Mimecast Plugin for Threat Exchange
This document explains how to configure Mimecast with Cloud Threat Exchange in the Netskope Cloud Exchange platform. This integration allows for sharing of file hashes with Netskope that has been identified by Mimecast or Netskope. The file hashes shared with Mimecast can be used to perform various actions, like Block, Allow, or Delete on the messages with attachments matching the file hash(es).
To complete this configuration, you need:
A Netskope tenant (or multiple, for example, production and development/test instances) with a Netskope Secure Web Gateway license.
A Threat Protection license for malicious file hash sharing.
A Netskope Cloud Exchange tenant with the Threat Exchange module already configured.
A Mimecast account with a Bring Your Own Threat Intelligence (BYOTI) package for file hash sharing.
Create a custom File Profile.
Configure Mimecast credentials.
Configure the Mimecast Plugin.
Configure sharing for Netskope and Mimecast.
Validate the Mimecast Plugin.
In the Netskope UI, go to Policies , select File , and click New File Profile.
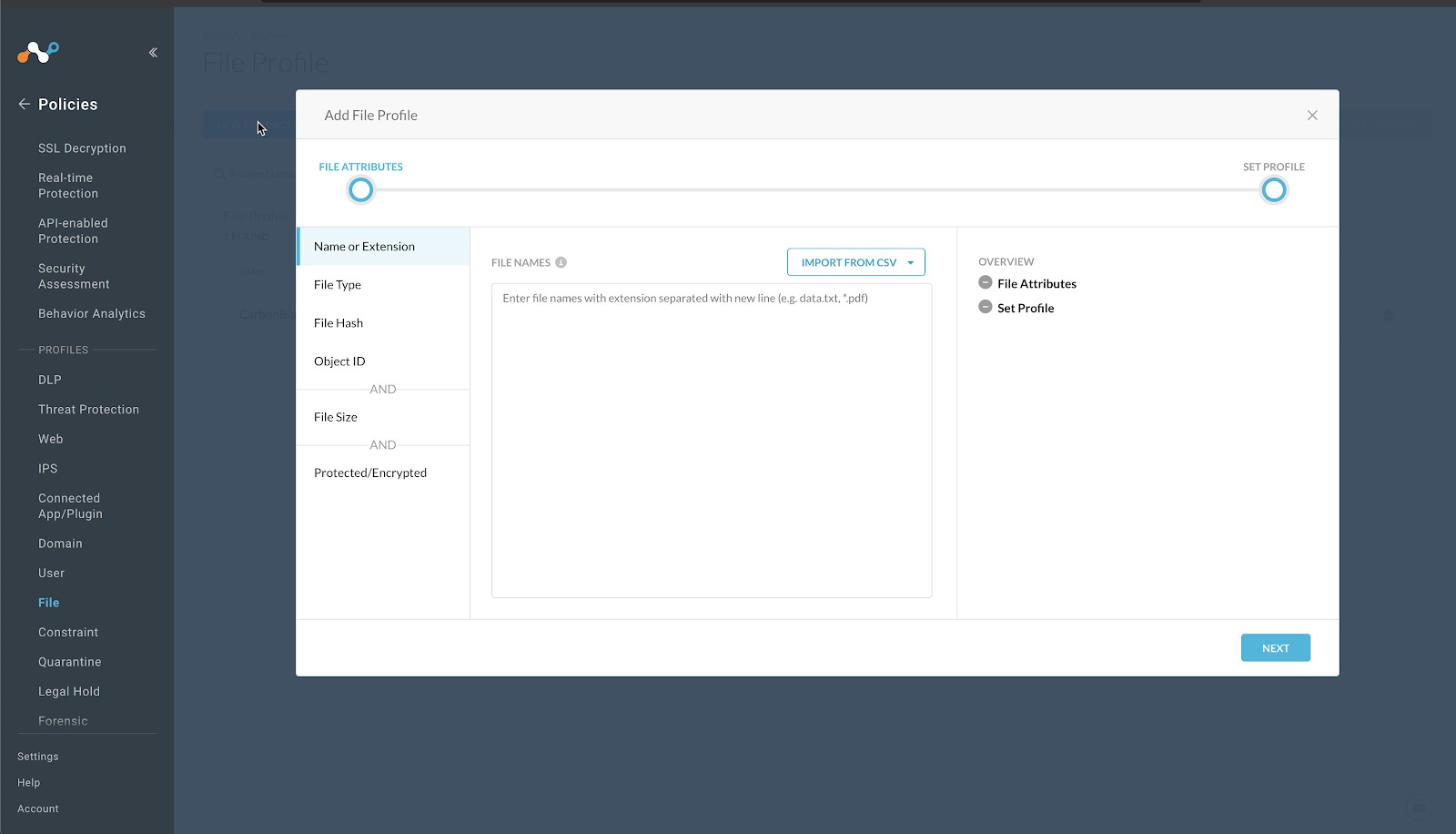
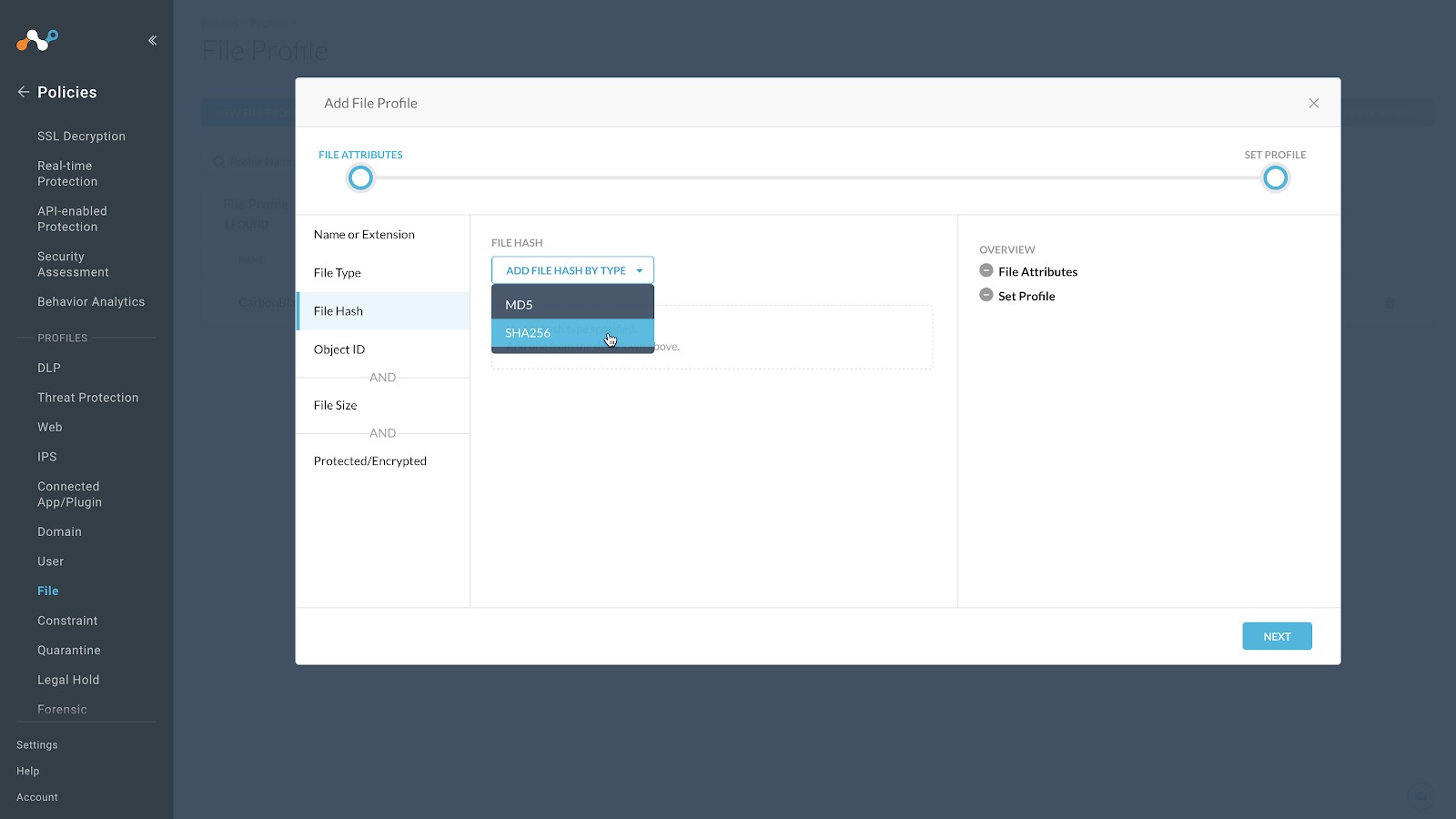
Click File Hash in the left panel, select SHA256 from the File Hash dropdown list.
