Virtual Appliance Overview
A Virtual Appliance (VA) can be configured to run on VMware ESX, Microsoft Hyper-V, Linux KVM, and AWS AMI. The VA can be deployed as a Log Parser, Secure Forwarder, or a proxy server.
Log uploads provide a quick and easy way to discover cloud apps in your environment and provide a baseline assessment of the risk to using these cloud apps.
You can upload the log files from your enterprise web proxy, next generation firewalls, and other devices to the tenant instance in the Netskope cloud. Netskope Risk Insights can parse these logs to provide insight into the cloud apps being used.
The On-Premises Log Parser (OPLP) Virtual Appliance (VA) can be deployed onsite so you can upload log files. All log processing happens locally, and only the extracted events are sent to your tenant instance in the Netskope cloud.
Note
This document is dedicated to the hybrid data plane on-premises management in the cloud deployment mode; there's a separate guide if you are managing appliances on-premises.
The target audience for this document includes IT administrators and security specialists.
Benefits of the OPLP include:
Local log parsing before sending extracted events to the tenant instance
Obfuscation of sensitive information before sending it to the tenant instance
You can upload logs to the OPLP in two ways.
Upload logs through SFTP or SCP to the VA.
Configure the OPLP VA as a syslog server to stream syslog messages directly from the firewall or proxy server.
Prerequisites
We do not recommend deploying both the Log Parser and Secure Forwarder on the same VA for performance reasons. For installation instructions on deploying the Secure Forwarder, go to Settings > Security Cloud Platform > On-Premises Infrastructure and click Installation Instructions.
If you haven't already, download a virtual appliance (VA) package. Go to Settings > Security Cloud Platform > On-Premises Infrastructure and click one of the VA buttons to download it. Downloading the VA zip file requires 7 GB of free space, plus you must unzip the file using 7zip. Using another tool creates a false error saying 789 PB of space is required.
The downloaded VA has a starting point requirement of 8 CORES, 32 GB RAM and 400 GB disk space. Requirements vary depending on the amount of logs that needs to be processed per day. Refer to the OPLP Sizing Guide for more information.
The OPLP VA requires certain ports to be open; refer to the Outbound Ports and Inbound Ports sections below for more details.
Supported Log Formats
Netskope currently supports the following log formats:
Device | Log Format |
|---|---|
CiscoASA | asa,asasyslog |
BroIDS | broids |
Check Point | chkp |
Cisco Catalyst | ciscofwsmsyslog |
Cisco IronPort | ciscowsa, ciscowsasyslog |
Fortinet | fortigate |
Bluecoat logs sent to Greenplum logserver | greenplumbluecoat |
MicrosoftISA | isasplunk |
Juniper SRX | junipersrxstructuredsyslog, junipersrxunstructuredsyslog |
Mcafee Web GW | mcafee |
Juniper Netscreen | netscreentraffic |
Palo Alto Networks | panw,panwsyslog |
Blue Coat | proxysg, proxysghttpmain |
Blue Coat logs exported in Websense format | proxysgwebsense |
Cisco ScanSafe | scansafe |
Sensage SIEM | sensage |
Sonicwall | sonicwallsyslog |
Squid Proxy | squid |
Sophos Web Gateway | sophos |
Symantec Web Security | Symantecwebsecurity |
Trustwave | trustwave |
Websense | websense |
Zscaler | zscaler |
Netskope log based discovery requires the destination URL in addition to the destination IP address to accurately identify and map cloud apps. Since most service providers use netblocks to host their services, a destination IP address can be shared by multiple services and therefore, the destination IP address alone does not provide sufficient information required to identify the cloud app.
Netskope recommends either turning on SSL decryption on your firewall or proxy server to capture the destination URLs in the logs so that Netskope can more accurately determine the cloud app service in use, or steering user traffic through Netskope cloud for the most accurate understanding of apps, tenants, and activities.
Log requirements:
The log file must have the extension .csv, .cef(*), .leef(*), or .log, like 20160301.log.
