Netskope IPSec with Cisco Firepower
Netskope supports Internet Protocol Security (IPSec) tunnels as a traffic steering method. IPSec tunnels allow you to route web traffic (port 80 and 443) to Netskope using logical tunnel interfaces that terminate to a Netskope IPSec gateway. When you create IPSec tunnels in the Netskope UI, Netskope provides parameters for configuring the tunnels on your firewall.
This guide illustrates how to configure IPSec tunnels between Netskope and Cisco Firepower appliances running Firepower Management Center (FMC) version 7.0.1. To learn more about the steps in the FMC: FMC documentation.
To create the IPSec tunnels for Cisco Firepower appliances in the Netskope UI:
Go to Settings > Security Cloud Platform > IPSec.
Click Add New Tunnel.
In the Add New IPSec Tunnel window:
Tunnel Name: Enter a name for the IPSec tunnel.
Source IP Address: (Optional) Enter the source peer IP address (i.e., exit public IP) of the Cisco firewall that Netskope will receive packets from. Netskope identifies traffic belonging to your organization through your router or firewall IP addresses.
Source Identity: Enter an IP address, a fully-qualified domain name (FQDN), or an ID in email address format. For example, 1.1.1.1 or sourcelocation@company.com. The router or firewall uses the source identity for authentication during Internet Key Exchange (IKE).
Primary Netskope POP: Select the primary Netskope point of presence (POP) closest to you, and copy the IPSec Gateway IP address. You need this information to establish the primary IPSec tunnel on your Cisco firewall. For optimal performance, Netskope recommends using the geographically closest POPs and configuring at least two tunnels for each egress location in your network.
Failover Netskope POP: Select the backup Netskope POP closest to you, and copy the IPSec Gateway IP address. You need this information to establish the backup IPSec tunnel on your Cisco firewall. For optimal performance, Netskope recommends using the geographically closest POPs and configuring at least two tunnels for each egress location in your network.
Pre-Shared Key (PSK): Enter the pre-shared key that both sides of the tunnel will use to authenticate one another. The PSK must be unique for each tunnel.
Encryption Cipher: Select an encryption algorithm for the IPSec tunnel.
Maximum Bandwidth: Enter the maximum bandwidth for the IPSec tunnel. The tunnel size can be up to 1 Gbps. To enable the 1 Gbps option, contact your Sales Representative.
Advanced Settings: Click to view the following options.
Rekey: Select to rekey SAs when they expire. Netskope recommends using the default setting.
Reauthentication: Select to create new IKE and IPSec SAs when they expire. Netskope recommends using the default setting.
Trust X-Forwarded-For Header: Select to trust IP addresses contained in the X-Forwarded-For (XFF) HTTP header at the tunnel level. If you trust XFF at the tenant level, you can't select this option.
Apply to all traffic: Use the XFF HTTP header to identify all user traffic going through the IPSec tunnel.
Apply to specific NAT/proxy IP(s): Use the XFF HTTP header to identify traffic from specific NAT and proxy IP addresses going through the IPSec tunnel. Click +Add Another to add multiple IP addresses.
