Advanced Threat Protection
Note
To enable Advanced Threat Protection, you must contact Netskope Support.
Netskope Advanced Threat Protection includes multiple detection engines that detect sophisticated zero day threats and targeted attacks. Our comprehensive, multi-engine approach ensures higher efficacy and protection against evasive threats that may be optimized to bypass some detection engines.
The Netskope Advanced Threat Protection solution includes:
Ransomware Detection and Remediation.
Advanced Threat Protection enables engines in deep scan that overcome the limitations of traditional signature-based detection techniques:
Detects unknown malware (dynamic vs reactive).
Performs dynamic analysis, which can determine indicators of compromise (IOCs) such as command and control (C2) domains, IPs, endpoint registry keys, created files, etc. IOCs can be used to detect the next occurrences of the same malware without re-analyzing the artifact.
Deep scan analysis takes aproximately 5 to 10 minutes. The patient zero is not blocked, but future occurrences of the same malware are detected immediately and can be blocked inline by threat policy.
Patient zero detection.
REST APIs for integrating into typical security operations center (SOC) workflows.
Retrohunt API provides an API that allows you to query detections by hash (e.g., MD5 and SHA-256) if the file is seen (whether malicious or benign) in traffic within the Netskope tenant. Additionally, a report can be retrieved for the detections and verdicts by the different engines. To learn more, go to Settings > Tools > REST API v2 in your Netskope tenant, and then click the API Documentation.
Sandbox file submission API. Allows submitting files and retrieving a detailed analysis report from the sandbox.
ATP alerts appear on the Malware page.
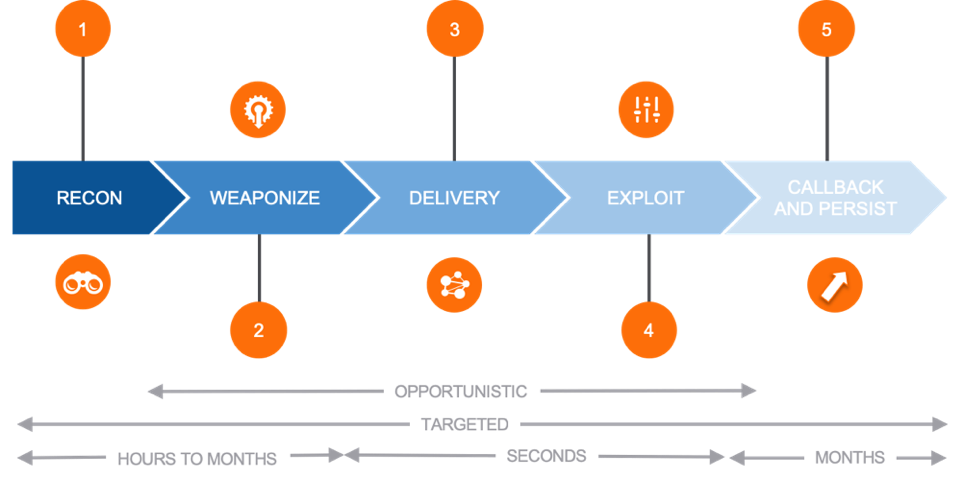
The Kill Chain & How the Cloud Affects It
The typical kill chain involves five stages:
Recon: Typically used in targeted attacks, the attackers gather intelligence about their victims. This stage can also involve social engineering (e.g., learning weaknesses of the victims that can be exploited to deliver malicious payloads). The growing adoption of cloud services gives attackers some additional entry points. In this phase, malicious actors can research cloud services used by their victims or look for publicly accessible resources.
Weaponize: The malicious actors prepare their attack vectors (e.g., develop their malicious payload). This phase also involves the preparation of the malicious infrastructure. In the original model, these preparation tasks can involve the registration of malicious domains and the staging of the exploit kits. Today, cloud services are increasingly used to distribute malware or host the C2 infrastructures (see the delivery phase), so they play an important role in this phase as well.