Enter a temporary value in the text field. Netskope does not support progressing without having a value in this field, and recommends entering a string of 64 characters that consists of the character
f. For example,ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff. This will have a very low possibility of matching a valid file format.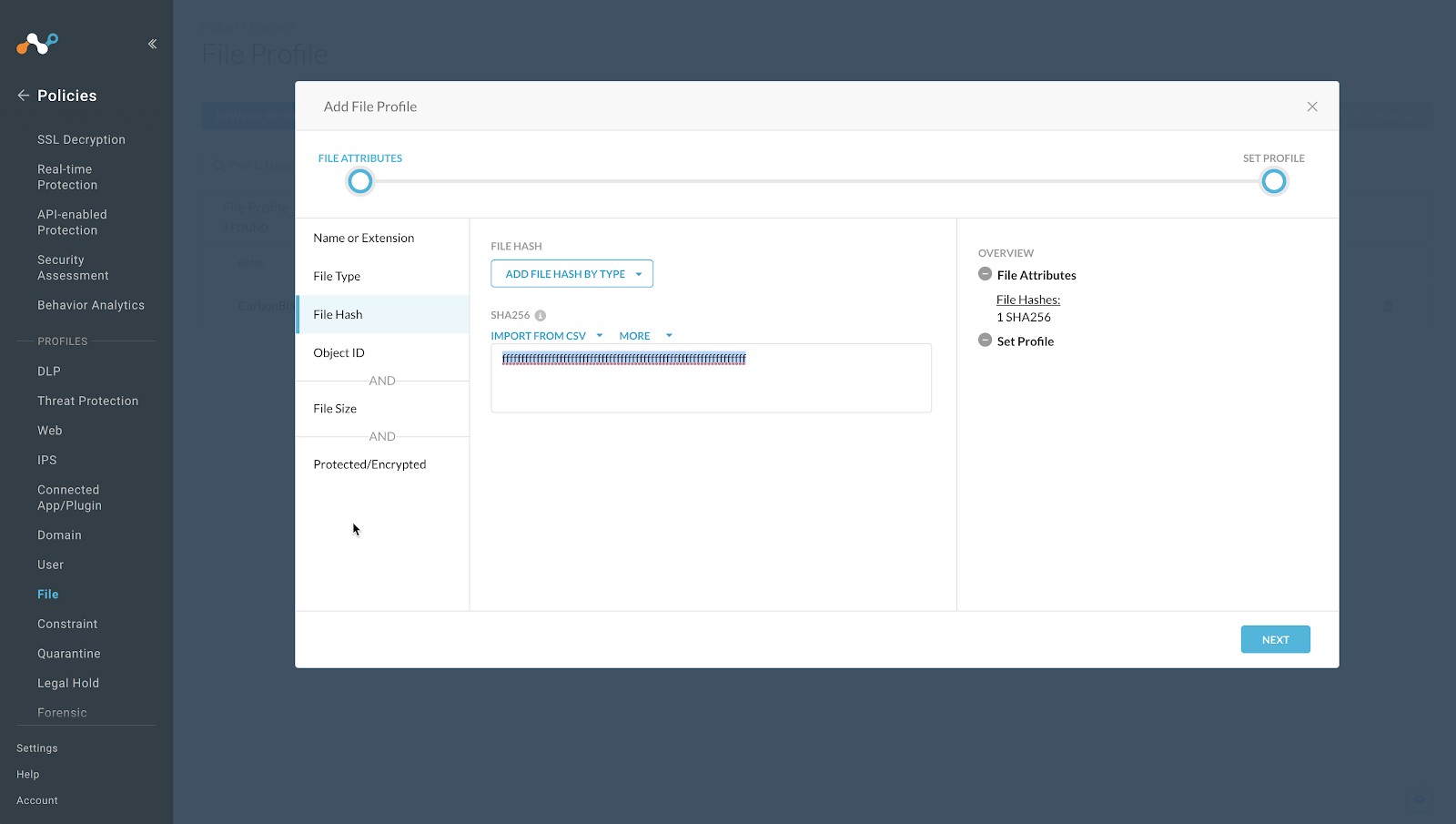
Click Next.
Enter a Profile Name and a Description. We recommend not having blank spaces in your profile name; use underscores for spaces.
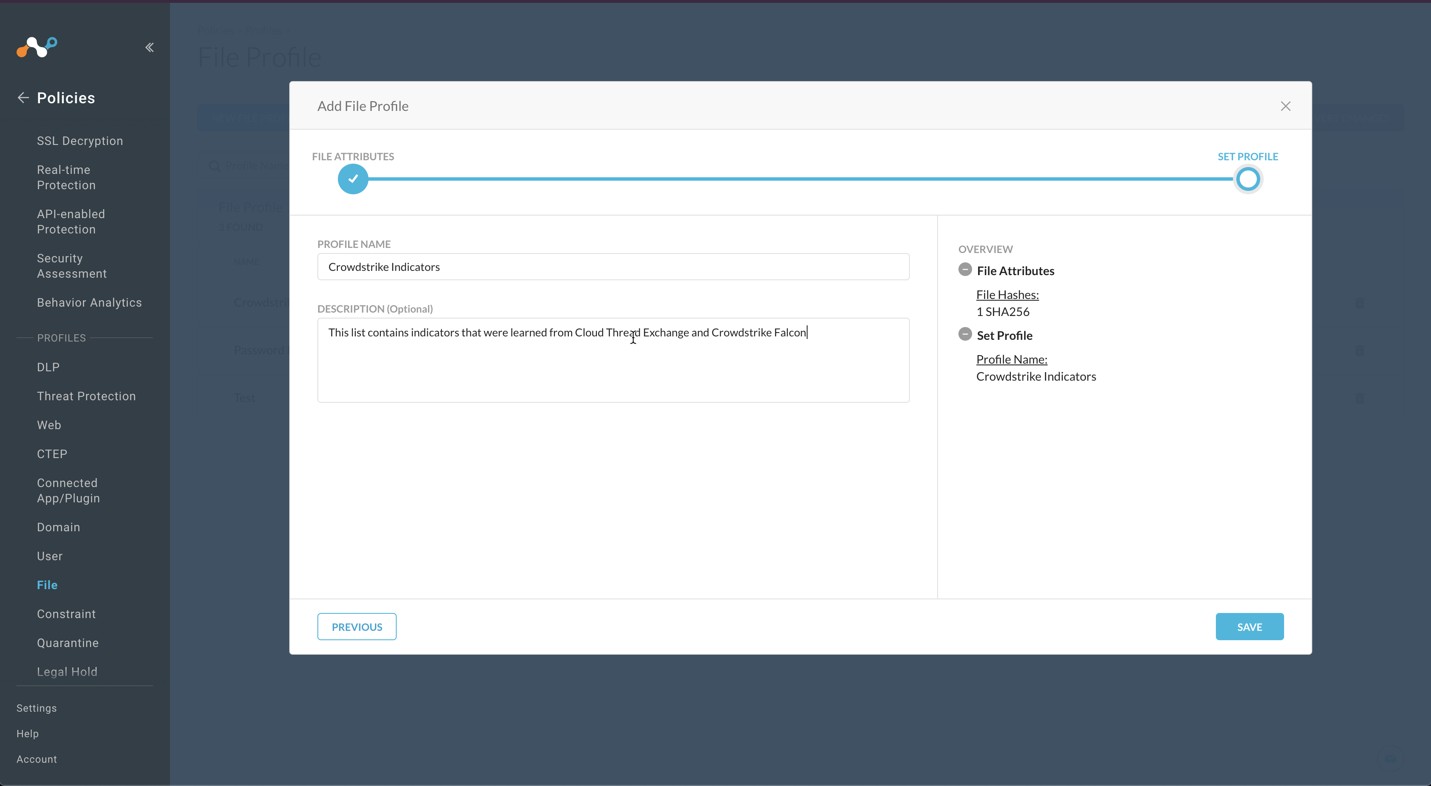
Click Save.
To publish this profile into the tenant, click Apply Changes in the top right.
Log in to your Mimecast instance.
Make note of the region in Mimecast Instance URL, in the form of
https://login-<region>.mimecast.com/.... You will need this when configuring the Mimecast Plugin in Threat Exchange.Create a new user.
Go to Administration > Directories > Internal Directories to open the Internal Domains page.
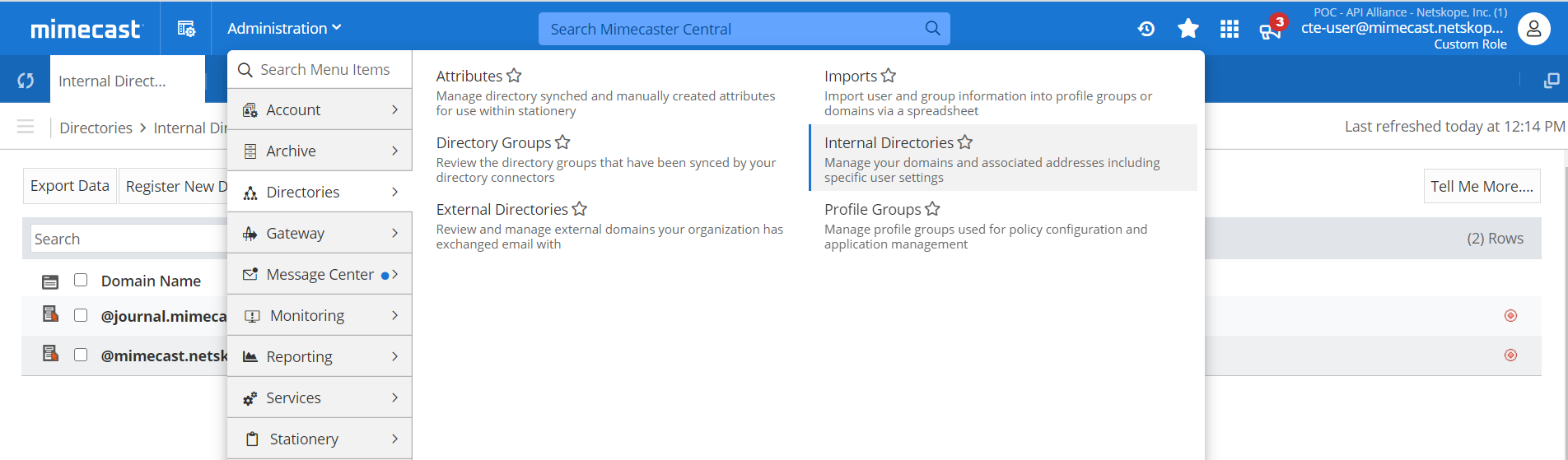
Select the internal domain where you want to create your new user.
Select the New Address button from the menu bar.
Enter a new email address, the user’s password, and phone number (required for 2FA). Select Save and Exit to create the new user.
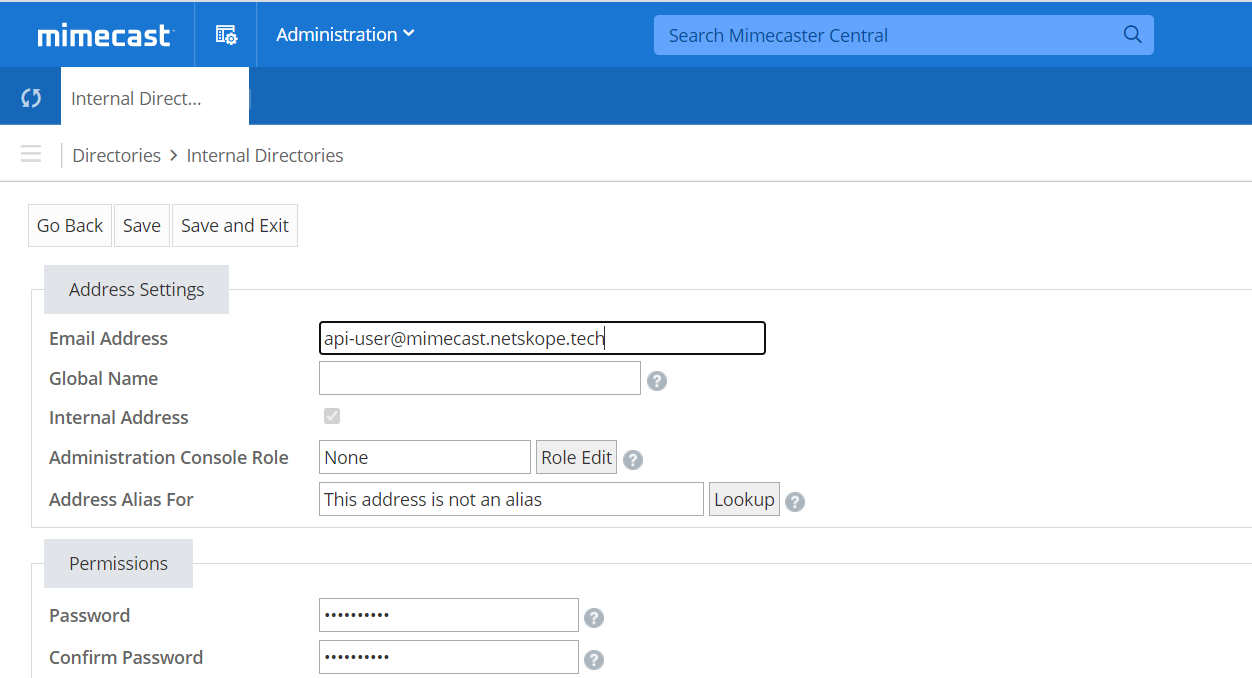
Keep a note of the password because you will use this to get your Authentication Tokens at a later stage.
Add the newly created user to an Administrative Role.
Go to Administration > Account > Roles to open the Roles page.
Right-click the Basic Administrator role and select Add Users to Role.
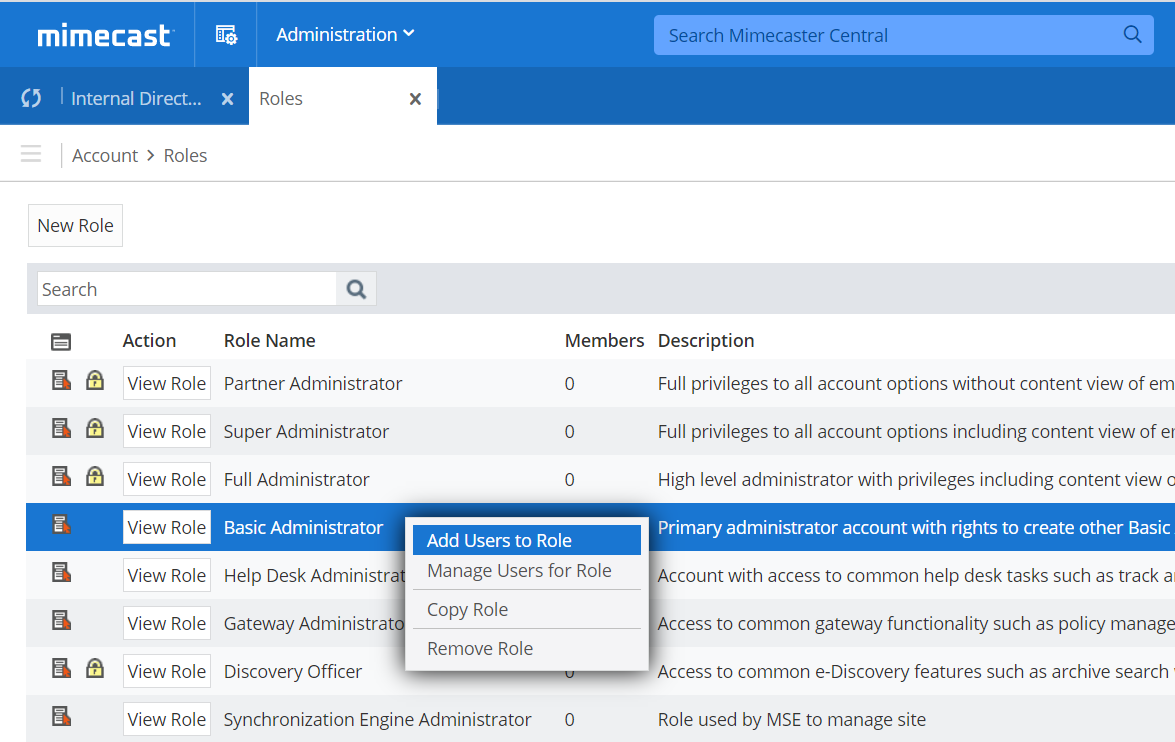
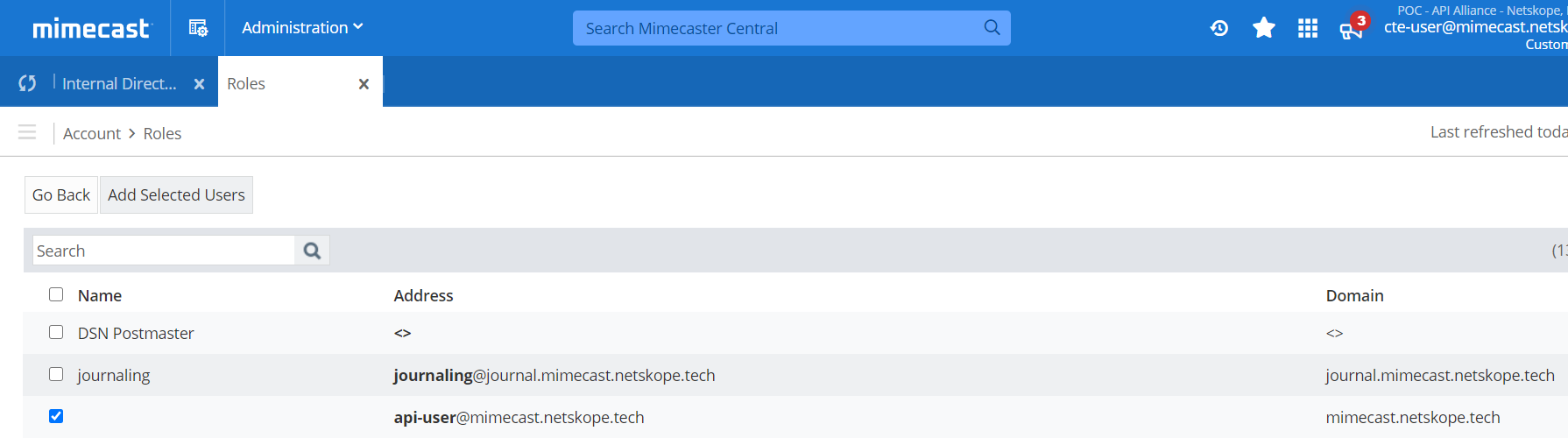
Browse or search to find the new user created in Step 3.
Select the checkbox to the left of the user.
Click Add Selected Users to add the user to this role.
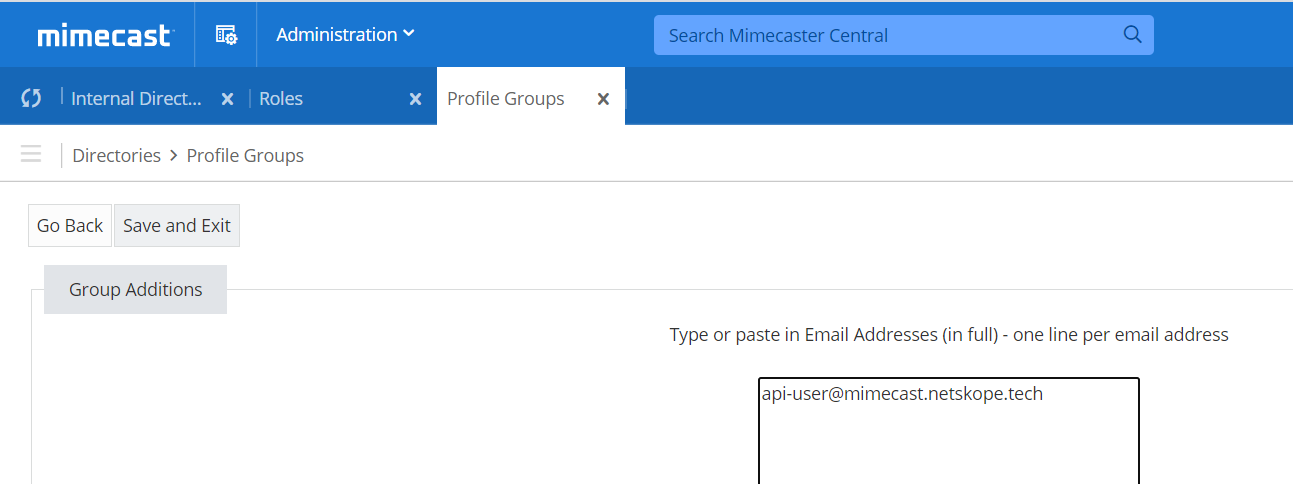
Create a new group and add your new user.
Go to Administration > Directories > Profile Groups to open the Profile Groups page.
Create a new group by selecting the plus icon on the parent folder where you would like to create the group. This creates a new group with the name New Folder.
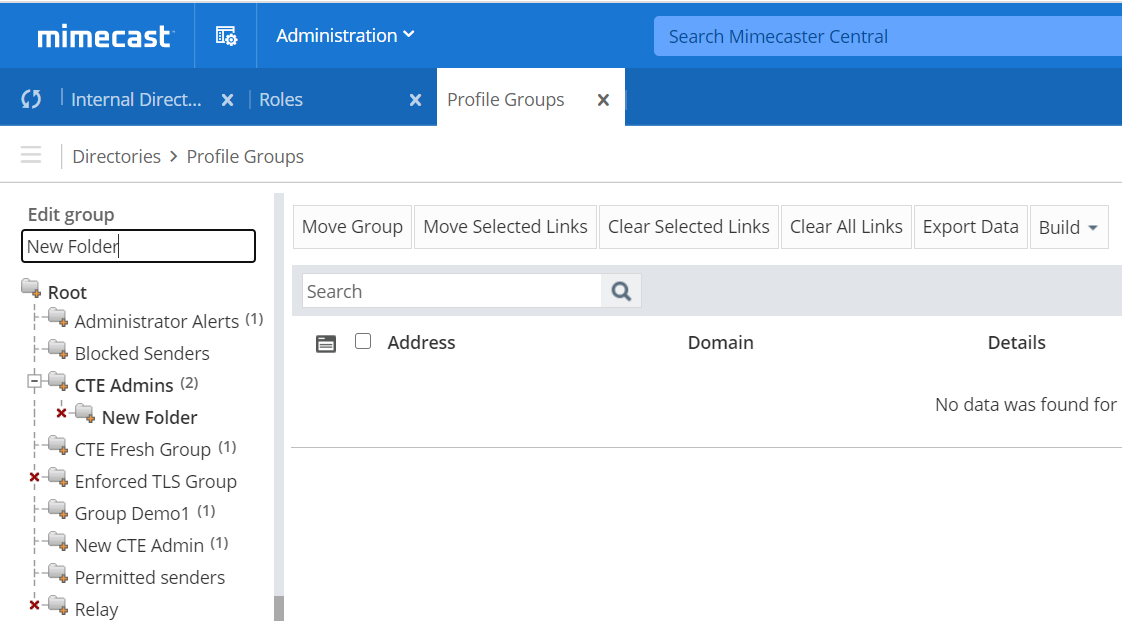
To rename the group, select the newly created New Folder group, and then in the Edit group text field, enter the name you want to give the folder; for example, CTE Admin and then press the Enter key to apply the change.
With the group selected, select the Build drop down list and select Add Email Addresses.
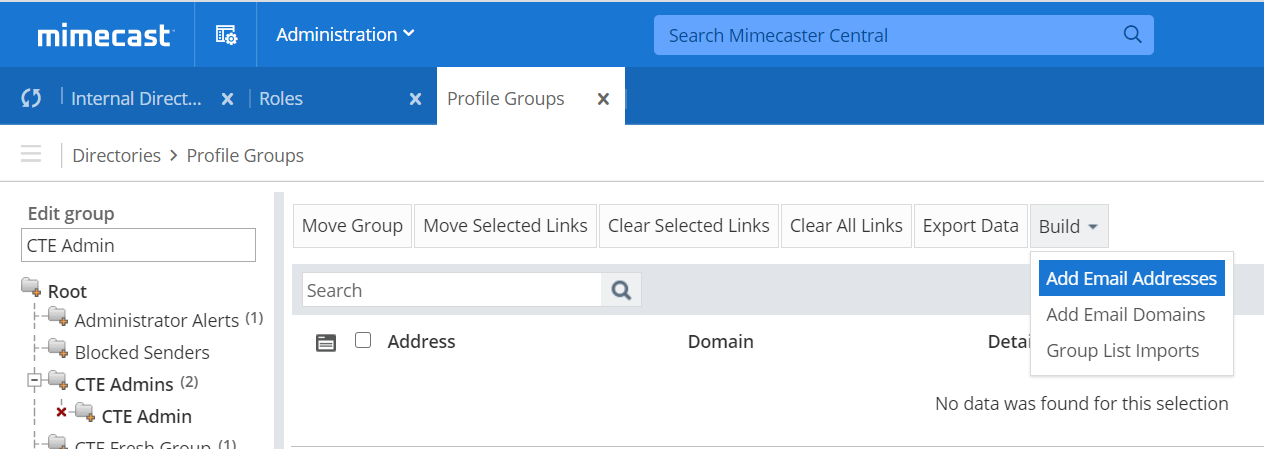
Enter the name of the new user created in Step 3.
Select Save and Exit to add the new user to the group.
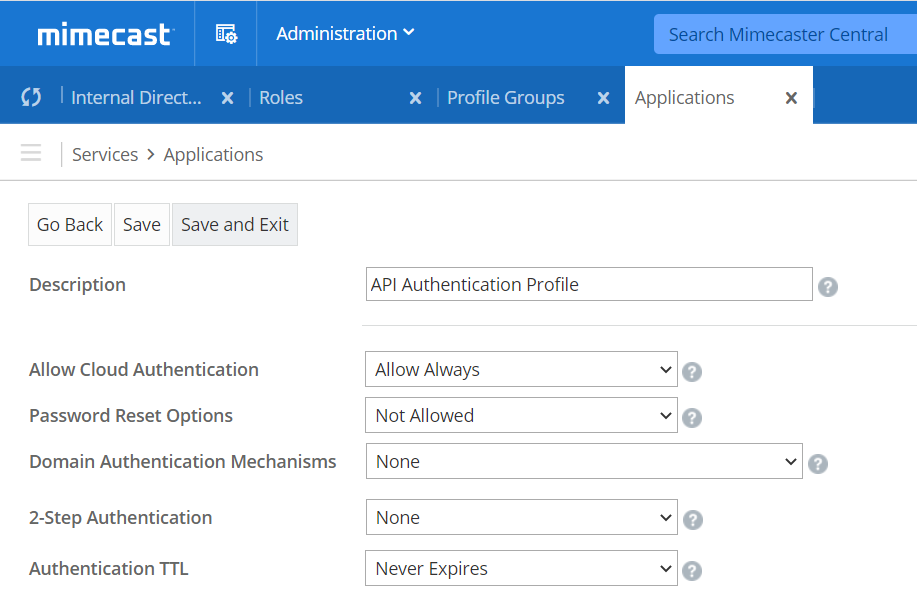
Create a new Authentication Profile.
Go to Administration > Services > Applications to open the Application Settings page.
Select the Authentication Profiles button.
Select the New Authentication Profile button.
Type a Description for the new profile.
Set the Authentication TTL setting to Never Expires. This ensures that your Authentication Token will not expire and impact the data collection of the app.
Leave the other setting defaults.
Select Save and Exit to create the profile.
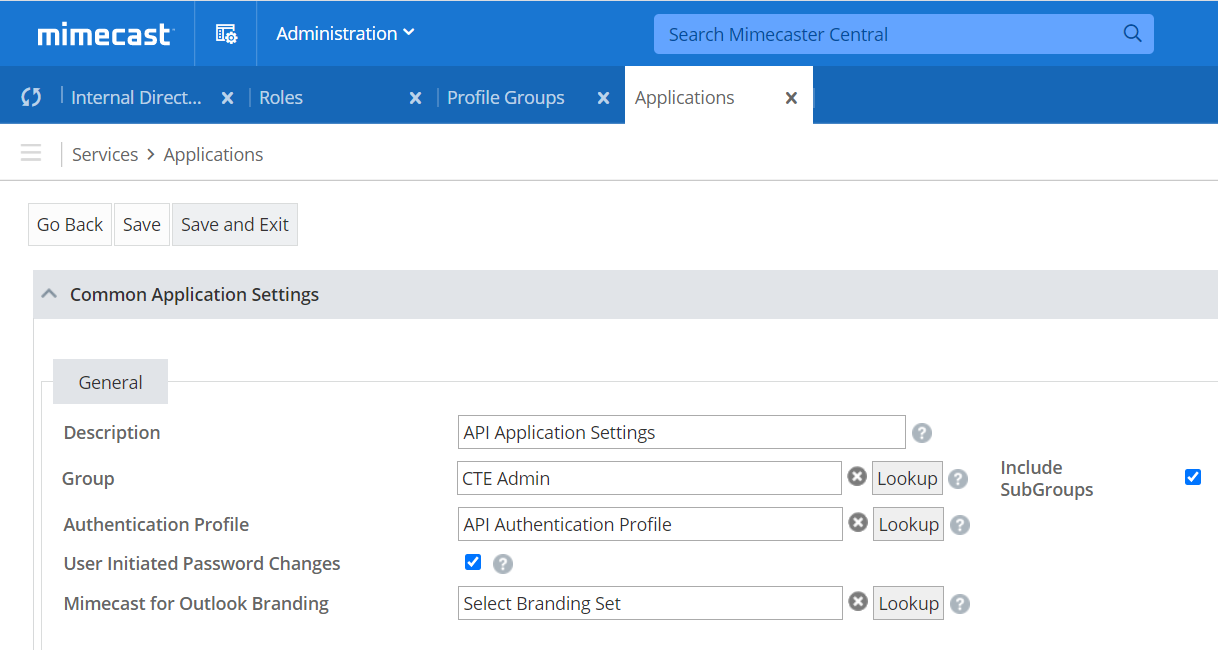
Create a new Application Setting.
Go to Administration > Services > Applications to open the Application Settings page.
Select the New Application Settings button.
Enter a Description.
Use the Group Lookup button to select the Group that you created in Step 5.
Use the Authentication Profile Lookup button to select the Authentication Profile created in Step 6.
Leave the other setting defaults.
Select Save and Exit to create and apply the Application Settings to your new group and user.
Create a new API Application.
Go to Administration > Services > API Applications to open the API Applications page.
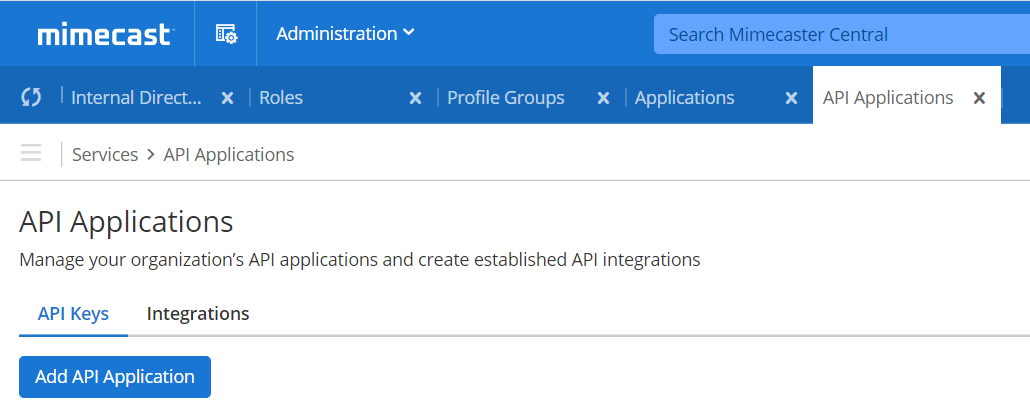
Click on Add API Application to create a new API application to be used in Threat Exchange.
Enter the appropriate information for your API Application. Check Enable Extended Session to ensure your API token will never expire. Select Other in Category, and then click Next.
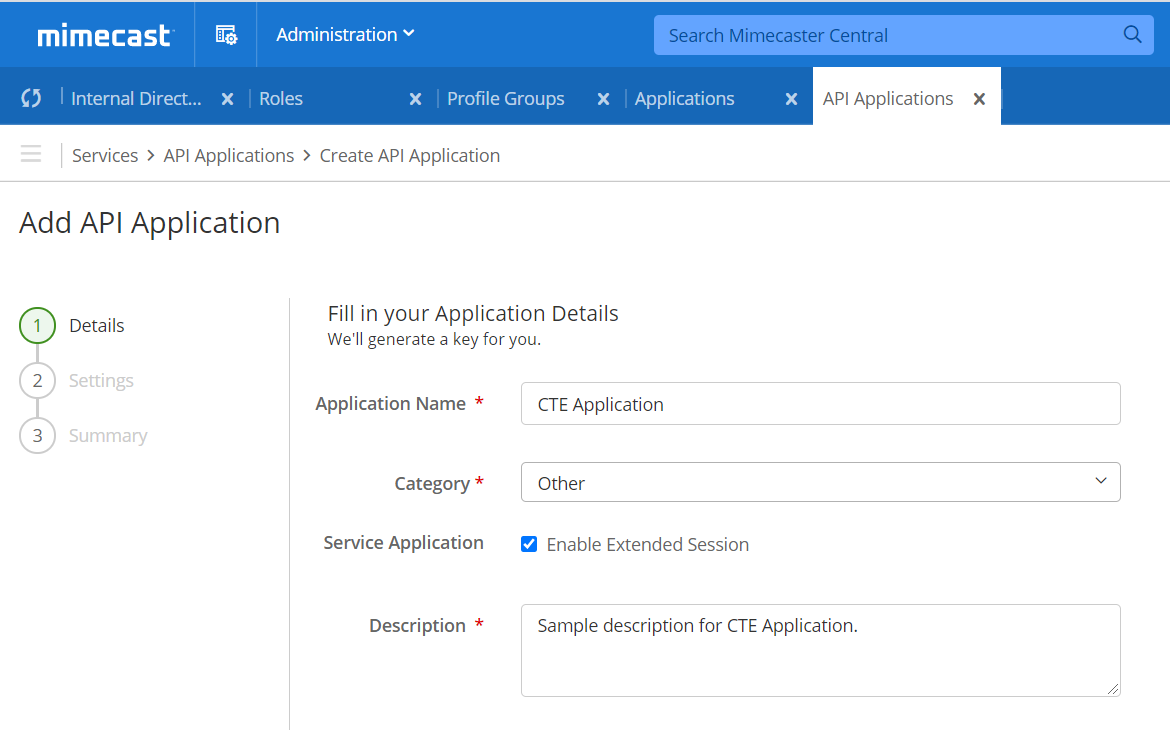
Enter a Developer Name, and enter the Email address created previously, which links the user's application/profile settings to the API application. Click Next.
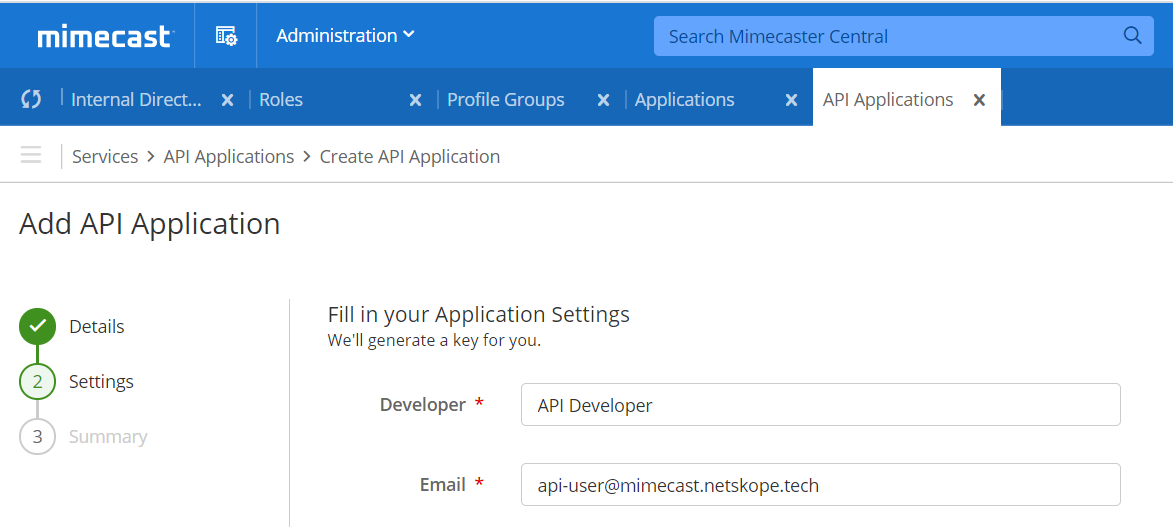
Review the entered configuration parameters, edit them if required, and then click Add in the bottom right.
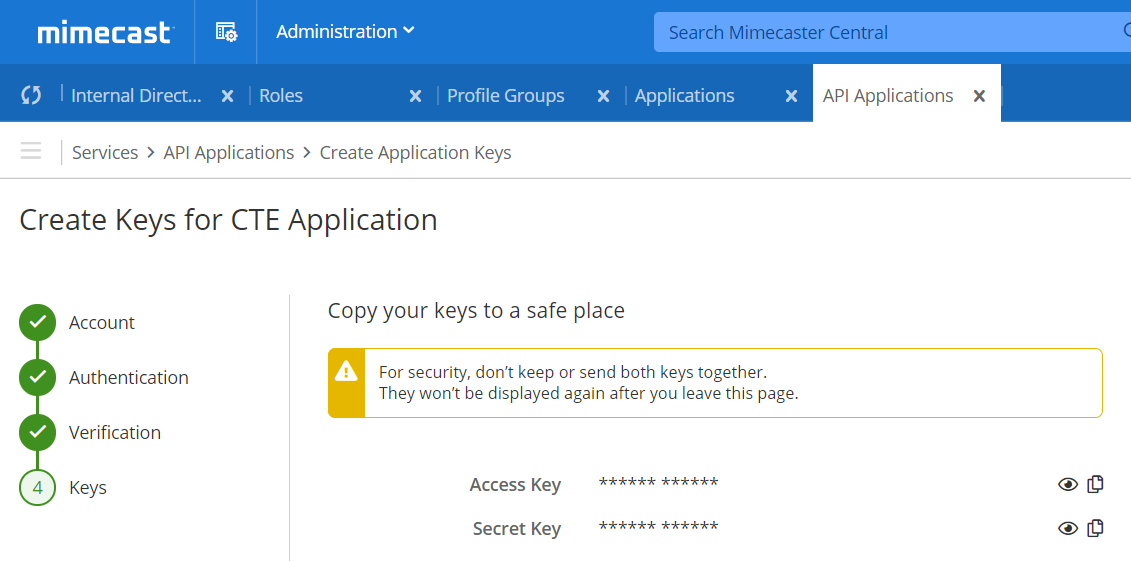
Your API application will be created and its details will be displayed. Click the small “eye” icon beside Application Key in order to view it. Copy both Application ID and Application Key for configuring the Mimecast plugin.
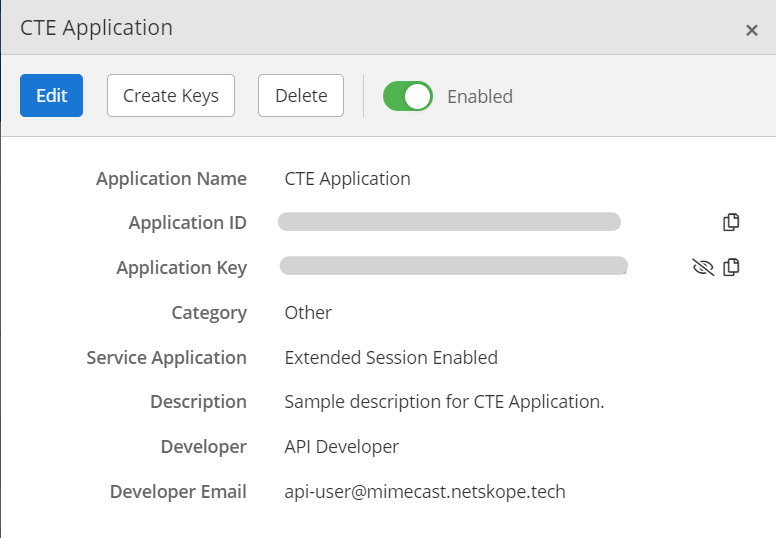
Get Access key and Secret Key
Note that these Keys can be generated only after 30 minutes of creating a new API application.
Go to Administration > Services > API Applications to open the API Application page.
Select your newly created API application, and then click Create Keys from the top menu.
Enter the email address of the user created previously and click Next.
For Type select Cloud and enter the password of the user created previously. Click Next button.
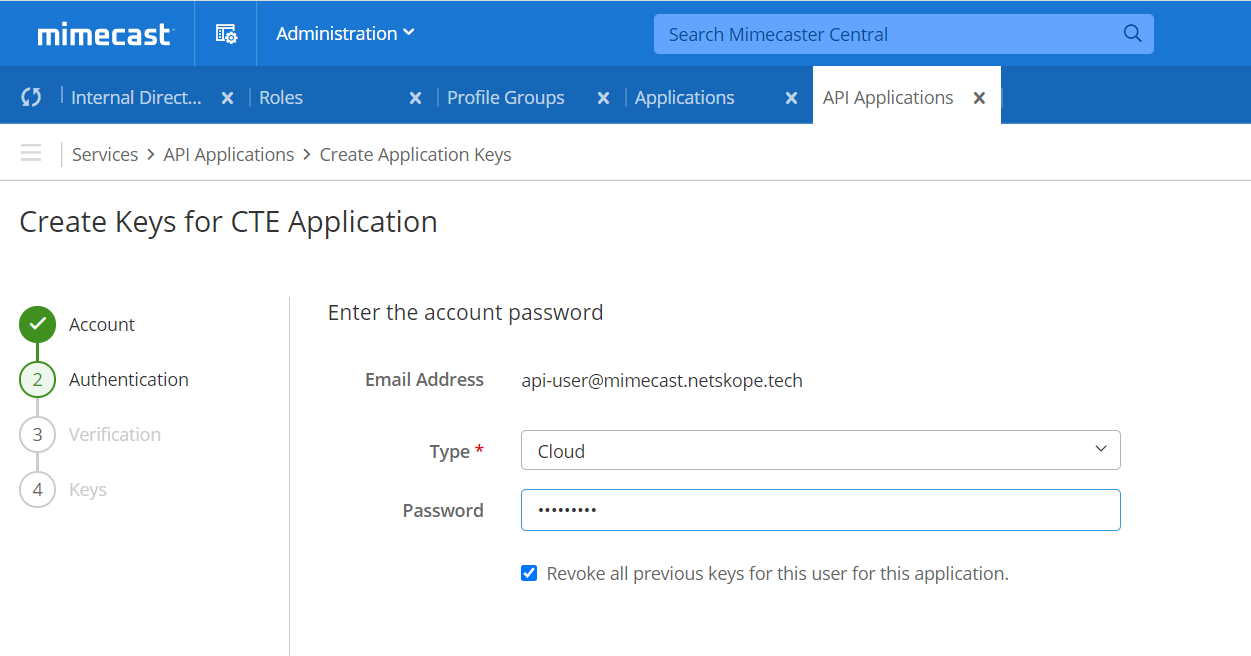
An OTP (Code) will be generated and sent to the user's mobile device. Enter the OTP here, and click Next.
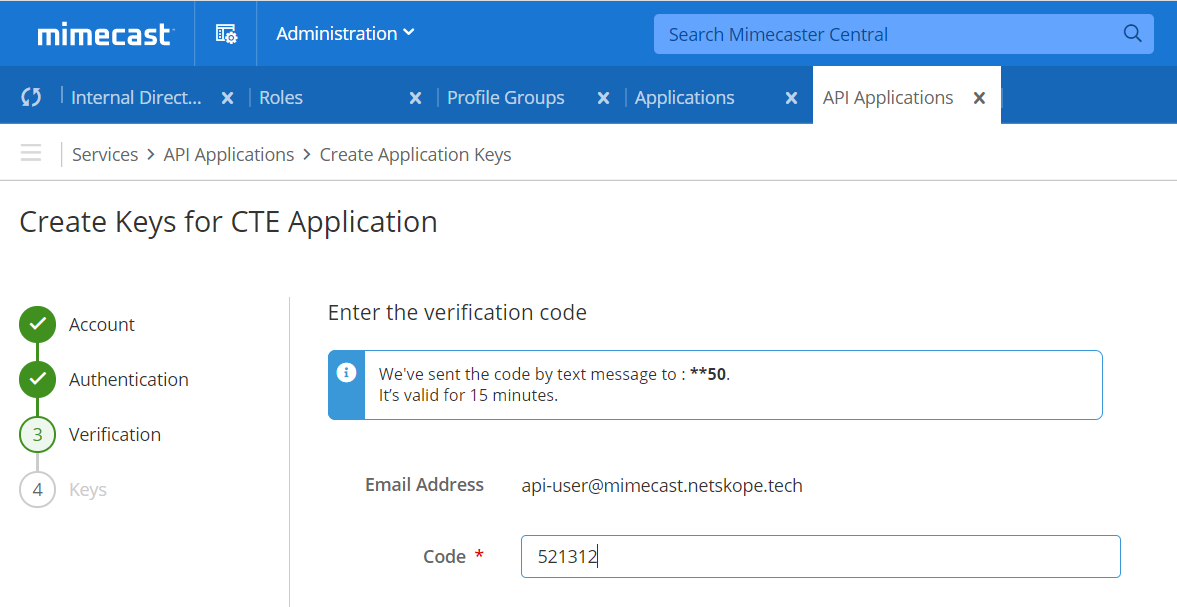
Copy both of the keys displayed by pressing the small copy icon beside each. You will need these when configuring the Mimecast Plugin. When finished, click Close.
In Cloud Exchange, go to Settings and click Plugins.
Search for and select the Mimecast box to open the plugin creation pages.
Enter and select the Basic Information on the first page:
Configuration Name: Enter a name appropriate for your integration.
Sync Interval: Adjust to environment needs. We recommend not to go below 5 minutes for production environments.
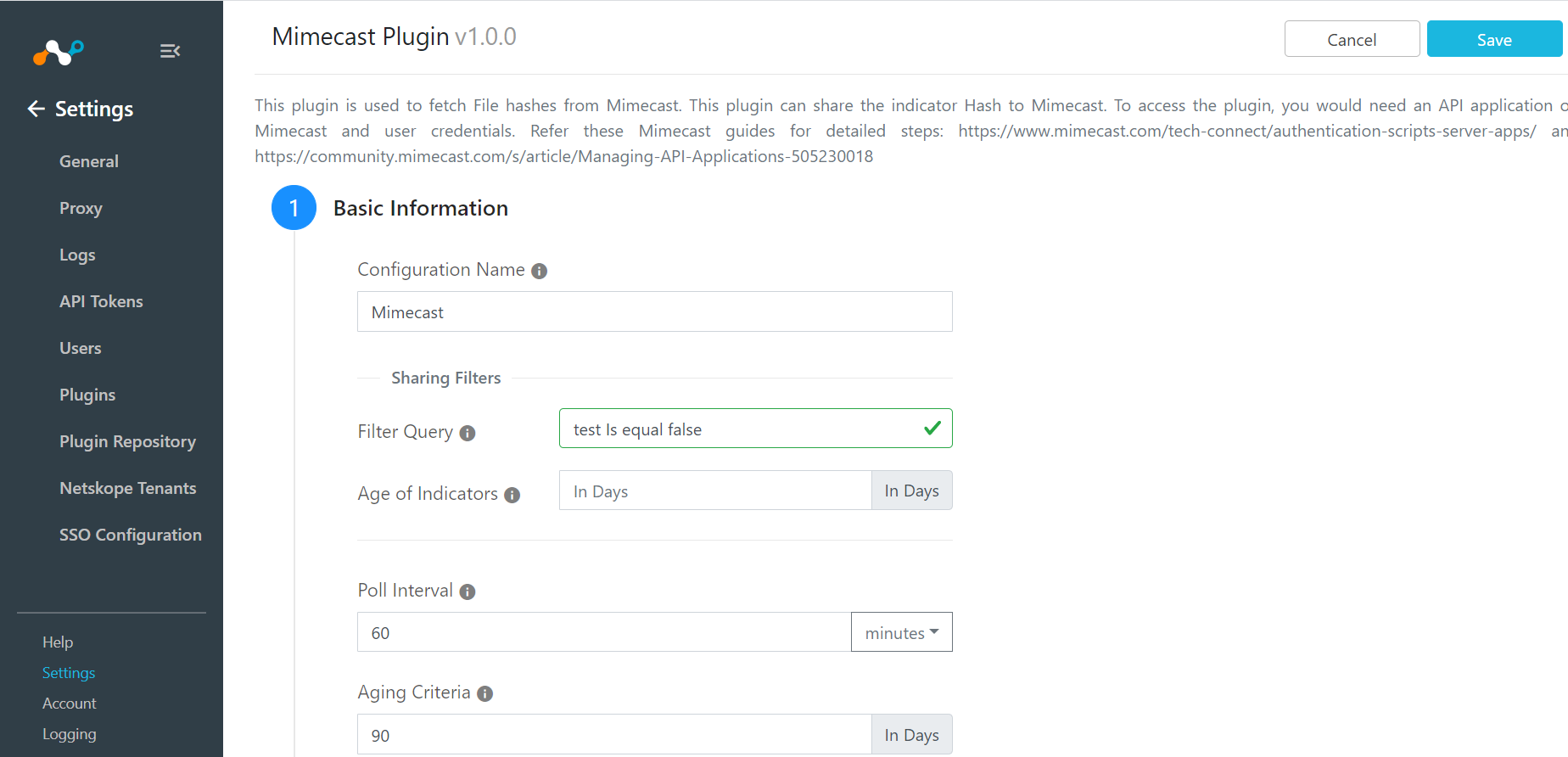
Click Next.
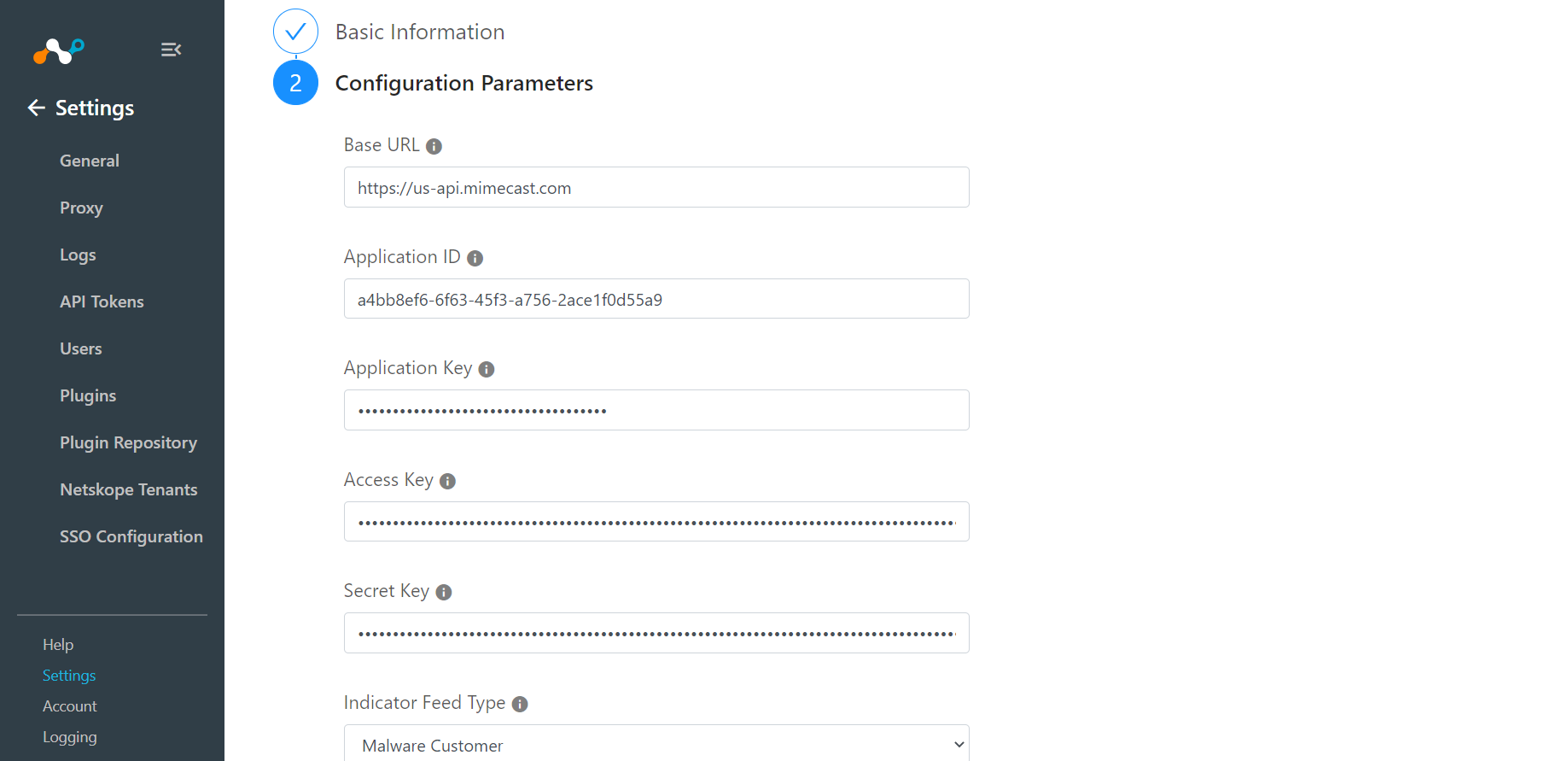
Enter and select the Configuration Parameters on the second page:
Base URL: Enter your Base URL, the region URL you noted in the step 2 when configuring Mimecast credentials. For more information about Base URLs, https://www.mimecast.com/tech-connect/documentation/api-overview/global-base-urls/
Application ID: Enter your Application ID copied when creating your API Application.
Application Key: Enter your Application Key copied when creating your API Application.
Access Key: Enter your Access Key copied when creating your API Application.
Secret Key: Enter your Secret Key copied when creating your API Application.
Leave the other setting defaults.
Click Save. Click on Threat Exchange in the Cloud Exchange left nav panel to view the installed plugins.
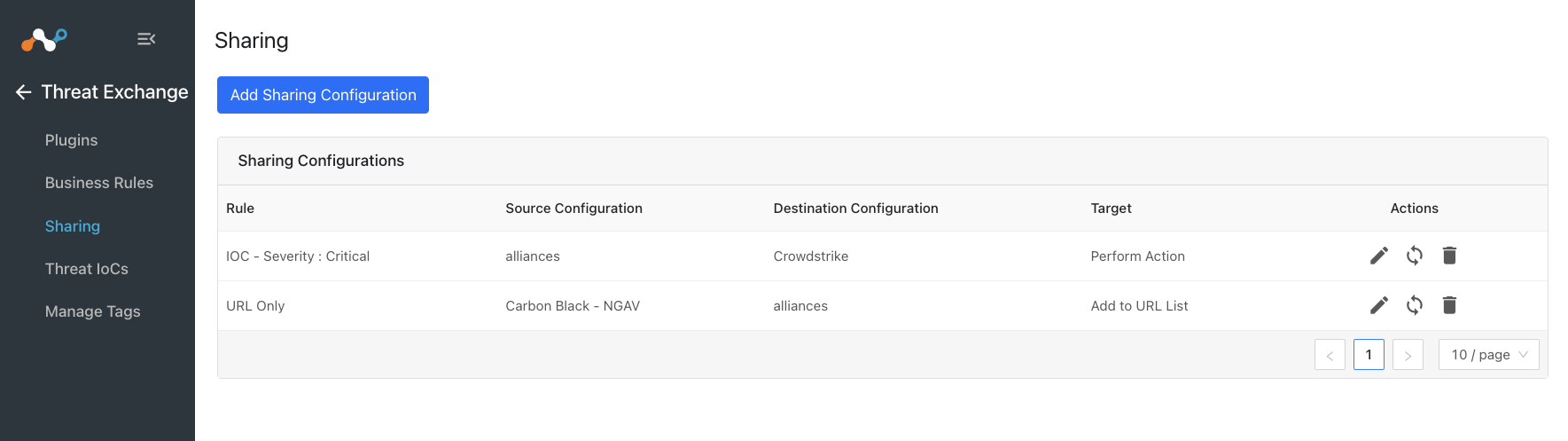
Go to Threat Exchange and select Sharing. The Sharing page displays the existing relationships for each sharing configuration in grid view as shown below. The Sharing page also has inputs to configure new sharing from one plugin to another.
Click Add Sharing Configuration, and in the Source Configuration dropdown list, select Mimecast.
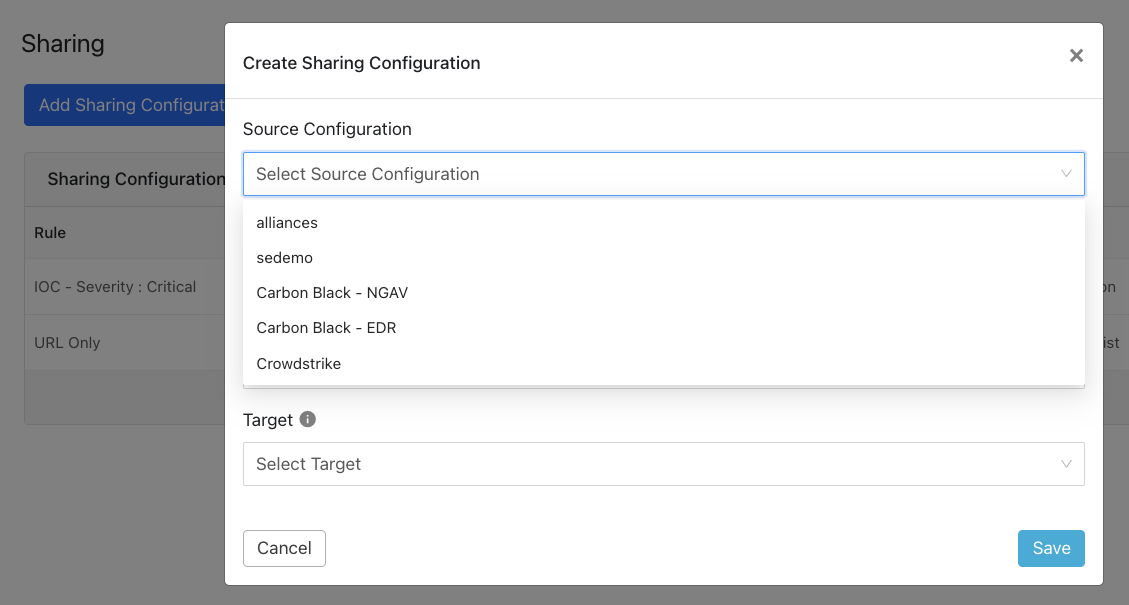
Select a Business Rule, and then select Netskope for the Destination Configuration. Sharing configurations are unidirectional. data obtained from one plugin is shared with another plugin. To achieve bi- or multi-directional sharing, configure each separately.
Select a Target. Each plugin will have a different target or destination for the IoC.
Click Save.
Repeat steps 2-5, but select Netskope as the Source Configuration and Mimecast as the Destination Configuration.
Click Save.
Adding a new sharing configuration on the active source poll will share the existing IoCs of the source configuration to the destination configuration. Whenever a new sharing configuration is built, all the active IoCs will also be considered for sharing if they match the source/destination combination.
Note
Plugins that do not have API for ingesting data cannot receive threat data. This is true of the installed plugin API Source, which provides a bucket associated with an API endpoint for remote 3rd-party systems to push data to. Once a Sharing policy has been added, it takes effect.
After a sharing configuration has been created, the sharing table will show the rule being invoked, the source system providing the potential IoC matches, the destination system that will receive matching IoC, and the target applicable to that rule. Multiple Sharing configurations can be made to support mapping certain IoC to multiple targets even on the system destination system.
Modify, Test, or Delete a Sharing Configuration
Each configuration supports 3 actions:
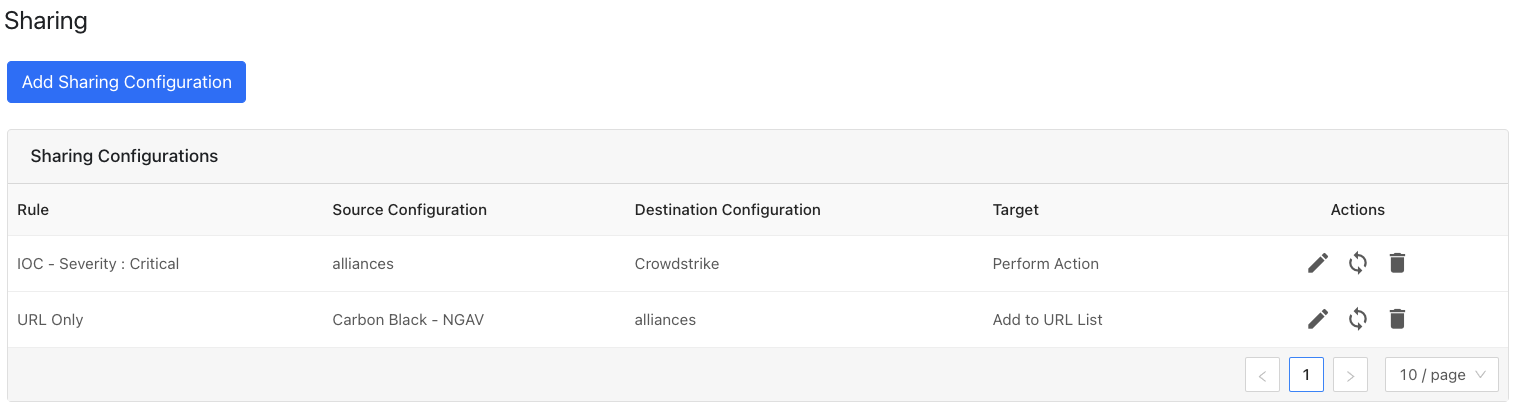 |
Edit the rule by clicking on the pencil icon.
Test the rule by clicking on the synchronization icon. This tests how many IoC will actually be sent to the destination system based on the timeframe and the rule.
Delete the rule by clicking on the garbage can icon.
In order to validate the workflow you must have Netskope Alerts and/or Mimecast attributes/indicators. Polling Intervals are defined during plugin configuration.
Go to Threat Exchange and select Threat IoCs.
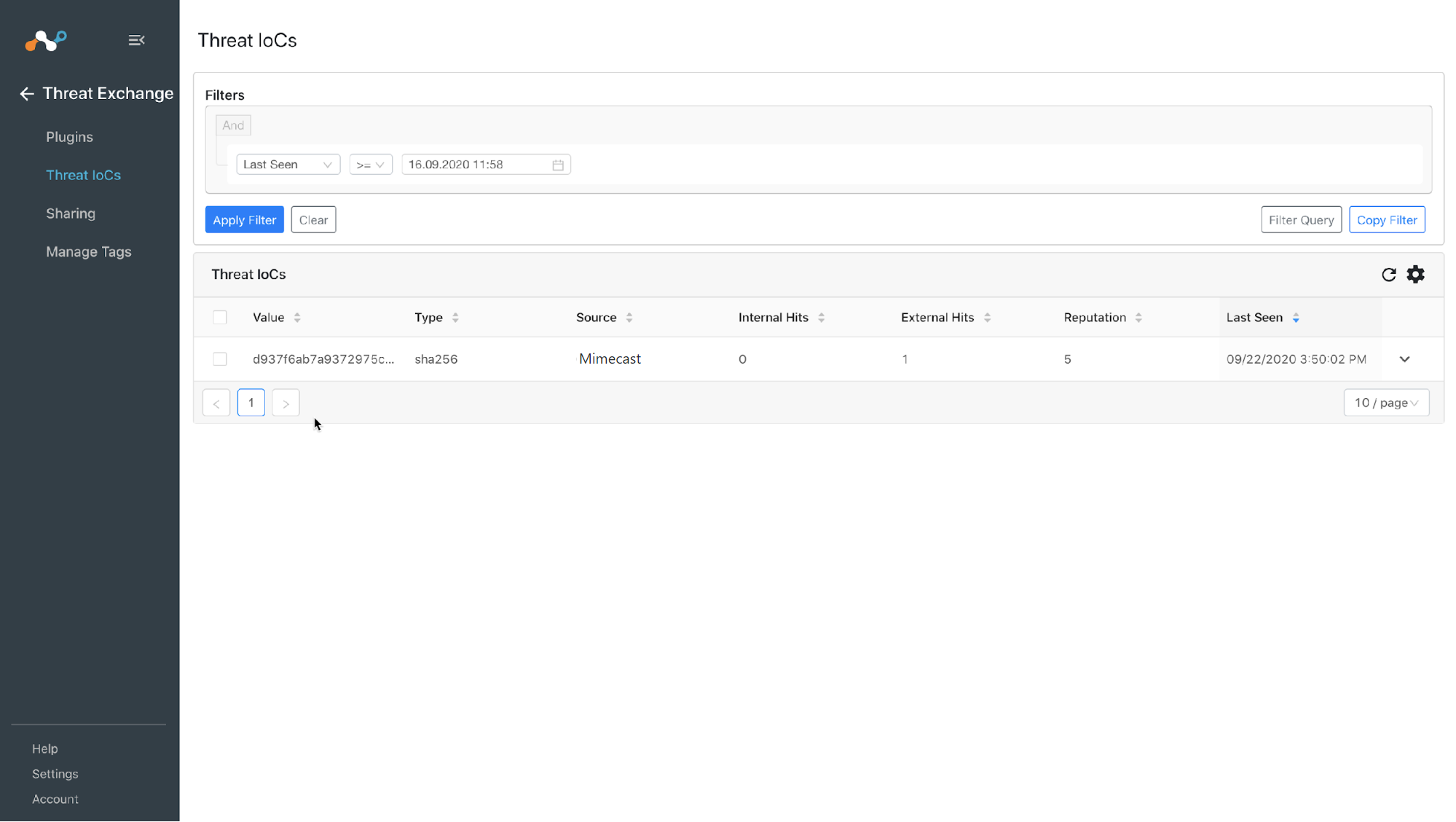
In your Netskope tenant, go to Policies and select File > Your Custom File Profile, and then click File Hash.
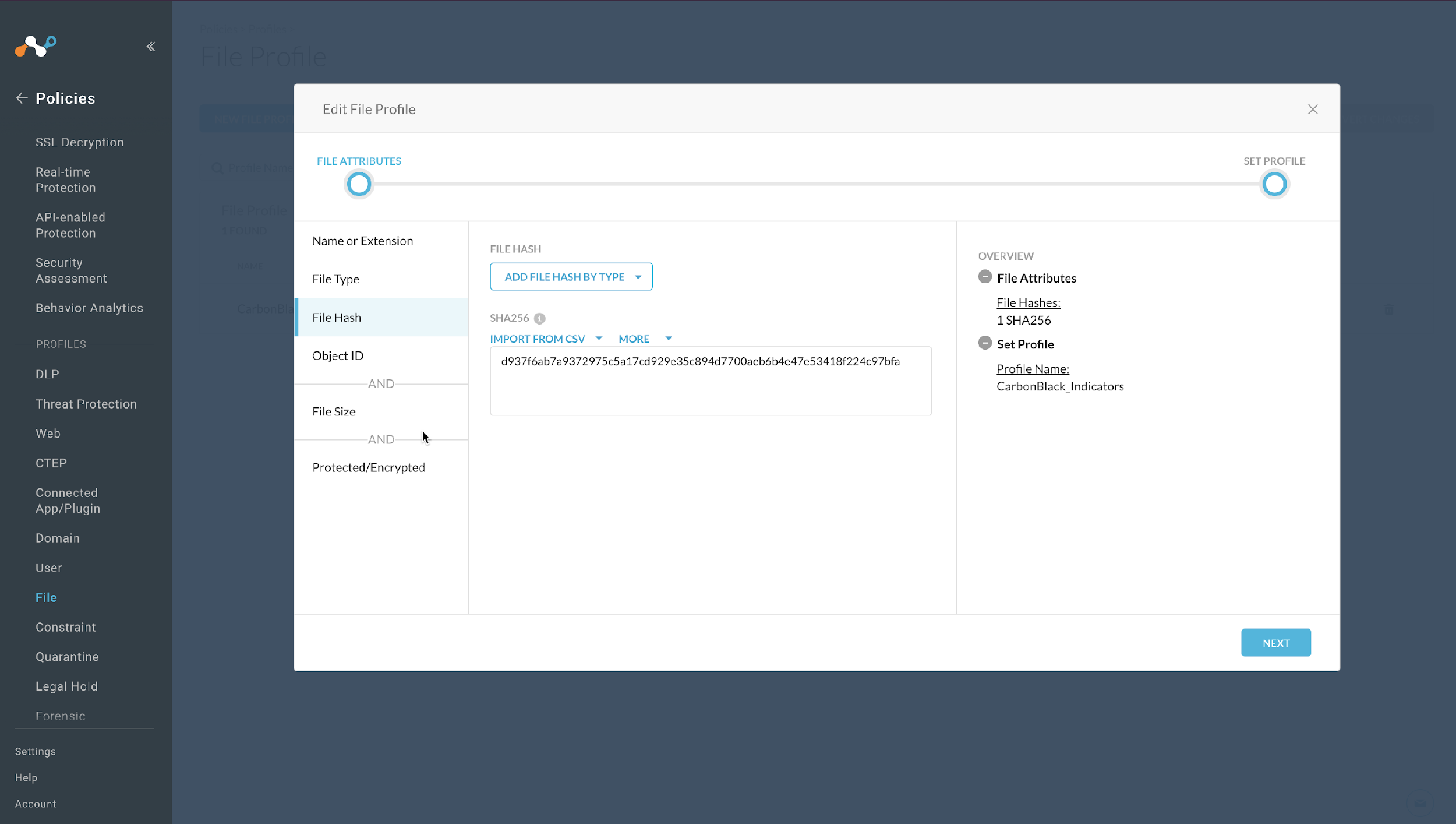
Note
The indicators shared with Mimecast won’t be displayed on the Mimecast console. However, based on the Operation Type selected in your Mimecast configuration, the messages/emails matching the pushed file hashes will be either Allowed, Blocked, or Deleted.
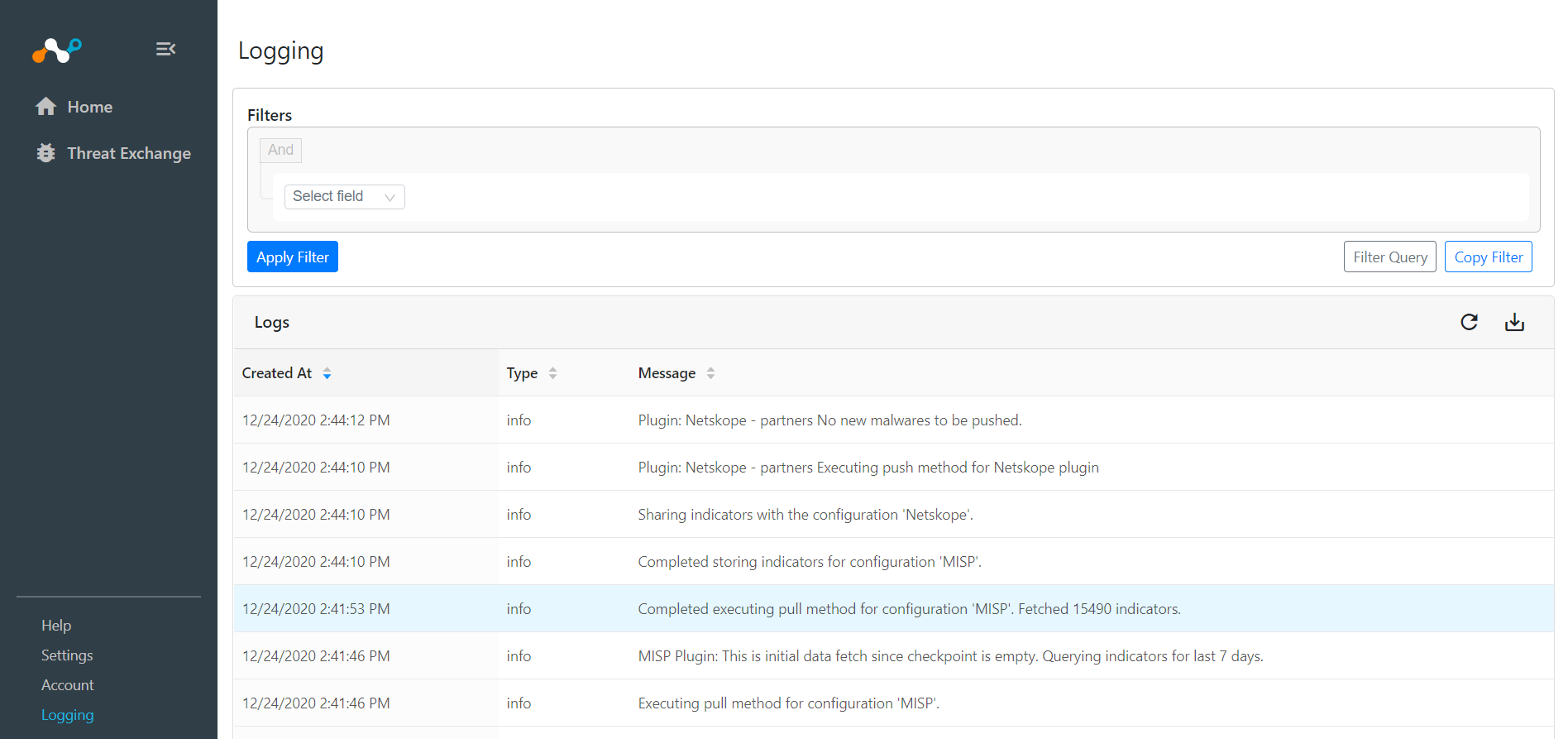
If data is not being brokered between the platforms, you can look at the audit logs in Threat Exchange. In Threat Exchange, select Logging, and then look through the logs for errors.