Cloud Exchange Users
New users can be added only by the Super Admin (user with the admin user name). There are these types of user roles:
Admin: An Admin has write level access to the application, and will be able to create configurations, upload plugins, configure sharing, and edit settings.
Read-only User: The read-only user will have limited access to the application, and will not be able to perform any edit or update actions on plugins and their configuration settings.
Custom Admin: The users can be given custom read/write permissions so they can perform module-specific admin actions based on the type of permissions provided.
The Users page displays all the current users in a table. Users can be edited or deleted.
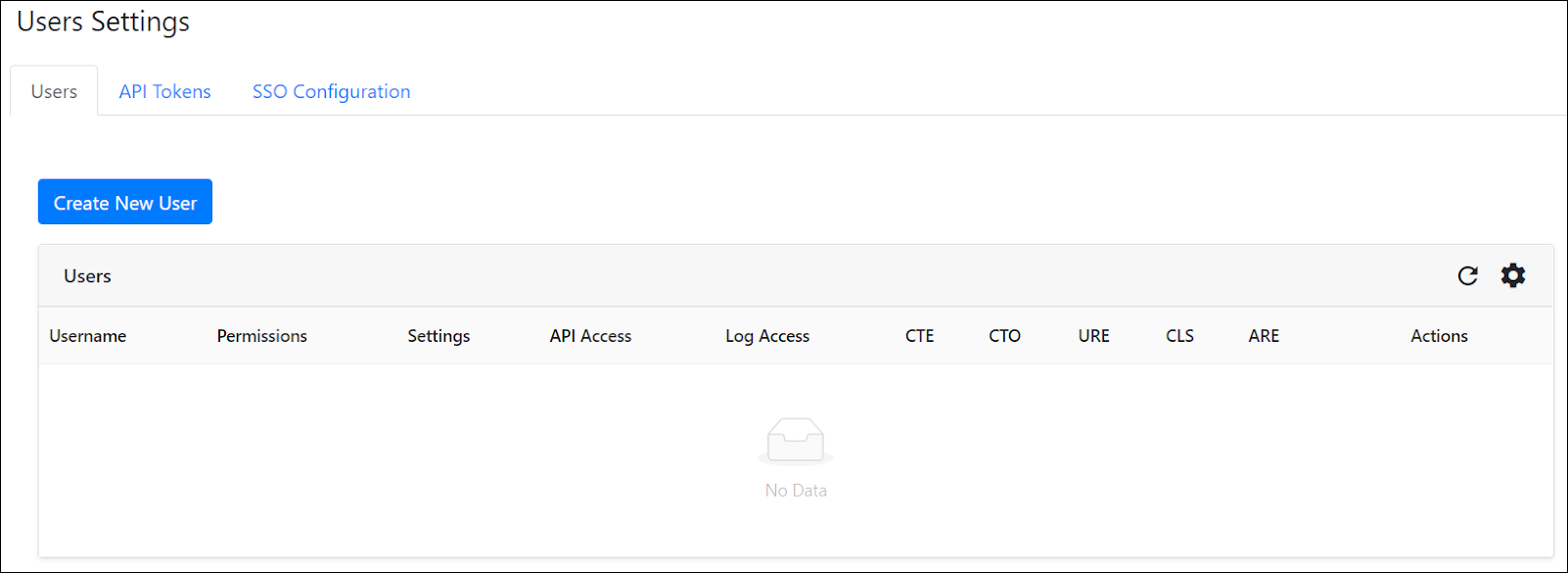 |
New users can be created by clicking the Add User icon in the upper right corner. Create a user by entering these parameters:
Username: Username associated with this account.
Password: Initial password for the user. User will be prompted to change password at the first login.
User Role: Super admin, Read-only User or Custom User roles can be assigned. The Custom User can have module-specific read/write permissions (refer to User Roles below). Enable the check boxes to give the Custom User API access and the ability to generate API tokens.
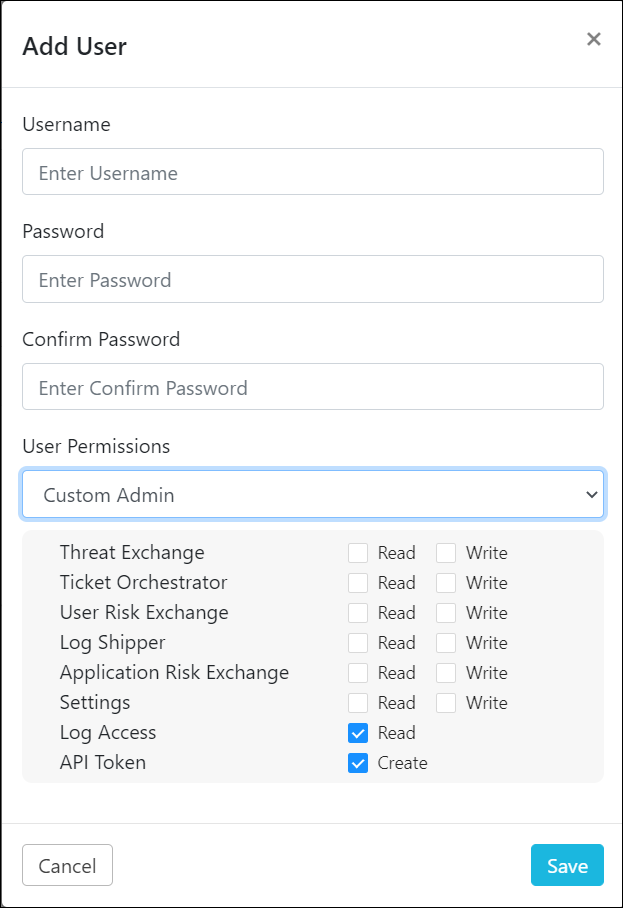 |
When finished, click Save.
User Roles
This user will have write level access to the application. Users will be able to create configurations, upload plugins, configure sharing and edit settings.
Admin users will not be able to create new users.
The read-only user will have limited access to the application. This user will not be able to perform any edit/update action on plugins and their configuration and settings.
The custom user can be given module-specific permissions that allow the following actions:
Read | Write | |
|---|---|---|
Settings |
|
|
Log Shipper |
|
|
Ticket Orchestrator |
|
|
Threat Exchange |
|
|
Risk Exchange - User |
|
|
Risk Exchange - Application |
|
|
RBAC Privillages
If this role is given then user can create new api token under Users -> API Tokens. User can access API Docs page as well.
If this role is given then user will be able to access Logging page and Tasks page.