Proofpoint Plugin for Threat Exchange
This document explains how to integrate Proofpoint with the Threat Exchange module of the Netskope Cloud Exchange platform. This integration allows for sharing of URLs and file hashes with Netskope that have been identified by Proofpoint.
A Netskope tenant (or multiple, for example, production and development/test instances).
A Secure Web Gateway subscription for URL sharing.
A Threat Protection subscription for malicious file hash sharing.
A Netskope Cloud Exchange tenant with the Threat Exchange module already configured.
Your Proofpoint TAP username and password.
Create a Custom File Profile to use in Threat Exchange.
Get your service principal and secret (username/password) from the Settings page in the Threat Insight Dashboard to authenticate the Proofpoint APIs in Threat Exchange.
Configure the Proofpoint plugin in Threat Exchange and then configure sharing of IoCs.
To configure the Proofpoint plugin:
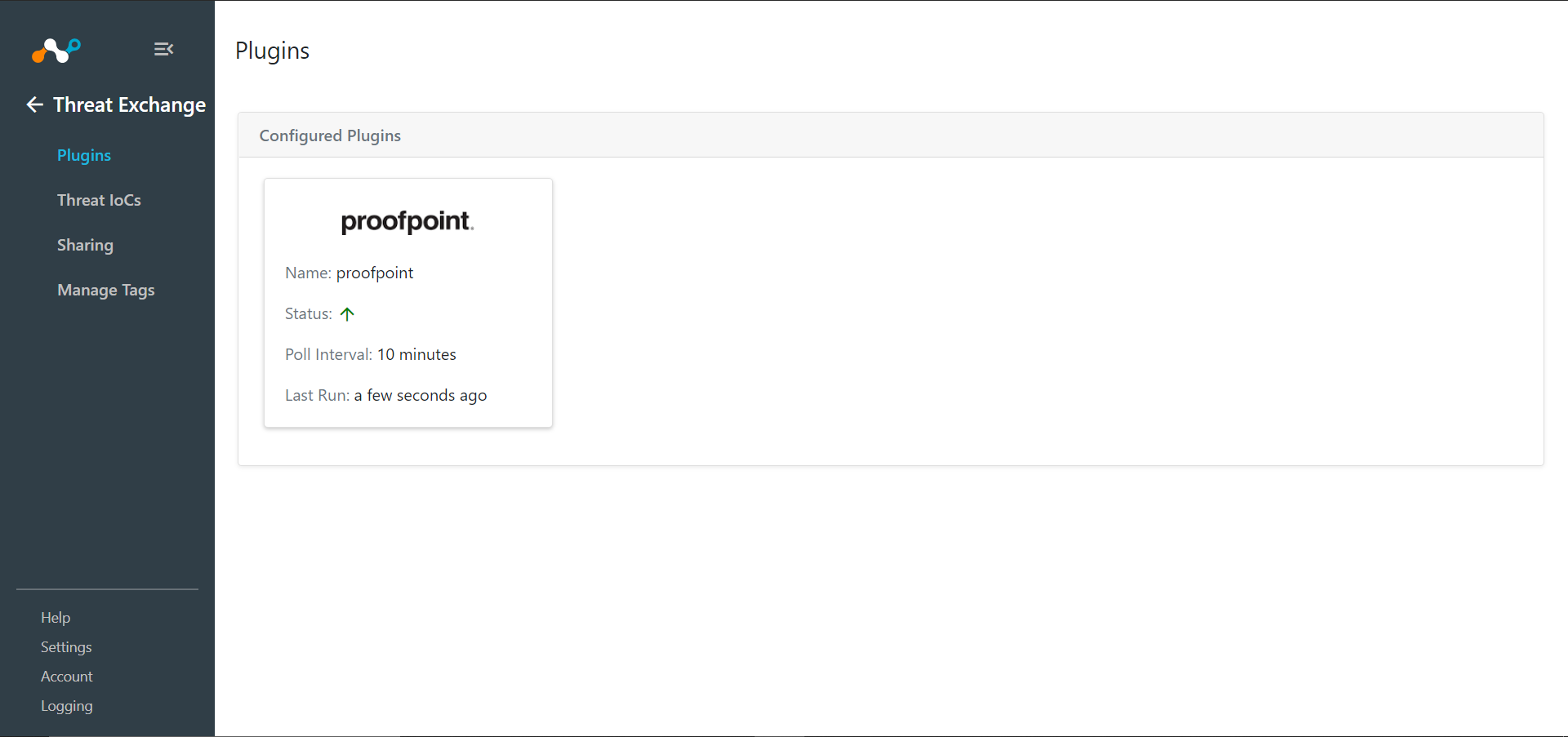
In Cloud Exchange, go to Settings and click Plugins.
Search for and select the Proofpoint plugin box to open the Plugin creation pages.
Enter a Configuration Name.
Adjust the Poll Interval to appropriate value: Suggested is 5+ minutes.
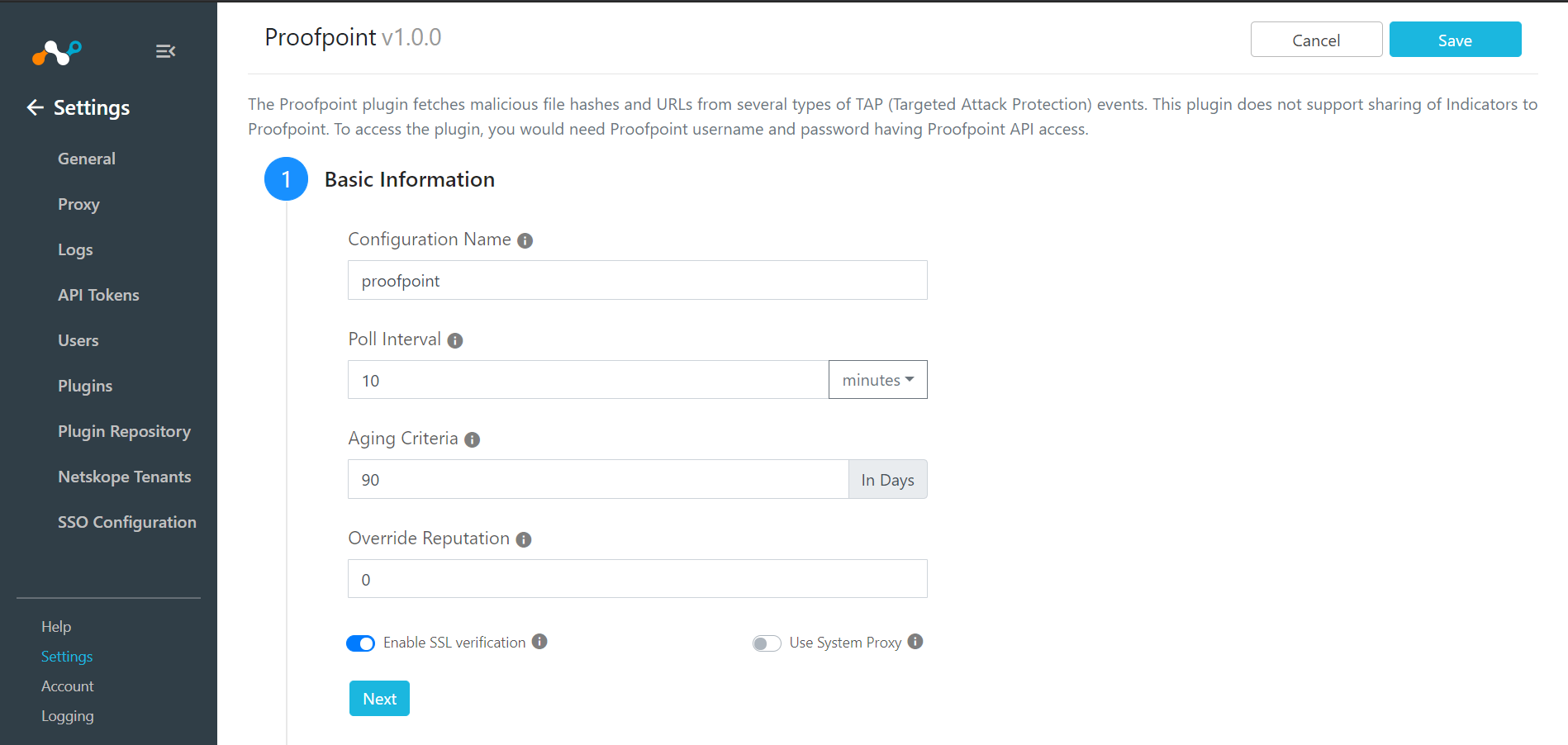
Click Next.
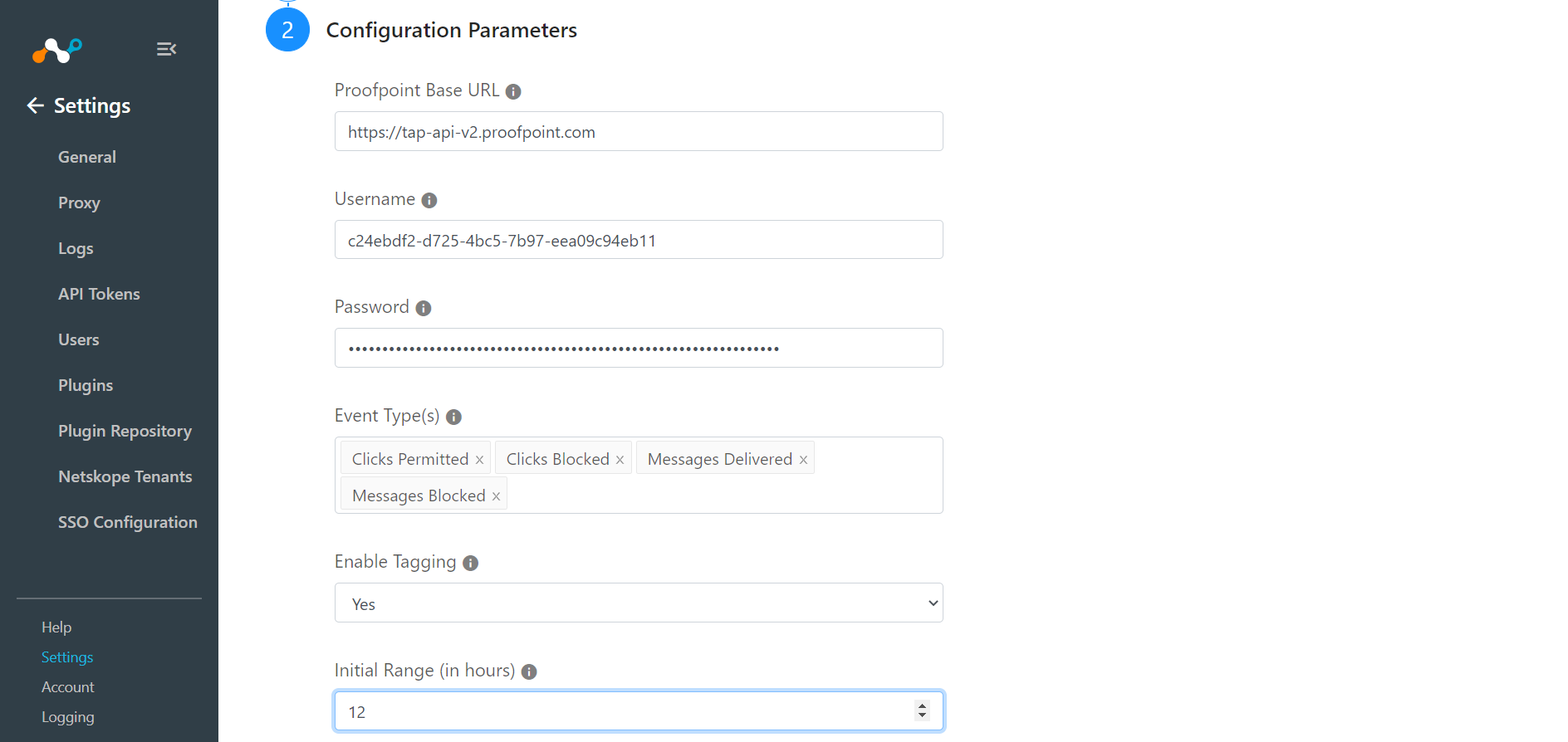
Enter your Proofpoint Base URL (if it’s different from the default one).
Enter your Proofpoint Username and Password.
Enter appropriate Event Type(s) to be fetched from Proofpoint. The IoCs corresponding to selected event types will be fetched.
Set the Initial Range (in hours) from 1 to 12 (The maximum time into the past that can be queried is limited to 12 hours by Proofpoint. Therefore, if “Last Run” is older than 12 hours, the data older than 12 hours won’t be fetched).
The rest of this form can remain as default.
Click Save.
Go to Threat Exchange and select Sharing. The Sharing page displays the existing relationships for each sharing configuration in grid view as shown below. The Sharing page also has inputs to configure new sharing from one plugin to another.
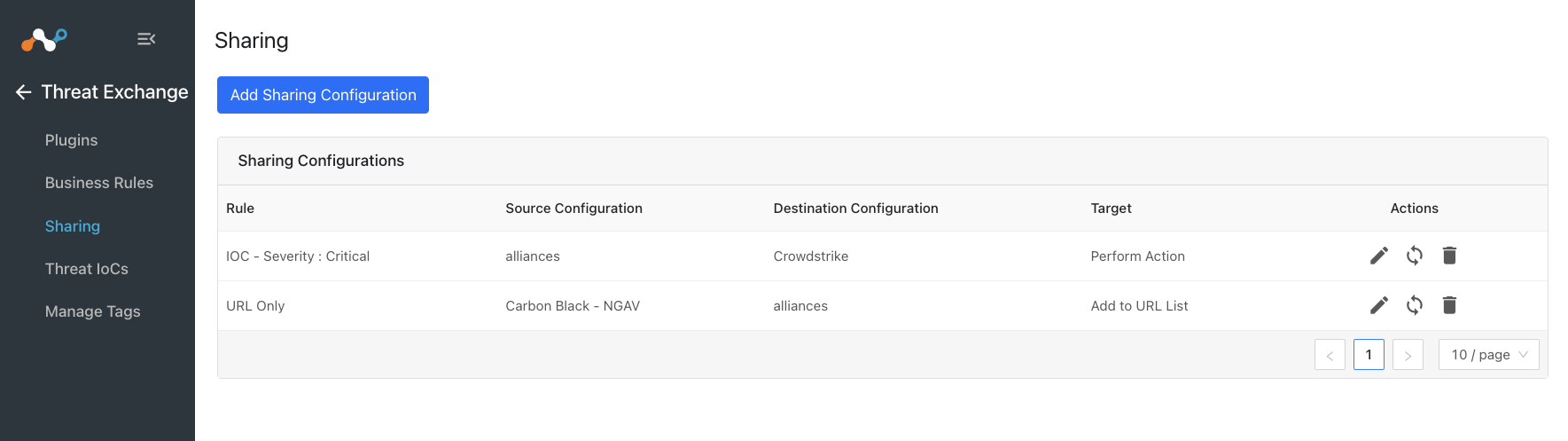
Click Add Sharing Configuration, and in the Source Configuration dropdown list, select Proofpoint.
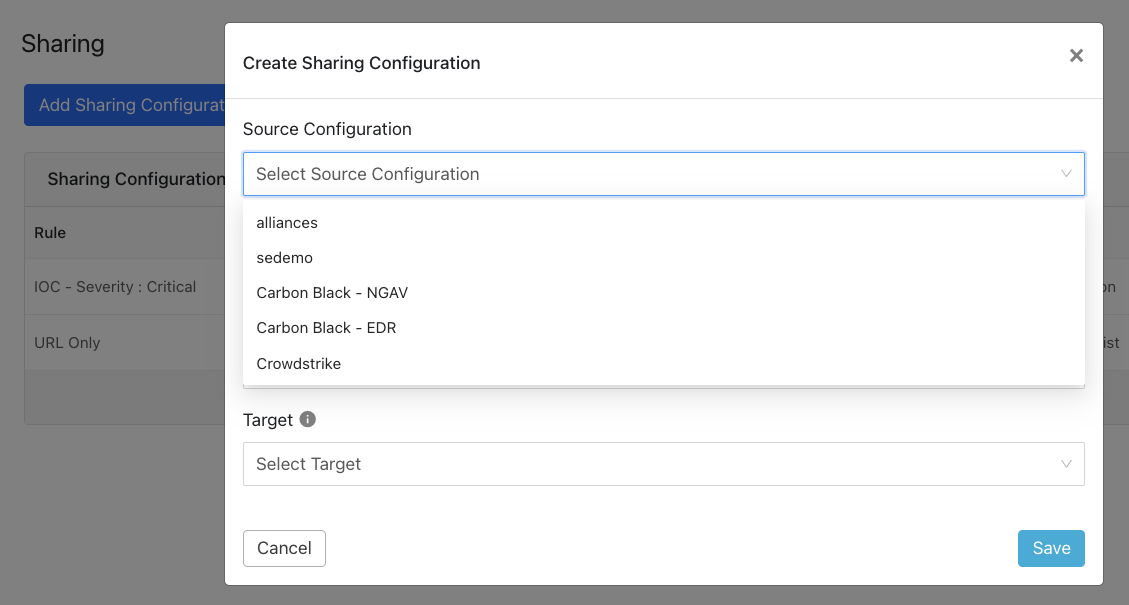
Select a Business Rule, and then select Netskope for the Destination Configuration. Sharing configurations are unidirectional. data obtained from one plugin is shared with another plugin. To achieve bi- or multi-directional sharing, configure each separately.
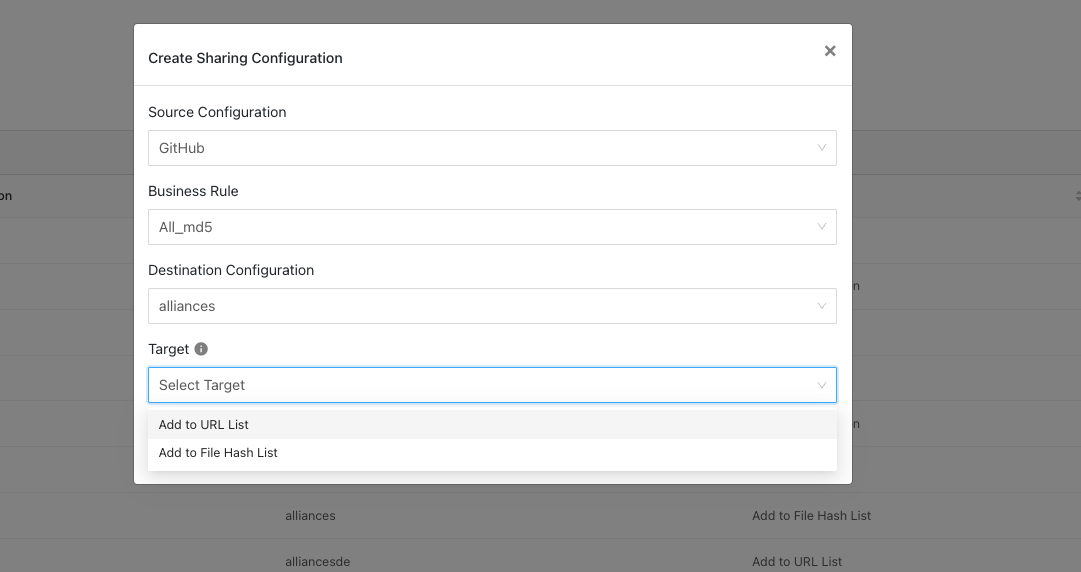
Select a Target. Each plugin will have a different target or destination for the IoC.
Click Save.
Note
Sharing IoCs from Netskope to Proofpoint is not supported. Proofpoint does not accept 3rd-party intel.
In order to validate the workflow, you must have Proofpoint indicators. Polling Intervals will be defined during plugin configuration.
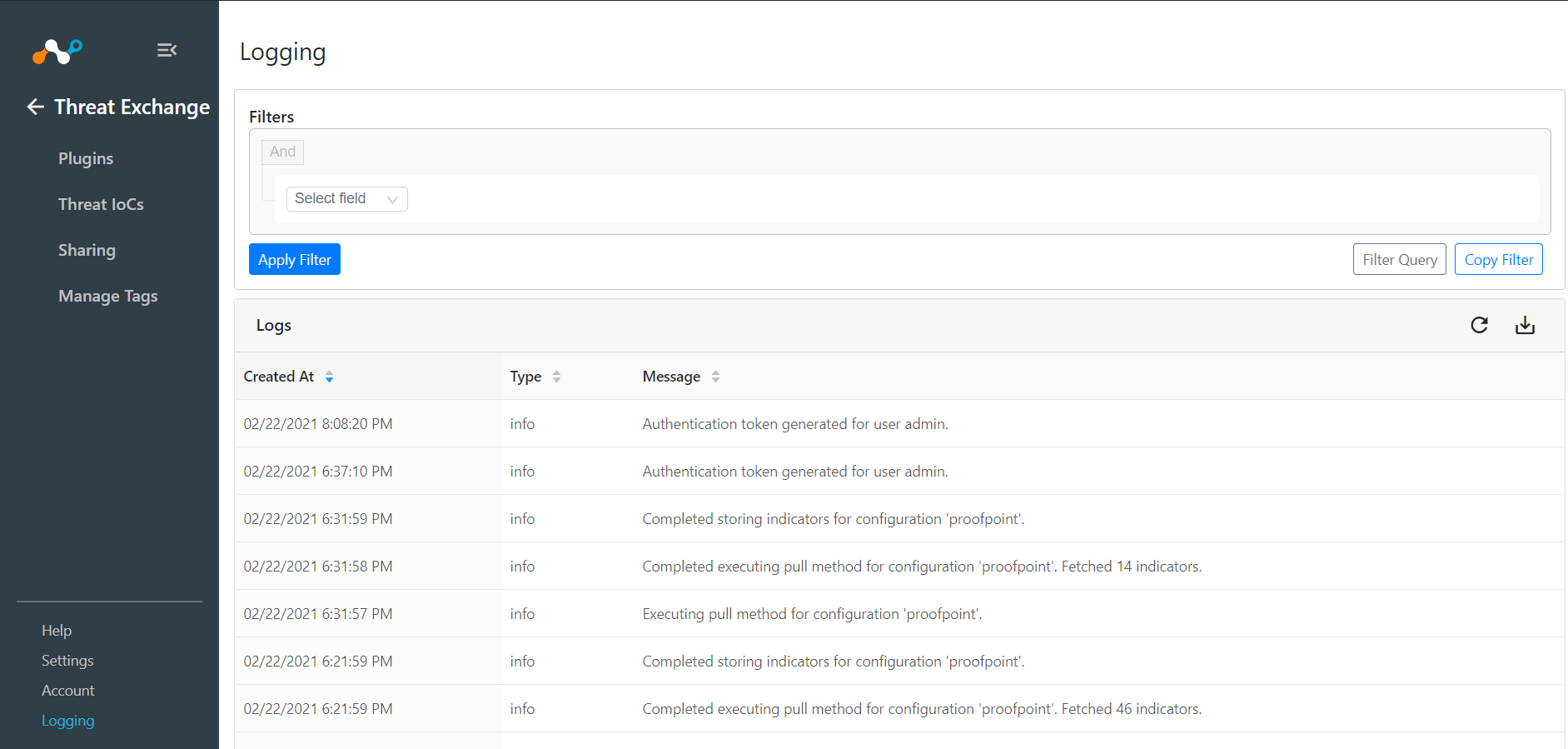
Go to Threat Exchange and select Threat IoCs.
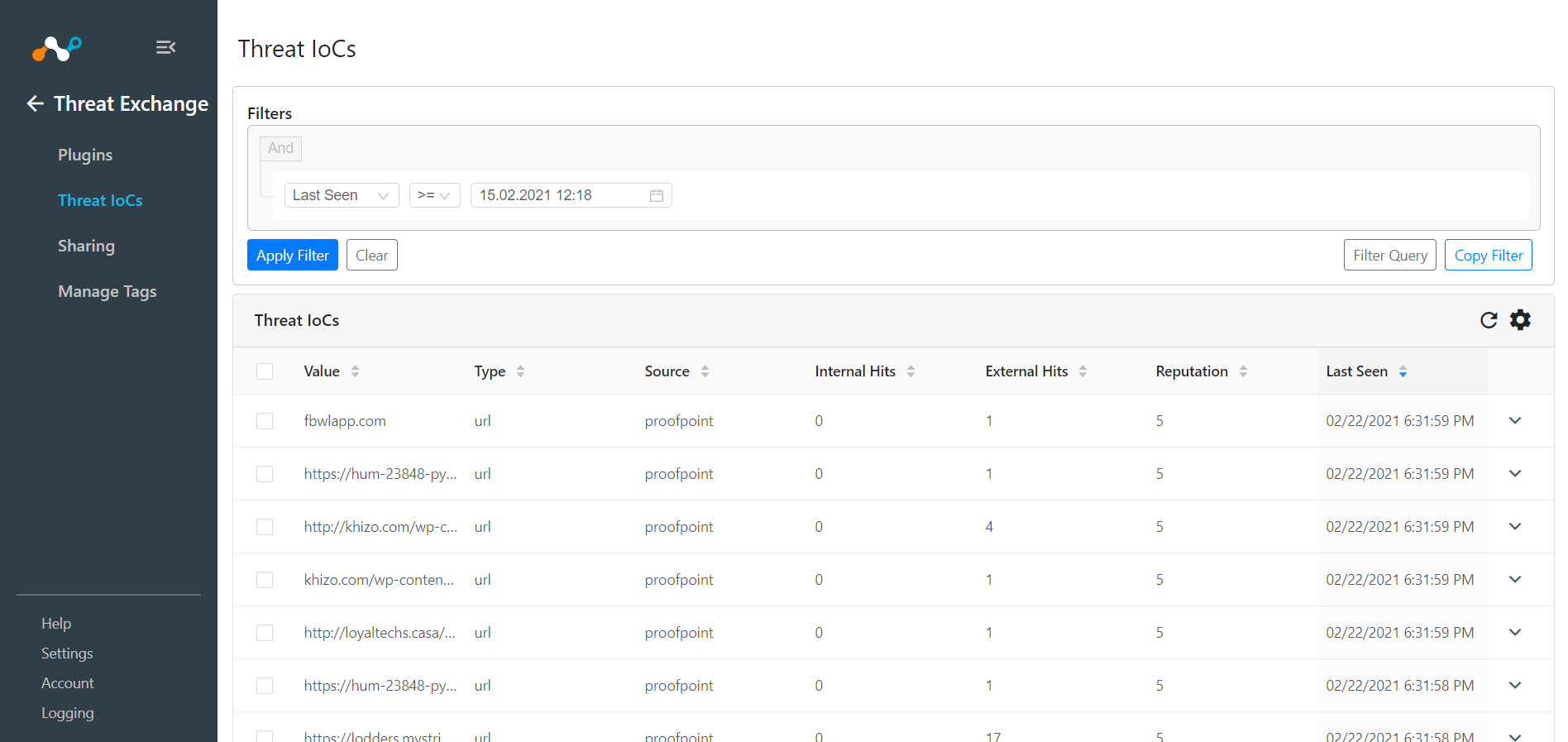
Validate data is being shared between the two plugins. If data is not being shared between the platforms, look at the audit logs in Cloud Exchange. Select Logging and look through the logs for errors.