Adding Exceptions
A steering configuration steers traffic to the Netskope cloud. By specifying exceptions in a steering configuration you can send traffic from a selected source (e.g., apps, domains, etc.) directly to their respective destination and bypass the Netskope cloud. For example, in an environment that uses a full tunnel VPN setup, you might want to send specific traffic to the respective VPN gateway directly instead of the Netskope cloud. This article provides insight on adding various exceptions to a steering configuration.
To better understand exceptions, Netskope recommends seeing the following articles:
Steering Exception Guidelines
When creating exceptions, consider the following:
Ensure you have administrator privileges to your Netskope account.
OU and User Group based exceptions cannot be applied when the Netskope Secure Web Gateway uses the cookie-surrogate feature to get user identity.
In the case of GRE and IPSec deployments, the Netskope Secure Web Gateway gets the user identity with the help of the Netskope Client (if installed and enabled), or through SAML authentication. If by chance the traffic arrives before the user identity is known to the Netskope Secure Web Gateway, OU and User Group based exceptions cannot be applied.
If the user identity is not known to the Netskope Secure Web Gateway, the default exception configuration will be applied.
Exception Traffic Logs
By default exception traffic is not logged in Skope IT Events. If you prefer to see exception traffic in Skope IT, you must enable it on the Steering Configuration page.
Supported Exceptions
The following are the supported exceptions:
Exception Type | Dynamic Steering Enabled | Dynamic Steering Disabled | ||
|---|---|---|---|---|
On-Prem | Off-Prem | Cloud Apps | All Traffic | |
Y | N | Y | Y | |
N | Y | N | Y | |
Y | Y | Y | Y | |
Y | Y | Y | Y | |
N | Y | N | Y | |
Y | Y | Y | Y | |
Y | Y | Y | N | |
Y | Y | Y | Y | |
Application
Organizations that use home grown applications can use the Application exception to bypass traffic from their custom app definitions. App definitions allows you to add custom apps, connectors or private apps. To learn more about creating App Definitions, see App Definition.
Adding an Application Exception
To add an application exception:
Go to Settings > Security Cloud Platform > Steering Configuration.
On the Steering Configuration page, click
 for the steering configuration you want to add exceptions to.
for the steering configuration you want to add exceptions to.Click View Exceptions.
In the Exceptions tab, click New Exception and then Application.
In the New Exception window:
Exception Type: Choose Application and select applications from the dropdown list. You can also search for applications.
Action: Choose one of the following actions.
Bypass: Choose to bypass the selected apps, sending all traffic straight to the destination. This is the default action.
Bypass, except for DNS traffic: If you enabled the Steer DNS traffic option and selected an application that includes port 53 (the standard port for DNS), choose to bypass the selected apps, sending all traffic except DNS traffic to the destination.
Notes: Optionally, enter comments or notes for the exception.
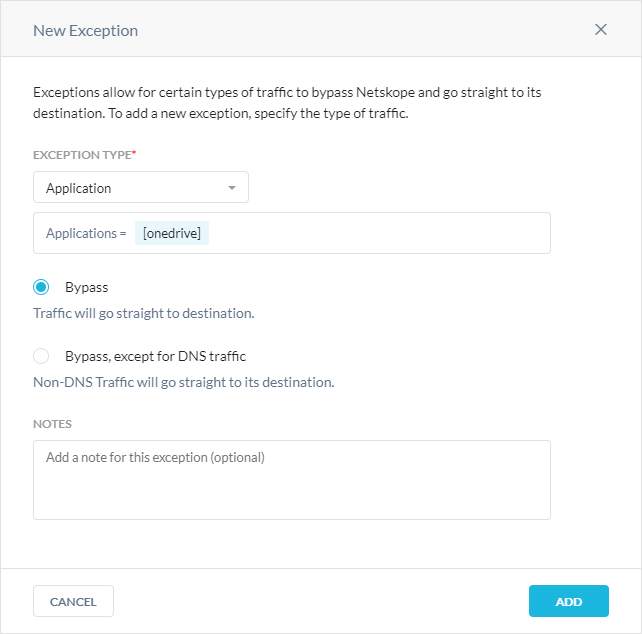
Click Add.
Category
A category defines a collection of destinations (websites) that serve similar types of content. For example, the Art category is a collection of websites that contain creative art judged solely for its intellectual or aesthetic components. When you select the Art category as an exception, traffic to all destinations (websites) in this category bypasses the Netskope cloud and goes directly to their respective destinations.
