New Features And Enhancements In Release 106.0.0
Here is the list of the new features and enhancements.
Support App Exclusion In Application Filter
UEBA supports a setting for excluding applications for predefined and custom UEBA policies. This allows selection of specific applications to exclude from evaluation for predefined and custom UEBA policies.
Incident Detail Page Update
The summary and event timeline detail is enhanced for several UEBA detections. This provides additional context for the detection to assist with forensic investigation and remediation.
UEBA UCI threshold alert
A new alert allows setting the User Confidence Index (UCI) threshold value for all users. When the UCI for any user drops below the specified value configurable from Incidents > Behavior Analytics, a UEBA alert is triggered in Skope IT showing the UCI value in the alert details. To learn more: Behavior Analytics User Confidence Index
Dedicated Inline Connector For Generative AI Apps
Added the following four new App Connector for Apps with Generative AI capabilities:
Google Bard
Microsoft Bing (This App also covers the Bing Chat AI functionality in addition to larger Bing Search functionality.)
Beautiful.ai
Perplexity AI
Critical activities like Post, Upload and Download are covered with these connectors to monitor and prevent data exfiltration.
InstanceID improvement For Box
Improved instance ID detections for upload and download API based operations made to Box application.
AuthProxy Authentication support
With auth proxy endpoint URL configuration on IDP side, endpoint URL is configured to point Netskope auth proxy URL instead of actual ACS URL. As no other changes are done as part of this configuration, the ACS URL can be maliciously modified to default MS URL and bypass Netskope rproxy control.
AuthProxy Authentication for Office Portal now supports optional resigning feature at each IDP with Netskope Tenant certificate, to enforce Netskope security check and prevent MITM attack.
Renamed App Tag Constraint
The App Tag criteria for Real-time Protection was renamed to CCI App Tag. A similar change was made for Skope IT, where the Tag filter was renamed to CCI App Tag.
Note
This change helps differentiate between the usage of CCI App Tags applied at the Application Level from the CCI page, and App Instance Tags used to tag a specific instance for an app and are applied through App Instance profiles.
Added Support For Cert Pinned Apps
Added four new Cert pinned apps to the list, these are associated with Windows OS platform:
Adobe Acrobat Reader (Fill & Sign)
Blizzard Online Games
Signal
Windows Store
App Type Tagging
The following changes have been made to CCI App Type default tag mappings:
Deprecated Departmental tag
Enterprise is mapped to apps that qualify the following criteria:
These apps are used by a minimum of 1000 users across Netskope customer base.
These apps do not belong to one of these Consumer categories:
Arts
Automobile
Consumer
Chat
IM and other communication
Dating
E-Commerce
Education Entertainment
Fashion
Financial News
Food & Drink
Forums
Health & Nutrition
Insurance Investors & Patents
Job Search Kids
Knowledge Management
Lifestyle
News and Media
Nursing Personal Sites & Blogs
Pets
Philanthropic Organisation
Photo Sharing
Professional Networking Real Estate
Science
Search Engines
Shopping
Social
Streaming & Downloadable Audio
Translation Travel Trading & Investing Logistics
These apps have enterprise/multi-user licensing.
All other apps are tagged as Consumer
Application Category Modifications
Updated the application category for Google Maps from Consumer to Technology.
Google Cloud Platform (GCP) App Rename
GCP Apps are renamed as follows:
Google Cloud Storage renamed to GCP Storage
Google Firebase Storage renamed to GCP Storage for Firebase
Renamed Vulnerabilities & Exploits Section
The Vulnerabilities & Exploits section in CCI Application Information page has been enhanced and renamed to Attack Surface Management. It will now highlight results of more than 50 passive vulnerability scans including OWASP Top 10 Vulnerabilities, in addition to information on recent breaches.
ITIN Entity Update
Updated Taxpayer ID Numbers (US; "ITIN") Entity to support groups from '50' to '65' based on the current ITIN definition.
DLP Entity Filter tooltips update
Updated UI tooltips for Unlikely Matches and Common-Sense Filters under the Entities tab of DLP.
Medical Conditions Entity
The "Medical Conditions (English)" Entity has been completely overhauled in order to reduce false positives caused by matching medications. For example, "acetaminophen" and "Tylenol" and anatomical references (like, "pulmonary" and "jugular vein") to improve detection of more natural ways of referring to common ailments.