You can compress the logs before uploading. Bzip, zip and gzip are currently supported.
Each compressed file can contain only one single log file.
Make sure to upload the log to the correct log folder. For example, for checkpoint logs, use the
upload/chkpfolder, and for Blue Coat Proxy logs useupload/proxysghttpmainfolder, and so on.
Please reach out to your SE to learn if there are any new log formats that are not listed.
Supported Character Encoding
Netskope supports ASCII and UTF-8 character encoding formats.
Outbound Ports
Use these ports for management connectivity and log uploads.
Note
In release 46
domain names changed. Using version 46 and later requires using the new domain
names. Existing deployments (release 45 and prior) do not require the new
domain names, but using them are recommended. The one required update is for
auto-updates; either turn off auto-update or use the new
download-<tenant
hostname>.goskope.com domain name. New deployments with
release 46 and higher do need to use the new domain names.
For management connectivity:
Domain | Description | Port |
|---|---|---|
New: Old:
| Use for configuration updates. The domain needs to be SSL allowlisted if you have SSL decryption enabled. | 443 |
New:
Old:
| Use for software upgrades. | 443 |
New:
Old:
| Use for reporting and status updates in the UI. The domain needs to be SSL allowlisted if you have SSL decryption enabled. | 443 |
New:
Old:
| Use for receiving metrics from on-premises appliances and forwarding them to cloud tenants, as well as receiving event data from an on-premises dataplane appliances. Also for receiving custom user attributes from user endpoints. The domain needs to be SSL allowlisted if you have SSL decryption enabled. | 443 |
Note
For international deployments, use ~
-<tenant
hostname>.eu.goskope.com or ~
-<tenant
hostname>.de.goskope.com.
For log uploads:
Domain | Description | Port |
|---|---|---|
New:
Old:
| Use for sending logs to the Netskope cloud with SFTP. This is the default port for log uploads. | 22 |
No change:
| Use for sending logs to the Netskope cloud with HTTPS. This port is enabled by default. | 443 |
No change:
| Use for fetching the REST API token with HTTPS. | 443 |
Note
For international deployments, use ~
-<tenant
hostname>.eu.goskope.com or ~
-<tenant
hostname>.de.goskope.com.
Inbound Ports
Service | Description | Port |
|---|---|---|
Syslog | Use for receiving syslog traffic. | 514 |
AD Connector | Use for getting IP-to-user mapping with the Netskope AD connector. | 4400 |
SFTP and SCP | Use for management connectivity and log uploads to the log parser appliance. | 22 |
FTPS | Use for management connectivity and log uploads to the log parser appliance. | 21 (using explicit SSL) |
Note
Netskope does not support implicit ssl over port 990.
OPLP Sizing Guide
To ensure you have enough processing power for the amount of logs being processed, review these guidelines. Keep in mind these guidelines are for predefined parsers; core and RAM requirements for custom parsers vary depending on the complexity of the logs.
Expected Log Traffic | Cores Required | RAM Required | Disk Space Required |
|---|---|---|---|
Approximately 72 GB per day or 3 GB per hour | 8 | 32 GB | 400 GB |
Approximately 144 GB per day or 6 GB per hour | 16 | 64 GB | 600 GB |
Approximately 216 GB per day or 8 GB per hour | 24 | 96 GB | 900 GB |
Netskope recommends the following when deploying an OPLP appliance for the first time.
Deploy the VA to the default disk storage without adding additional storage.
Create a new disk such as vmdk, vhdx, as appropriate for your hypervisor.
Add a new disk to the appliance.
Run the following commands to increase the root or log partition.
troubleshooting expand-partition root OR troubleshooting expand-partition log
For information about increasing partition size, refer to Increase the size of the partition.