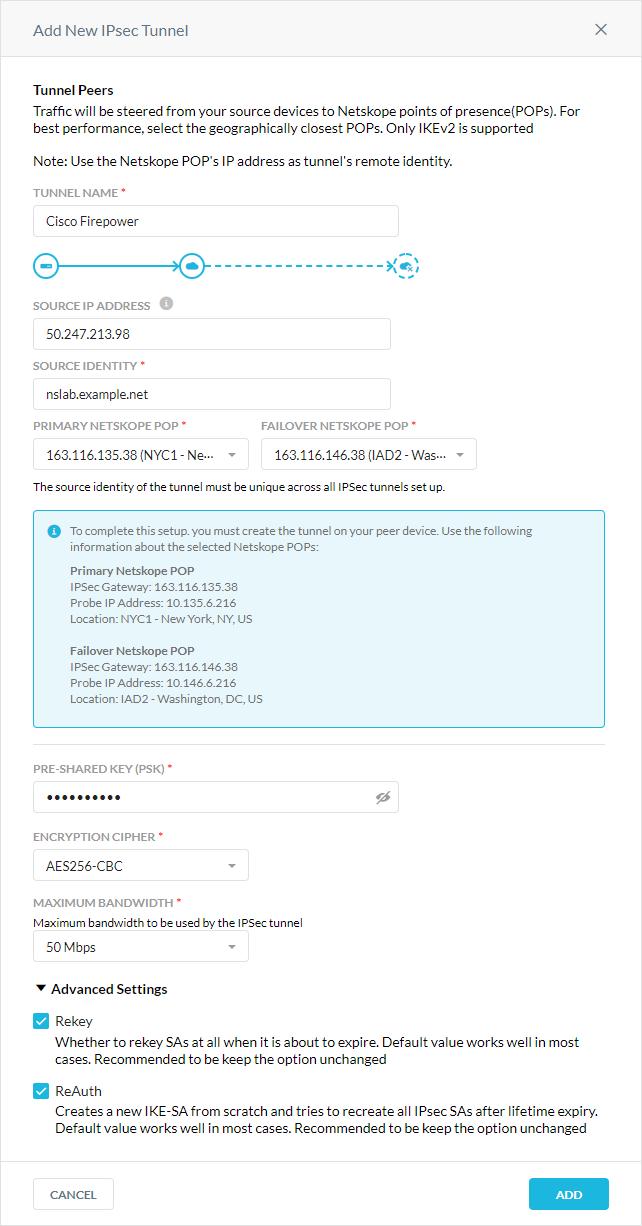
Click Add.
To configure the access lists that will match the traffic that goes inside the tunnel:
In the Firepower Threat Defense (FTD) Management, go to Objects > Object Management.
Select Access List > Extended.
Select the option to create a new access list.
Create the following entry to match all HTTP/HTTPS traffic to the internet:
Seq: 1
Action: Allow
Source: Internal LAN network Source
Port: any
Destination: any
Destination Port: HTTP / HTTPS. You can add non-standard ports, but ensure you add them in Netskope as well.
Create the following entry to allow ICMP from the internal network to the Netskope Probe IP address.
Seq: 2
Action: Allow
Source: Internal LAN network Source
Port: any
Destination: Netskope Probe IP addresses. You can copy them from the IPSec tunnels you configured in Netskope.
Destination Port: ICMP
Click Save then Continue.
Go to Objects > VPN > IKEv2 Policy.
Select the option to create a new policy.
Configure the phase 1 parameters. To see a list of the Netskope supported IPSec parameters: IPSec.
Click Save then Continue.
Go to Objects > VPN > IKEv2 IPsec Policy.
Select the option to create a new policy.
Configure the phase 2 parameters. To see a list of the Netskope supported IPSec parameters: IPSec.
Click Save then Continue.
To configure the VPN tunnel:
Under VPN, go to Devices > Site-to-Site.
Select the option to create a new VPN Topology.
In the Edit VPN Topology window:
Topology Name: Enter a name for the VPN.
Policy Based (Crypto Map): Select.
Network Topology: Choose Point to Point.
IKE Version: Select IKEv2.
In the Endpoints tab:
Node A (Netskope)
Device: Select Extranet.
Device Name: Enter a name for the device.
Static IP: Enter the primary and secondary IPSec GW addresses in the following format: <Primary IPSec GW>,<Secondary IPSec GW>. You can copy these POP addresses in Netskope.
Protected Network: NEW.
Access List Extended: Select the access list you created above.
Node B (FTD)
Device: Enter the appliance establishing the tunnel.
Interface: The WAN interface.
IP Address: The IP address associated with the WAN Interface.
Connection Type: Bi-directional.
Protected Network: NEW.
Access List Extended: Select the access list you created above.