Remove Medical Rules from PII-type DLP Profiles
In order to better delineate our predefined PHI and PII DLP Profiles, Medical-related Rules (PHI) were removed from the following PII Profiles:
DLP-PII
US Personally Identifiable Information
Australia Personally Identifiable Information
Singapore Personally identifiable Information
CCPA/CPRA
Updated Driver License Number Terms Entity
Added more plurals terms support for driver licenses (for example, "driver licenses"), as well as specific terms "dls#", "cdl#", and "cdls#".
Predefined Entity Validation
Custom Entities (defined on the Entities page) that reference a single predefined Entity will now inherit the predefined Entity's default validators and filters.
If the Entity Modifier feature is enabled, you will now also have the option to change or remove the inherited filters that are applied to their new custom Entity. Netskope recommends using the default filters that apply to the predefined entity.
Support For Entity Obfuscation
You can now choose to obfuscate the matched content for custom entities created using the Entities tab in the UI.
The obfuscated content will be stored in the customer managed forensic folder and seen in the "Preview" and "Preview File" sections of an incident in the WebUI. Entity Obfuscation requires the Entity modifier feature to also be enabled on the tenant.
For customers using DPOP, the appliance versions will need to be upgraded to Release 106 to leverage this feature.
Note
This feature is currently in Controlled GA. Contact your Sales Representative or Support to enable this feature.
Alert And Event Rename
Endpoint DLP events and alerts previously used both "MacOS" and "macOS" for the OS field. This has been made consistent and will always report "macOS".
Endpoint DLP Process Rename
The application name for the Endpoint DLP application is changed to Netskope Endpoint DLP on macOS.
Blocking MTP/PTP Android Devices
