Protect Netskope IoT Security
The policy engine allows admins to define rules and take actions in detection of alerts or security incidents in enterprise IT deployments. Using Netskope IoT Security's policy engine, admins can enforce corrective measures for securing the network environment through alerts and micro segmentation using existing NACs, firewalls or other cloud based controllers in the environment.
You can navigate to the Policies menu to view a list of policies already created. To edit the existing policies, click on the policy name from the list and to delete the policy, click on the dustbin icon in front of the policy in the list.
Types of Policies
You can configure three types of policies:
Context-based policy - the purpose of a context-based policy is to define rules using device attributes as policy conditions. You can set context based policies with parameters like manufacturer, OS, model_name, etc.
Network-based Policy - the purpose of a network-based policy is to define rules for triggering alerts and corrective actions based on device connection properties (Source IP address, Source Ports, Subnet, Destination IP address, Destination Port, etc) along with the device context (Type, OS, Ownership, etc).
Threat-based policy - the purpose of a threat-based policy is to define rules for triggering alerts and corrective actions on the detection of a device-level threat or anomaly. The threat-based policy can act upon multiple alert categories, such as DDoS attack, suspicious string, attempted user privilege gain, etc. You can also define the threat severity when you create a threat-based policy.
Create Policy
Navigate to Policies menu and click Create Policies button. You will see a create policy section.
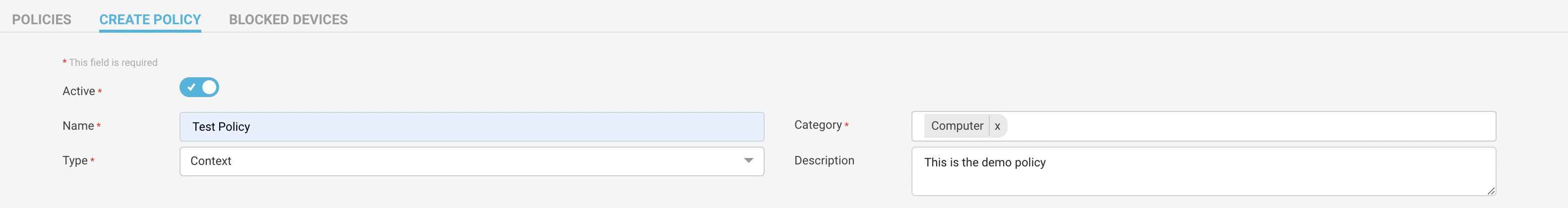
Mark the status of the policy to be active or inactive on creation.
