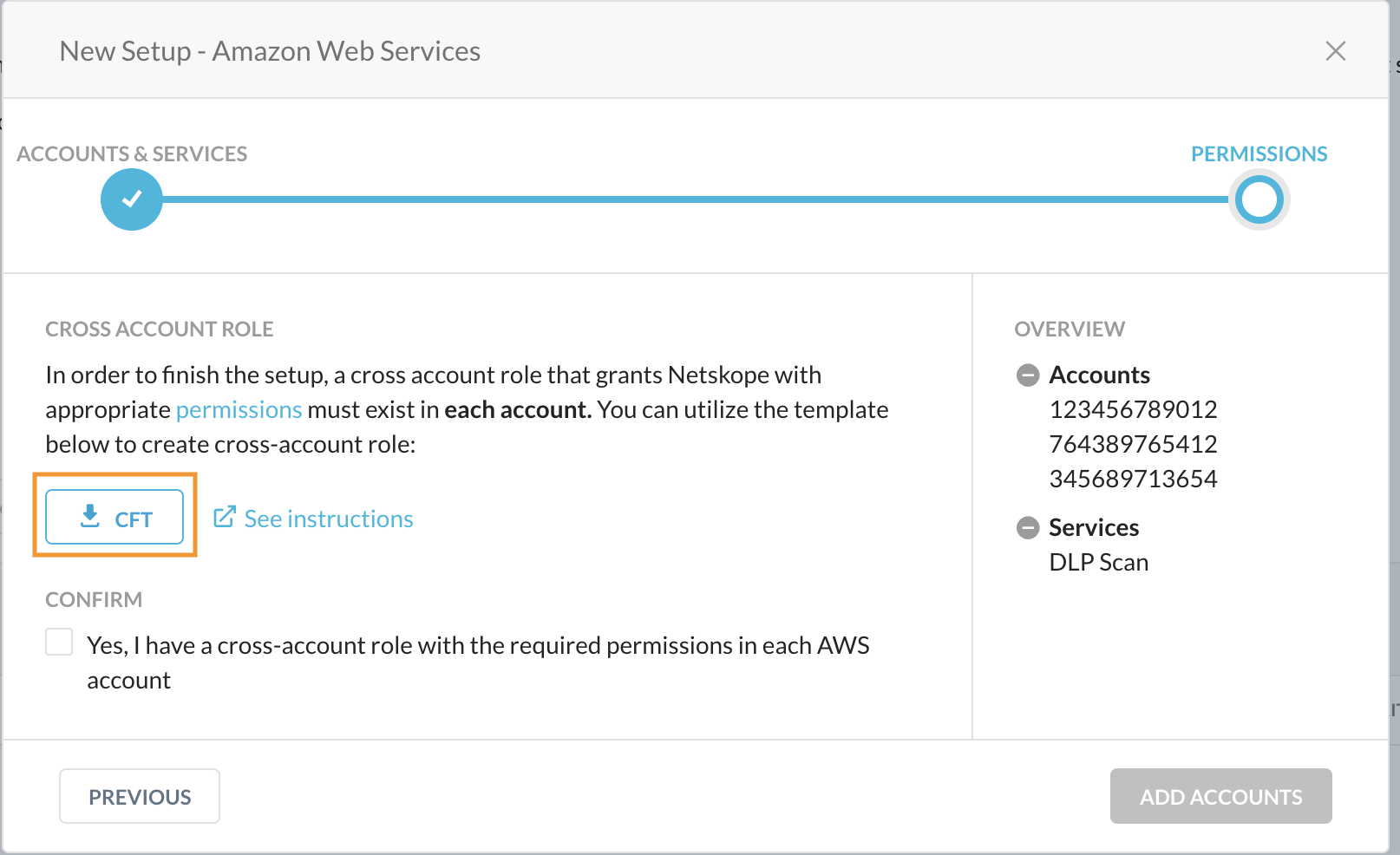
Download the CFT.
Upload the CFT to a new CloudFormation stack in each AWS account.
Confirm that a cross account role with the required permissions is created.
Follow the detailed instructions below to complete the set up.
In the Permissions screen of the New Setup window, click the link to download the CFT.