Endpoint DLP agent for macOS can now block Android phones in both Media Transfer Protocol (MTP) and Picture Transfer Protocol (PTP) modes.
TLSv1.3 For EPDLP Client
The Endpoint DLP agent now requires TLS1.3 to communicate with datacenter APIs.
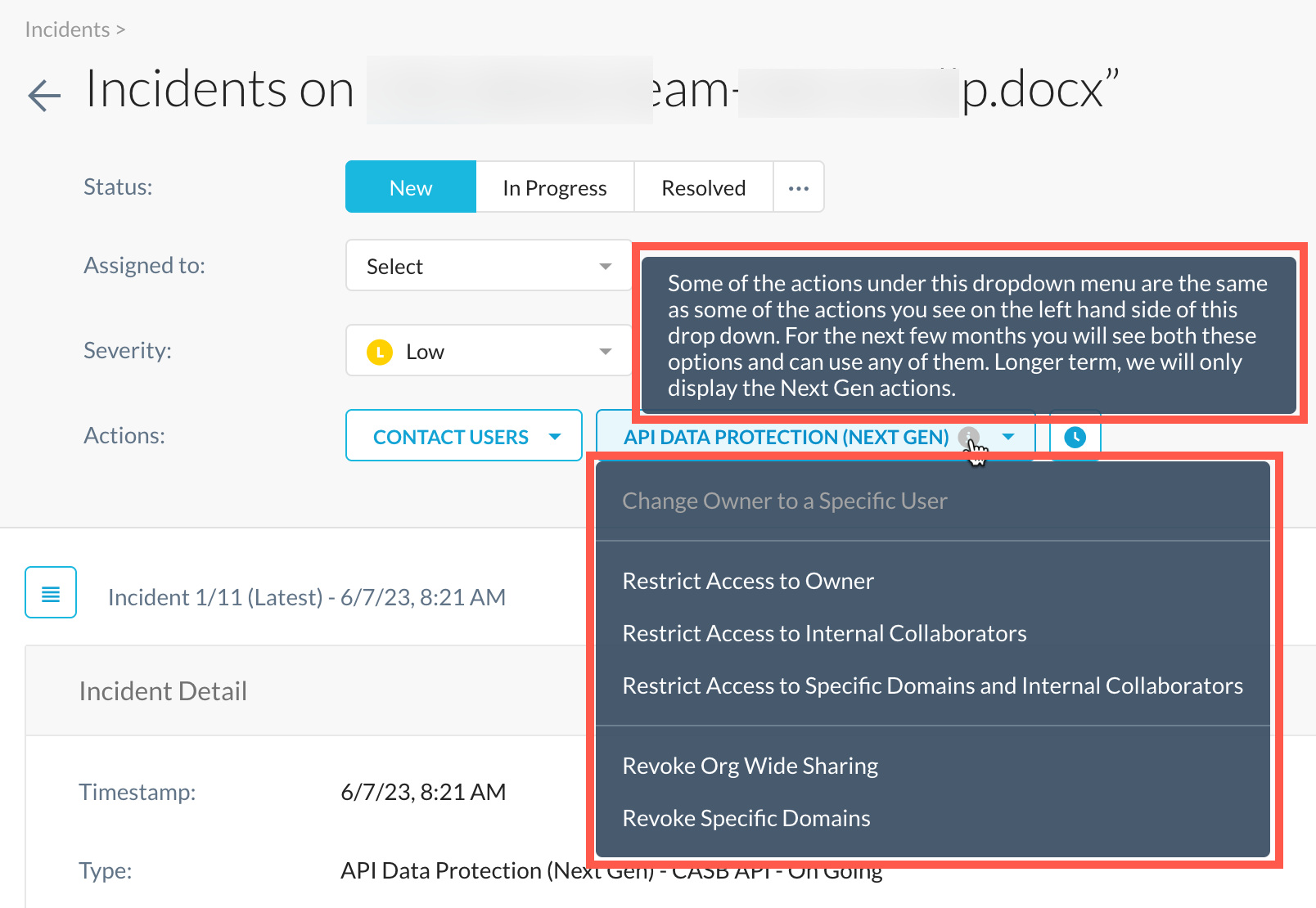
Remediation Actions On Incident Page
Classic API Data Protection supports manual remediation. The same support is now extended to Next Generation API Data Protection. An administrator can manually take a remediation action on an incident from the Incidents > DLP page. The available actions are:
Change owner to a specific user
Restrict access to owner
Restrict access to internal collaborators
Restrict access to specific domains and internal collaborators
Revoke organization-wide sharing
Revoke specific domains
Note
To know the definition of each of the remediation actions, see Create a Next Generation API Data Protection Policy (step 7).
For apps that support remediation actions, see Next Generation API Data Protection Feature Matrix per Cloud App.
You can navigate to the Incidents > DLP page, click an incident, under Actions > API Data Protection (Next Gen), choose the remediation actions.
 |
Important
Some of the actions under this drop-down menu are the same as some of the actions you see on the left hand side of this drop down. For the next few months you will see both these options and can use any one of them. In the long term, the UI will display the Next Generation actions only.
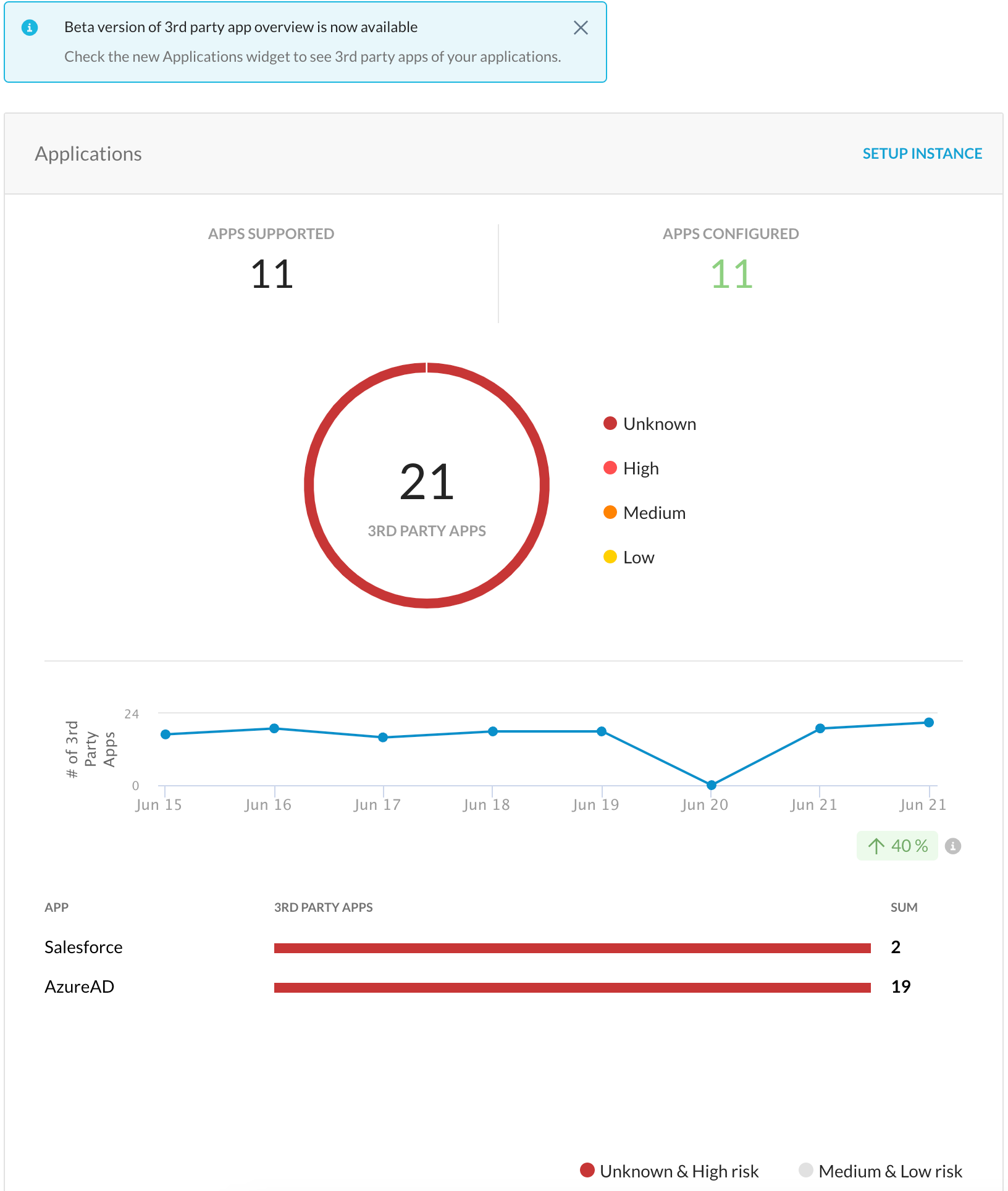
Summary of 3rd-Party Connected Apps
Starting this release, Next Generation SSPM shows a summary of 3rd-party connected apps on the Next Generation SSPM Overview page. Connected app is mechanism to link a 3rd-party application to a SaaS application platform using OAuth for authorization. For example Box for Salesforce is a connected app that allows integration between Salesforce and Box.