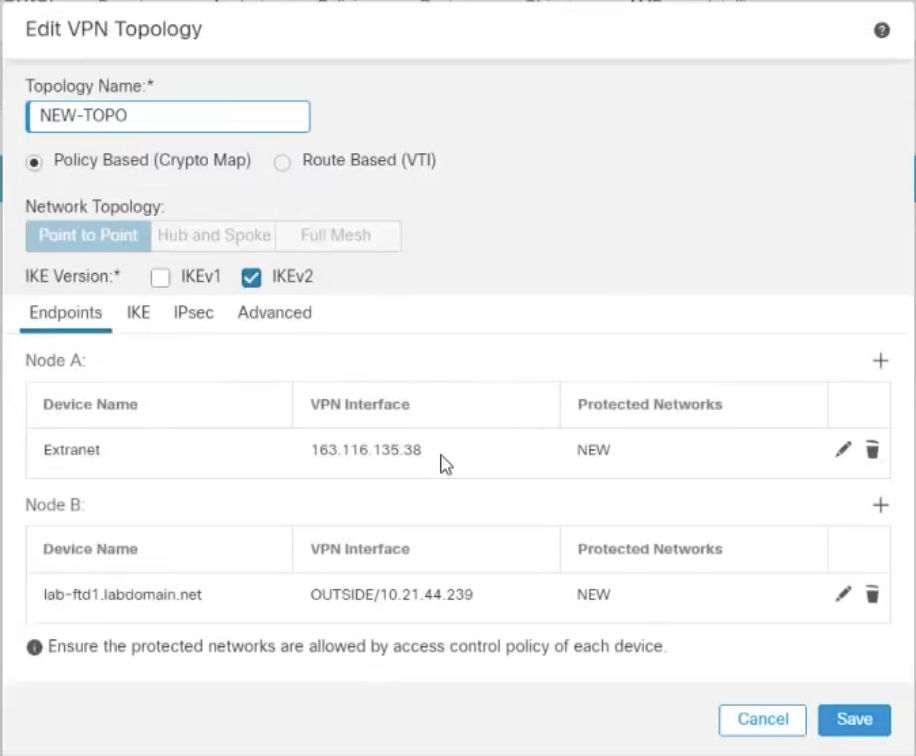
Click the IKE tab.
Under IKEv2 Settings:
Policy: Choose the Phase 1 proposal you configured above.
Authentication Type: Choose Pre-shared Manual Key.
Key: Enter the pre-shared key (PSK) you created in Netskope.
Confirm Key: Reenter the PSK.
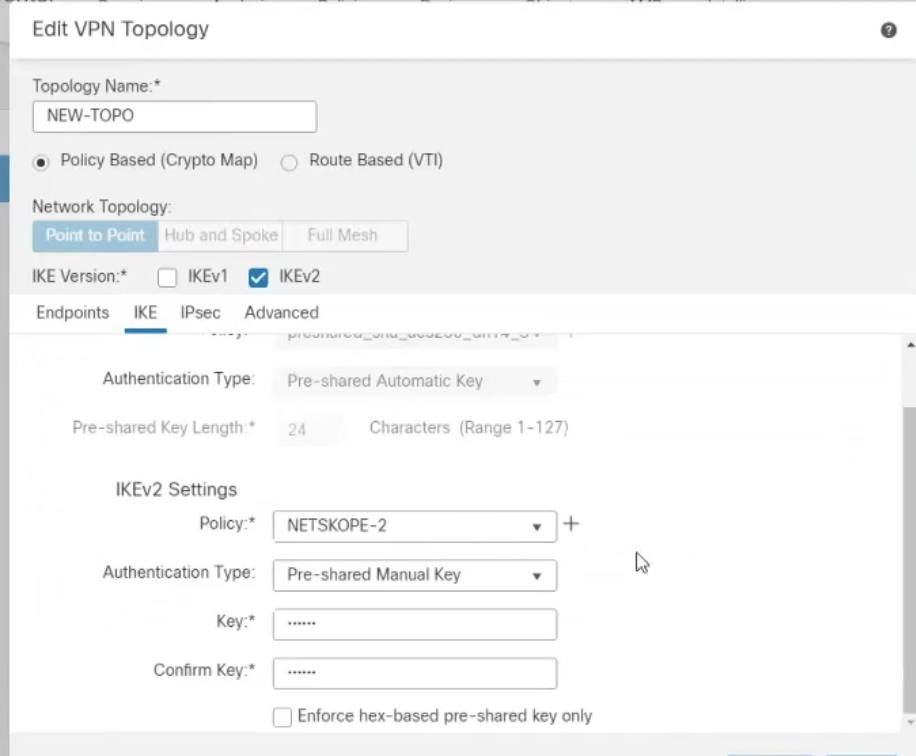
Click the IPsec tab.
In the IPsec tab:
Crypto Map Type: Select Static.