Delivery: The malicious payload is delivered to the designated victim. Before the cloud advent, this phase involves drive-by (targeted), watering-hole (opportunistic) attacks, or spear phishing campaigns. Today phishing pages can be served from cloud services (see the Netskope Blog), and similarly cloud services can be used to host malicious payloads. Another way to exploit cloud services in this phase is to create fake cloud application login pages (mimicking the ones used by the victims) with the only purpose to lure the victim and phish their credentials.
Exploit: The attack vector is exploited. If the attack involves a malicious executable or a bait document, the artifact is clicked by the victim, executed, and then its malicious action is performed. If the attack involves an exploit kit, the vulnerability on the endpoint (or the browser) is exploited to execute the payload after delivery. Bait documents may also connect to cloud services to evade detection where a second stage payload is delivered or a phishing page is served. See the Netskope Blog.
Callback and Persist: After the malicious payload has been executed, the malware needs to connect to its C2 (callback) to communicate with infected machines, exfiltrate information, establish a foothold for the attackers to move laterally and/or dig deeper into the organization. Again, the cloud is playing an important role in this phase, as the attackers can host the C2 infrastructure in trusted cloud services. In case of compromise of cloud services, such as AWS, attackers can move laterally across resources.
An attack can involve traditional vectors and cloud services across kill chain activities. Netskope calls these threats "Hybrid Threats".
Some phases may or may not be present. Recon and Persist are typically used for targeted attacks, where the malicious actors are more interested in establishing a deeper and consolidated relationship with their victim.
Malware & Site Types in a Kill Chain
Knowing the malware or the site type can help determine the stage of the attack. The following flowchart illustrates where the different payload or site types come into play inside the kill chain. A specific detection type can indicate if the attack is in the initial stage or if it was successful and the malware is trying to “phone home” (bot), which drive the subsequent remedial actions.
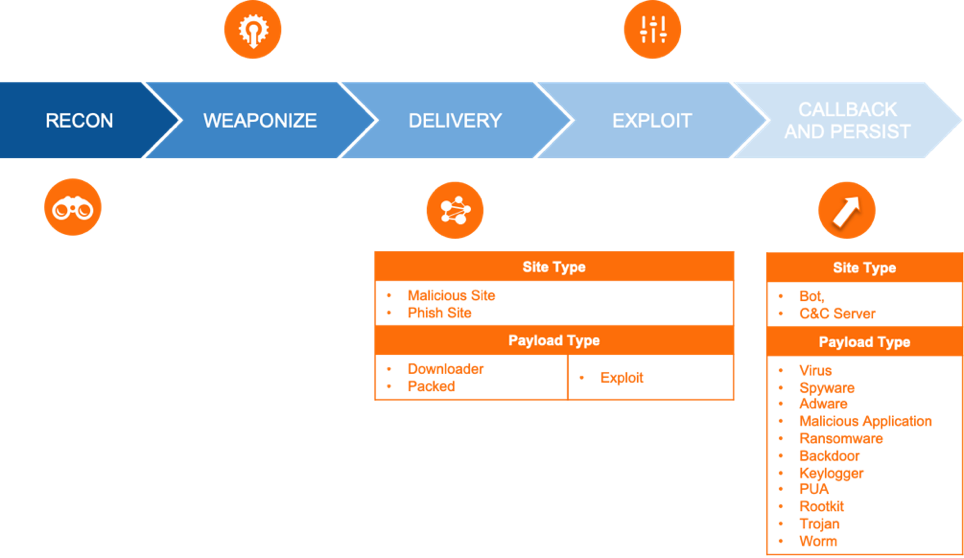
The classification of artifacts detected by the Advanced Heuristics and the Cloud Sandbox engines is still unknown at the time of the detection, so these artifacts have two dedicated categories (Advanced Heuristics and Cloud Sandbox).
