Viewing Cloud Sandbox Analysis
Note
You must have the Advanced Threat Protection license to use Cloud Sandbox analysis.
Behavior-based analysis is a key technology for security teams to detect advanced threats. By detonating suspicious files in a controlled sandbox environment, you can record the observed malicious file behaviors and use it for forensic analysis. Netskope's cloud-based dynamic sandbox analysis engine is resistant to evasion techniques and is built on Netskope's high-performance, cloud-scale security platform to optimize threat protection.
The Netskope Cloud Sandbox engine:
Detonates files in controlled sandbox environment.
Monitors samples for a wide range of malicious behavior.
Detects evasive, zero-day malware.
Allows REST API sample submission.
You can export the indicators of compromise (IOCs) in Structured Threat Information eXpression (STIX) format so the information can be consistently exchanged with other entities. Similarly, you can export the network traffic (i.e., PCAP) generated during the analysis of the artifact. For example, the analysis might show a dropper downloading the second stage payload during execution.
You also can immediately add the hash of the detected artifact to the tenant, lookup the sample on VirusTotal, and use REST API to submit samples directly to the sandbox.
To view the Cloud Sandbox analysis:
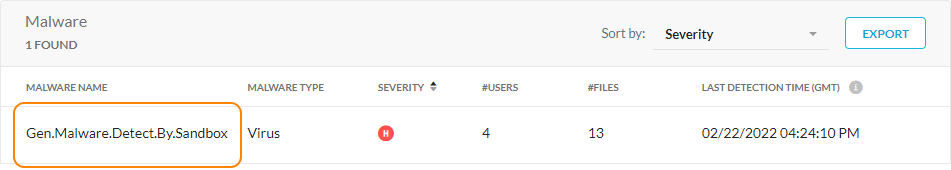
Go to Incidents > Malware.
In the Malware Name column, click the malware name to go to the Malware Details page.
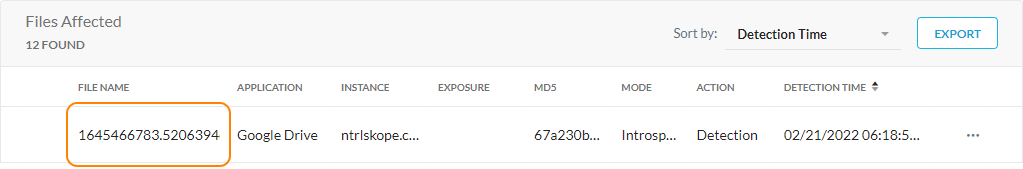
In the File Name column, click the file name to view the File Details page.
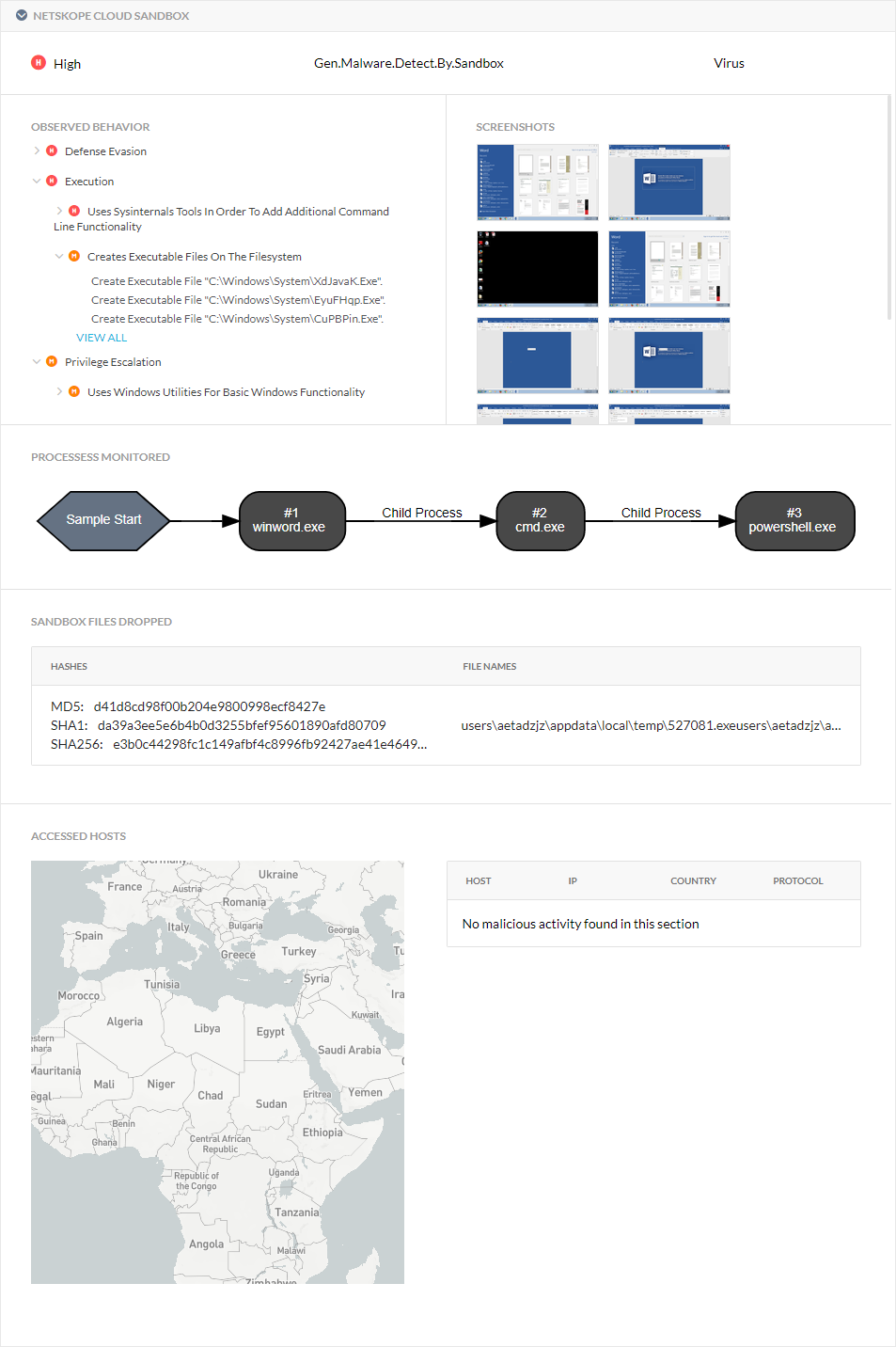
Expand the Netskope Cloud Sandbox section. The following information appears:
Observed Behavior: Shows the sample behavior observed in the tree representation of Tactics, Techniques, and Procedures (TTPs) mapped to MITRE ATT&CK® for Enterprise.
The MITRE ATT&CK framework is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. Observed behaviors in the Netskope Cloud Sandbox are mapped to the MITRE ATT&CK® framework for security teams to understand the scale and impact of an incident quickly and drive actionable mitigation measures.
Screenshots: Shows what appeared on the user's monitor during the detection process.
Processes Monitored: Shows the entire process flow of what occurred when the malware was detected.
Sandbox Files Dropped: Shows the hashes and names of the files created during the detection process.
Accessed Hosts: Shows the geolocation of the host that the sample accessed during the detection process as well as the host name, IP address, country, and protocol.