IKEv2 Mode: Choose Tunnel.
Transform Sets: Next to IKEv2 IPsec Proposals, click the Edit icon, and select the Phase 2 proposal you configured above.
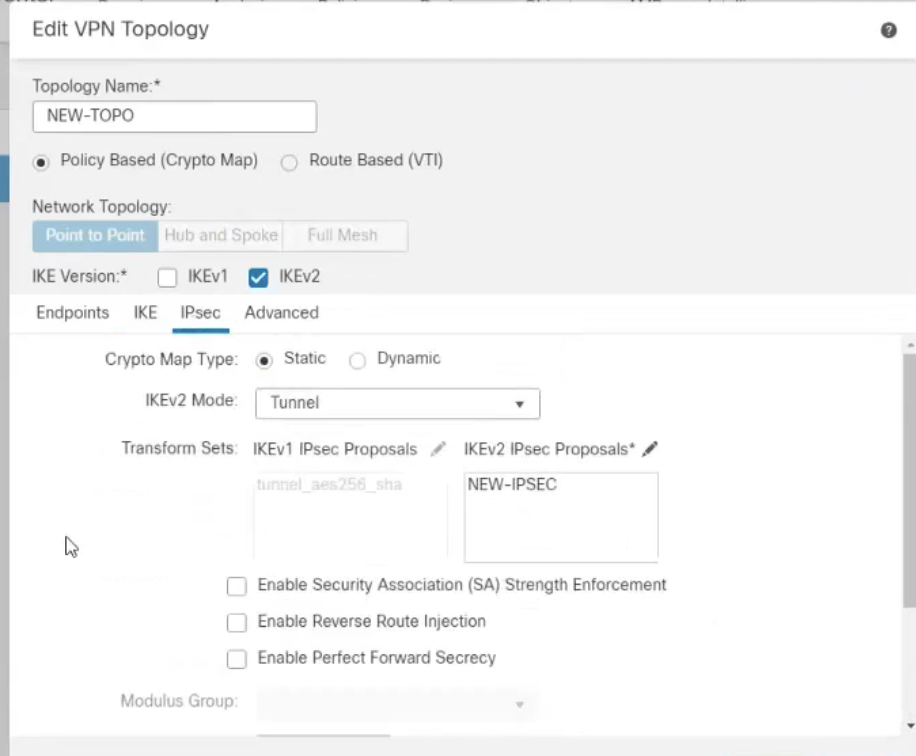
Click the Advanced tab.
Under ISAKAMP Settings:
Identity Sent to Peers: Choose the identity type that matches the configured FQDN field in Netskope.
Peer Identity Validation: Choose Required.
Under IPsec and Tunnel, use the default settings.
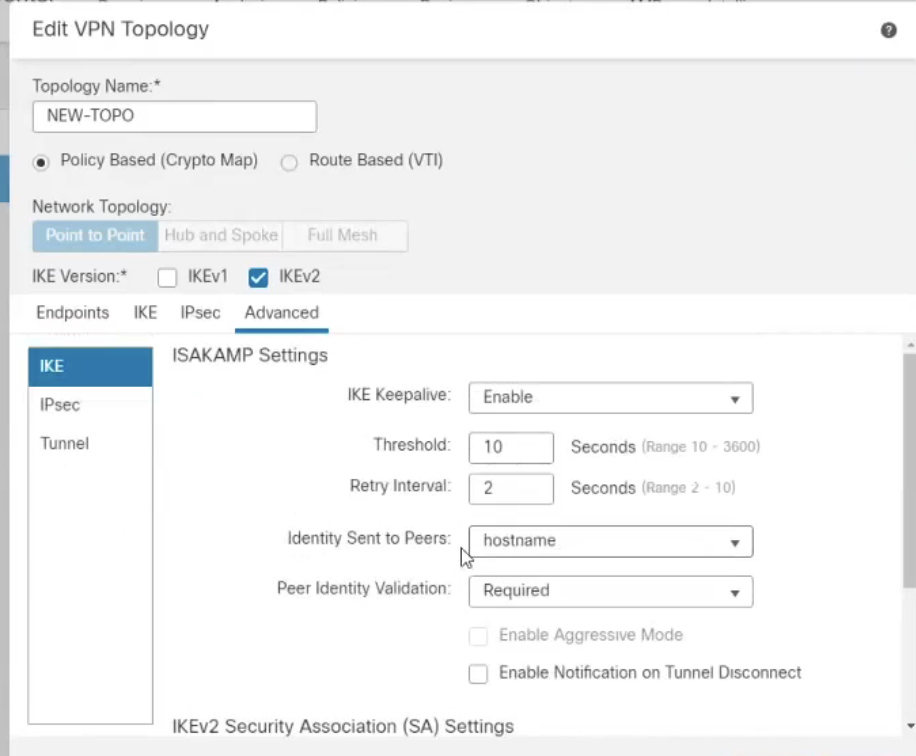
Click Save.