ATP Terminology
Following are some helpful term definitions:
Term | Description |
|---|---|
Botnet | Network of compromised computers (bots) used by the attacker for different purposes like stealing data, launching DDoS attacks or SPAM campaigns. Bots are controlled via a central infrastructure called command and control (C2 or C&C). |
Drive-By | Attack performed by injecting the malicious content into the victim’s machine without explicit consent. This is normally achieved by redirecting the victim to the exploit kit landing pages. Even legitimate websites can be compromised to perform this attack if the attacker is able to exploit the vulnerability of injecting the malicious content. |
Exploit Kit | Malicious software used to exploit unpatched or zero-day vulnerabilities on the endpoint (e.g., browser or plugins) to inject malicious code. Exploit Kits are hosted on specific domains controlled by the attackers where users are redirected via malicious links or visiting compromised legitimate websites (drive-by). |
Heuristics Analysis | Set of rules used to detect malicious behavior without having to uniquely identify the sample responsible for it (e.g., the sample is similar to other ones known to be malicious). Netskope statically analyzes files against 3,000+ indicators. |
Sandbox | Virtual environment where the samples are executed in a controlled condition to reveal malicious behaviors even if there is no previous knowledge of the file itself. This kind of analysis is dynamic in contrast to signatures that are purely static. Malware tries to avoid sandbox detection using evasion techniques. Sandboxing is frequently used to test unverified programs that may contain a virus or other malicious code, without allowing the software to harm the host device. |
Indicator of Compromise | Indicators of compromise (IOCs) are artifacts observed on a network or in an operating system that indicates a compromise. Typical IOCs are IP addresses, domain names, URLs, and MD5 hashes of malware files patterns or other attributes. After IOCs have been identified, they can be used for early detection of future attack attempts. |
Watering Hole | A targeted version of the drive-by. Malicious actors target a specific organization, compromising the website in an element of the victim’s supply network. In this way, they can compromise users of the targeted organizations, such as injecting remote access tools inside their machines. This is a subset of the more general category of supply chain attacks where malicious actors compromise an organization by targeting less-secure elements in the supply network. |
Zero-Day | Vulnerability that has not been patched already by the vendor. Zero-day (0-day) vulnerabilities can be exploited by attackers to execute arbitrary code, including the possibility to inject malware (typically droppers). |
Configuring Advanced Threat Protection
The Netskope cloud platform has threat protection capabilities, including advanced threat detection engines, such as heuristic analysis, sandbox analysis, and ransomware detection and remediation.
You can also leverage some of your existing, trusted threat detection products like Palo Alto Networks Wildfire, Juniper SkyATP, and Check Point SandBlast to work with Netskope ATP. An advanced threat protection license is required. Contact Support to get this feature enabled.
After integration, verify the status is green. Go to Settings > Threat Protection > Integration. Under Advanced Threat Protection look for a green arrow besides Status:. Verifying the status is green ensures that blocklisted and allowlisted files are included in your Ransomware detection scan.
The file types sent vary per application:
Juniper SkyATP: Hash lookup of all file types
Check Point SandBlast: All file types
Palo Alto Networks Wildfire:
Android application package (APK) files
Adobe Flash files Archive (RAR and 7-Zip) files
Java Archive (JAR) files
Microsoft office files
Portable executable (PE) files
Portable document format (PDF) files
Mac OS X files
Linux (ELF) files
Before you begin, make sure you have your ATP app API key and server IP address; these are needed to complete this procedure.
To configure an ATP app integration:
Go to Settings > Threat Protection > Integration.
Click on the Juniper SkyATP, Palo Alto Networks Wildfire, or Check Point Sandblast application box.
Enter and select parameters for each field:
API Key: Enter your ATP app API key
Rate Limit Per Hour: Enter a rate limit value per hour. Rate limiting controls the rate of traffic sent or received by the server. If a value of 200 is entered, Netskope will make a maximum of 200 API calls to the endpoint server in a span of one hour.
Juniper SkyATP, PAN Wildfire, and Check Point Sandblast applications vary in rate limits. Check the product documentation for these apps to learn their rate limit per hour.
Note
This field is visible only if a rate limit is configured on your systems.
Type: Select Cloud.
Only send files that are detected malicious by Netskope engines: Sends only files that are detected as malicious by Netskope ATP engines.
Server: Enter the IP address or FQDN of your ATP server.
Instance Name: Enter a meaningful name to identify this integration.
When finished, click Save.