Certificates
Netskope certificates are used by default to trust devices. The Netskope proxy provides the following types of certificates:
Trusted Central Authority (CA)
Certificates for SSL/TLS Decryption
Certificates for Private Apps Browser Access
By default, the Netskope platform blocks connections to sites with untrusted certificates. The trusted certificates feature provides the ability to upload private, custom, and uncommon CAs to the Netskope platform. This allows you to ensure that Netskope trusts sites that are signed by a CA that is either private, or one that’s is not in our common CA store.
Prior to this feature, the only way to make this work was to allow untrusted certificates, which was a global setting (Error Settings under Steering Configuration), and would weaken security if enabled. The uploaded trusted certificates only apply to the tenant where the certificate is uploaded.
The certificate file must have a specific structure and be in PEM format. The Intermediate and Root certificates need to be combined into a single PEM file. The order of those two certs in that PEM file must be Intermediate first, and then Root below it. Finally, upload the .PEM file to the Netskope UI.
Go to Settings > Manage > Certificates.
In the Trusted CA tab, click New Trusted Cert.
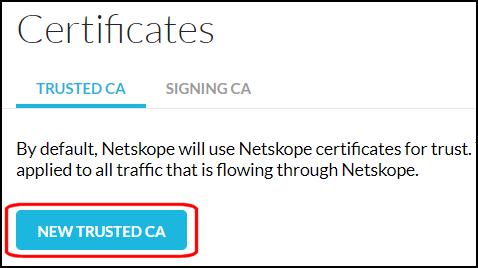
Enter a name, click Select File, and upload your certificate in PEM format.
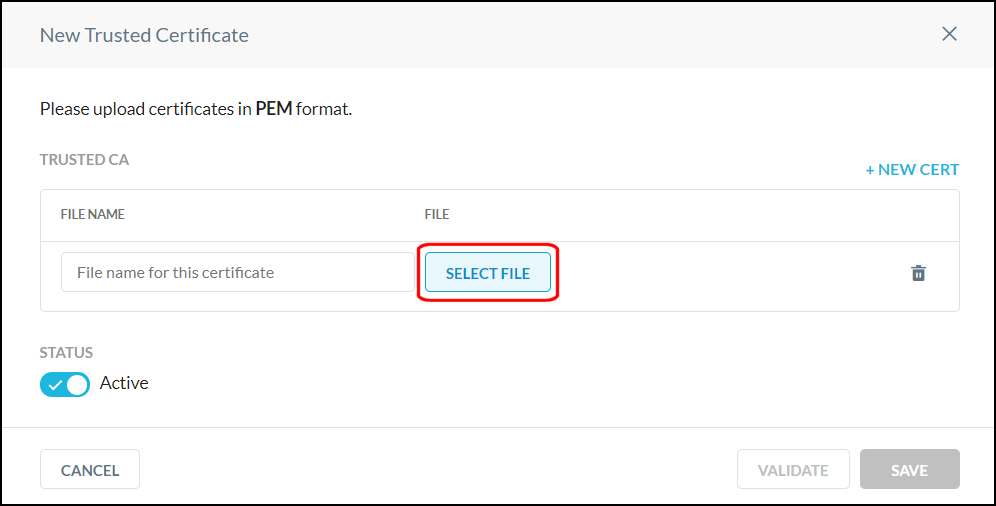
Click Validate.
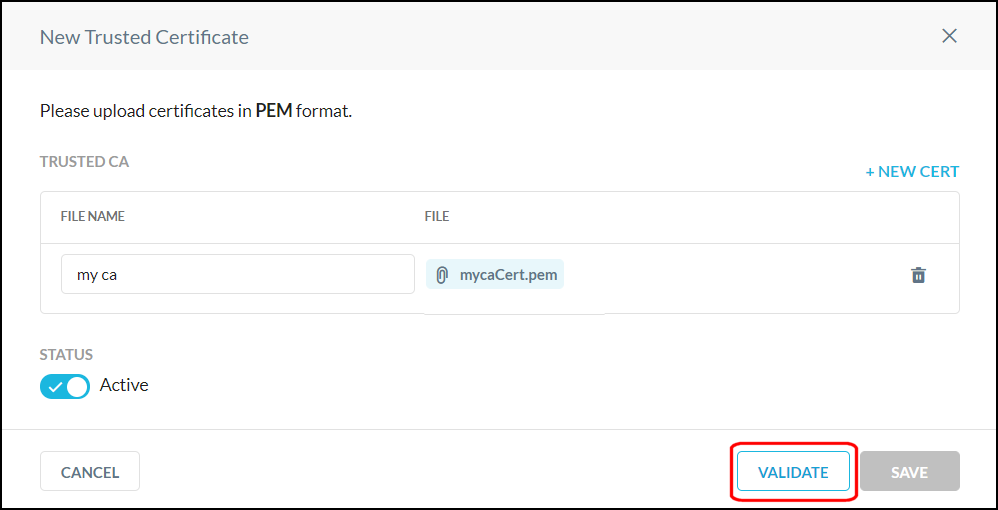
To add another certificate, click the +New Cert link.
When the Valid Certificates message appears, click Save.
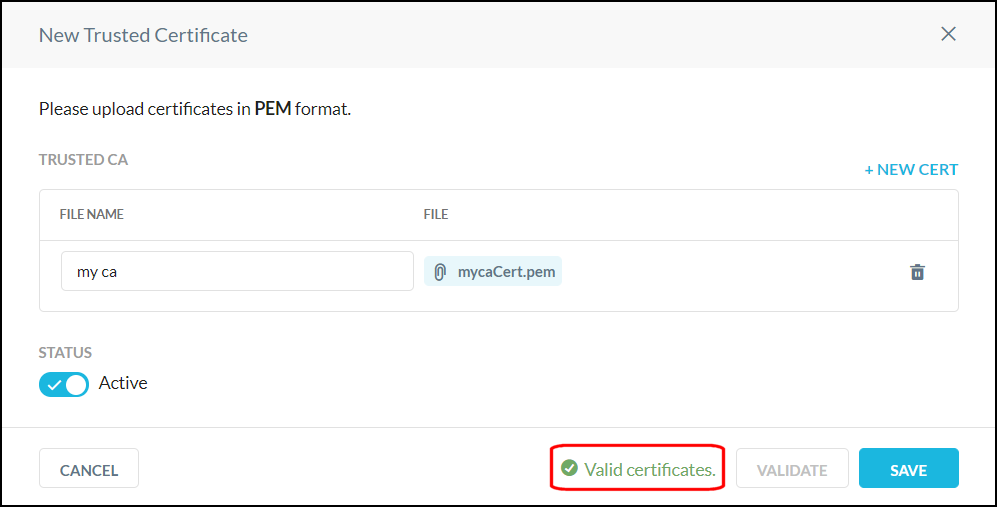
The certificate you just created appears on the page.
