New Features and Enhancements In Release 94.0.0
Here is the list of the new features and enhancements.
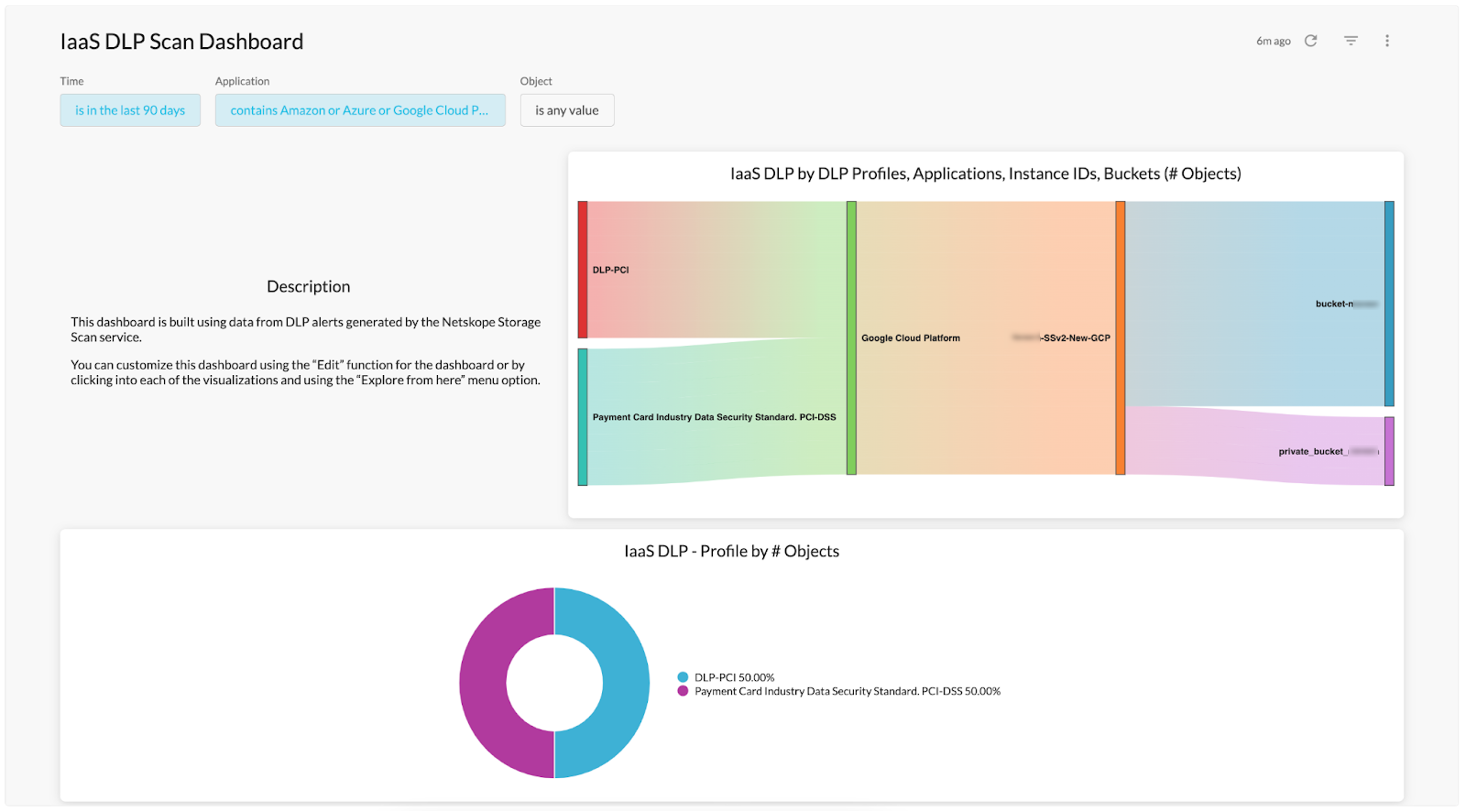
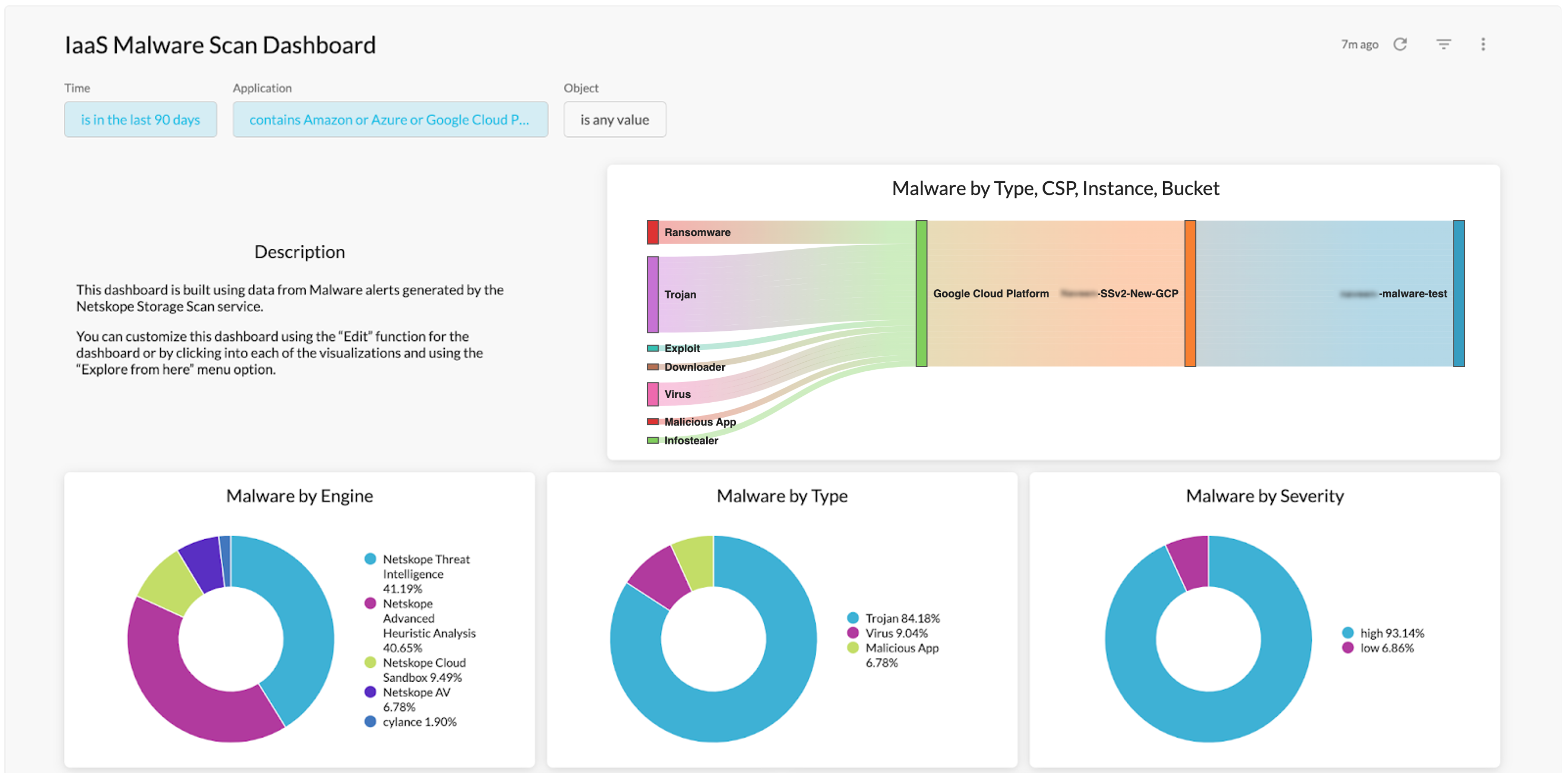
IaaS Storage Scan Dashboards
Two new dashboards for IaaS specific to Data Loss Protection(DLP) and Malware detection are added to the Netskope library. These dashboards are created from policy-based alert data related to DLP and Malware policy settings. You can use these dashboards as a starting point to further customize the data presented.
You can schedule a dashboard directly from the Netskope shared folder and automatically get updates that Netskope makes to improve that dashboard. If you do not want automatic updates, copy the dashboard into your group or personal folders and schedule from there.
 |
 |
Handle Empty Text Field in Slack Message
Netskope API Data Protection for Slack does not process Slack notifications with an empty text section. Examples include notifications generated by Slack Bot integrations.
Support Salesforce Organization ID as a Valid Instance Name
In addition to organization name, Netskope now supports Salesforce.com organization ID as a valid instance name when setting up a Salesforce instance in Settings > API-enabled Protection > SaaS > Salesforce.com > Setup Instance.
Support For OneLogin Activities
Netskope supports the following activities for OneLogin:
Create
Delete
Edit
Share and Unshare
Planner Integration In Microsoft Teams
Netskope adds coverage for Microsoft Planner integration in Microsoft Teams for the following activities:
Create
Edit (DLP supported)
Delete
Post (DLP supported)
New Activity In PagerDuty
In this release, Netskope extends support for POST activity in PagerDuty.
New Instance ID And Activity Detection Support
Figma is a web-based vector graphics editor and prototyping tool with additional offline features enabled by desktop applications for macOS and Windows. The activities detected for browser and native(Mac, Windows) applications are:
Login Attempt
Login Successful
Logout
Login Failed
Upload
Download
Share
View
Unshare
Create
Rename
Edit
Delete
Post
New Activities For Microsoft Whiteboard
Microsoft Whiteboard is a cloud-based digital whiteboard application which enables collaborative brainstorming on a whole new scale. The activities detected for browser based access are:-
Login Attempt
Login Successful
Logout
Login Failed
Upload
Download
Share
View
Create
Edit
Microsoft Cross Tenant Access Policies Support
With this feature, Netskope now enhances its Header-insertion capabilities to support Microsoft's Cross Tenant Access Policies.
The administrators can now select the Cross-tenant Access Policy key from the drop-down for Microsoft Office 365 Suite or Microsoft Live Suite under Application Feature Support in their Netskope settings and enter the corresponding Values (DirectoryId>:<policyGuid>) obtained from Microsoft's Cross Tenant Access Policy (XTAP) APIs. This allows administrators to control the external accounts accessed from their networks and devices.
Asana Workspace Access Support
With this feature, Netskope enhanced its Header-insertion capabilities that allow Asana to enforce restrictions on Workspace access.
Administrators can now select the following keys from the dropdown for Asana under Application Feature Support in their Netskope Settings and enter the corresponding Approved Domain IDs as Values.
Asana-Allowed-Domains-Requester-Id (1)
Asana-Allowed-Domain-Ids(2)
If admins want to allow only their own domain, the values in (1) and (2) remain the same. If they want to allow multiple domains, (2) will contain multiple values.
User Field For Unauthenticated Flows
The user field in Skope IT will be displayed in the format <IP Address> (Unknown) for unauthenticated flows.
Support For Metadata Extraction For Email Files
This release adds support for metadata extraction for the following email file types: .msg, .pst, .eml, .mbx, and .ost. You can create DLP rules to match metadata including headers, from/sent/to/cc, and subject values when inspecting email files.
CloudTrail Listing and CFT Permission Update
The CFT template used for Cloud Security Posture Management (CSPM) setup is now updated to include `cloudtrail:ListTrails` permissions.
Note
Netskope recommends you download and deploy this in your AWS account for the improved listing of cloudtrails.
AWS Foundational Security Best Practices
The new CSPM profile AWS Foundational Security Best Practices profile helps detect violations when AWS accounts and deployed resources do not align with security best practices defined by AWS security experts.
New REST API In Inline Enforcement
The new REST API allows creating, updating, and deleting app instances along with a new option to apply Instance tags for inline enforcement.
Unsanctioned Account Controls / Policies / Constraint
Introduced capabilities are:
New Instance Tagging capability with enhanced policy constraint to enforce instance tag-based policies.
New App Suite Construct for Inline Policy Enforcement at the Suite level.
Sanctioned Instance Sync/Feed through CSA integration for AWS.
New Union Based Activity selection model for greater flexibility in multi-app/multi-category policy definition.
Enhanced SkopeIT events with additional context App Suite, Instance Tags, and so on.
Addressed use cases:
Real-time visibility and control of Sanctioned vs Unsanctioned Instance Access.
Fine-Grained control over activities across categories/applications and activities.
Real-Time prevention of data exfiltration and threat protection against Malware.
Benefits:
Identify and control access to Sanctioned vs Unsanctioned access to IaaS/SaaS instances and resources.
Secure data perimeter by preventing data exfiltration to unsanctioned accounts.
Prevent Sensitive/Risky actions performed by users on sanctioned Instances.
Threat Protection for inline traffic with real-time enforcement.
Identify anomalous activity based on real-time events.
Validate Cert Expiry Instantly At Upload
With this release, the device certificate expiration in the Client configuration is displayed immediately after upload.
Display Publisher CN Field Under Session Category
The Publisher CN field is now visible under the SESSION category for Network Event Details with respect to Netskope Private Access. This field was previously queried only through the Skope IT advanced query Search but was not visible on the user interface (UI) .
Non-Functioning Clientless NPA SSO
For any SAML service providers that are:
Functioning: Nothing changes and continue sending format value as " ".
Non-functioning: The administrator needs to modify the SAML configuration table and add the following field :value pair in the JSON configuration value: name_id_format”:”urn:oasis:names:tc:SAML:2.0:nameid-format:persistent.
All possible values can be:
urn:oasis:names:tc:SAML:2.0:nameid-format:persistent
urn:oasis:names:tc:SAML:2.0:nameid-format:transient
urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress
urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified
urn:oasis:names:tc:SAML:1.1:nameid-format:x509SubjectName
New NPA Improvements
This release introduces NPA support for Android 12 and Apple MacBook M1 laptops.
NPA Publisher Ubuntu 20.04
Starting with this release, you can deploy NPA Publishers for production traffic using Ubuntu 20.04.
Existing deployments based on CentOS Publishers are not affected and continue to be supported through the calendar year 2022.
Ubuntu Publishers have feature parity with CentOS-based publishers and do not have any capability limitations.
You can use a mix of CentOS and Ubuntu Publishers simultaneously for application access.
New capabilities will only be released on Ubuntu publishers, post this release.
Access Method For Private Apps In Real-Time Policy
With this release, the access method for Private Apps in Real-Time Policy is updated as follows:
Access Method = Client. This displays all private apps (the private apps that have Browser Access enabled can also be accessed through the client).
Access Method = Browser Access. This displays only the private apps that have Browser Access enabled.
Access Method = Client, Browser Access. This displays only the private apps that have Browser Access enabled.
IPv4 Address To Bypass Traffic Flag
Netskope Client and VPN are up and running at the same time. The native application uses IPv6 to connect with the server, Netskope Client bypasses the IPv6 flow but the VPN interface blocks or does not accept IPv6 connections. Now Netskope Client uses the IPv4 address over IPv6 if a special feature flag bypass IPv4 address is enabled.
Transaction ID For CTEP Alerts
Netskope Client Traffic Exploit Prevention (CTEP) Alerts now support a Transaction ID field. This enables the correlation of multiple events related to the same attack, further enhancing UEBA detection capabilities, Advanced Analytics dashboards, and customer alert triage and investigation activities.
New alert type for CTEP And C2 Detections
The Alert Field now displays CTEP and C2 that enables to identify and filter these alerts uniquely in SkopeIT. The Alert Name for these alert types changed from the policy name to the Netskope detection name.
CTEP User Interface
A simplified CTEP user interface is enabled for all tenants. The legacy user interface is now deprecated.
Support For Windows 10 2HCY21
Starting with release 94, the Netskope Client support Windows 10 Version 21H2.
Non-configurable Bypass RFC1918 Addresses In Netskope Cloud Firewall (CFW) Steering
Starting with this release, the Netskope Client tunnels RFC1918 IP address range in the All traffic steering type (Cloud Firewall mode). Prior to this release, the Netskope Client bypassed the RFC1918 IP address range irrespective of the Steering Configuration exception.
Note
To bypass the RFC1918 IP address range, add Local IP Address Range to exceptions in Steering Configuration.
Netskope Client Tunnels DTLS Packets
Starting with release 94, the Netskope client tunnels DTLS packets in the All traffic steering type (cloud firewall mode). Prior to this release, the Netskope client bypassed DTLS packets locally irrespective of the steering configuration exception.
Note
To bypass DTLS packets, add the particular app to exceptions in the Steering configuration.
macOS Netskope Client Native M1 support
With this release, a macOS Netskope Client installer supports both x86_64 and Apple Silicon (M1 chip) natively (without Rosetta). Thus, all binaries are now considered Universal Binaries.
Authentication During Cert Installation
Netskope displays a Firefox authentication dialog that prompts you to enter the password while installing the certificate into the password-protected Firefox cert store.
Request for Client Installation Suppression On Failure
With this release, Netskope introduces a new JAMF parameter for silent mode installation. You can pass silent_mode as an optional parameter as part of the JAMF script parameter to disable prompting error messages whenever the installer fails.
Flag To Store The Self-Protection Status
Earlier, the Netskope Client Self-Protection feature was enabled only after a reboot and the tunnel creation. Now, with this release, the Client caches the Self-Protection status and immediately enables the status after the reboot.
Android 12 Support
With this release, the Netskope Client supports Android 12.
New Fields In Network Events
Publisher CN and POP Name fields are available in the Network Event Details panel for Network Events.
New Skope IT Alert Type
Netskope added a new alert type to the dropdown filter options for CTEP in Skope IT Alerts. To filter alerts using the advanced query, use query alert_type eq ctep.