To identify whether a session belongs to a bypass category, the Netskope Client sends a few initial packets to the Netksope cloud. Hence, you might observe a few packets being forwarded to the Netskope cloud. After confirming the category, the Netskope Client bypasses the traffic locally on the user's device.
Note
If dynamic steering is enabled, category exceptions aren't available for on-premises devices.
Adding a Category Exception
To add a category exception:
Go to Settings > Security Cloud Platform > Steering Configuration.
On the Steering Configuration page, click
 for the steering configuration you want to add exceptions to.
for the steering configuration you want to add exceptions to.Click View Exceptions.
In the Exceptions tab, click New Exception and then Category.
In the New Exception window:
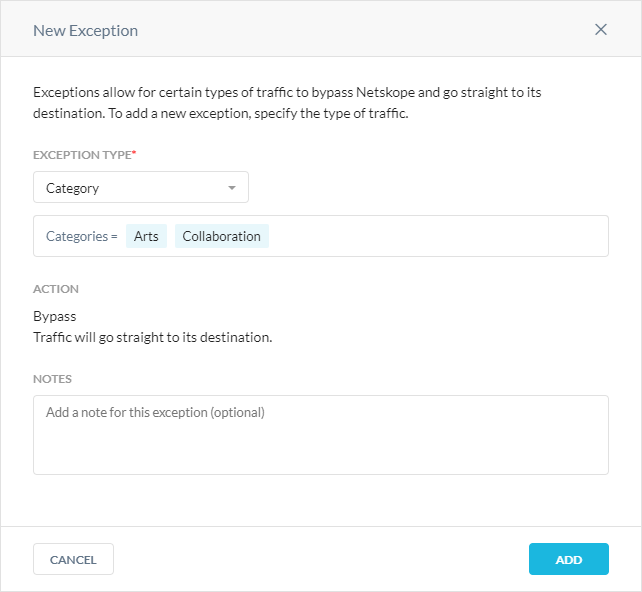
Click Add.
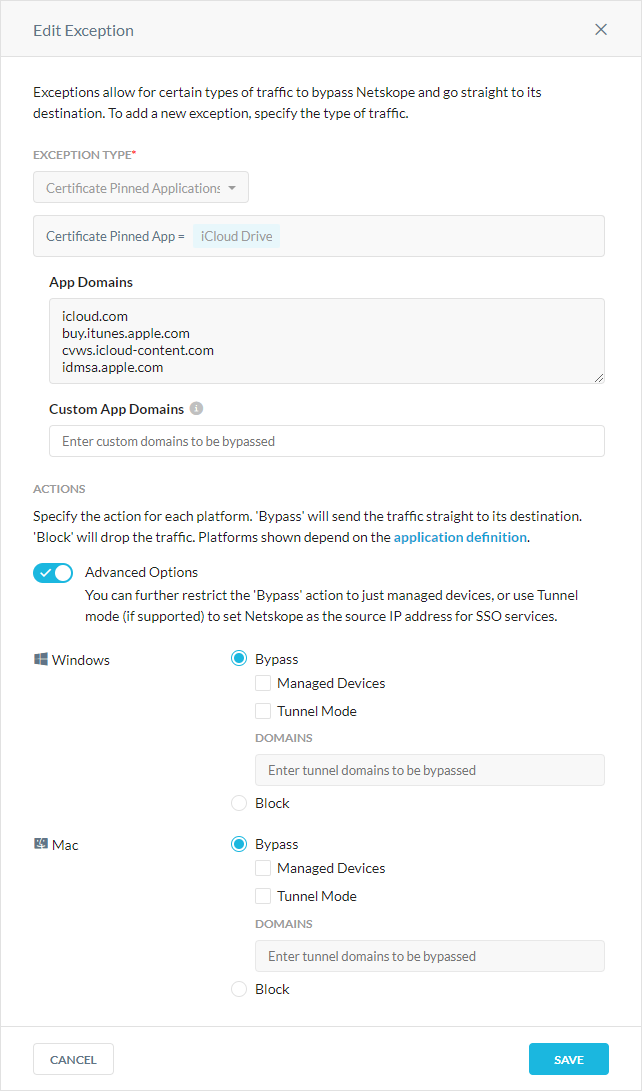
Certificate Pinned Applications
By adding applications as a certificate pinned application exception, the traffic from such applications is bypassed by Netskope cloud. A pinned app stores the public certificate or key of its destination website and presents it to Netskope cloud. When contacting the destination website/server, Netskope cloud verifies the pinned certificate with the server certificate. If they are validated, Netskope cloud bypasses traffic from the pinned application.
Adding a Certificate Pinned Application Exception
To add a certificate pinned app exception:
Go to Settings > Security Cloud Platform > Steering Configuration.
On the Steering Configuration page, click
 for the steering configuration you want to add exceptions to.
for the steering configuration you want to add exceptions to.Click View Exceptions.
In the Exceptions tab, click New Exception and then Certificate Pinned Application.
In the New Exception window:
Exception Type: Choose Certificate Pinned Application and select any predefined or custom certificate pinned applications you want to create exceptions for. Click
 to view the predefined and custom certificate pinned apps on the Certificate Pinned Apps page. You can also click the + icon to create a new certificate pinned app.
to view the predefined and custom certificate pinned apps on the Certificate Pinned Apps page. You can also click the + icon to create a new certificate pinned app.Custom App Domains: These are domains used by the application to send traffic from the managed device. Enter each domain separated by a comma. Netskope doesn't support wildcard domains (e.g., *.example.com) for certificate pinned applications but bypasses the subdomains of the domain entries. You must enter specific domain names, such as example.com, drive.example.com, mail.example.com, or *. Each domain is matched against the destination hostname using suffix matching. For example, the domain name "example.com” matches the hostname “mail.example.com” but not “mail.1example.com”. * matches any hostname.
If the destination hostname of the certificate pinned app traffic matches the Custom App Domains definition, the traffic is bypassed. If you unselect Tunnel Mode, the traffic is bypassed locally; whereas, if you select Tunnel Mode and the hostname matches domains via suffix matching (* matches all), the traffic is tunneled and bypassed on the Netskope proxy.
Note
You must contact your Netskope Sales Representative to enable this field. Once enabled, you must explicitly populate the domains for all custom cert-pinned apps, or they will cease operation until configured.
Actions: You can choose to bypass or block traffic per platform.
Note
There are separate platforms options to add a new application for Android and Chrome OS. When adding a certificate pinned application, use:
Domain-based configuration for Android 9 or lower.
Process-based configuration for Android 10 or higher.
Advanced Options: (Only available for Windows and Mac devices) Enable for the following granular control.
Bypass + Direct: Bypass the configured apps / domains directly to the destination.