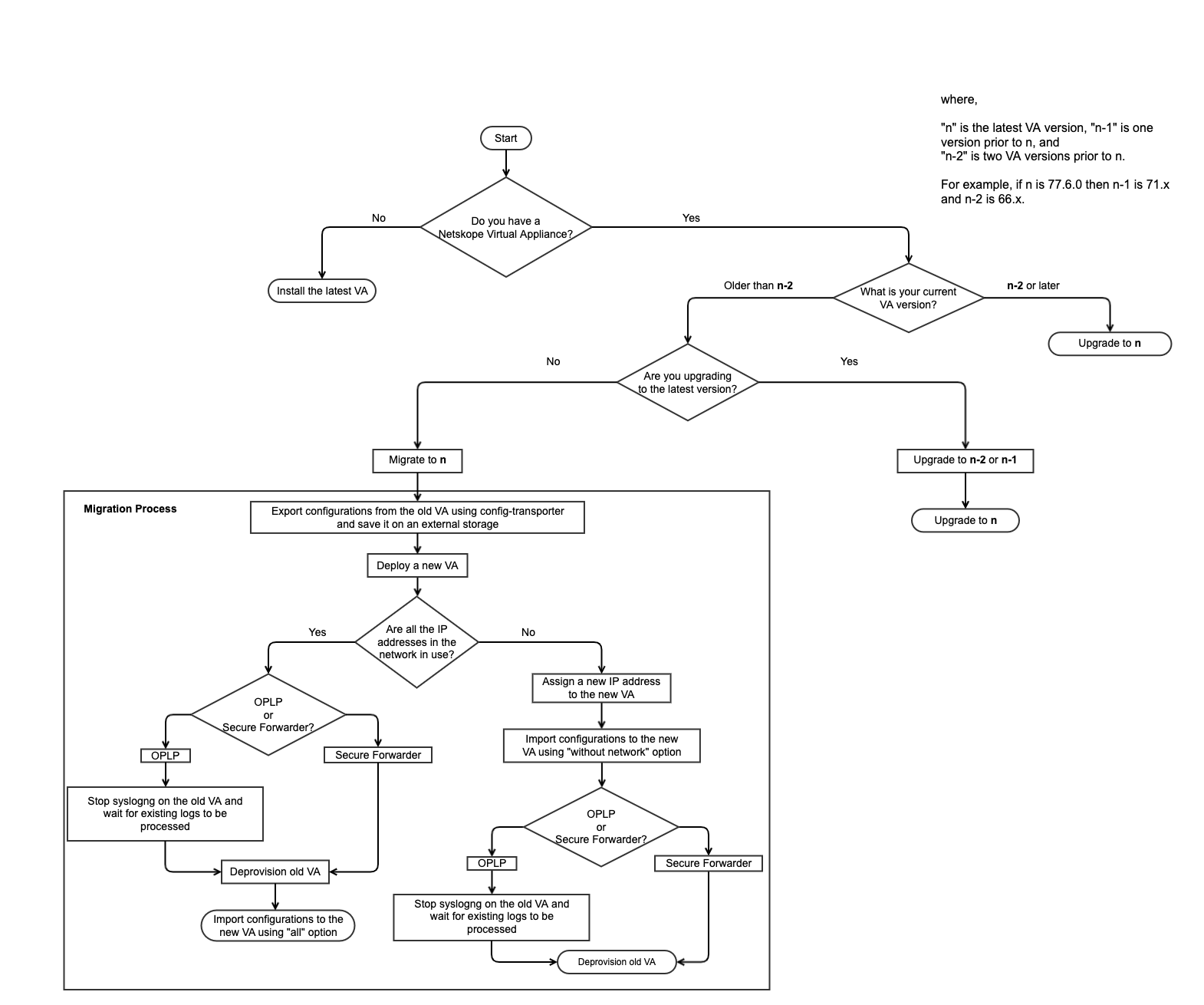
Understanding the Software Installation, Migration, and Upgrade
The flow chart describes the process you can follow to install, migrate, or upgrade the virtual appliance. For the detailed installation, migration, and upgrade procedures, refer to the following topics: