Integrating Carbon Black for EDR
Before you begin, make sure you have your Carbon Black API key and server IP address; these are needed to complete this procedure.
To configure a Carbon Black integration:
Go to Settings > Threat Protection > Integration.
Click the Carbon Black application box.
Enter and select parameters for each field:
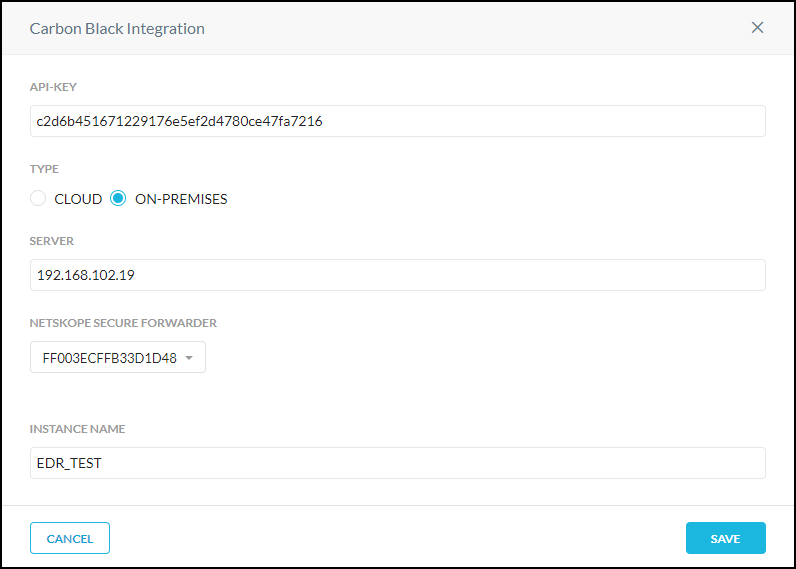
API Key: Enter your API key.
Type: Select Cloud or On-premises to specify whether the endpoint server is cloud-based or local (on-premises). On-premises requires a Netskope Secure Forwarder integration.
For On-Premises appliance integrations, select the serial number of your Secure Forwarder from the dropdown.
Tip
For specifics about Secure Forwarder integrations, go to Settings > Security Cloud Platform > On-Premises and click On-Premises Infrastructure. The Infrastructure section on this page displays the serial numbers of your appliances.
Server: Enter the IP address or FQDN of your Carbon Black server.
When finished, click Save.
After configuring Carbon Black:
Create a Remediation Profile that specifies this Carbon Black integration.
Go to Policies > Threat Protection > Remediation Profiles, and then click New Malware Remediation Profile.
Select the Carbon Black EDR server and the Actions to perform (Isolate, Alert, or Add to Watchlist/Blocklist). When finished, click Next.
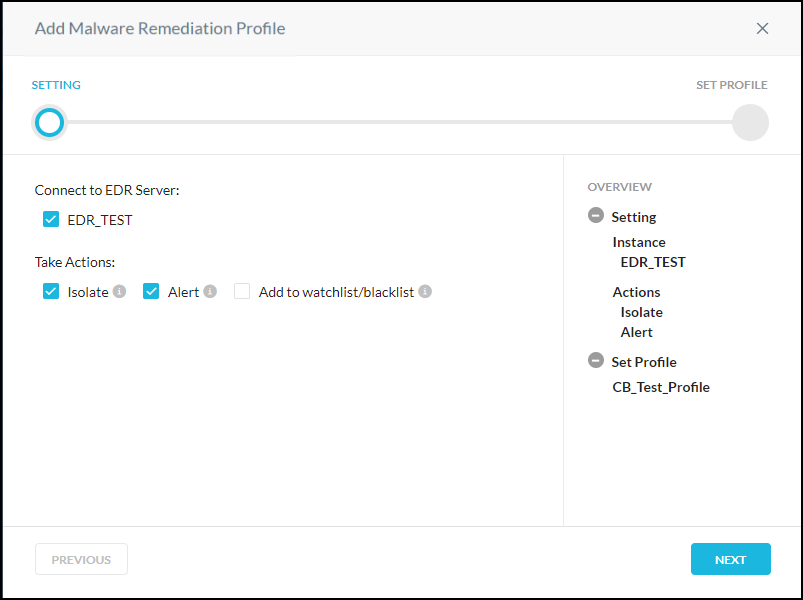
Name the profile and click Save Malware Remediation Profile.
