Apply policies based on AD users, groups, or OU
To apply inline policies based on security needs and various constraints such as AD/user groups/Organizational unit, Source of traffic/Trusted or untrusted, networks/Forward or reverse proxy, Application instance, Constraint profile or augmenting authentication (Multifactor authentication), follow the steps as shown below:
Navigate to Policies > Real time Protection > New Policy > Cloud App access.
Under ‘Source’ section, select Users/User groups or Organizational Unit. Options selected here will apply in the policy being created.
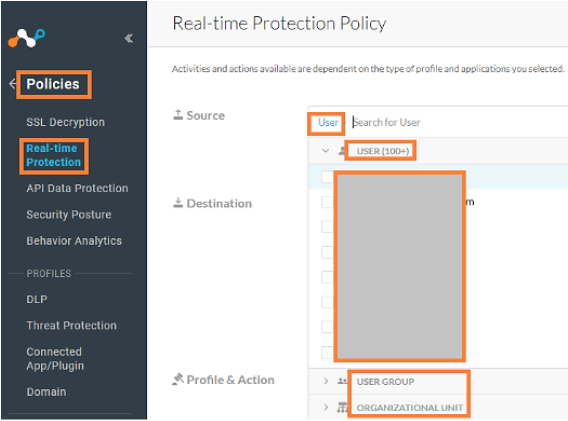
Under ‘Source’ section, select ‘ADD CRITERIA’ drop down option.
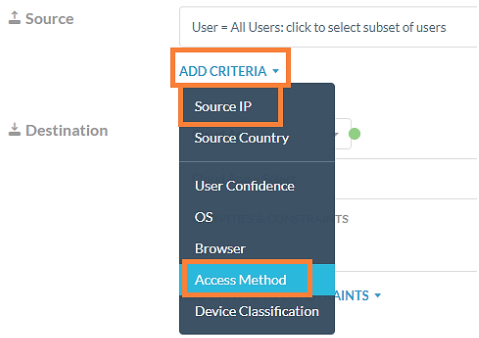
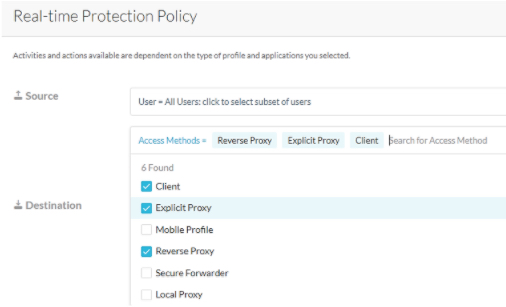
Select the ‘Access method’ option and select the required source of traffic and proxy type (forward, reverse).
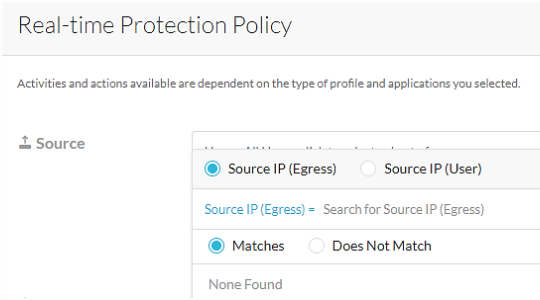
For trusted or untrusted networks, select ‘Source IP’ and provide the details.
To apply policies based on application instance, navigate to ‘Destination’ section of the policy creation template, and select the ‘App Instance’ option.
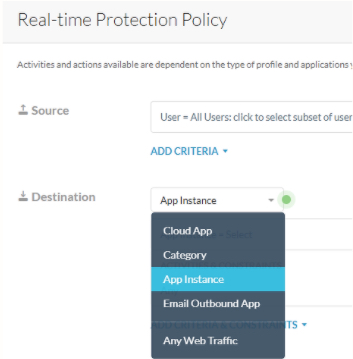
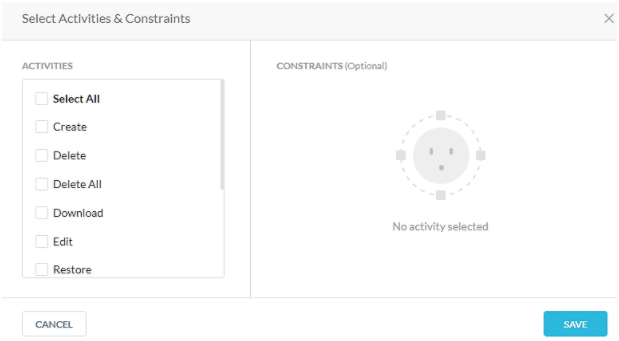
Selection of a cloud app or an app instance activates the ‘Activities and Constraints’ section where activities that have to act as constraints can be placed in the policy.
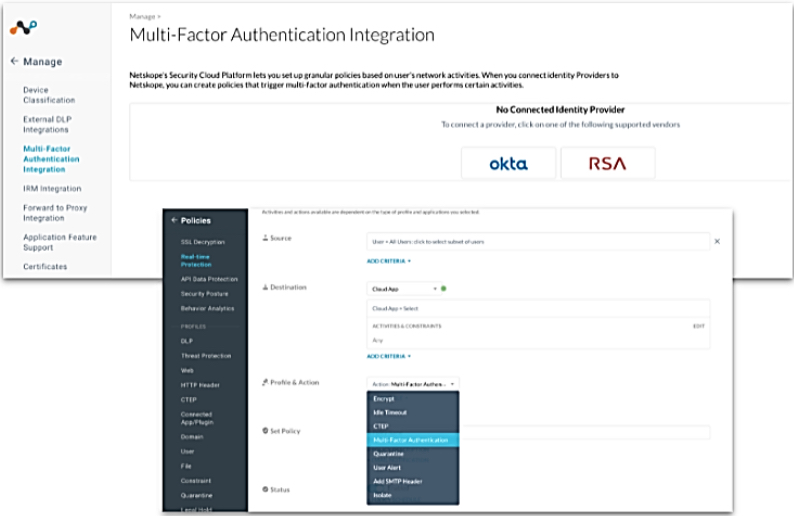
To include multi factor authentication in policies, ensure that Multifactor authentication is enabled for the tenant.
Under the Profiles & Action section in the policy creation template, select the Action = Multifactor authentication. This will help to provide layered security for higher risk activity.
To learn more: Real-time Protection Policies