Bypass + Tunnel: The client tunnels the traffic from apps / domains but the Netskope proxy will bypass it. This option is useful for domains associated with an SSO authentication service, since these services use the source IP of the Netskope cloud to determine if access to the cloud app is protected by Netskope.
Bypass Managed Devices + Direct: The client will bypass the app only if the device is managed, per the Device Classification policy, but will otherwise block it.
Bypass Managed Devices + Tunnel: The client will tunnel (to be bypassed by Netskope proxy) only if the device is managed, per the Device Classification policy, but will otherwise block it.
Block: The mode and other options are not applicable and the client blocks all the app traffic.
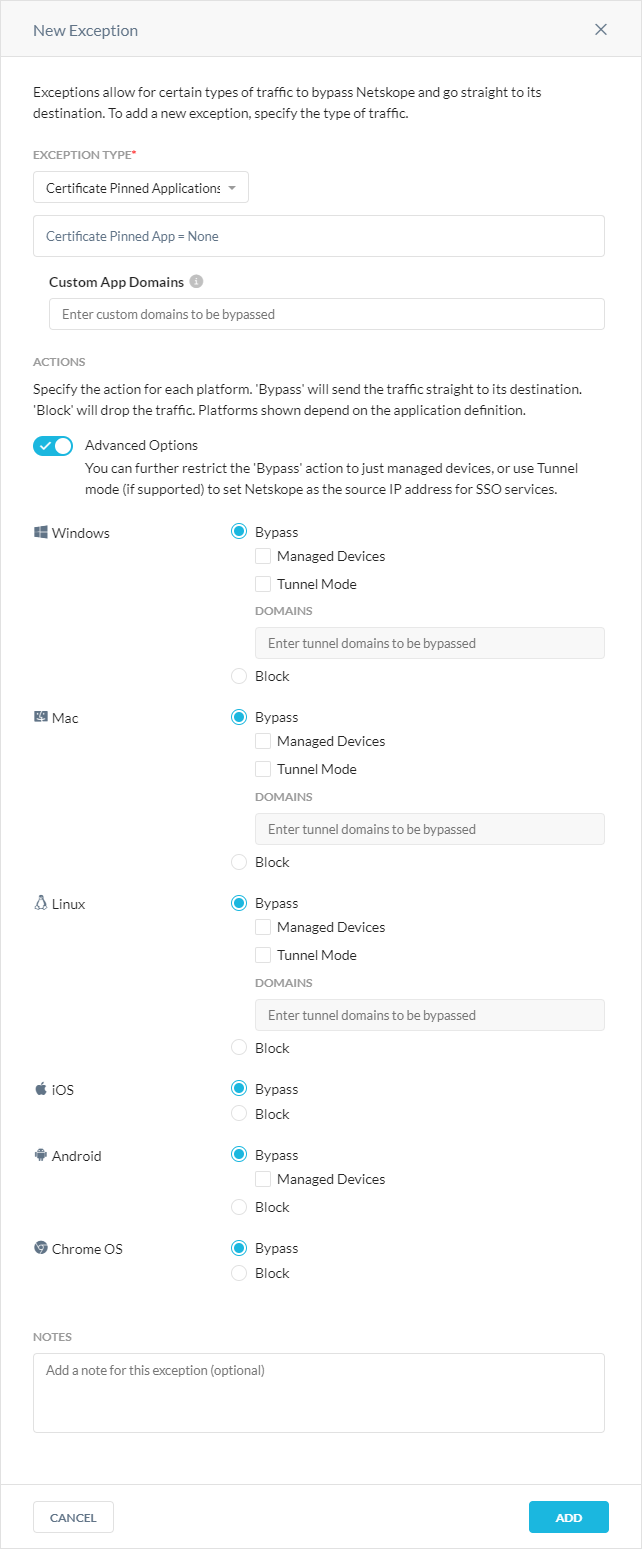
Viewing Domain Exceptions for Predefined Certificate Pinned Applications
On the Exceptions page, you can see the predefined and custom certificate pinned applications that are bypassed from the Netskope cloud for your steering configuration. To see a list of all predefined certificate pinned application exceptions: Certificate Pinned Applications.
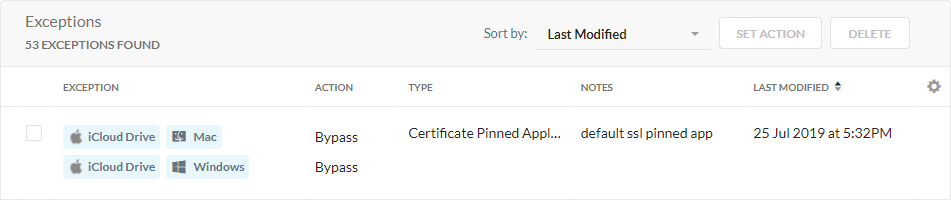
You can click the certificate pinned application exception to edit the bypass settings and view a list of the default App Domains bypassing Netskope.
Domains
Domain exception is used to bypass traffic to and from domains as configured in the exception. A common reason to add domain exceptions is to bypass traffic from domains that are used for software updates, such as adding domains used to upgrade Macbooks with macOS updates.
Note
The default exception list includes common domains (as wildcard entries) that are used for software updates. If a software / app update is interrupted ensure that the domain used for update is added to the exception list.
Adding a Domain Exception
To add a domain exception:
Go to Settings > Security Cloud Platform > Steering Configuration.
On the Steering Configuration page, click
 for the steering configuration you want to add exceptions to.
for the steering configuration you want to add exceptions to.Click View Exceptions.
In the Exceptions tab, click New Exception and then Domains.
In the New Exception window:
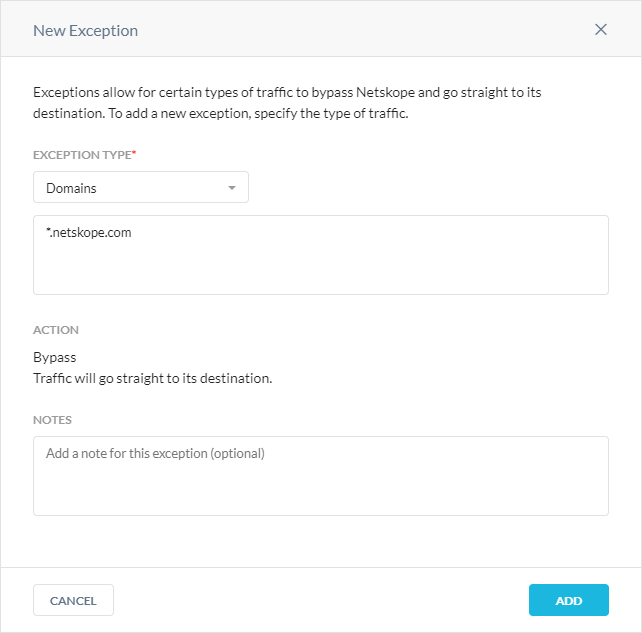
Exception Type: Choose Domains and enter the domains you want to create exceptions for. You can enter multiple domains separated by comma. You can enter them either as Fully Qualified Domain Name (FQDN) or wildcard names. When you trust a domain and want to bypass all its traffic, you can add the specific domain as a wildcard entry. Wildcard domains (e.g., *.example.com) include the root domain and all subdomains.
Wildcard Pattern
Matches
Does Not Match
*.netskope.com
netskope.com
www.netskope.com
docs.netskope.com
netskope.com
netskope.com
www.netskope.com
Action: All traffic bypasses the Netskope cloud and goes straight to its destination. You can’t modify this field.
Notes: Optionally, enter comments or notes for the domain exception.
Click Add.
DNS
The DNS exception allows you to bypass DNS traffic.
Adding a DNS Exception
To add a DNS exception:
Go to Settings > Security Cloud Platform > Steering Configuration.
On the Steering Configuration page, click
 for the steering configuration you want to add exceptions to.
for the steering configuration you want to add exceptions to.Click View Exceptions.
In the Exceptions tab, click New Exception and then DNS.
In the New Exception window:
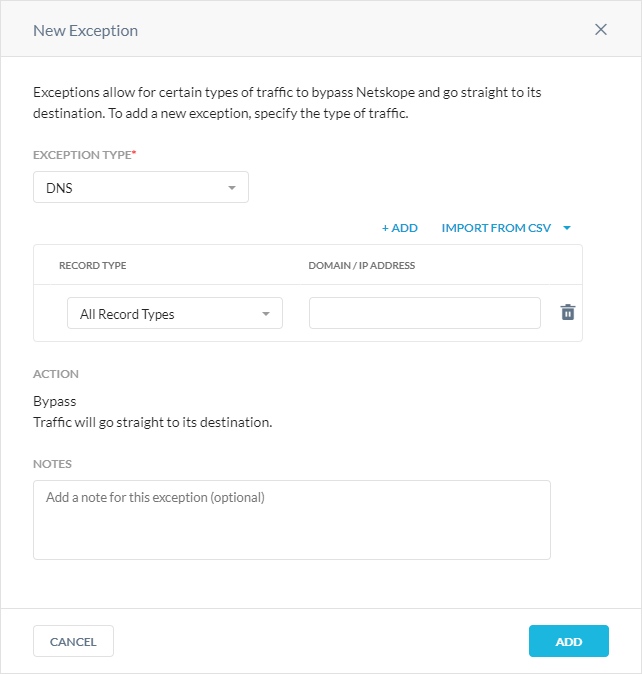
Exception Type: Choose DNS and enter the domains you want to create exceptions for.
For each domain, you must specify the Record Type or choose All Record Types. You can click + Add to add more domains or click Import From CSV to upload a CSV file (the maximum upload is 8 MB).
Note
If the Record Type is PTR, you must enter IP addresses or IP ranges.
Action: All traffic bypasses the Netskope cloud and goes straight to its destination. You can’t modify this field.
Notes: Optionally, enter comments or notes for the DNS exception.
Click Add.
Destination Location
Destination Location exception bypasses traffic sent to specific destinations as defined in the network location profile. When installing Netskope Client along with 3rd party apps, like a VPN application, you will need to add exceptions to bypass VPN traffic and send it directly to the respective VPN gateway. The Destination Location exception allows you to add target destinations either as Fully Qualified Domain Name (FQDN) and/or public IP address.
Adding a Network Location Exception
Before adding destination location exceptions, you must add network location objects. A Network Location is a profile with a list of public IP addresses.
Go to Policies > Network Location.
On the Network Location page, click New Network Location and select Single Object or Multiple Objects.
Select Single Object, if you are adding a small set of destinations manually.
In the Add Network Location pop-up window, enter the destination address (IP address/range or CIDR network). Click the + icon to add additional addresses. Click Next to continue.
Give a name for this network location. You will need this when adding the exception in steering configuration.
Select Multiple Objects, if you are adding a large set of destinations via a CSV file.
In the Upload Network Locations pop-up window, select the CSV file (max size 8 MB) with the list of destination addresses. The CSV file must have entries in the following format:
[Net Location Name], [IP Address 1], [IP Address 2], , ,For example: Location1, 11.2.3.4, 12.3.5.125/16
Click Upload.
Adding a Destination Location Exception
To add a destination location exception:
Go to Settings > Security Cloud Platform > Steering Configurat.
On the Steering Configuration page, click
 for the steering configuration you want to add exceptions to.
for the steering configuration you want to add exceptions to.Click View Exceptions.
In the Exceptions tab, click New Exception and then Destination Locations.
In the New Exception window:
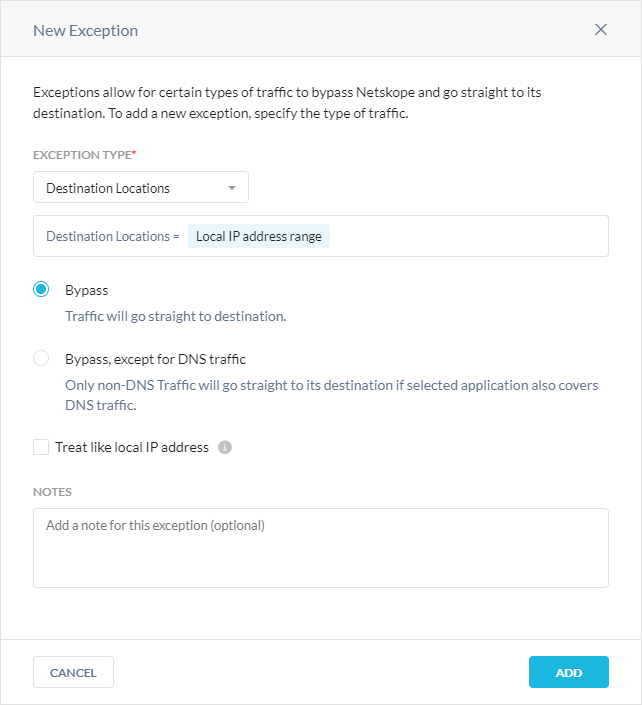
Exception Type: Choose Destination Locations and enter the destinations you want to create exceptions for.
Bypass: Bypass all the traffic for the destination location.
Bypass, except for DNS traffic: Netskope Client bypasses non-DNS traffic and only tunnels DNS traffic to the Cloud Firewall.
Note
You can only see this option if you have the Cloud Firewall license.
Treat like local IP address: Select if you want Netskope Client to consider this traffic local so it never sends the traffic within the tunnel, like a private IP address in RFC 1918.
Notes: (Optional) Enter comments or notes for the Destination Location exception.
Click Add.
Source Location
Source location exception bypasses traffic from a specific set of address (treated as source of traffic) as defined in the network location profile.
To learn about creating source network location, see Adding a Network Location Exception.
To learn about a network location as the exception, follow the steps described for Adding a Destination Location Exception
Source Countries
The Source Countries exception allows you to bypass traffic from specific geo-locations.
Adding a Source Country Exception
To add a source country exception:
Go to Settings > Security Cloud Platform > Steering Configuration.
On the Steering Configuration page, click
 for the steering configuration you want to add exceptions to.
for the steering configuration you want to add exceptions to.Click View Exceptions.
In the Exceptions tab, click New Exception and then Source Countries.
In the New Exception window, for Source Countries, select the source countries you want to bypass.
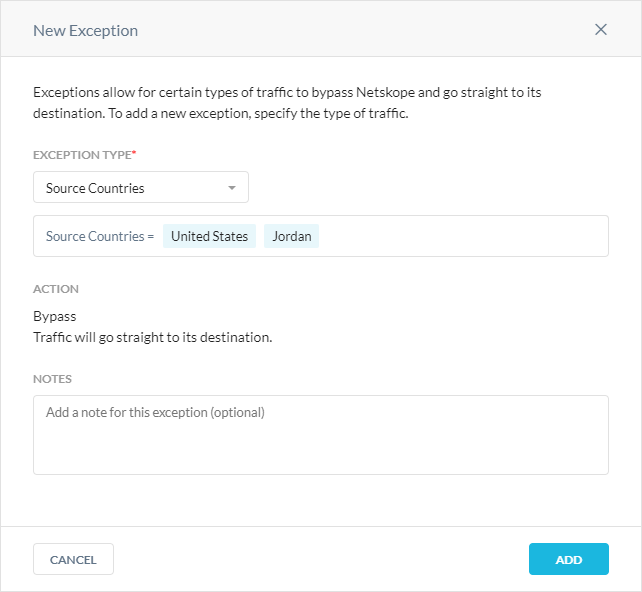
Click Add.