Specify the Remediation profile in an API Data Protection or Real-time Protection policy (for Real-time Protection, see the next step).
For an API Data Protection policy, go to Settings > Threat Protection > API Data Protection. Scroll down to the Settings section and click Edit Settings. Enable one or more Remediation Endpoints checkboxes, depending on severity preferred, and then select the Carbon Black remediation profile. When finished, click Save.
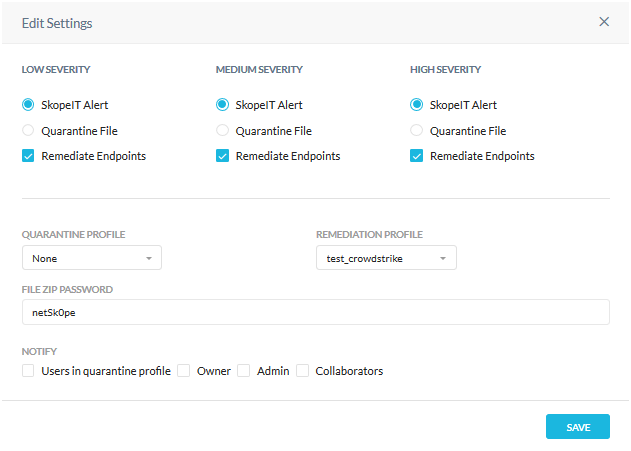
For more details about using threat protection in an API Data Protection policy, refer to: Creating a Threat Protection Policy for API Data Protection.
For an Real-time Protection policy, go to Policies > Real-time Protection and click New Policy. While creating the policy, in the Action section, select an an option from the Action dropdown list, and then select a Carbon Black Remediation profile from the dropdown list. Finish creating the Real-time Protection policy.
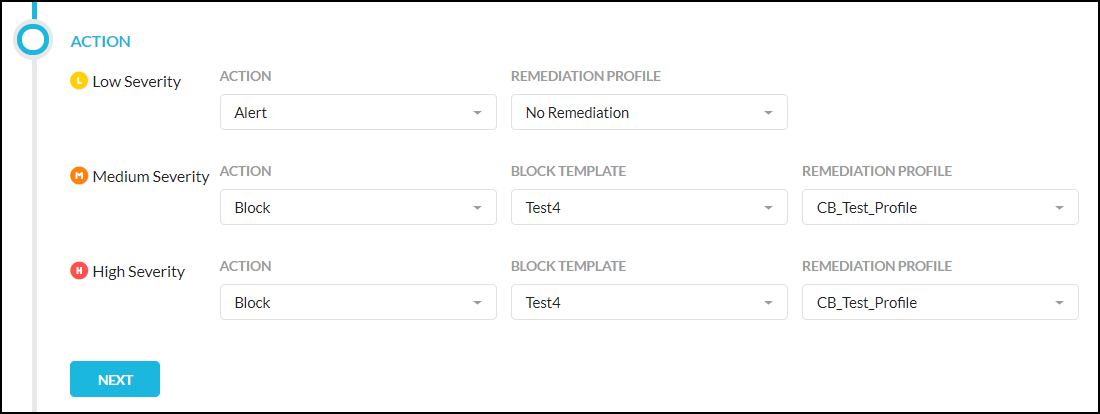
For more details about using threat protection in an Real-time Protection policy, refer to: Creating a Threat Protection Policy for Real-time Protection
After a Remediation Profile has been added in policy settings, Remediation alerts will get generated in Skope IT when malware gets detected.