Give a unique policy name.
Select the type of policy from context, threat, or network-based policy.
Give a category of the policy. The category helps you easily organize the policies, but it does not affect the policy condition.
Optionally, add a description to explain the policy behavior.
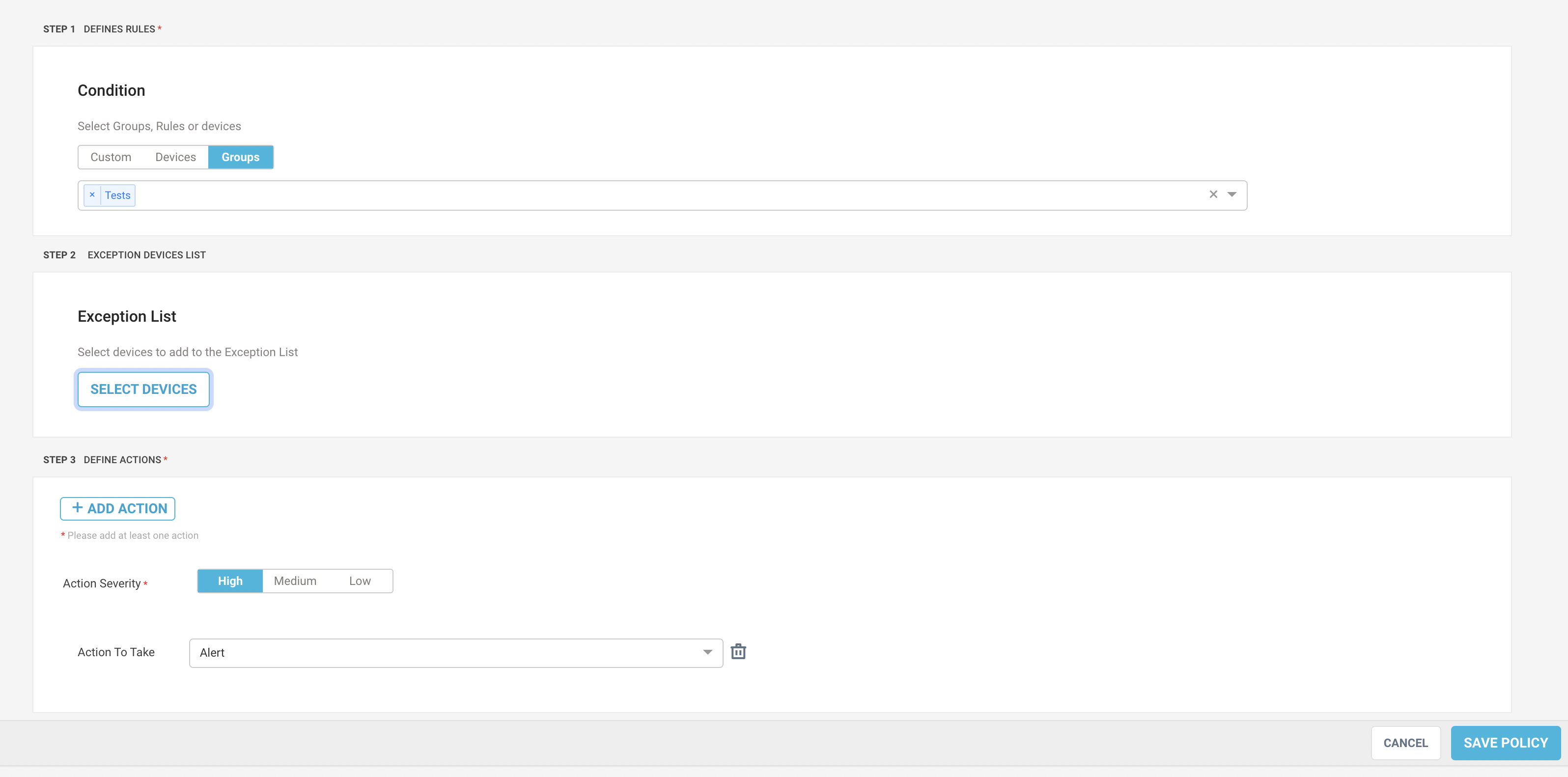
Define a condition to check in the environment. You can define the policy rule or condition in these ways:
Custom - create a customized policy by adding the rules using “and” or “or” conjunction. Select parameter field, operation and value to add a new rule.
Device - select the devices from the list to check the condition.
Groups - select a group created in your appliance. You can create groups in the Manage > Tags and Groups -> Groups tab.
Optionally, you can add devices to the exception list to exclude executing the policy. Click on the Select Devices button and use “+/-” button to add the devices to the exception list.
Define an action to perform on the selected group of devices.
Select the alert severity between high, medium, and low.
Select the action type:
Alert - generate an alert on detection of policy violation. The alert event appears in the user interface. You can pass the same to a SIEM through APIs.
Email - send email notifications to designated recipients.
NAC - blocking or segmenting the devices through Network Access Controllers (NAC). The NACs supported include Cisco ISE, Aruba Clearness, FortiNAC, Juniper ATP, Mist and Cisco Meraki.
Save the policy.
Blocked Devices Dashboard
The Blocked Devices section lists all the blocked or segmented devices. The page allows admins to undo the current state of the devices - unblock them or remove them from the segmentation group or add the devices to the exception list for bypassing policy controls.