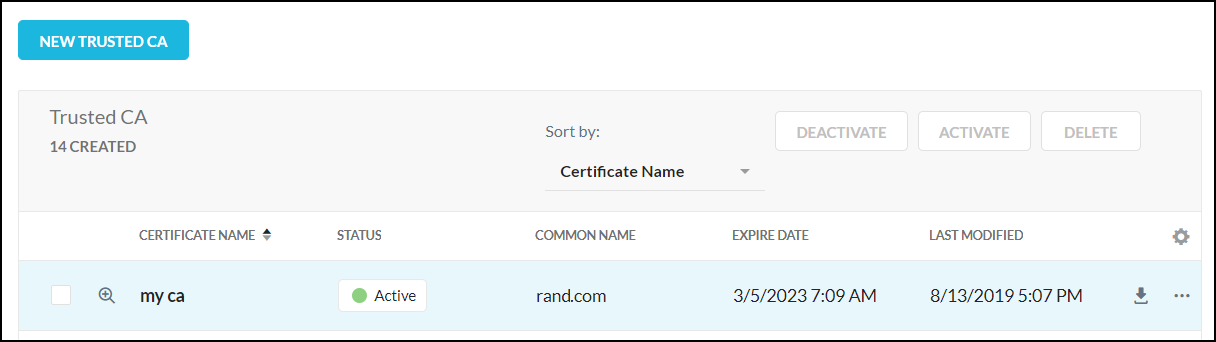 |
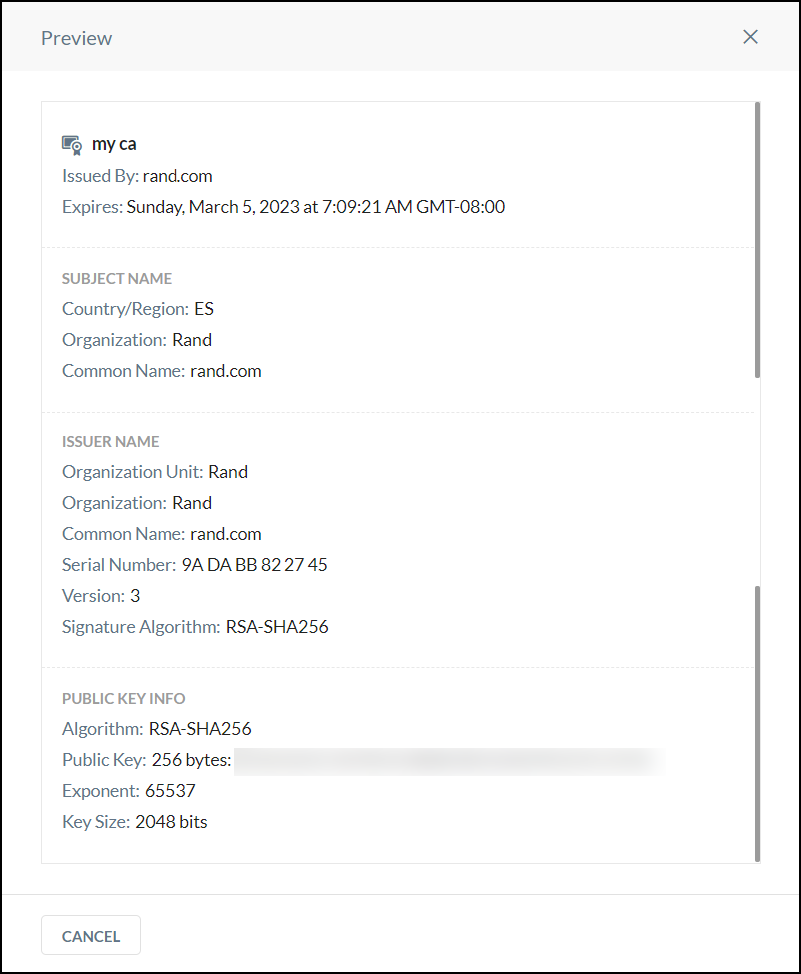
The certificate name, status, common name, expiration date, and last modification date are shown in the table . Click the Preview icon  to see a detailed view of the certificate.
to see a detailed view of the certificate.
 |
To customize the columns on the page, click the gear icon  and specify the columns you want to see.
and specify the columns you want to see.
To sort certificates shown on the page, use the Sort By dropdown list.
 |
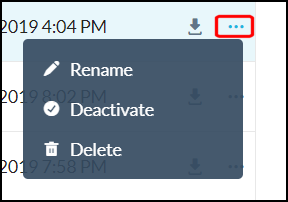
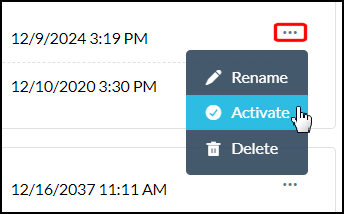
To download, rename, deactivate, and delete certificates, use the buttons above the listings or use the popup beside each listing.
 |
The Netskope proxy decrypts TLS/SSL traffic at scale. You can decrypt TLS/SSL traffic using these methods:
Signing CA (i.e., Bring Your Own Key or BYOK): Use your own signing CA certificate. This allows you to continue using your own Root CA that is installed on the endpoints without the need to install and trust Netskope’s Root CA. Contact your Netskope Sales Representative to enable this license. You can use your signing CA certificates these two ways:
Note
The Netskope certificates are the default active certificates. Multiple custom certificate sets can be created, but only one certificate set can be used (i.e., be active) at one time. Make sure the active Root CA is deployed on your end-user devices.
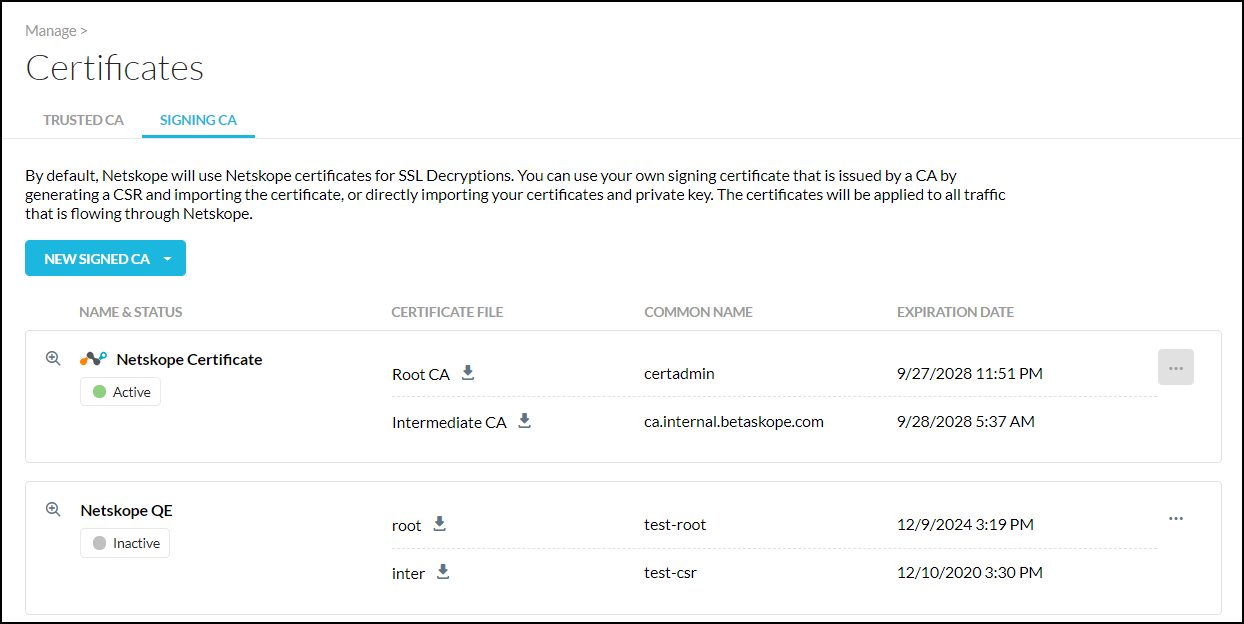
To begin, you can go to the Signing CA tab. The certificate name, status, common name, and expiration date are shown in the table. Click the Preview icon  to see a detailed view of the certificate. Once familiar with the Signing CA page, proceed to the sections below.
to see a detailed view of the certificate. Once familiar with the Signing CA page, proceed to the sections below.
 |
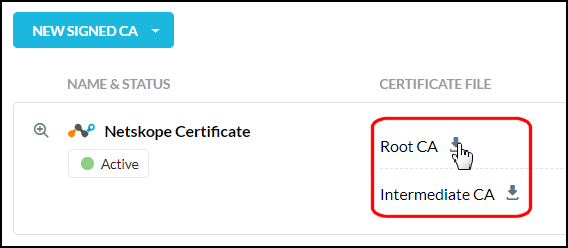
You can use Netskope’s issued Root and Intermediate CA certificates for TLS/SSL interception of inline traffic. The certificate gets auto-installed with Netskope Client installation. You can download these certificates so you can upload them to the end-user device trusted store.
To download and install the Root or Intermediate CA manually:
Go to Settings > Manage > Certificates.
Click the Signing CA tab.
Locate the Netskope Certificate and click the Download icons to download each type of certificate.
 |
Netskope Client automatically installs the Root certificate.
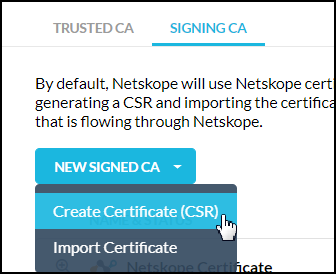
You can create a Certificate Signing Request (CSR), get it signed by your trusted CA, and then upload it to Netskope. You can upload the Root and Intermediate CA certificates (one per file), or upload the entire certificate chain (in a single file), in PEM format.
Click New Signing CA and select Create Certificate CSR
Enter these parameters:
Signing CA Name: Required. This name appears in the Name and Status column of the Signing CA page.
Common Name: Required. This name appears in the Common Name column of the Signing CA page.
Organization: The full legal name of your organization including the corporate identifier. This field is optional.
Organization Unit: Your department such as "Information Technology" or "Information Security". This field is optional.
Email Address: The email address of your organization. This field is optional.
Country: The official two-letter country code (i.e. US, CH) where your organization is legally incorporated. This field is optional.
State: The state or province where your organization is legally incorporated. This field is optional.
City: The locality or city where your organization is legally incorporated. Do not abbreviate. This field is optional.
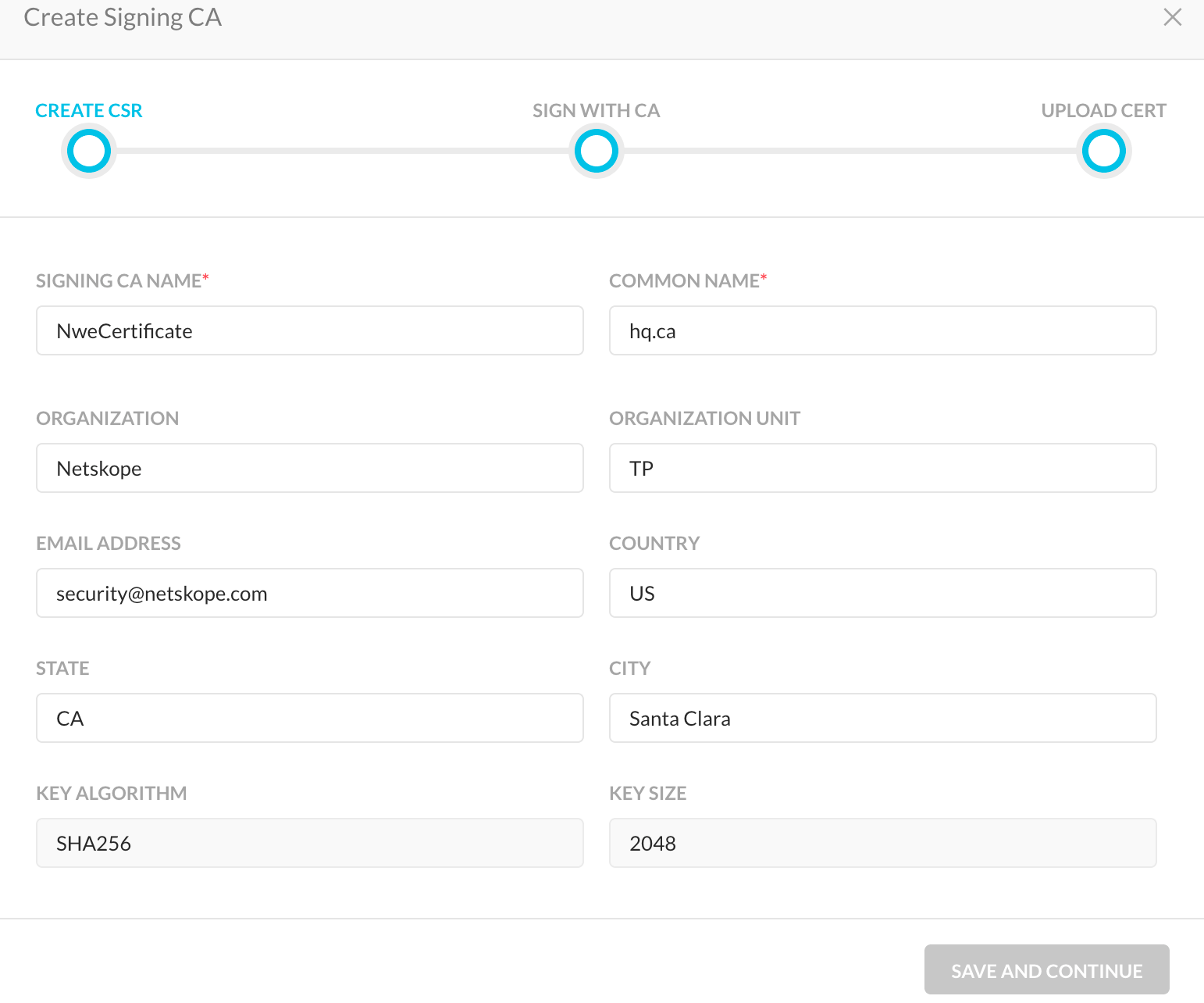
Key algorithm and key size cannot be changed. When finished, click Save and Continue.
Copy or download the CSR and get it signed by your CA. When you have it, click Next.
Enter a name for the certificate file, and click Select File. Locate and upload the file. If you are uploading individual files instead of a certificate chain, click + New Cert to upload subsequent files.
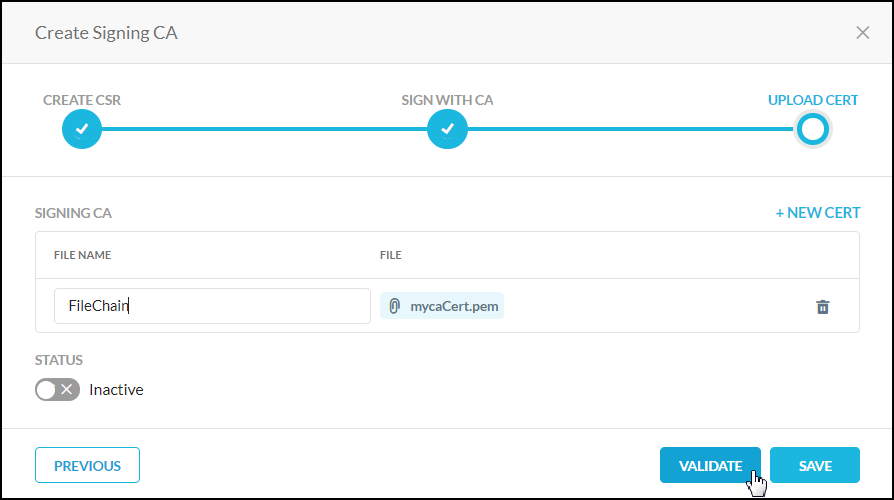
When finished, click Validate. After validation is complete, you can use the Status toggle to make the certificates active, or do so later on the main Signing CA page. Click Save.
You can import signing certificates from your CA along with the associated private key.
Click New Signing CA and select Import Certificate.
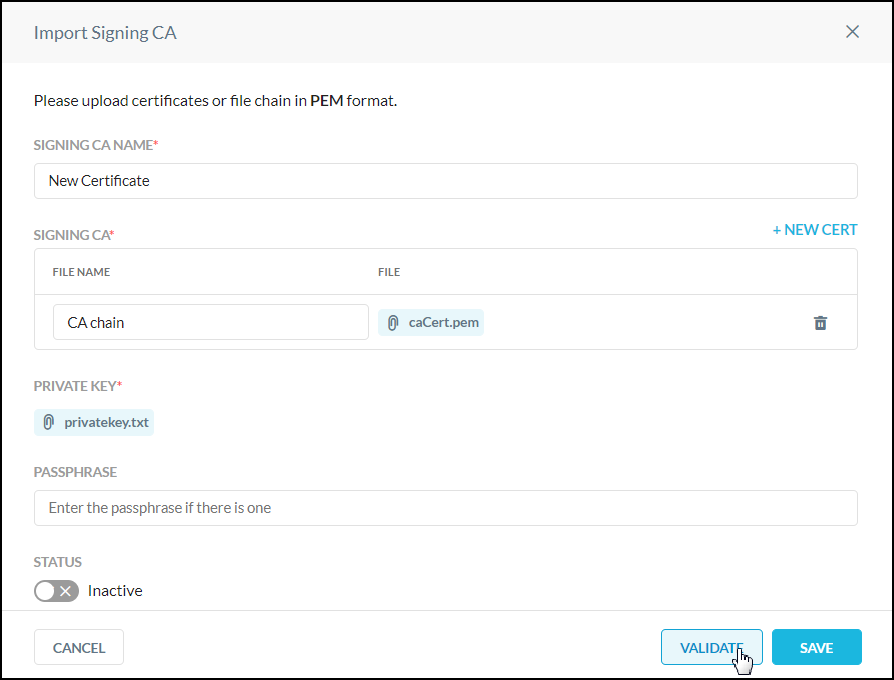
Enter a signing CA name and a file name, and then click Select File. Upload either the CA Root and Intermediate certificate files individually or the certificate chain in a single file. To upload subsequent certificate files, click + New Cert, and then enter a file name and click Select File again.
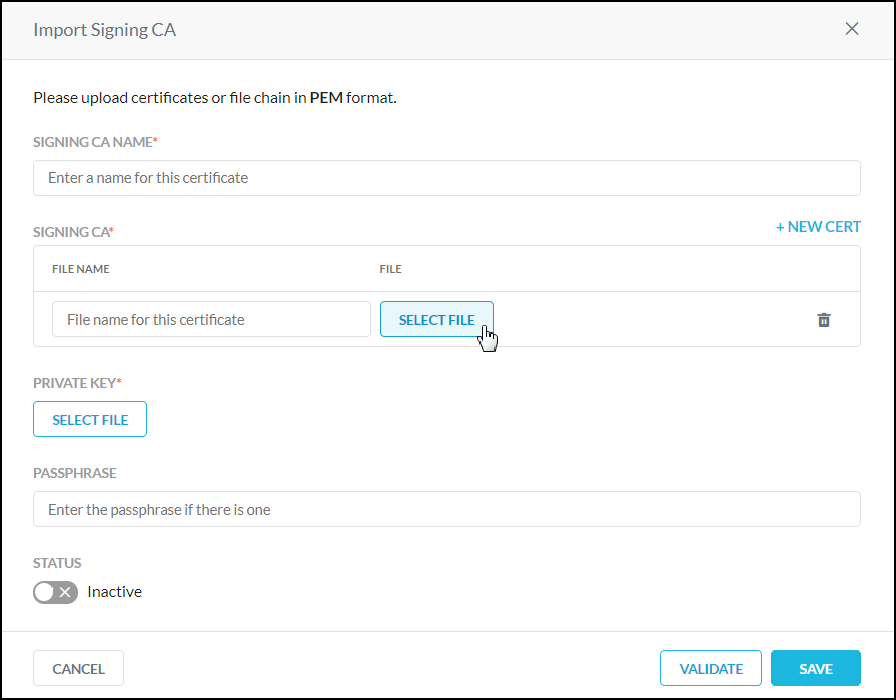
For Private Key, click Select File to upload your private key, and if a passphrase is used, enter it in the Passphrase text field.
When finished, click Validate. After validation is complete, you can use the Status toggle to make the certificates active, or do so later on the main Signing CA page. Click Save.
To use your custom certificates (if not already active), first add them, click the  icon to the right of the certificate, and then select Activate.
icon to the right of the certificate, and then select Activate.
 |
Note
Contact your Sales Representative or Netskope Support to enable this feature.
You can use your on-premises hosted HSM to sign a certificate that Netskope can use to generate an emulated certificate for TLS/SSL interception of inline traffic.
Create a private key pair inside the Key Management Interoperability Protocol (KMIP) server
Export the private key to a local secure system
Generate a CSR for the intermediate custom CA certificate and delete the private key
Sign the intermediate certificate using Root CA
This intermediate certificate will be used as the tenant certificate for the specific tenant only
You must provide the intermediate certificate to Netskope while keeping the private key inside the KMIP server
Before configuring an on-prem CA, ensure you have:
A Key Management System (KMS) server with KMIP SIGN operation support (e.g., CipherTrust Manager 170v, version 2.0.0)
A KMIP
An RSA private key cryptographic object in KMIP server
An RSA Key Pair (See Creating an RSA Key Pair in CipherTrust Manager)
Created pinhole egress-IP firewall rules that allow the following IP addresses:
31.186.239.163/24 163.116.128.36/24 163.116.131.70/24 163.116.160.5/24 163.116.206.32/25 163.116.206.2 163.116.148.2 163.116.171.24 163.116.185.2
To connect an on-prem CA:
Go to Settings > Manage > Certificates.
Click the Signing CA tab.
Click New Signing CA and then Connect On-Prem Certificate.
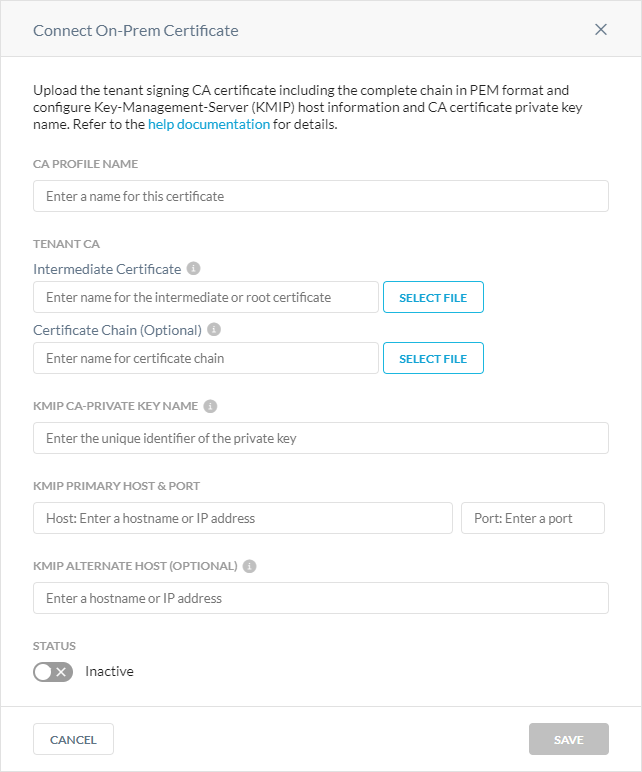
In the Connect On-Prem Certificate window:
CA Profile Name: Enter a name for the signing CA.
Tenant CA: Upload the following certificates.
Intermediate Certificate: Upload your custom intermediate CA. If you only have a root certificate, you can upload it here and leave the certificate chain empty.
Certificate Chain (Optional): Upload any other custom intermediate CAs that complete the chain to the custom intermediate or root CA you uploaded above.
KMIP CA-Private Key Name: Enter the KMIP key name for the custom CA certificate private key.
KMIP Primary Host & Port: Enter the on-prem KMIP (KMS) server primary destination host and port.
KMIP Alternate Host (Optional): Enter an alternate KMIP supported host for redundancy. You must enter a valid hostname or public IP address. Private IP addresses are blocked for security reasons.
Status: Enable or disable the certificate.
Click Validate and then Save.
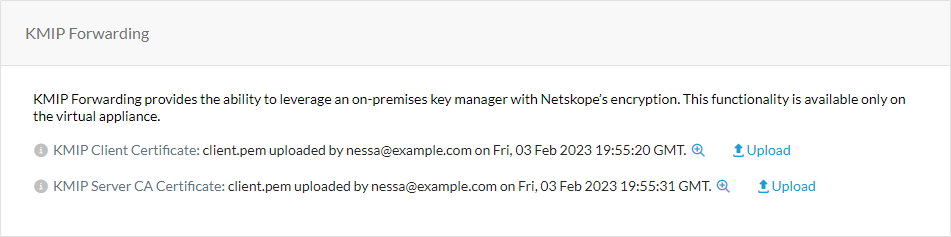
KMIP Forwarding provides the ability to leverage an on-premises key manager with Netskope’s encryption. This functionality is available only on the virtual appliance. For TLS mutual authentication of KMIP requests from the Netskope cloud to your on-premise KMIP server, you must upload the KMIP client and server CA certificates.
To configure KMIP forwarding:
Go to Settings > Security Cloud Platform > On-Premises Infrastructure.
Under KMIP Forwarding, do the following:
KMIP Client Certificate: Upload the KMIP client certificate, which Netskope uses to communicate with the on-premises key manager.
KMIP Server CA Certificate: Upload the KMIP server CA certificate, which Netskope uses to validate the server certificates used by the on-premises key manager.
Contact your Netskope Sales Representative to help validate the certificate configurations and end-to-end connectivity to the on-premise key manager.
Upload the Root CA for this certificate in the trusted store on end-user devices and browser stores for TLS/SSL interception.
Note
Only one certificate can be active for TLS/SSL decryption.
To create an RSA key pair and export it to a local secure system to generate a custom CA in CipherTrust Manager k170v:
Go to Keys & Access Management.
Click Create a New Key.
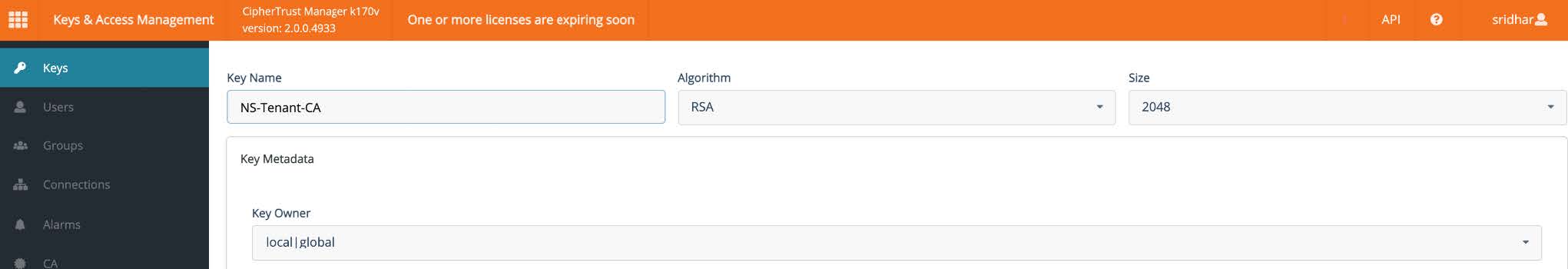
Enter the following information:
Key Name: Enter a name for the key.
Algorithm: Choose RSA.
Size: Choose 2048.
Key Owner: Enter
local|globalso Netskope can access the key.
In the Key Properties section:
Alias (KMIP Name): Set it to the key name you created in Step 3.
Key Properties: Select the following properties.
Sign
Verify
Certificate Sign
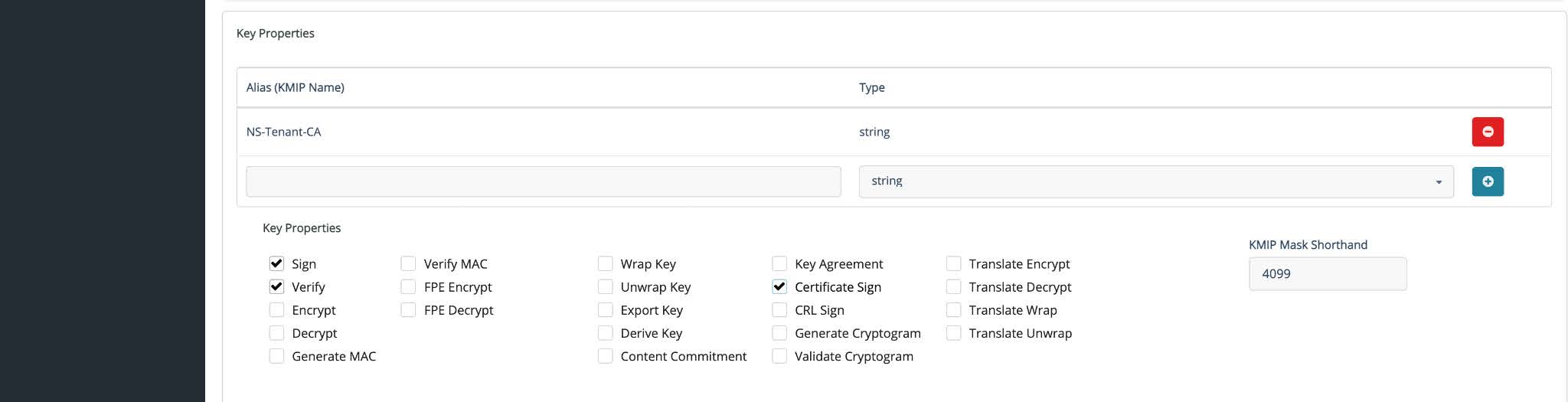
In the Key Behaviors section, deselect the following:
Prevent this key from being deleted
Prevent this key from being exported
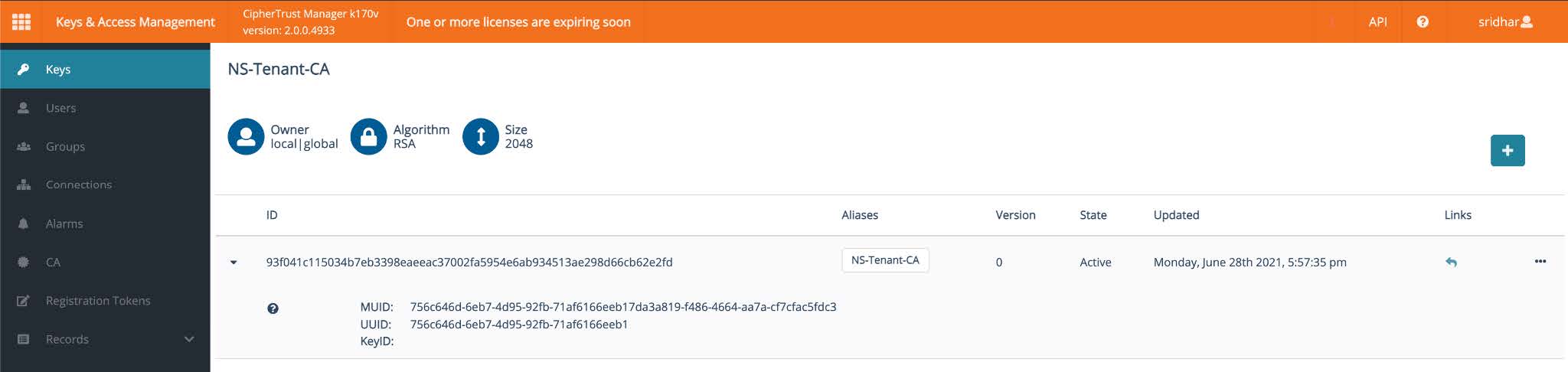
Click Create to generate the public and private crypto objects.

Click the private key object and copy the unique ID assigned from the KMS server. In this example, it's 93f041c115034b7eb3398eaeeac37002fa5954e6ab934513ae298d66cb62e2fd.
On the top right, click API.

Authenticate to use REST API, so you can download the private key material.
On the left pane, go to Keys.
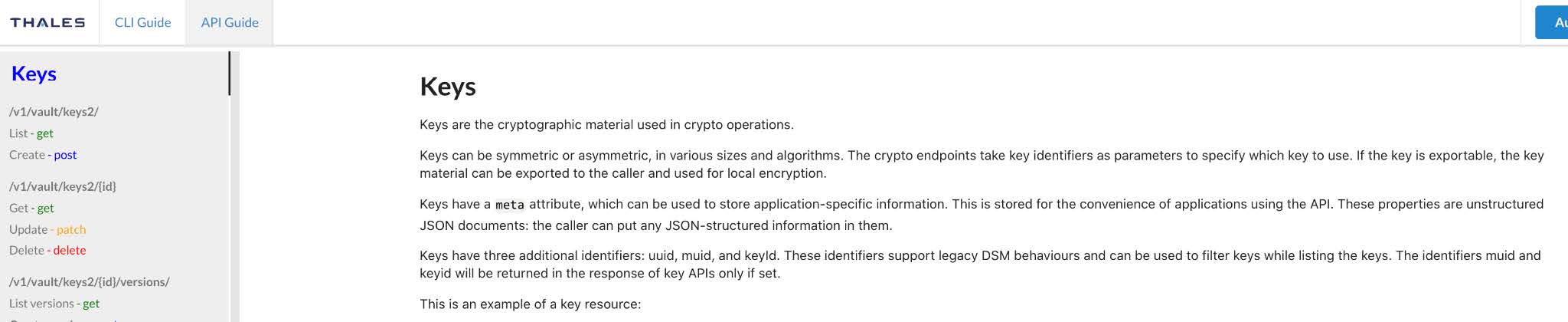
Select the Export API and enter the unique ID you copied in Step 7.
