Creating an IPSec Site
Note
This feature is currently in Beta. Contact your Sales Representative or Support to enable it. If you're using the previous IPSec page, see IPSec.
To create an IPSec site:
Go to Settings > Security Cloud Platform > IPSec.
Click New IPSec Site and then Create New.
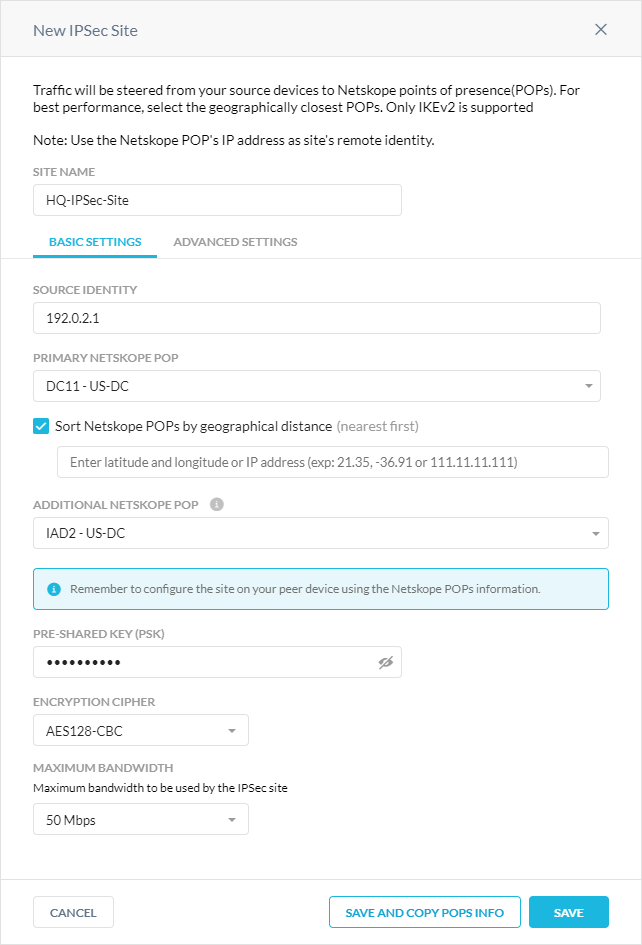
In the New IPSec Site window, for Site Name, enter a name for the IPSec site.
In the Basic Settings tab:
Source Identity: Enter an IP address, a fully-qualified domain name (FQDN), or an ID in email address format. For example, 1.1.1.1 or sourcelocation@company.com. The router or firewall uses the source identity for authentication during Internet Key Exchange (IKE). This doesn't need to be a real DNS record.
Primary Netskope POP: Select the closest primary Netskope point of presence (POP). For optimal performance, Netskope recommends using the geographically closest POPs and configuring at least two POPs for each egress location in your network.
Sort Netskope POPs by geographical distance: Select to sort the Netskope POP list by the closest geographical distance. You can search for the nearest POP by entering an IP address or longitude and latitude coordinates.
Additional Netskope POP: Select the second closest Netskope POP to use as the backup/failover site. You can select a maximum of 9 more POPs. For optimal performance, Netskope recommends using the geographically closest POPs and configuring at least two POPs for each egress location in your network.
Pre-Shared Key (PSK): Enter the pre-shared key that both sides of the tunnel will use to authenticate one another. The PSK must be unique for each tunnel.
Encryption Cipher: Select an encryption algorithm for the IPSec tunnel.
Maximum Bandwidth: Enter the maximum bandwidth for the IPSec tunnel. The tunnel size can be up to 1 Gbps.
Note
The 500 Mbps option requires an additional license. Contact your Sales Representative or Support to enable it.
The 1 Gbps option is in Beta currently. Contact your Sales Representative or Support to enable it.
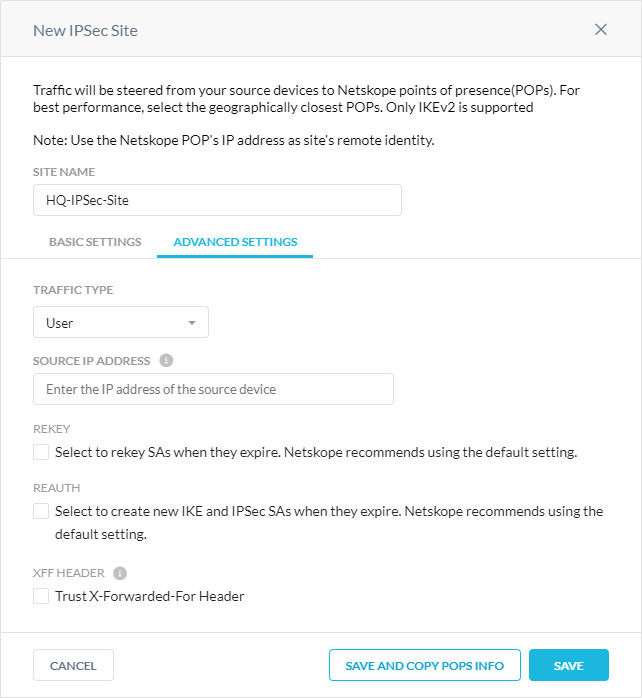
(Optional) In the Advanced Settings tab:
Traffic Type: Choose the type of traffic traversing the IPSec site.
User
IoT
Mixed
Machine
Guest Wifi
Source IP Address: Enter the source peer IP address (i.e., exit public IP) of the router or firewall that Netskope will receive packets from. Netskope identifies traffic belonging to your organization through your router or firewall IP addresses.
Rekey: Select to rekey SAs when they expire. Netskope recommends using the default setting.
Reauthentication: Select to create new IKE and IPSec SAs when they expire. Netskope recommends using the default setting.
Trust X-Forwarded-For Header: Select to trust IP addresses contained in the X-Forwarded-For (XFF) HTTP header at the tunnel level. If you trust XFF at the tenant level, you can't select this option.
Apply to all traffic: Use the XFF HTTP header to identify all user traffic going through the IPSec tunnel.
Apply to specific NAT/proxy IP(s): Use the XFF HTTP header to identify traffic from specific NAT and proxy IP addresses going through the IPSec tunnel. Click +Add Another to add multiple IP addresses.
Click Save and Copy POPs Info to save the IPSec site and copy the Netskope POP info to your clipboard. You need this information to establish the primary and backup IPSec tunnels on your router/firewall.