To view the 3rd-party connected apps, navigate to API-enabled Protection > SECURITY POSTURE (NEXT GEN) > Overview, then view the Applications widget. Clicking the donut chart takes you to the Inventory > Resources page to list the 3rd-party connected apps. To learn more: View Security Posture Overview
 |
Note
This is a beta feature. Though the widget displays 4 risk levels, all 3rd-party connected apps are currently categorized under the Unknown risk level. In a future release, they will be categorized under appropriate risk levels.
Support for Categorization of SSPM Rules & Findings on MITRE ATT&CK for SaaS and Security Domains
Starting this release, Next Generation SSPM now supports categorizing SSPM rules and findings on MITRE ATT&CK for SaaS and security domains.
MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is a globally recognized framework and knowledge base that helps organizations understand and categorize the tactics, techniques, and procedures (TTPs) used by cyber adversaries during various stages of a cyberattack.
In the context of Security Operations (SecOps), there are several well-known domains or categories that are commonly addressed to ensure a comprehensive security posture. These domains cover various aspects of security operations and help organizations in managing and responding to security incidents effectively.
To accommodate these new rules and findings, Next Generation SSPM has introduced new categories under the security posture policy wizard:
MITRE ATT&CK
Domain
Netskope Best Practices - These are rules recommended by Netskope for supported SaaS apps.
In addition, you can create a custom rule and include them as part of the above new categories.
To learn more: Next Generation SaaS Security Posture Management Policy Wizard
TLS Decryption
This feature provides customers the ability to use their on-premises hosted HSM/key manager to sign the certificate for TLS decryption of real-time traffic in Netskope Cloud. <Please refer online help for more details.>
Transaction Events Format 2 and 3
Transaction Events Format 2 and Format 3 are now GA and available for all tenants.