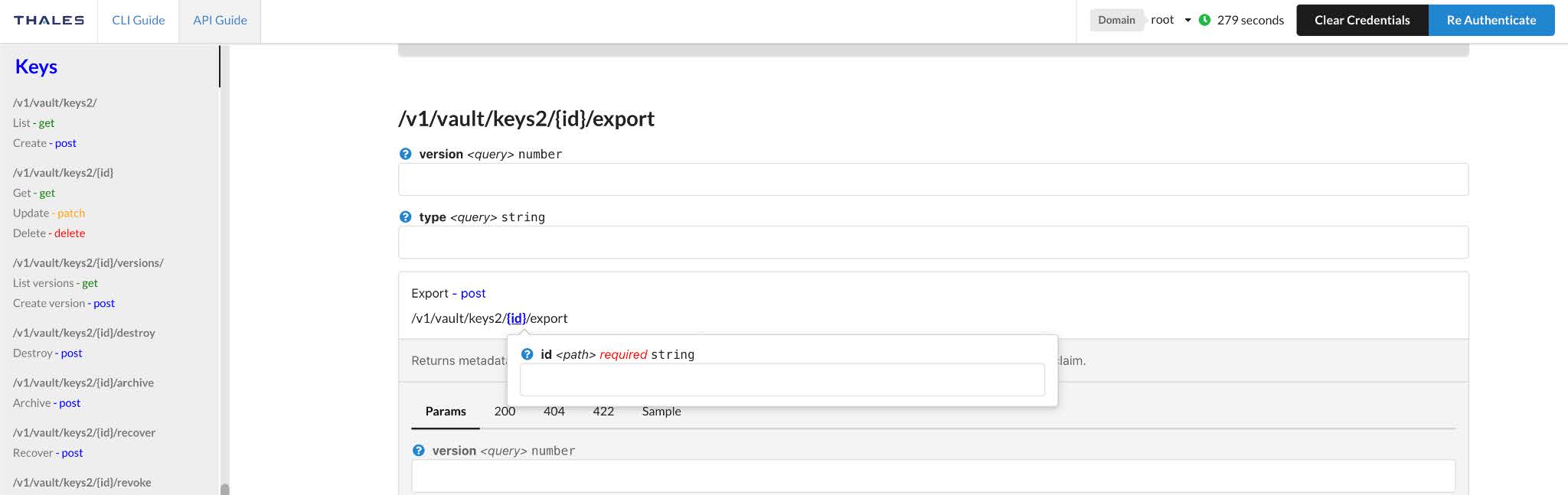
Click POST to run the API. Following is the response from the POST request, which will include all the details for the created RSA key pair:
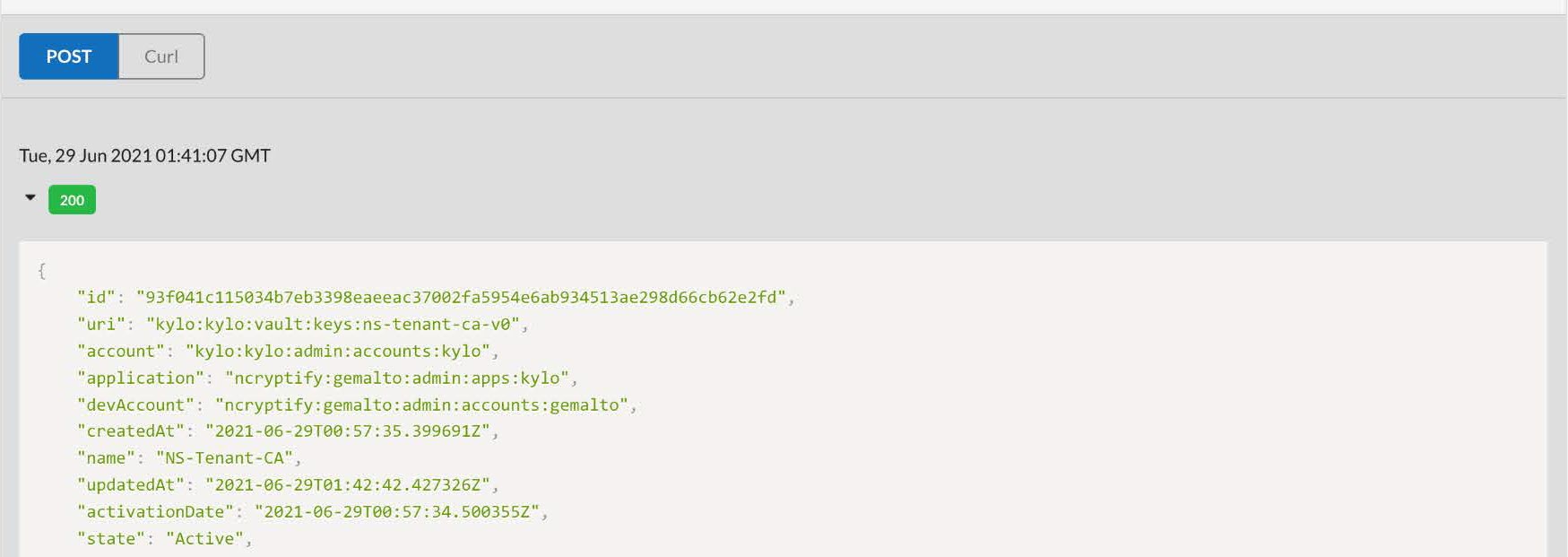
The private key can be found in the material field. Copy to a file and use it in CSR creation.
To revoke a certificate, deactivate the current activated certificate and activate the new certificate to be used. Once the new certificate is activated, the previous certificate is no longer valid for SSL/TLS decryption and it will be purged from all our data plane nodes.
After you upload a signing certificate to Netskope, Netskope initiates the following processes:
Generates and uses an encryption key specific to your organization to encrypt your certificate using Netskope’s key management system (KMS).
When users access a domain over HTTPS, Netskope:
Calls its KMS to decrypt the user-provided certificate and loads the certificate into the system memory.
Generates a server certificate for the destination site signed by your signing certificate.
Uses the server certificate to complete the HTTPS connection while allowing inspection of the user traffic by the proxy.
When steering Private Apps over Browser (agentless) Access, certificates are needed when using custom hostname.
Note
Refer to Enable Browser Access for a Private App for additional details about how to configure NPA over Browser Access.
Note
For Netskope-encoded URLs with the suffix *.npaproxy.goskope.com, Netskope will serve a certificate that is already signed by a trusted Certificate Authority.
The following instructions explain how to upload certificates on the Certificates page, but you can also upload certificates when creating an Private App Definition by clicking Upload the Certificate.
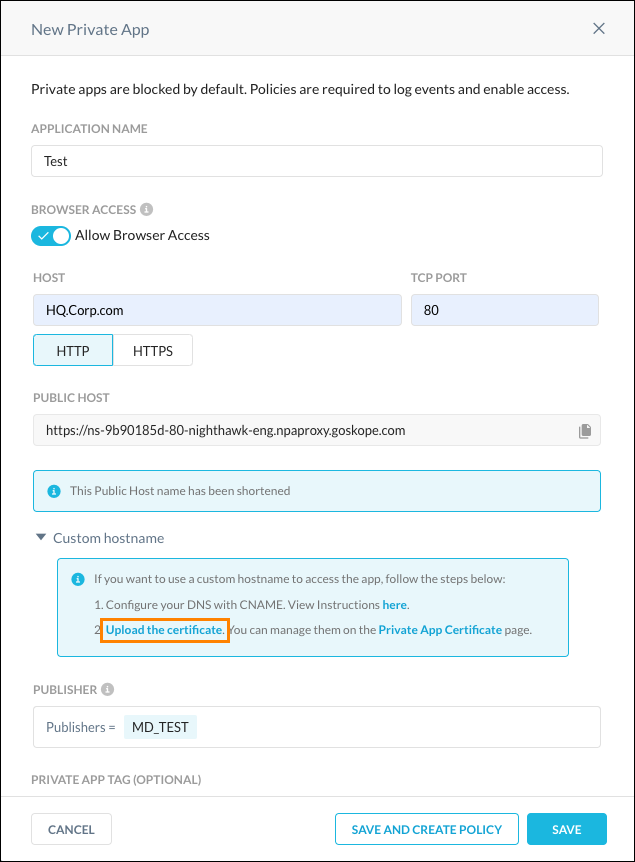 |
To create a new certificate for Browser Access:
Go to Settings > Manage > Certificates.
Select the Private App Cert tab and click New Certificate.
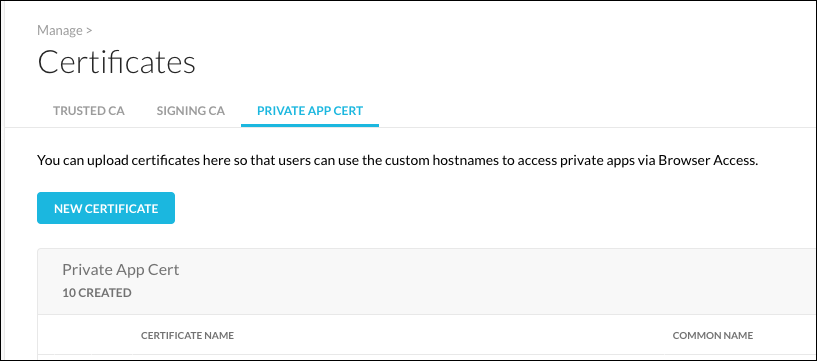
Enter a name, and then upload your certificate chain and private key in PEM format. The server certificate should be on top, followed by the rest of the chain, with the root certificate at the bottom.
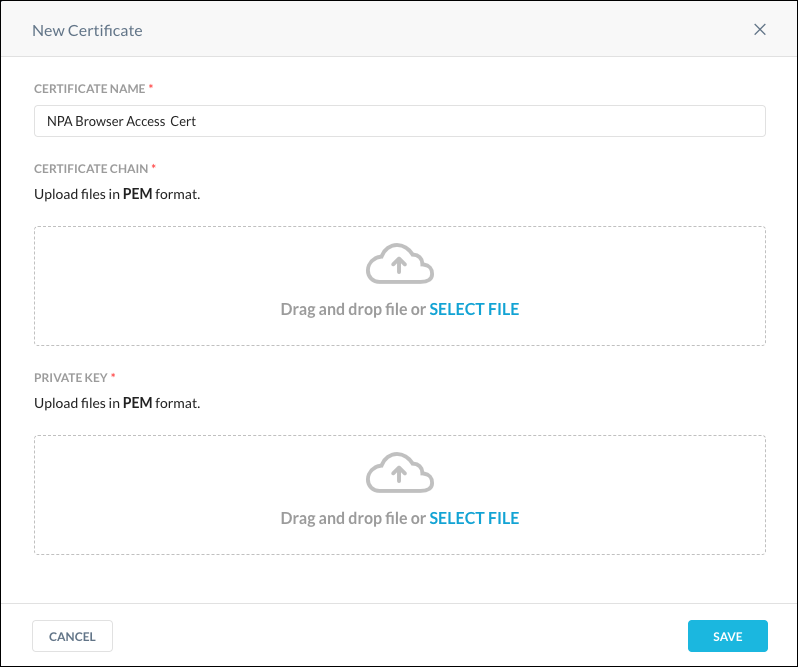
Click Save.
The certificate you just created appears on the page. The Gear icon enables you to customize the columns shown on the page.
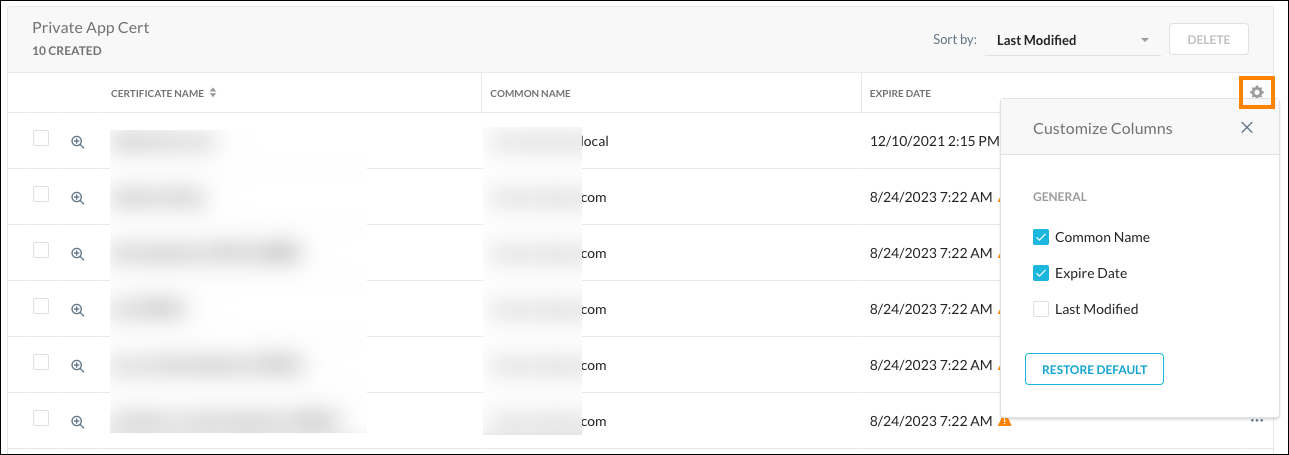 |
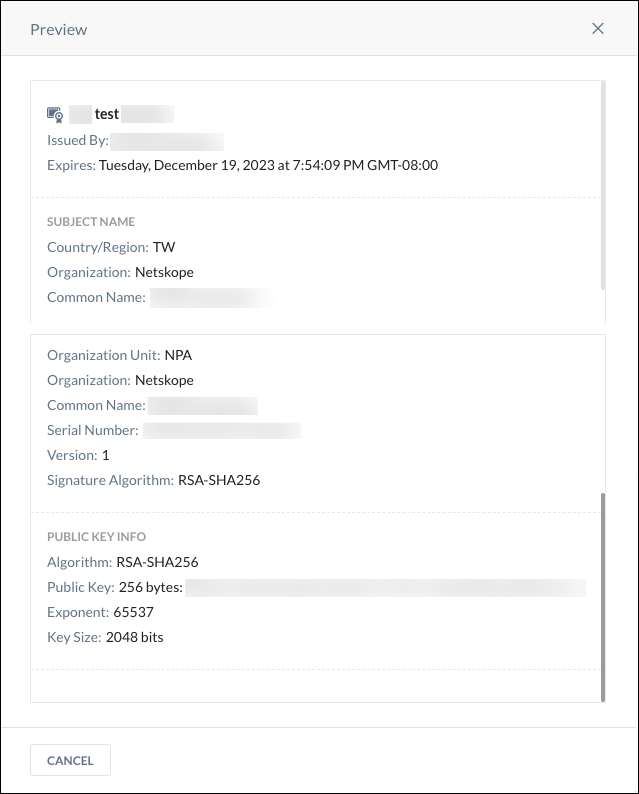
The certificate name, common name, expiration date, and last modification date are shown in the table. Click the Preview icon  to see a detailed view of the certificate.
to see a detailed view of the certificate.
 |
To sort certificates shown on the page, use the Sort By dropdown list.
 |
To rename a certificate, use the popup beside each listing.
 |