Managing Error Settings
You can use the steering error settings to configure actions for anomalies observed in the HTTP/HTTPS traffic.
Note
Netskope doesn't perform SSL inspection for any bypassed traffic in the error settings.
To configure the error settings for your steering configurations:
Go to Settings > Security Cloud Platform > Steering Configuration.
Click Manage Error Settings. The Error Settings window appears. All error settings are global.
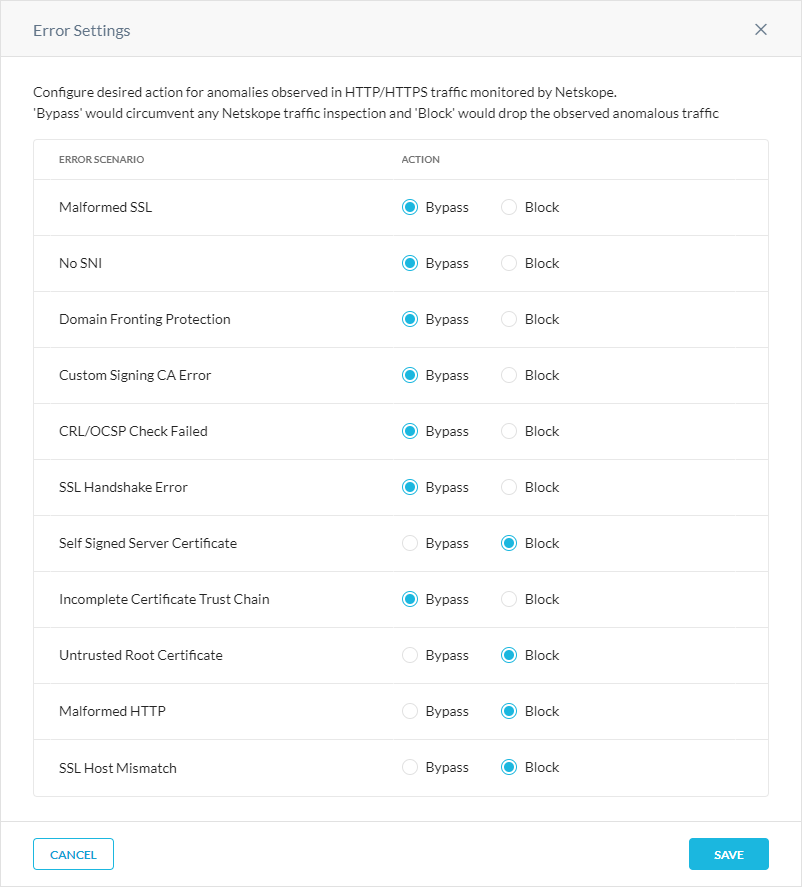
In the Error Settings window:
Note
Due to a limitation, when you select Bypass for SSL failure actions (e.g., Incomplete Certificate Trust Chain), the first connection to a given site on a given node will receive a block page while Netskope caches the certificate’s status. Users must reload the page to continue to the site.
No SNI: Bypass or block traffic between the Netskope Client and the Netskope Cloud Proxy if the Netskope Cloud Proxy can't determine the Server Name Indication (SNI).
Malformed SSL: Bypass or block traffic between the Netskope Client and the Netskope Cloud Proxy if the designated port is 443 but fails to parse the first packet in the SSL traffic.
Domain Fronting Protection: Bypass or block traffic between the Netskope Cloud Proxy and the internet server if domain fronting is detected. Netskope detects domain fronting when the SNI and HTTP request Host header are mismatched. Selecting Bypass ignores mismatches.
There are cases where the SNI mismatches the Host header, or research teams use domain fronting for testing purposes. Before configuring the Domain Fronting Protection feature, Netskope recommends using it in monitor mode first by reviewing the transaction events for domain-fronted fields and domains to gain granular understanding of domain-fronted sites.
Caution
The Domain Fronting Protection option is a global setting and will be applicable to all websites. If you experience blocked traffic to legitimate domains, update the Domain Fronting Protection option to Bypass to unblock the traffic immediately. Then contact Netskope Support to report the domains that were blocked.
Additionally, HTTP/2 is not currently supported for Domain Fronting Protection. Using this feature with HTTP/2 might cause HTTP/2 websites to not load properly or to load slowly without error notifications.
Custom Signing CA Error: When the Netskope proxy is reloading due to planned upgrades, block or bypass (fail open) HTTPS requests during the Netskope proxy re-booting time. This is only applicable when the custom signing CA feature is used for inline TLS decryption, which allows customers to upload their own certificate for TLS decryption without trusting Netskope’s root CA.
CRL/OCSP Check: Block traffic between the Netskope Cloud Proxy and the internet server if the server’s certificate is revoked. Netskope terminates SSL for this error and performs deep packet inspection for failed CRL and OCSP checks. Selecting Bypass ignores mismatches and failures.
SSL Handshake Error: Bypass or block traffic between the Netskope Cloud Proxy and the internet server if the SSL handshake fails.
Self-Signed Server Certificate: Bypass or block traffic between the Netskope Cloud Proxy and the internet server if the server’s certificate is self-signed.
Incomplete Certificate Trust Chain: Bypass or block traffic between the Netskope Cloud Proxy and the internet server if the server’s certificate chain is incomplete.
Untrusted Root Certificate: Bypass or block traffic between the Netskope Cloud Proxy and the internet server if the server’s certificate isn't trusted.
Malformed HTTP: Bypass or block traffic between the Netskope Client and the Netskope Cloud Proxy if the Netskope Cloud Proxy receives an invalid HTTP request.
SSL Host Mismatch: Block traffic between the Netskope Cloud Proxy and the internet server if the domain name of the server doesn’t match the common name in a server’s certificate. Netskope terminates SSL for this error and performs deep packet inspection for SSL host mismatches. Selecting Bypass ignores mismatches and failures.
After configuring the error settings, the steering configuration starts bypassing or blocking extranet services.
Error Settings
Below are the Netskope error settings that you can configure for your organization to optimize security:
Error Setting | Default Setting | User Notification Type |
|---|---|---|
No SNI | Bypass | Browser |
Malformed SSL | Bypass | Browser |
Domain Fronting Protection | Bypass | Browser |
CRL/OCSP Check | Bypass | Browser |
SSL Handshake Error | Bypass | Browser |
Self-Signed Server Certificate | Block | Browser |
Incomplete Certificate Trust Chain | Bypass | Browser |
Untrusted Root Certificate | Block | Browser |
Malformed HTTP | Block | None |
SSL Host Mismatch | Block | Browser |