Log in to the AWS Management Console using the credentials of the AWS account you are setting up with Netskope for IaaS and navigate to Services > CloudFormation.
In the CloudFormation page, click Create stack.
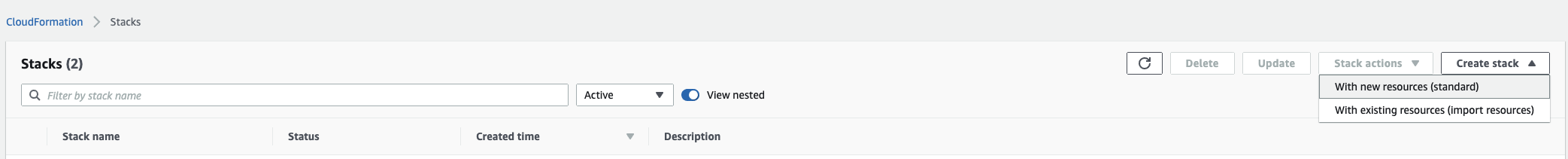
To create a stack with new resources, choose With new resources (standard).
To create a stack with existing resources, choose With existing resources (import resources).
Select Upload a template file and click Choose file to upload the aws-instance-setup.yml. Click Next.
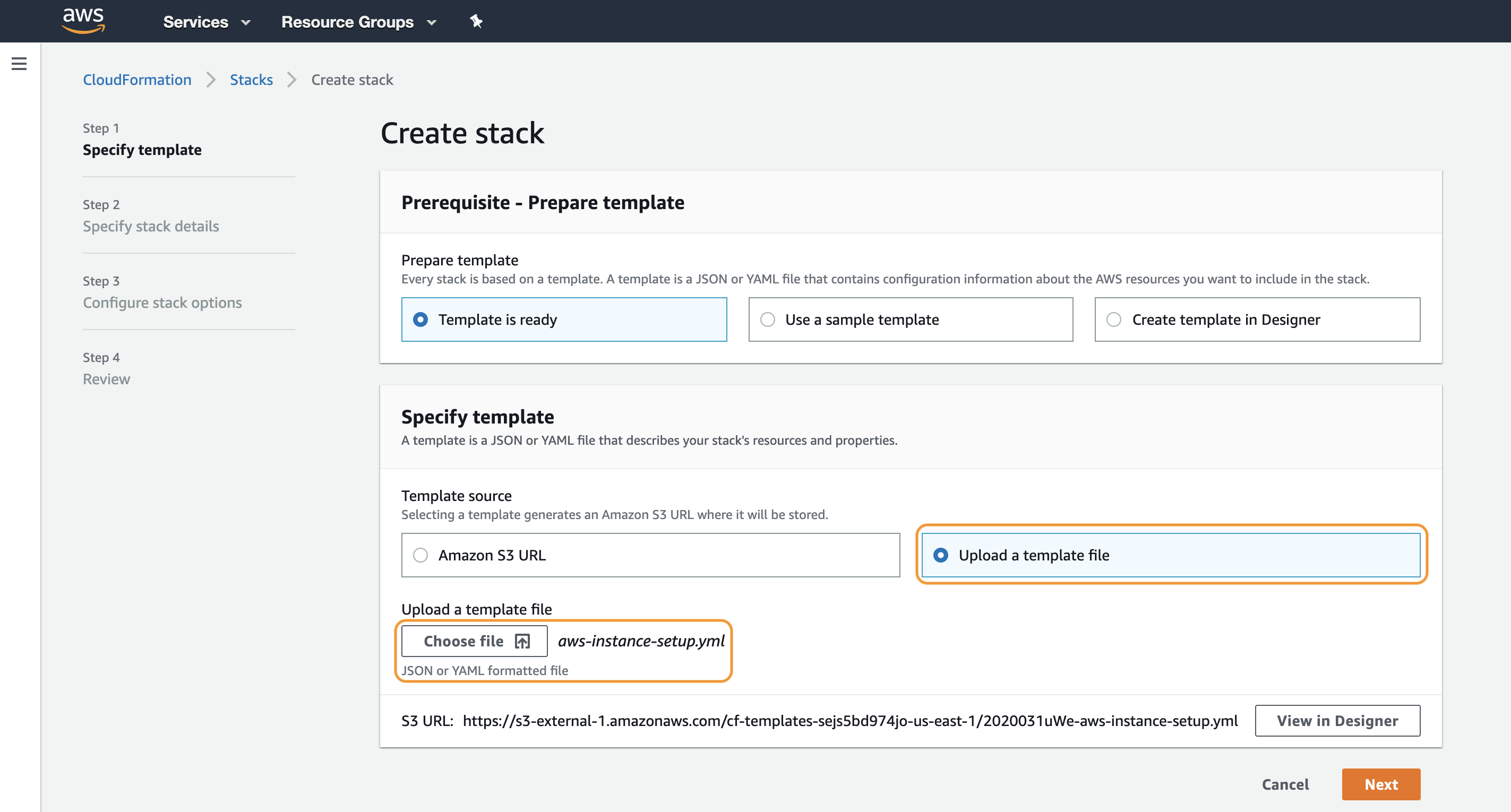
In the Specify stack details page, specify a Stack name. Click Next.
The stack name must:
Only contain alphanumeric characters and hyphens,
start with an alphabet, and
not exceed 128 characters.
In the Configure stack options page, use the default configuration, and click Next.
Review your stack details on the Review page, click the acknowledgment and then click Create stack.
When the creation process is complete, your stack will be displayed on the CloudFormation page.
You can click on the stack to view the details about the stack. The Resources tab displays the various components that are part of aws-instance-setup.yml. The Template tab displays the permissions defined in the template.
In the Netskope UI, confirm that a cross account role with permissions is created in each AWS account. Click Add Accounts.
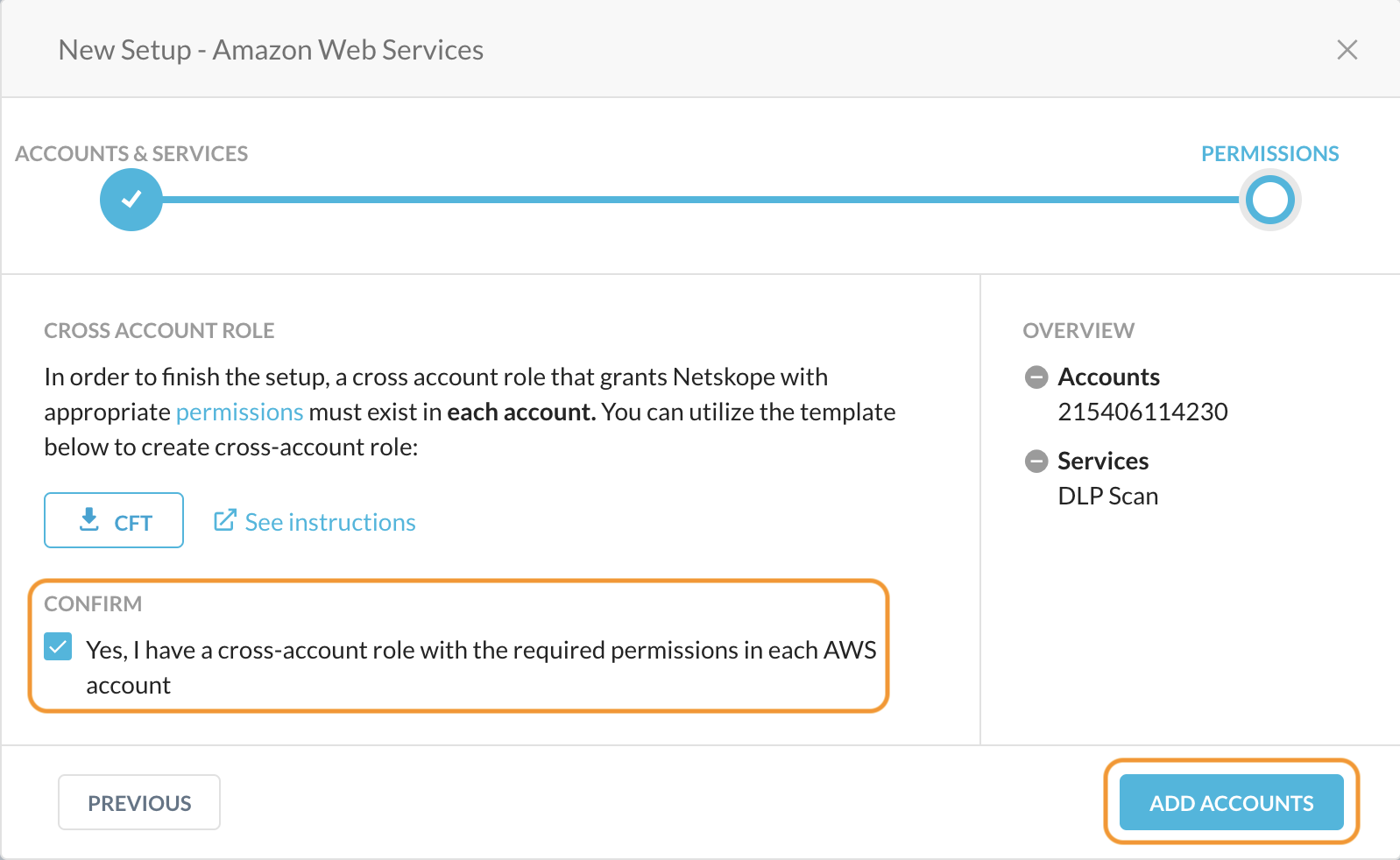
Netskope adds the AWS accounts to the Settings > API-enabled Protection > IaaS page. The page also displays the services that are enabled for each account.
What happens in the process?
Netskope assumes an IAM role which enables Netskope to create, update and delete trails and scan S3 buckets for log files. In this case, the CFT aws-instance-setup.yml requires the following permissions.
AWS Permissions for UEBA | Purpose |
|---|---|
cloudtrail:CreateTrail | Creates a trail that specifies the settings for delivery of log data to an Amazon S3 bucket. |
cloudtrail:UpdateTrail | Updates trail settings that control what events you are logging, and how to handle log files. |
cloudtrail:DeleteTrail | Deletes a trail. |
cloudtrail:StartLogging | Starts the recording of AWS API calls and log file delivery for a trail. |
cloudtrail:StopLogging | Suspends the recording of AWS API calls and log file delivery for the specified trail. |
cloudtrail:GetTrail | Returns settings information for a specified trail. |
cloudtrail:GetTrailStatus | Returns a JSON-formatted list of information about the specified trail. Fields include information on delivery errors, Amazon SNS and Amazon S3 errors, and start and stop logging times for each trail. |
cloudtrail:GetEventSelectors | Describes the settings for the event selectors that are configured for trail. |
cloudtrail:GetInsightSelectors | Describes the settings for the Insights event selectors that we configured for the trail. |
cloudtrail:PutInsightSelectors | Enable Insights event logging by specifying the Insights selectors that we want to enable on an existing trail. |
cloudtrail:PutEventSelectors | Configures an event selector or advanced event selectors for the trail. |
s3:CreateBucket | Creates a bucket where CloudTrail logs are to be stored. |
s3:PutBucketPolicy | Adds a policy in the S3 bucket for scanning. |
s3:DeleteBucketPolicy | Deletes the S3 bucket policy. |
s3:GetObject | This implementation of the GET operation retrieves objects from Amazon S3. |
s3:GetBucketLocation | This implementation of the GET operation uses the location subresource to return a bucket's region. |
sns:Publish | Sends a message to all endpoints to which a topic is subscribed. |
sns:Unsubscribe | Deletes a subscription. |
sns:Subscribe | Prepares to subscribe to an endpoint by sending the endpoint a confirmation message. |
sns:ConfirmSubscription | Verifies an endpoint owner's intent to receive messages by validating the token sent to the endpoint by an earlier Subscribe action. |
sns:SetTopicAttributes | Allows a topic owner to set an attribute of the topic to a new value. |
sns:ListTopics | Returns a list of the requester's topics. |
sns:CreateTopic | Creates a topic to which notifications can be published. |
sns:DeleteTopic | Deletes a topic and all its subscriptions. |
sns:GetTopicAttributes | Returns all the properties of a topic. |
Create a Behavior Analytics Policy
You can setup Rule-Based or Machine Learning Based policies by going to Policies > Behavior Analytics. To learn more: Behavior Analytics Policies.