Enabling Log Ingestion at Organization Level
This section describes the steps to enable log ingestion at the organization level.
Step 1: Creating a Role
Netskope requires permissions to support log ingestion from an organization successfully. Create a custom role using the cloud shell terminal provided by GCP.
Log in to console.cloud.google.com.
On the top-right, click the Activate Cloud Shell icon.

The cloud shell terminal opens at the bottom of the page.
On the shell prompt, type nano netskope_ueba.yaml and then press the enter/return key.
Copy the code below and save the file. To save, press Ctrl O followed by the enter/return key.
title: "Netskope_UEBA_Role" description: "Role for supporting Netskope for performing Audit Log Ingestion" stage: "ALPHA" includedPermissions: # get IAM roles to check the Netskope_UEBA_Role is present - iam.roles.get # get log sinks created for the project - logging.sinks.get # get project metadata and list projects under organization - resourcemanager.projects.get # this permission is required while listing and getting metadata for folders under root folder chosen for instance creation - resourcemanager.folders.get # get organization - resourcemanager.organizations.get
Execute the following command to create the Netskope_UEBA_Role and attach it to the organization. Replace the <
organization-id>with the actual ID of the organization.gcloud iam roles create Netskope_UEBA_Role --organization=<organization-id> \ --file=netskope_ueba.yaml
To identify the
organization-id, see this Google article.Ensure that the role is created by executing the command below. Replace the
<organization-id>with the actual ID of the organization.gcloud iam roles describe --organization=<organization-id> Netskope_UEBA_Role
Step 2: Creating a Service Account
Note
Service account can only be created inside a project and cannot be created at the organization level.
The service account created in this step will be used during the Netskope instance setup to perform operations such as verification of the log sink. In this procedure, you will create a service account with the role created in step 1 and download the JSON private key.
Log in to console.cloud.google.com.
Navigate to the project inside the organization where you intend to create the service account.
In the search box, type
IAMand click IAM & Admin.
On the left navigation bar, click Service Accounts.
On the main section, click + CREATE SERVICE ACCOUNT.
The Create service account page opens.
Under the Service account details section, enter a service account name and click Create and Continue.
Under the Grant this service account access to project section, click the Select a role drop-down, hover over the Custom roles and select Netskope_UEBA_Role. This is the same role you created in step 1.
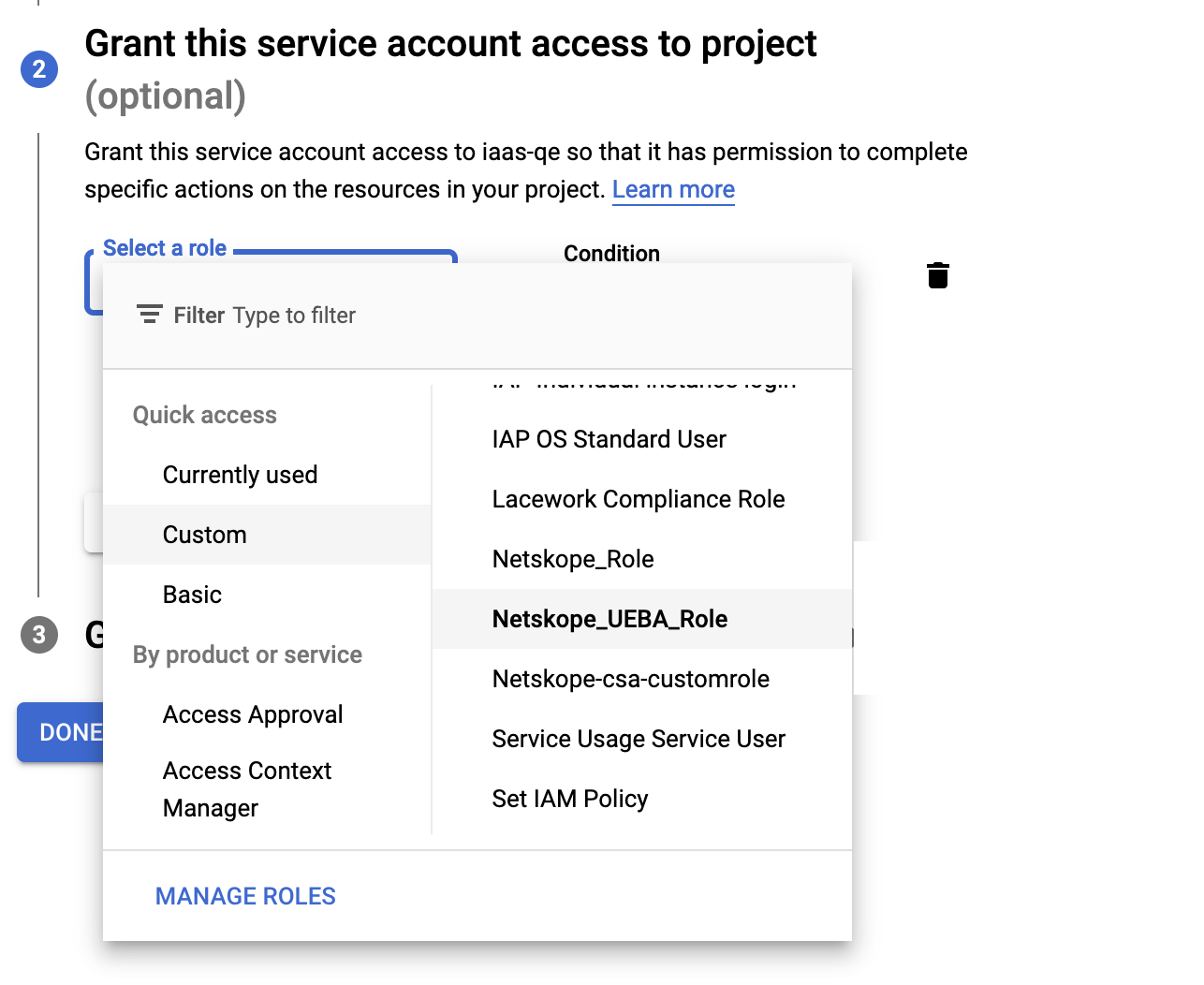
Click Continue and Done.
The new service account will be listed on the Service Accounts page.
Click the newly created service account and navigate to the Keys tab.
Click the ADD KEY drop-down list and select Create New Key.
On the Create private key for ... pop-up window, select the JSON key type radio button and click Create.
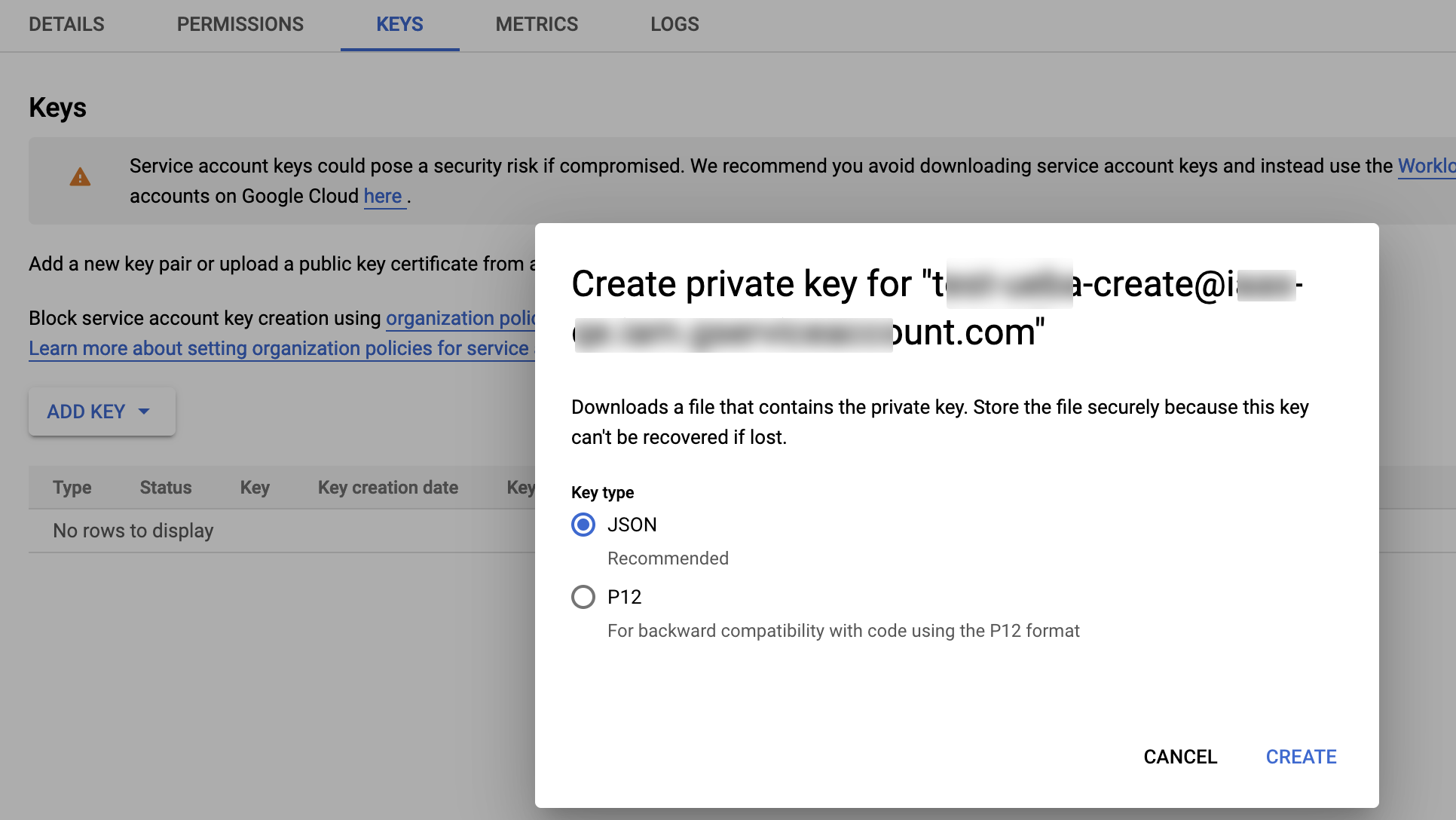
The UI will prompt you to download the JSON private key file onto your local laptop. This key will be required during the Netskope instance setup.
Step 3: Adding a Service Account to the Principal
To permit service account permissions at the organization level, the service account email address should be added as principal.
Log in to console.cloud.google.com.
Copy the email address of the service account you created in step 2.
At the top of the page, click the project selection drop-down list and select the organization.

In the search box, type
IAMand click IAM & Admin.
On the main section, click + ADD.
The Add principal to ... page opens.
Under the Add principals to ... pop-up window, paste the email address of the service account.
Click the Role drop-down list, hover over the Custom roles, and select Netskope_UEBA_Role.
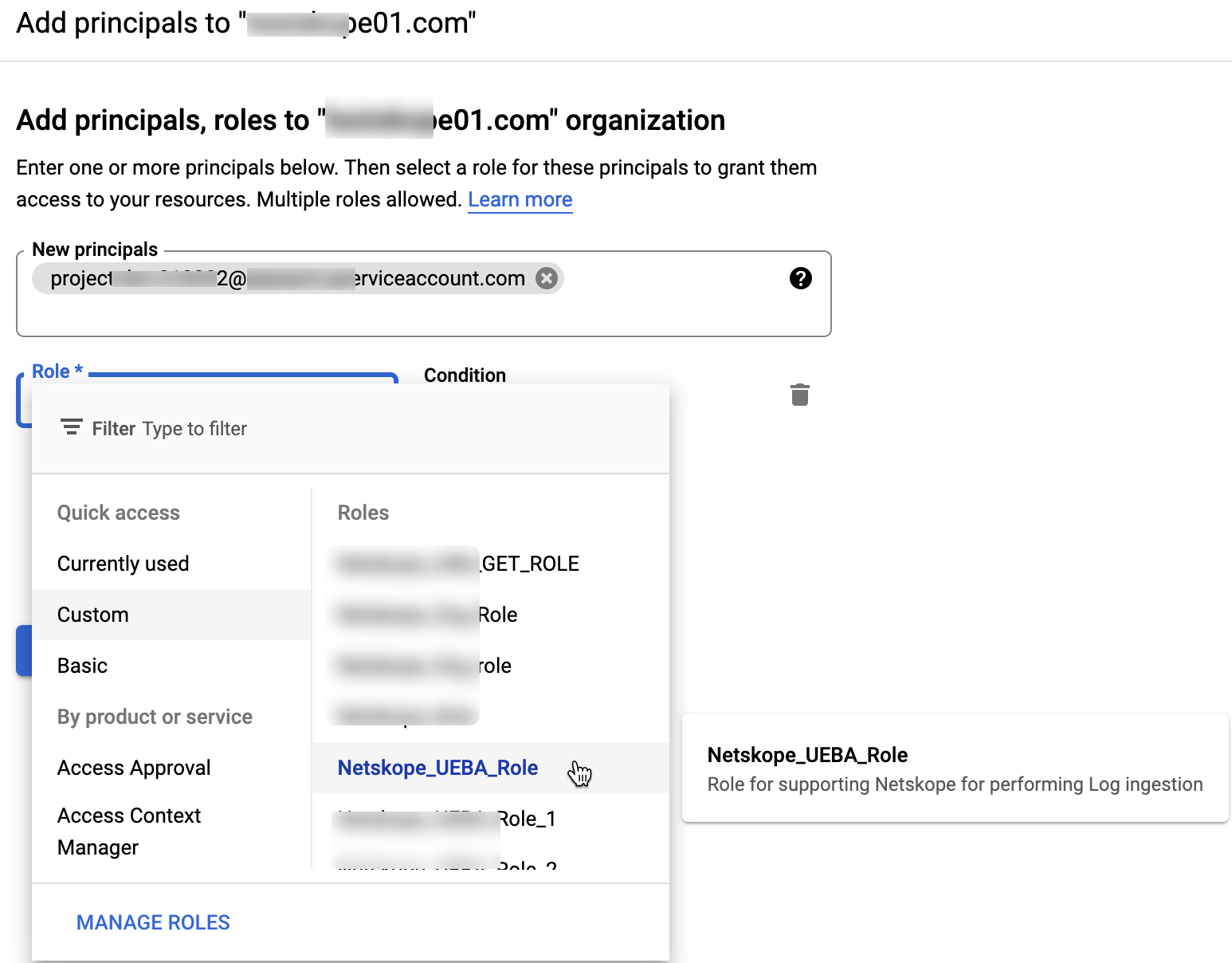
Click Save.
Step 4: Creating a Logs Router
Create a logs router using the cloud shell terminal provided by GCP. The logs router routes the logs from the organization to the Netskope pub/sub topic. For additional information on Log Router, see this Google article.
Log in to console.cloud.google.com.
On the top-right, click the Activate Cloud Shell icon.

The cloud shell terminal opens at the bottom of the page.
Execute the following command:
gcloud logging sinks create ns_ueba_sink pubsub.googleapis.com/projects/ns-iaas-ueba-prod/topics/ns_ueba4gcp_dc_<dc_name> --log-filter='protoPayload.@type:"type.googleapis.com/google.cloud.audit.AuditLog" AND NOT logName=~"vpc_flows$"' --include-children --organization=<organization-id>
dc_name: Based on the data center location of your tenant, enter the appropriate value:
AM2: nl-am2
FR4: de-fr4
SJC1: us-sjc1
SV5: us-sv5
Note
If you are not sure of the data center location of your tenant, contact your sales representative or Netskope support.
organization-id: To identify the organization-id, see this Google article.
On successful execution of the command, the cloud shell terminal will print the service account of the log router. Note down the service account of the logs router. This will be required during the Netskope instance setup.
A sample service account of the log router is as follows:
serviceAccount:<>-123456@gcp-sa-logging.iam.gserviceaccount.com
Note
As soon as you create a logs router, Google starts pushing logs into the logs router. However, the logs router may not have the appropriate permissions to publish to the pub/sub topic hosted by Netskope. The administrator of the organization, folder, or project may receive an email notification with an error code topic_permission_denied. You can ignore the email notification. To resolve this issue, log in to your Netskope tenant, set up the GCP instance, and grant access.
Once you have enabled log ingestion, log in to your Netskope tenant and set up the GCP instance. For detailed documentation, see Configure Google Cloud Platform on Netskope UI.