The Netskope cloud must see the original client IP addressess to authenticate them. If there is an existing NAT policy, the IPSec traffic must be exempted from it.
Go to Devices > NAT.
Add a new NAT rule above the existing NAT rule that disables NAT for all traffic going through the tunnel.
Under Interface Objects:
Source: Internal Networks
Destinatinon: Outside-Zone
Click the Translation tab, and configure accordingly.
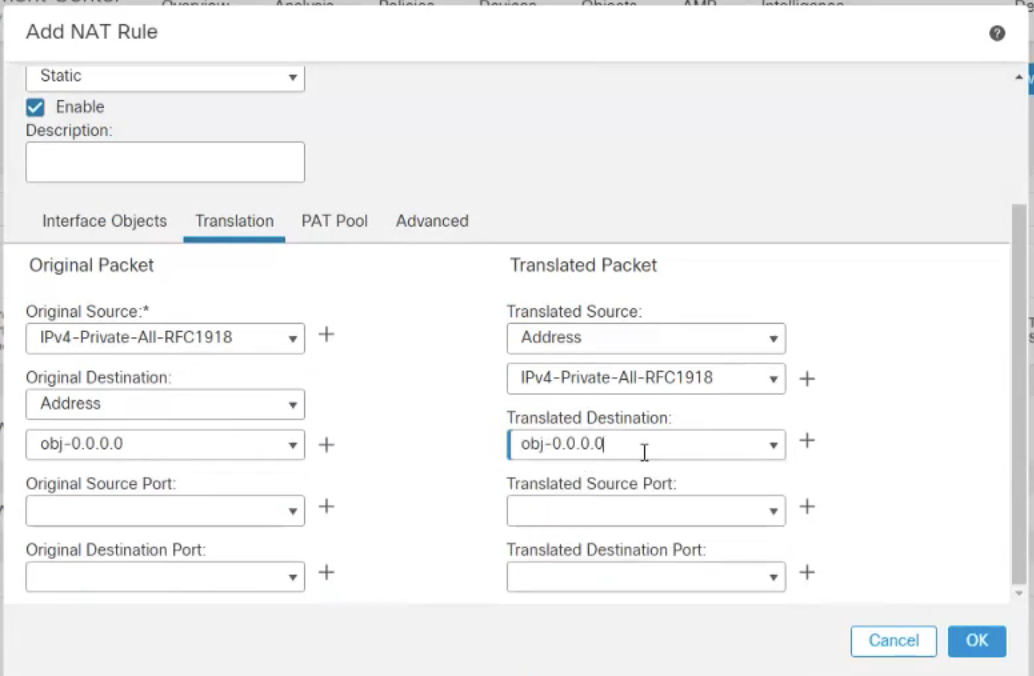 |
Go to Policies > Access Control.
Add a new rule:
Name: Enter a name for the policy.
Insert: Into Mandatory.
Action: Allow. If SNORT is used, you can use TRUST.
Source Zone: Internal Zone.
Destination Zone: Outside-Zone.
Source Zone: Internal Subnet(s).
Destination Zone: any-ipv4.
Click Save.
You can use any of the CLI commands below to troubleshoot the IPSec tunnels in the FMC. The CLI output displays the number of tunnels that are up, peers, and ciphers. You can use this information to verify tunnel establishment or identify a mismatch the phases.
Enter the following command to verify if there is a security association (SA) for Phase 1:
# Show crypto ikev2 sa
Enter the following command to verify if there is an SA for Phase 2:
# Show crypto ipsec sa