Identify Malware in data repositories and action per defined policy
Prerequisites for the API protection use cases | Roles/actors in the use cases |
|---|---|
|
|
To enable malware scan in data repositories which are API protected services, follow the steps shown below:
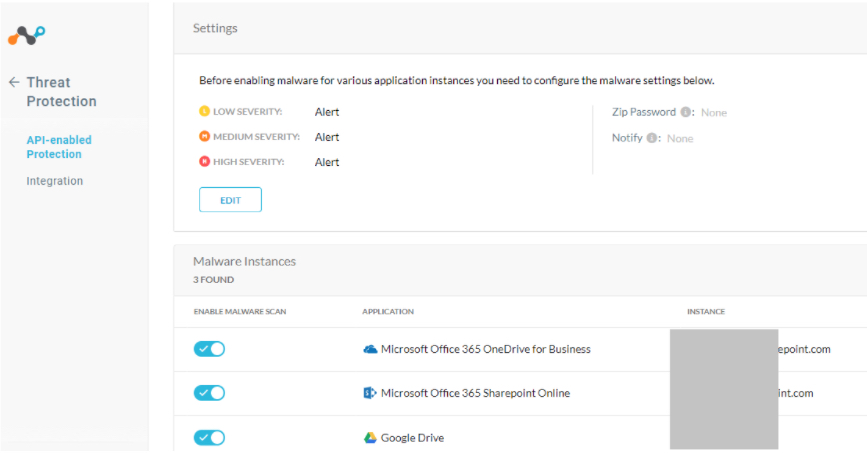
Navigate to Settings > Threat Protection > API enabled protection.
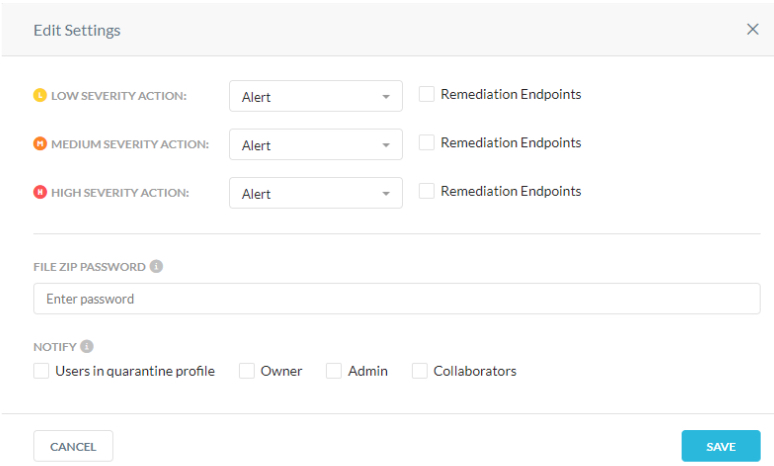
Under Settings, click ‘Edit’ and select the options for actions to be taken based on severity of the malware.
Enable the Malware scans for instances of the API protected services.
Edit Settings:
To learn more: Understanding API Protection