A total of 86 new fields have been added to the following topics:
SSL Policy: SSL Policy evaluation details, including action and policy name
SSL Certificate : Details of the remote server certificate validity
SSL Engine: Details on the analysis performed by the SSL Engine and SSL errors management
Errors found in SSL negotiation
Action performed and reason
The TLS and cipher versions
JA3 and JA3S fingerprints
Connection: More details added on layer 3/4 informations
More HTTP details added:
XFF headers
details on CONNECT requests
HTTP full URL, HTTP url path and HTTP version
Application and File topics: application details including activity, instance and user detection
General: general error field and user local time added
Real Time Policy: Realtime Policy evaluation details, including action and policy name
To learn more: Transaction Event Fields
File Type Feature
When admins login to the Web UI, a new banner about upgrading policies to the new file type feature and the expected migration timeline is visible. The file type feature provides more granular file type options to choose from and applies true file type detection.
To learn more: File Type Detection
Disabled Longest Prefix Match For Custom URL Lookup
We can now disable longest prefix match in NG-SWG when matching incoming URLs against URL lists. As a result, the incoming URL will match against all URL lists with a positive match criteria. This is different from the current behavior of matching with the URL list with the longest prefix match.
Important
Disabling the longest prefix match is a fundamental change in how policy processing happens with NG-SWG. Hence, it is recommended to review the intended behavior of this feature on your policy set thoroughly before enabling this feature.
Note
This feature is currently in Controlled GA. Contact your Sales Representative or Support to enable this feature.
Extended RBI License
Notice
This is a BETA feature. Contact your Sales Engineer to enable this feature in your account.
Extended RBI is an upcoming RBI new licensing, that expands RBI support for new risk scenarios: browsing of unsanctioned cloud apps.
Extended RBI is a new license that expands the RBI offering to cover additional risk scenarios in addition to the current 'Targeted RBI' scope: i.e., additional web categories and unsanctioned cloud apps which do not require isolation of all web traffic (full isolation).
Extended RBI will protect the browsing activity and browser for corporate users accessing unsanctioned cloud apps and websites.
To learn more: Extended RBI (BETA DOCUMENTATION)
Feature Flag Value Update
Updated the default value for the enableAOACSupport feature flag from disabled to enabled. No impact for the existing tenants with the feature flag enabled.
To learn more: Netskope Client Deployment Options.
Configuration Support For IPSec
New 500Mbps tunnel bandwidth support added under maximum bandwidth selection in the IPSec configuration page.
Note
Contact your Sales Representative or Support to enable this feature.
To learn more: IPSec and Creating an IPSec Site.
API Data Protection
Remove Forensic Option From Instance Setup Page For OneDrive
Based on Microsoft's latest Terms of Service, Netskope can no longer support OneDrive as a forensic destination. Due to this, Netskope will not support this feature in any new commercial or federal Netskope DC. Fine prints:
For existing customers who are using OneDrive as a forensic destination, the feature will continue to work as expected.
For new customers, the instance setup UI for OneDrive will no longer have the forensic checkbox. New forensic OneDrive instances cannot be enabled.
For existing customers who have not enabled OneDrive as a forensic destination, cannot enable it going forward.
Existing customers using OneDrive as a forensic destination, can disable the forensic checkbox from the UI. However, once disabled, you cannot re-enable it.
To learn more: Deprecation Notice for OneDrive as a Forensic Destination.
As an alternative, Netskope recommends to use a public cloud storage (like Azure Blob, AWS S3, or GCP Cloud Storage) as a forensic destination over a SaaS storage app. To learn more: Forensics.
App Connectors
Deprecated Google Plus/Google Currents Connector
Deprecating support for Google Plus (Google Currents) app connector as the corresponding app has been deprecated by Google. To learn more: Learn about the switch from Google Currents to spaces in Google Chat
SaaS Security Posture Management v1: The SaaS Security Posture Management (SSPMv1) documentation has been deprecated. This is because SSPMv1 will be made EOL (end of life) soon. Customers who are on the SSPMv1 platform should migrate to Next Generation SSPM platform. In addition, the SSPMv1 documentation will be deprecated by June '23. Additional documentation links:
App Definitions : Improved the content and structure for Netskope App Definitions.
Creating a Firewall App Definition: Improved the content and structure on how to create Firewall app definitions.
Interoperate with Proxy: Improved content describing the workflow of this feature in Client Configuration.
Captive Portal Detection Timeout: Added content for this feature in Client Configuration.